A modern workplace is inconceivable without remote work. While it may seem like a simple request, it could be quite a burden for IT personnel. The business priorities must also be considered to protect the company’s data.
However, many approaches exist to introducing IT security functions in your business. There are multiple technologies that you could choose to incorporate into your setup. One of the most forward-thinking methods is the adoption of the SASE framework. Here’s how it could modernize your legacy security infrastructure.
SASE adoption statistics
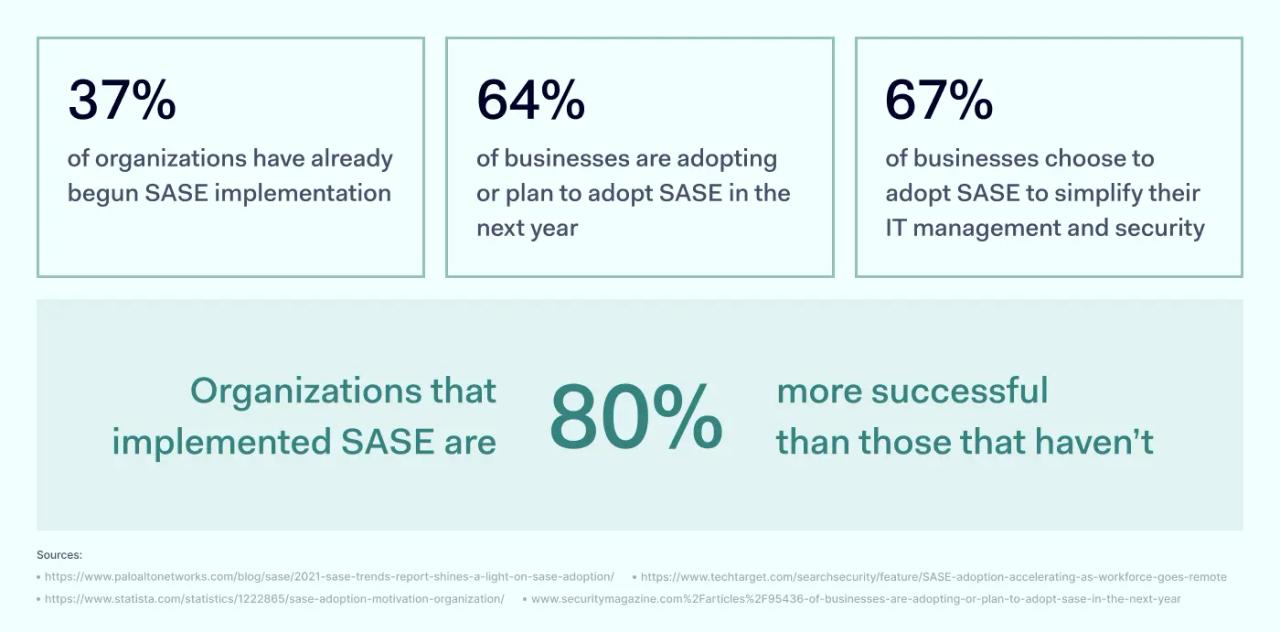
Based on various reports, SASE adoption is on the rise, we can expect that in the near future, SASE will become a common IT management standard. The benefits that SASE brings are among the reasons for its adoption. However, it may not always be clear where to start if you’re at square one.
Driving factors of SASE adoption
SASE is gaining traction in the corporate world. Here are the top five reasons that are driving companies toward SASE adoption:
- Increased remote work. The shift to remote work, which was accelerated by the pandemic, requires secure, flexible access to corporate resources from anywhere. SASE offers a solution that supports this need.
- Cloud adoption. As companies move more of their operations and data to the cloud, traditional network security models become less effective. SASE provides a more suitable security framework for cloud environments.
- Simplified IT infrastructure. SASE combines networking and security services into a single, integrated solution. This simplification reduces the complexity and costs of managing multiple vendors and products.
- Enhanced security posture. SASE offers improved security measures, including zero trust network access, which assumes no user or device is trusted by default. This approach strengthens companies' defense against cyber threats.
- Better user experience. By optimizing the route that traffic takes to the cloud, SASE can improve application performance. This leads to a better user experience for employees, which is important for productivity.
Key SASE requirements
Secure Access Service Edge (SASE) combines networking utilities with IT security tools in a unified, cloud-based service. This enables organizations to use a single platform to integrate and streamline cybersecurity management processes. Instead of jumping through multiple IT products for niche functionalities, SASE encompasses multiple solutions under one roof.
Here’s what a SASE service should integrate:
- Software-defined wide area network (SD-WAN) is a software-based approach to enterprise network connectivity. It acts as a networking extension over the internet, creating smart hybrid WAN hubs. Incorporating business VPN, wireless access, and broadband internet capabilities, SD-WAN is an efficient networking management solution enabled by the cloud. Routing traffic in the most efficient way possible to ensure high-performance speed and data integrity is possible. In addition, this eliminates the need for complex physical SD-WAN hubs.
- Zero Trust Network Access (ZTNA) is a technology that enables remote access that aligns with the Zero Trust model. Fundamental distrust of any connection inside or outside the organization is one of the key traits, enforcing strict authentication at every step. Unlike VPN, access is granted not at the network level but at the application level. This means no tunnels are established, and ZTNA acts as an intermediary granting access to an application hosted in a cloud. This separated network access from application access, and provided services remain hidden from the outside — only authenticated entities can access them.
- Firewall as a service (FWaaS) is a web traffic filtering tool delivered by cloud computing channels. Firewall functionality is delivered via the cloud, configuring firewall rules and deploying the service remotely and without any physical hardware. It may be a substitute or a supplement to traditional endpoint-based firewalls. Access data is always routed through the firewall to ensure the security policy requirement is upheld. The service itself is configurable via the provider’s management interface. Usually, some subscription model is used, but the price may vary depending on the required features and userbase size. However, the upside is that all maintenance and patch management falls on the provider’s responsibility.
- Next-generation firewall (NGFW) is a third-generation firewall technology using advanced detection tactics to stop sophisticated cyber attacks. It not only blocks specific ports but also examines the content of the data stream, looking for unusual behavior and malicious files. The system may also enforce security policies denying access to specific resources. It’s a significant improvement on the firewall product formula, greatly expanding its use cases. Integrating functionalities like antivirus and antispam filters, NGFW is a layer that protects the user’s endpoints before they get a chance to become infected. This type of firewall becomes an active decision-maker when allowing or denying traffic rather than a static ruleset.
- Secure web gateways (SWG) is a solution that protects connected devices from web threats. It can be used to enforce the company’s security policies for network traffic analysis and filtering. The gateway can be set up in the local network, delivered via the cloud, or in a hybrid approach. Unlike traditional firewalls, SWG can analyze the application level’s traffic and interfere if it detects some anomalies. SWGs can be administered via a web dashboard like the other SASE components.
- Cloud access security broker (CASB) is a service that secures cloud-hosted applications. It’s situated between the user and the cloud, monitoring incoming requests to the data center. This allows CASB to react to unwanted incoming traffic immediately or indicate reports of suspicious actions. CASB can greatly reduce the misuse of cloud services. In addition, CASB also makes it possible to create secure access requirements through user authentication and traffic encryption. The policies must be set up in advance, and then CASB will act as a policing mechanism to ensure the policies are followed.
Steps to successful SASE adoption
While it’s not imperative to begin adopting all SASE components simultaneously, the ultimate goal should be to have all five components present. It can be a lengthy and tedious process as it deals with replacing IT assets while they’re being used for day-to-day job functions. So, the bigger the organization, the longer it will take to implement SASE fully.
However, SASE is much easier to maintain and supervise than traditional methods. As many companies are already taking the first steps into the SASE world, here’s what could help you when implementing it in your company.
Step 1: Conduct an extensive audit
Your plan should start with an audit of your company’s IT security infrastructure. Analyze how users are validated, identify key risks, and incision what improvements should be made first. This will allow you to make informed choices on how to proceed with the SASE implementation plan. The main reasoning behind this transition shouldn’t change for the sake of change — SASE should be solving your specific business problems.
PRO TIP: Always ask questions and analyze. Correctly identifying problems sets the company on the right track to address various issues. In addition, clearly defining the desired outcomes will make evaluating the success of SASE adoption easier.
Step 2: Outline implementation plan
Once you’ve identified key business risks, have an action plan outlining each step. This will make SASE implementation a much clearer task for your technical team. It may also be beneficial to devise a roadmap indicating when you expect to achieve what steps. Having your plan from a time perspective will make it easier to set deadlines for when each step should be completed.
PRO TIP: Adequate assessment of deployment stages, goals, and objectives will be much easier if you keep widely used industry standards in mind.
Step 3: Analyze the market
While no provider has a SASE solution that includes all its components, it doesn’t mean that you necessarily need them all to ensure business IT security functions. Some cybersecurity areas in your organization will likely be worse off than others. Therefore, your provider should offer the best solutions for the specific areas that are the most relevant in your case.
It may also help to disassociate from known brands and marketing, as this rarely addresses your concerns. Also, don’t forget to check in with solution scaling capabilities fitting your company’s profile.
PRO TIP: No single provider can cover all SASE frameworks, so you should focus on the one that best fits your scaling needs.
Step 4: Start implementation in parts
Implementing SASE in parts can make the whole transition smoother. Not only will this limit the attrition on the IT department that will be implementing SASE, while in parallel working on the maintenance of the legacy systems. Segmenting the operations into smaller units will make them more easily manageable. In addition, this will help with the resources and personnel management. Organize the transition in sprints, which will make achieving your goals easier.
PRO TIP: Migration of used tools and SaaS applications will be easier when done in batches. You can also pre-define team roles to achieve maximum optimization.
Step 5: Troubleshoot and test
Don’t expect the whole process to go without any errors. SASE solutions must be thoroughly tested to avoid total breakdowns when deployed en masse. Otherwise, you’ll achieve the opposite effect, and troubleshooting will take up more time than the perceived benefits that the SASE brings. Ensure that your established processes don’t have any gaps or weaknesses that could backfire.
PRO TIP: Placing a dedicated team on the case can be very beneficial as you’ll have direct feedback and specialists to resolve potential bottlenecks.
Typical mistakes that can affect SASE adoption
While SASE adoption is still in its infancy, the businesses that were the first adopters were also the ones that figured everything out by trial and error. Here’s what you should avoid when implementing SASE.
Neglect separate component requirements
SASE, by definition, is a singularity of diverse networking and security components. Therefore, SASE implementation is impossible without these components. The biggest mistake would be to ignore each specific component’s requirement.
For this reason, it’s important to look at the current security infrastructure to check what prevents your company from adopting SASE. As it’s completely cloud-based, bandwidth requirements can be pretty high. However, SASE implementation may not be the best idea if your business suffers from frequent blackouts.
Change for the sake of change
SASE shouldn’t be regarded as a trend. Not to mention, businesses likely already have some security capabilities in place. You shouldn’t be throwing perfectly working cybersecurity tools just to start using the SASE alternative. This would be a waste of your resources without achieving anything substantial.
SASE adoption assessment questions
For most organizations, SASE adoption will mean turning to a third-party provider. This can get complicated quickly as, on the surface, all of them can look very similar. Finding out whether the provider matches the company's needs falls on you. The easiest method to determine which providers fit the bill will be by asking the following questions.
1. What is considered a successful SASE deployment?
The definition of successful deployment can greatly vary across service providers depending on the main reason you’re implementing SASE. The right provider should be able to provide detailed examples of successful deployment cases and help you outline key metrics for evaluation.
2. Does the provider have an edge in your needed use case?
SASE has a wide variety of applications. However, not all providers are equal regarding specific use cases. Doing your homework and prioritizing particular use cases will make it easier to filter out SASE providers. Asking direct questions about the needed functionalities and comparing them with the competitors is the best way to determine which provider fits your business case.
3. How was the cloud platform built?
Take time to learn as many details as possible about how the platform was built. These insights will help you better evaluate how the provider can ensure troubleshooting and support. There’s a big difference between providers that built their solution on the cloud from the start and those that only added virtualizations for cybersecurity services. If possible, you should always look for cloud-native providers as they prove more efficient.
4. What is your infrastructure’s network capacity?
An uninterrupted link to your employees' endpoints is one of the most important characteristics when choosing a SASE provider. If the provider can’t accommodate all your devices, your day-to-day operations may experience delays. Seamless data and application flow must be ensured for a good blend of security and efficiency.
5. What third-party integrations are supported?
If you already use third-party tools, you will likely not want to replace everything overnight. It’s not a bad idea to inquire whether your potential SASE provider can integrate monitoring or response tools that you’re already using. That way, you’re keeping the components you already rely on and integrating them into a unified setup.
6. What’s the solution’s scope?
While all provider’s marketing materials label them SASE solutions, there isn’t a single one that fully covers all SASE components. Therefore, you’ll need to find a way to figure out each provider’s unique definition of SASE. Your goal shouldn’t be to select a provider with the most capabilities but to find the one with just the right capabilities for your needs. Most of them will be teaming up with various third-party partners, so you should investigate how the service is constructed.
7. How many PoPs does your service have?
SASE systems rely on globally distributed points of presence (POPs) to route connections through the nearest gateways. This means that if you’re on the move, each time you connect, you’ll get optimal performance as you’re always connecting to the nearest one. However, different service providers have different amounts of POPs, which can mean that your performance can drop if the provider only has a few. This is something that should be discovered in advance.
8. How does the solution help ensure regulatory and administrative requirements?
Compliance is mandatory for organizations that handle sensitive data. SASE deployment can be a superb method to feed two birds with one scone: modernize your cybersecurity and stay compliant. Check beforehand whether the provider will help your organization in its pursuit of compliance. It’s never a bad idea to have several business goals in mind when looking into cybersecurity providers.
9. How are all endpoints handled?
Your SASE provider shouldn’t leave out endpoints from the equation. Endpoint security should always be considered regardless of what functionalities you’ve outlined as a priority. There are many methods to set up identity management solutions so that even policies like bringing your device would pose as little risk to your company as possible.
10. How can your service be managed?
The service management portal will be the principal tool when interacting with the service. You shouldn’t underestimate its convenience as the IT team will use it daily. Depending on its setup, you may also need certification or additional employee training. Remember this, as it will streamline its adoption once you start deployment.