Summary: Healthcare devices are targets for attacks that can disrupt care or expose data. Protect them with updates, strong access controls, and Zero Trust security.
As patient data becomes a prime target for data thieves, healthcare organizations are scrambling to counter numerous critical threats. Medical devices are now a cybersecurity frontier.
The medical devices we rely on to keep us healthy can fall victim to ransomware, identity theft, and DDoS botnets. Meanwhile, strict privacy regulations punish companies that don't take data security seriously.
Healthcare providers, device manufacturers, insurers, and third-party service providers are all part of the healthcare cybersecurity challenge. This article will explore how to secure medical devices and safeguard patient safety in an increasingly dangerous environment.
Key takeaways
Proactive approaches are vital when securing medical devices. Companies must assess risks,
monitor threats, and fix vulnerabilities before attacks occur.
Critical medical device risks include remote hacking, ransomware, data breaches, unpatched vulnerabilities,
insider threats, and botnet attacks.
Regulatory compliance is essential. Device manufacturers must meet FDA standards, while users should comply with HIPAA and GDPR. NIST and ISO frameworks provide a roadmap to compliance.
Device security best practices include inventorying devices, segmentation, vendor collaboration, monitoring threats, and applying regular updates.
Medical device security is evolving. Expect advances in AI and machine learning to detect threats while 5G delivers speed and reliability improvements. New technology also enables the deployment of
Zero Trust concepts to verify every device activity.
Why proactive cybersecurity is essential for patient safety
When we think about patient safety, medical competence, affordable care, and safe hospitals all come to mind. Cybersecurity risks aren't always a top priority until data breaches expose private information to malicious actors.
However, Protected Health Information (PHI) breaches cause serious harm. Data thieves can use confidential details to steal identities or blackmail individuals. Data tampering can falsify records and lead to improper treatments, while information about health conditions can influence the decisions of employers or insurers.
The bottom line is that health data should always be secure. This includes data from medical devices like heart rate trackers, diabetes monitors, and wearable technology. These devices gather confidential data about the patient's condition. They must also operate reliably - without downtime caused by cyberattacks.
Protecting medical devices demands a proactive cybersecurity approach. Security teams must assess each security risk and fix vulnerabilities before cyberattacks occur. Reactive security is too late. Healthcare providers need robust medical device cybersecurity systems that anticipate threats.
Built-in security for life-saving tech
Ensure patient safety and device security—talk to our experts
The cybersecurity risks medical devices face
Many people are not familiar with medical device cybersecurity risks. Let's dive a bit deeper and explore how cyber criminals target consumer and professional healthcare devices.
Remote hacking
Many medical devices depend on network connectivity to transmit data, but these networks are not always secure. Hospital and home networks are vulnerable to remote hacking via unpatched software or weak passwords.
Criminals with unauthorized network access can theoretically control medical devices, adjusting dosages or pacemaker settings. That's a terrifying prospect for professionals and patients.
Ransomware attacks
Medical devices, like all devices connected to the external internet, are vulnerable to ransomware infections. A quick exploration of the top ransomware attacks in 2024 shows that the infection risk is severe and growing.
These attacks deploy malicious software which encrypts devices and prevents legitimate access. This can have dangerous care implications if ransomware affects heart rate monitors or scanning equipment, although criminals usually relent when targets make crypto payments.
However, even if healthcare organizations make payments they may lose the data held by medical devices. Ransomware is a triple threat: affecting financial health, compromising critical systems, and exposing patient data.
Data breaches
Ransomware is not the only data breach risk linked to medical device cybersecurity. Cyber attackers may target monitoring tools and apps, gaining access to medical histories and current treatment programs.
Information about treatment is extremely valuable in the wrong hands. Criminals use it to launch insurance fraud scams, craft targeted phishing attacks, and even extract blackmail payments.
Exploits due to unpatched vulnerabilities
Medical device manufacturers may not update firmware or apps to address cybersecurity risks. This is a common issue with IoT technology that opens the door to exploit attacks leveraging outdated software.
Even worse, manufacturers often use proprietary software that is hard to update independently. And they sometimes delay patches due to complexity issues and concerns about compromising device functionality.
Healthcare providers often neglect updates in medical device cybersecurity strategies. However, when a single unpatched scanner can act as a network gateway, updating devices should be a priority.
Insider threats
Accidental errors and malicious employee activity can also compromise medical device security. For example, disgruntled staffers could use external drives to install malware on hospital systems or steal patient data for illegal purposes.
Negligent activity is equally damaging. Staff may ignore security protocols by sharing passwords, failing to encrypt laptops, or misusing physical access controls.
Botnet activity
Botnets pool large numbers of connected devices for criminal activities. For instance, bad actors could install malware on medical devices and use their computing power to mine cryptocurrency.
Lax medical device security also exposes healthcare organizations to DDoS attacks where attackers flood medical networks with traffic. These attacks take devices offline, disrupt care, and compromise security systems, opening the way to secondary attacks.
Related articles

Joanna KrysińskaOct 10, 20249 min read

Agnė SrėbaliūtėAug 7, 202415 min read
Medical device cybersecurity: What the regulations say
Governments have reacted to the growth in cyber threats against medical devices, passing many regulations to enforce data security. Organizations in the health sector must understand relevant regulations and use them to design security strategies.
| | Key requirements or recommendations |
|---|
| All medical device manufacturers in the US | Monitoring risks;
Ensuring device security and providing post-market patches |
|---|
| All healthcare providers in the US | Protection of patient data confidentiality, integrity, and availability |
|---|
| All medical device companies operating in the EU | Protection of patient data and the need for a patient’s consent before using their data on medical devices |
|---|
| | Suggests how to secure networks, manage cloud data risks, and ensure security measures meet healthcare professionals’ needs. |
|---|
| Best practice for managing IT risks in medical devices
In the U.S., it's not a legal requirement In the EU, it aligns with MDR (Medical Device Regulation) requirements for risk management but is not explicitly required | It emphasizes risk management in medical IT networks to balance cybersecurity and patient data safety |
|---|
FDA regulations for medical device manufacturers
Firstly, medical device manufacturers must comply with Food and Drug Administration (FDA) guidelines. The FDA regulates the safety of anything that "diagnoses, cures, mitigates, treats, or prevents [a] disease or condition." In practice, FDA rules cover most medical devices.
Specifically, section 524B of the Federal Food, Drug, and Cosmetic Act requires medical device manufacturers to:
Create a plan to monitor and address medical device security risks (including exploits)
Ensure devices are "cybersecure" and provide post-market patches as appropriate
Submit a software bill of materials to the FDA detailing firmware and other components of medical device software
HIPAA and GDPR rules on safeguarding patient data
The Health Insurance Portability and Accountability Act (HIPAA) and the EU's General Data Protection Regulation (GDPR) regulate how medical devices protect patient data.
HIPAA requires healthcare providers to protect data confidentiality, integrity, and availability. The law also suggests encrypting data on medical devices, controls on accessing patient data, and comprehensive audit logs.
GDPR protects patient privacy. It requires organizations to gain consent before using medical devices to gather data and the anonymization of patient data. Like HIPAA, GDPR's "privacy-by-design" model encourages encryption and data minimization (only collecting essential medical data).
Both HIPAA and GDPR levy significant penalties for data breaches. Device security is a core aspect of both frameworks.
For instance, the University of Rochester Medical Center received a $3 million fine from the Department of Health and Human Services for losing a hard drive containing protected health data. In 2015, the Lahey Hospital and Medical Center was penalized for failing to secure a CT scanner workstation.
NIST cybersecurity frameworks
The National Institute of Science and Technology (NIST) offers cybersecurity guidelines for device manufacturers and users. While not enforceable by law, NIST's cybersecurity framework explains how to:
Create secure and interoperable medical networks
Manage cybersecurity risks when storing medical data in the cloud
Apply quality control procedures in device manufacturing
Secure network communications within health settings
Ensure security measures meet the needs of healthcare professionals
ISO/IEC 80001: Managing device security risks
Similarly, ISO/IEC 80001 sets out an IT risk management framework for medical devices and is a valuable complement to NIST documents.
ISO recommends collaboration between device vendors and end users to assess and mitigate security risks. Device users should assess cybersecurity risks before deploying devices and apply continuous risk assessment throughout the product lifecycle. The risk management process includes proactively identifying and mitigating emerging data security threats.
The ISO approach works well because it balances cybersecurity standards with patient safety and performance. Systems should meet user needs while securing data and complying with relevant regulations.
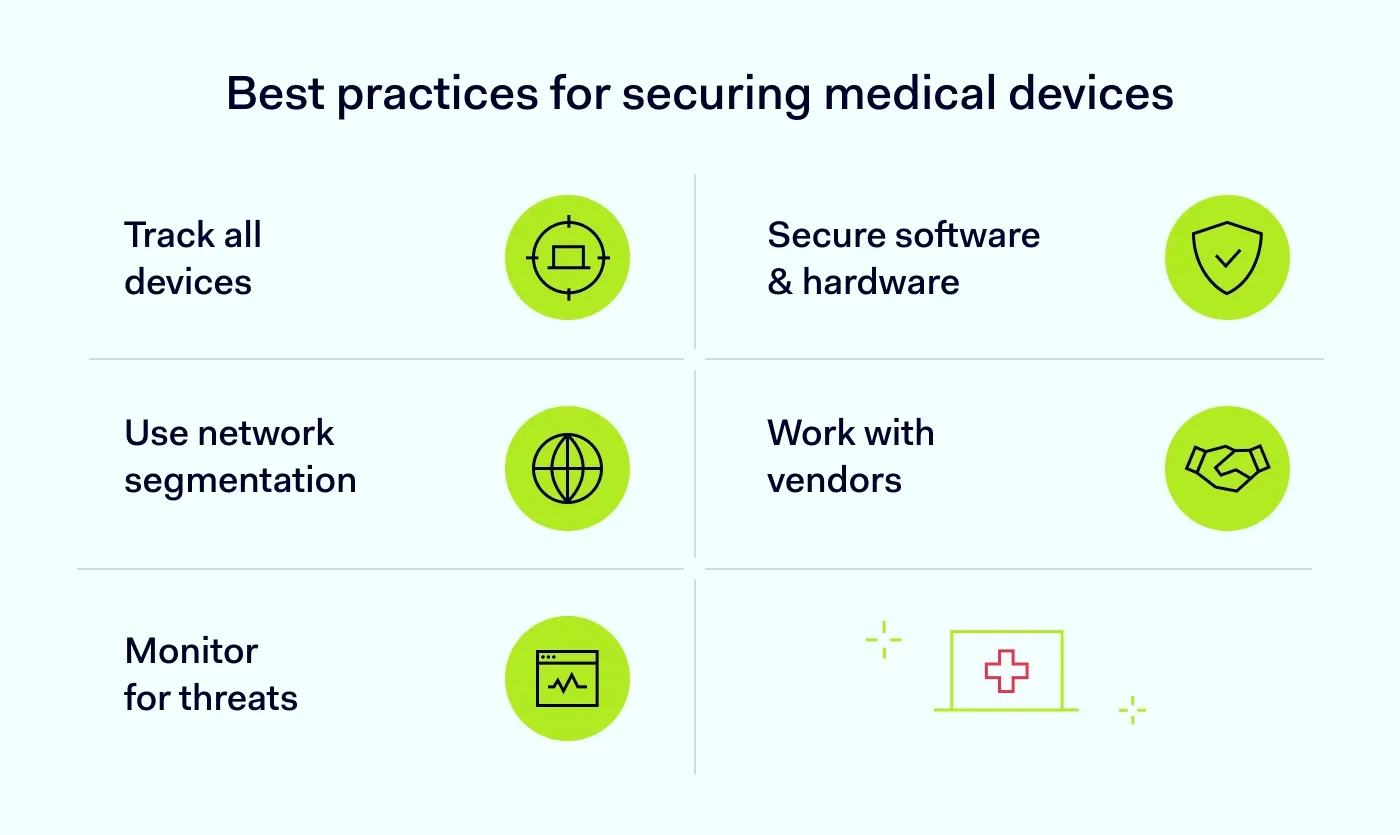
Best practices for securing medical devices
The size of compliance penalties and the reputational harm caused by data breaches make cybersecurity solutions essential. But how should you secure medical devices against cybersecurity threats?
Security solutions vary between medical contexts. However, here are some general best practices for cybersecurity in medical devices:
Understand your device landscape
The number of medical devices used by a healthcare provider can rapidly grow, especially when patients take monitoring devices home. Every device is a potential endpoint and security risk. Each device needs security protection.
Start by creating a comprehensive device inventory. Create processes to update and audit the inventory, bringing all devices under your security umbrella.
Inventory software and hardware
Medical devices must be physically secure, with measures to prevent theft and unauthorized access. However, cybersecurity measures must also secure device firmware. Log current software versions and use automated tools to update medical device software as needed.
Check for end-of-life devices as well. Medical devices become obsolete as new technology appears. Older versions often create security risks and require prompt replacement.
Carry out a comprehensive risk assessment
When you have an accurate inventory, it’s vital to assess the risks posed by cyber threats. In this context, third-party risk assessment makes sense.
Cybersecurity experts with medical device experience understand the threats faced by healthcare organizations, how to prioritize risks, and suitable mitigation options.
Secure sensitive assets with network segmentation
Segmentation creates barriers between network assets. Placing sensitive data within protected segments ensures that attackers cannot access patient records if they gain access to devices.
Additionally, access controls and multi-factor authentication should protect patient information. Users should not be able to access protected information with just a username and password combination.
Work closely with vendors to understand device security
When sourcing medical devices, ask vendors to disclose security features and potential vulnerabilities. Consult vendors to execute a risk assessment for new devices and request a software bill of materials. This assists IT teams when securing device software and makes it easier to manage updates.
Monitor devices and detect threats
Apply intrusion detection systems (IDS) across all medical devices. Deploy continuous monitoring to detect malware or malicious user activity, and feed security alerts into a streamlined incident response plan.
The future of medical device cybersecurity
Medical device security is a dynamic field. Technology is evolving rapidly as medical internet-of-things (MIoT) devices proliferate, providing new ways to detect and counter cyber threats.
For instance, AI and machine learning can analyze network activity to track anomalies and identify attacks at an early stage. Speed increases offered by 5G connectivity supplement AI, enabling real-time activity tracking and reliable data transmission.
Our models for thinking about medical device security are also changing. Forward-thinking healthcare organizations now focus on Zero Trust concepts. Devices request verification for each user action and limit user capabilities according to least-privilege principles.
AI, 5G, and Zero Trust approaches are part of tomorrow's cybersecurity toolkit. These technologies also reflect a trend toward enhanced collaboration between vendors, users, and regulators.
Work with NordLayer to secure your medical devices
Companies benefit from cloud-connected medical devices to learn about patients and deliver personalized treatment. But, as we've seen, medical devices bring security risks. Healthcare cybersecurity solutions are critical.
NordLayer can help you secure devices and serve patients securely and efficiently. Prevent unauthorized access with Identity and Access Management solutions and transfer data safely via Secure Remote Access. Conceal data in transit from attackers via AES 256 or ChaCha20 encryption, monitor 2FA adoption, and Share Gateway access in a centralized Control Panel dashboard.
Balance medical technology, ease of use, and cybersecurity. Contact the NordLayer team and solve your medical device security worries.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she has dedicated her life to simplifying complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.