Smurf attacks can devastate network performance and cripple websites for days. In these DDoS attacks, extended botnets, broadcast domains, and spoofed packets direct a flood of an overwhelming number of echo requests against targeted networks.
This article explains how smurf attacks work, the different types, and best practices to protect your network.
Smurf attack meaning
A Smurf attack is a form of distributed denial of service (DDoS) attack that uses the Internet Control Message Protocol (ICMP) to generate a flood of malicious traffic. Threat actors direct attack traffic via IP broadcast addressing, which converts small flows of data into overwhelming DDoS attacks.
How does a Smurf attack work?
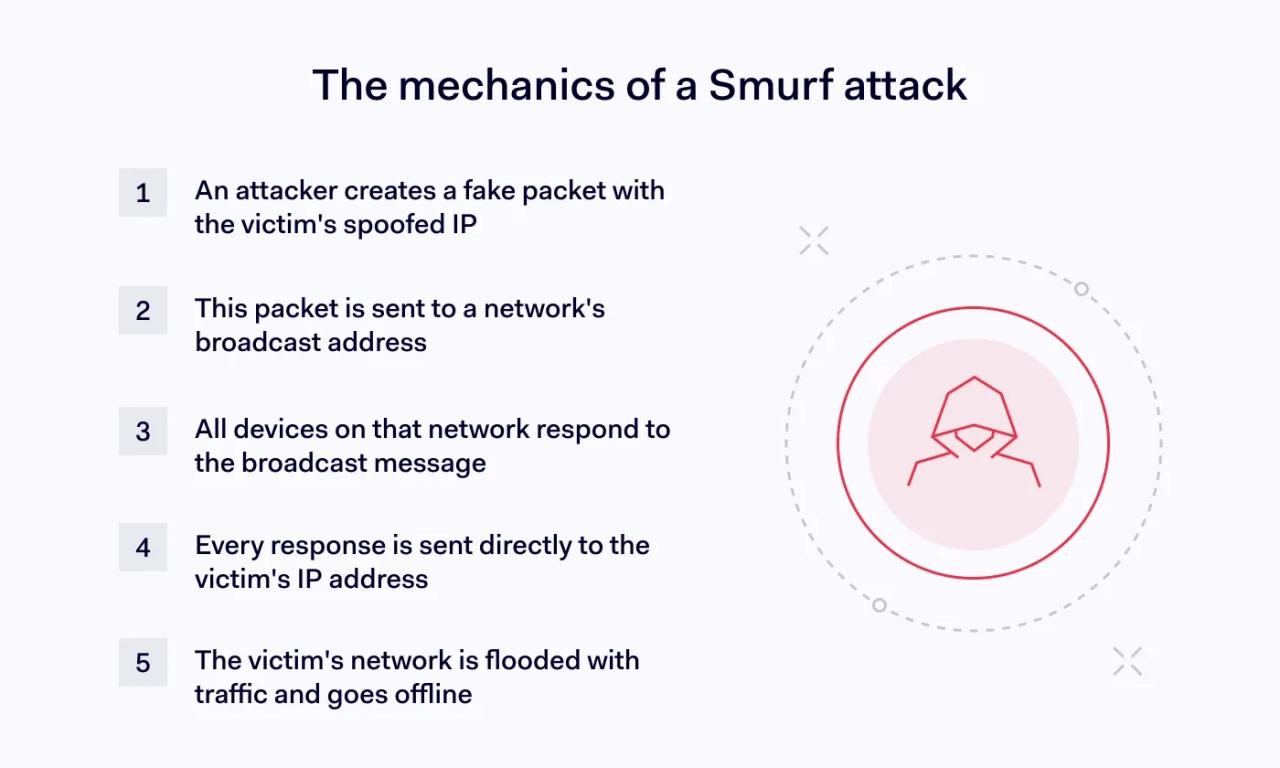
A smurf DDoS attack has three components: the attacker, an amplifier (or reflector) network, and the victim. Here's how the process usually works:
- Preparation. Attackers create a fake ICMP echo request (ping) packet by using IP address spoofing. Attackers use spoofing tools to fake the victim's IP address in the packet header. This creates an "echo" arrangement that reflects traffic to recipients.
- Transmission. Threat actors send spoofed ICMP packets to the broadcast address of a compromised network. Broadcast addresses allow systems to communicate with all devices on a connected subnet simultaneously.
- Amplification. Every device on a connected subnet receives traffic from the broadcast address. Devices respond with an ICMP echo reply. Normally, this is not a problem. However, in smurf attacks, every device on the same subnet responds simultaneously.
- Flooding.Thanks to packet spoofing at the preparation stage, ICMP echo requests pass from all connected devices to the victim's IP address. A single spoofed ping request can trigger multiple responses, overwhelming the victim's network.
- Attack completion. The smurf DDoS attack succeeds when the traffic flood results in a denial of service. Victims see their bandwidth saturated with malicious traffic. This blocks legitimate traffic, compromising performance and - eventually - taking systems offline.
Smurf attacks gained their name because the first known examples involved a script called "smurf.c". The script gained its name from the cartoon series, where a community of relatively powerless characters regularly wins by working together. However, in smurf attacks, bots cooperate for malicious ends.
You may also encounter references to fraggle attacks. Fraggle attacks are very similar to smurf attacks. Both are network-level amplification attacks. Smurf attacks exploit ICMP packets, while fraggle attacks leverage UDP packets and send spoofed packets to specific network ports.
Types of Smurf attacks
Smurf attacks tend to follow the playbook above, but we can helpfully divide them into basic and advanced tiers.
Basic smurf attacks direct an unlimited flood of ICMP echo requests at the victim's device or network. This classic variant relies on spoofing and IP broadcast addressing. It uses a single network segment to generate traffic. The force of the attack depends on the size of the broadcasting subnet.
Advanced smurf attacks are potentially more powerful and harder to neutralize. Advanced attacks begin as normal. However, they use distributed botnets to exploit a far larger pool of traffic sources.
Advanced attacks also use other forms of amplification. For example, attackers leverage misconfigured DNS and NTP servers and CLDAP reflectors. This method sends tiny echo requests from large networks of bots. While each request is small, the result is a massive traffic flow that far exceeds the capabilities of traditional smurf attack vectors.
Sophisticated botnets can enable threat actors to target multiple victims with smurf attacks, affecting web applications and corporate websites.
How to prevent a Smurf attack
The effects of smurf attacks range from mild annoyance to severe performance issues, downtime, and system failure. Companies need to implement effective prevention measures to avoid these outcomes. Best practices to block smurf attacks include:
- Disable IP-directed broadcast forwarding and echo replies on critical routers. Administrators should prevent the network from being used as an amplifier and configure border routers to prevent automatic echo replies to IP-directed broadcasts. This prevents attackers from using your network resources as amplifiers. Most routers apply this by default, but security teams should verify each device for security.
- Use ingress and egress filtering. Ingress filtering interdicts data packets entering the network. Filters detect incoming packets with IP addresses linked to local devices. Egress filtering works in tandem, blocking outgoing packets with source IP addresses outside your local network. This cuts the risk of threat actors integrating local devices into malicious botnets.
- Configure firewalls to block ICMP requests. Firewalls can block or drop ICMP echo requests sent to the broadcast address, acting as a last line of defense.
- Segment networks to limit domain sizes. DDoS Smurf attacks exploit large subnets to amplify traffic floods. Use network segmentation to create logically grouped network sections and limit the scope of broadcast domains.
- Implement intrusion detection systems (IDS). IDS solutions help prevent smurf attacks by monitoring network traffic. Look for spikes in incoming/outgoing traffic or traffic originating from known malicious sources.
The recommendations above help to prevent smurf attacks. However, they are less useful when mitigating ongoing denial-of-service incidents.
To handle DDoS attacks, companies should implement DDoS mitigation tools and inform their ISPs. Security teams should also activate contingency measures, such as blocking all incoming ICMP packets until DDoS attacks are resolved.
Take measures to prevent and mitigate smurf attacks
Basic smurf attacks use packet spoofing and IP address broadcasting to flood target networks. Emerging variants employ increasingly sophisticated amplification and transmission methods. These techniques increase the size and power of smurf attack traffic - posing a critical risk to network assets.
Take action to prevent a smurf DDoS attack by configuring routers, filtering traffic, and using IDS solutions. Integrate DDoS attacks into your incident response plans, and remain vigilant as threat actors seek ways to expand botnets and amplify their attacks.
