In cybersecurity, detecting attacks early is always better than waiting for ransomware attacks or data breaches. Indicators of compromise (IOCs) provide evidence of attacks, enabling companies to contain threats and fix vulnerabilities before the worst happens.
This article introduces IOCs. We will explore types and examples of IOCs, how they differ from indicators of attack (IOAs), and best practices for using IOCs to safeguard critical assets.
Indicators of compromise (IOCs) definition
Indicators of compromise (IOCs) are items of forensic evidence that indicate when a system has been compromised. Security teams use indicators of compromise to detect and mitigate previously unknown data breach attacks, malware infections, or insider threats.
IOCs are collected after network security breaches, when attacks are already underway. They allow containment and threat mitigation, but are generally reactive tools. Security teams must combine IOCs with threat intelligence and behavioral monitoring to proactively neutralize threats.
Why are indicators of compromise important?
Indicators of compromise are important because they enable security teams to respond to ongoing cyberattacks.
Monitoring IOCs allows companies to rapidly identify malware infections, endpoint breaches, and malicious user behavior. This facilitates prompt incident response processes and limits the damage caused by active cyber threats.
We also use indicators of compromise to test and refine security measures. For example, network security teams use IOCs to test heuristic threat detection systems. IOCs also verify that sandboxing tools effectively isolate compromised assets.
IOCs are also important in building institutional cybersecurity knowledge. IOCs enable analysts to understand attack techniques, including how attackers could move laterally within network environments. When combined with threat intelligence and indicators of attack (IOAs), this knowledge helps detect and defeat advanced threats.
Indicators of compromise (IOCs) vs indicators of attack (IOAs)
Understanding the differences between indicators of compromise and indicators of attack is critically important. IOCs and IOAs play different roles in healthy cybersecurity systems, but they are far from identical.
Indicators of compromise (IOCs) are reactive forensic tools. Analysts gather IOCs to detect ongoing or historical security threats. This means that IOCs are useful when responding to incidents or assessing the root cause of cyberattacks. However, detecting IOCs does not prevent breaches.
Indicators of attack (IOAs) are proactive. Security teams collect data from network traffic in real-time. Systems scan for deviations from normal user behavior, signatures of malicious software, or suspicious activities, including unauthorized code execution or data transfers.
Advanced threat detection software correlates IOAs to detect multi-level attacks before they breach network defenses and steal data or damage assets.
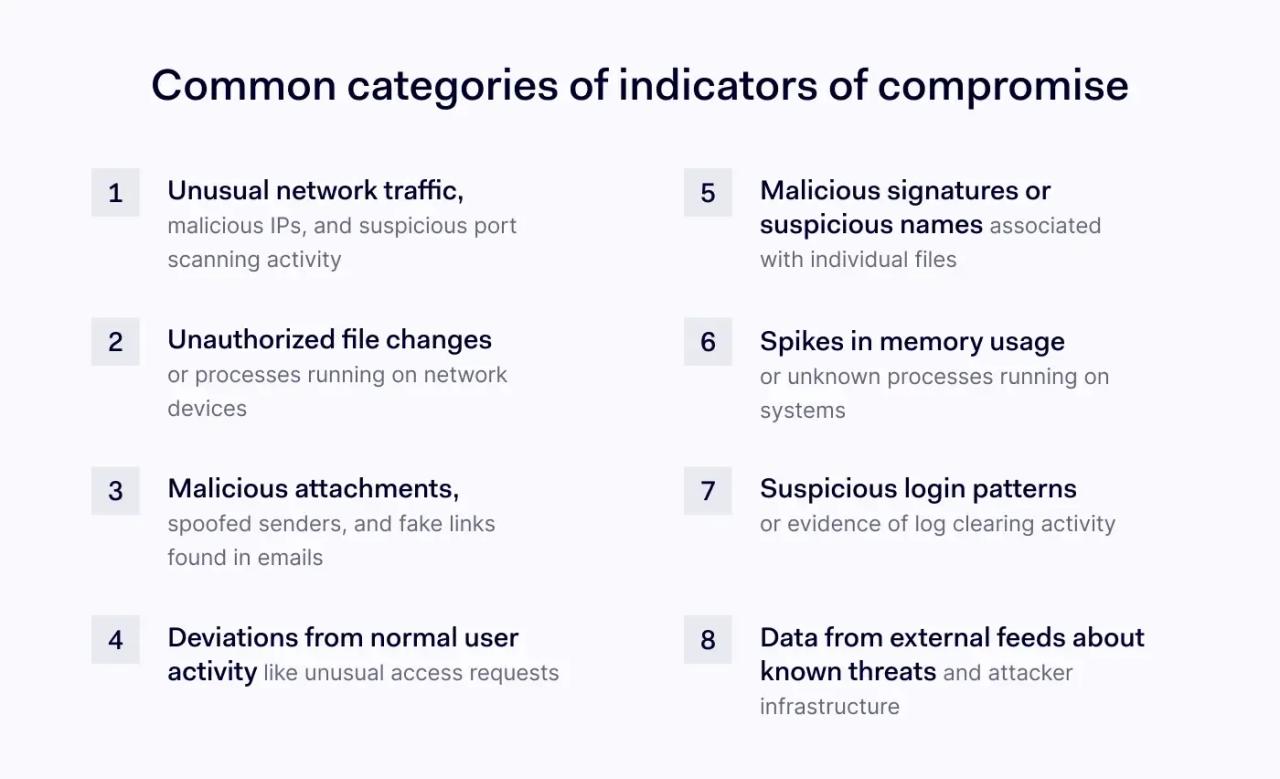
Types of indicators of compromise
Forensic analysts collect many types of indicators of compromise when diagnosing security incidents. Common variants of IOCs include:
- Network-based IOCs: These indicators of compromise arise from network traffic analysis. For example, security tools scan outbound traffic for evidence of data exfiltration. They look for the use of malicious IP addresses, links to flagged website domains, port scanning, or DNS data that indicates cyber-squatting attacks.
- Host-based IOCs: These IOCs relate to network devices and applications. For instance, security teams check for unauthorized file deletions, transfers, or processes running on connected devices. They use threat intelligence to scan for known malware hashes. And tools look for suspicious registry changes that could denote rootkit attacks.
- E-mail IOCs: Indicators of compromise also relate to employee communications. Security tools monitor emails for IP addresses, spoofed sender addresses, malicious attachments, and fake websites. They use IOCs to detect phishing campaigns, often connecting multiple email inboxes to establish the scope of attacks.
- Behavioral IOCs: Advanced security tools scan for indicators of compromise linked to user activities. For example, tools may detect unauthorized privilege requests on a user account or repeated password login failures. They look for unusual lateral movement within the network and access requests for resources that lie outside the user's standard permissions.
- File-based IOCs: Scanning solutions gather information about security threats linked to individual files or applications. For instance, tools look for files contaminated with malware signatures and flag suspicious file names or extensions. They also check DLLs for evidence of malicious side-loading attacks.
- Memory-based IOCs: This class of IOCs relates to system performance and processing functions. Tools look for unusual memory consumption spikes that could indicate denial-of-service attacks. They flag unknown processes and evidence of code injection attacks.
- Log-based IOCs: Security tools scan network traffic logs to detect the footprints of attackers. For example, security software checks login attempts for evidence of brute force attacks. They also look for log clearing to delete evidence of attacks, and track login locations and times for unusual patterns.
- IOCs from threat intelligence: Indicators of compromise can also be sourced externally via global threat intel feeds. For example, companies leverage information about known command and control servers when analyzing data breach attacks.
How can organizations identify IOCs?
Organizations can gather a vast array of forensic evidence to diagnose security threats. But how does this work in practice? Security teams use a range of tools to detect and correlate IOCs, including:
- Endpoint detection and response (EDR): Gathers data at network endpoints, including employee laptops, workstations, smartphones, web servers, and IoT devices.
- Sandboxing and malware analysis: Detects active malware threats and quarantines affected assets with sandboxing techniques. This enables secure analysis of IOCs.
- Security information and event management (SIEM): Generates detailed security logs and applies pre-defined rules to detect and mitigate incidents.
- Network traffic analysis (NTA): Analyzes network traffic to discover suspicious patterns and generate alerts.
- Threat intelligence platforms: Aggregate global intelligence about cyber threats and deliver customized feeds to clients.
- Open source intelligence: Security analysts may also draw on OSINT databases to detect fake websites and malicious IP addresses.
- Deception tools: These tools seek to deceive attackers by creating honeypots and decoys. Deception may expose lateral movement techniques and uncover advanced threats.
Companies generally employ a portfolio of tools to detect and analyze indicators of compromise. Security architects take a multi-layered approach to cover as many bases as possible, without generating needless complexity and false positives.
Examples of indicators of compromise
Indicators of compromise (IOCs) have many use cases in managing and mitigating security incidents. The evidence types listed earlier enable analysts to focus on active attacks and limit their extent before data breaches occur. Here are some ways to do so.
- Tracking inbound and outbound traffic: Monitor traffic for sensitive data, unusual traffic volumes, or port usage. Note unknown sources or destinations. Leverage threat intelligence to identify known C2 servers and attack techniques.
- Time or geolocation factors: Check for new login locations or times that depart from user baselines. Look for unusual VPN connections or links to new cloud services. Flag logins from countries or regions where the business is not active.
- Suspicious login attempts: Employ SIEM tools to record failed login attempts, password requests, and the use of multiple user IDs. Track repeated requests from the same IP address, and link logins to IOCs relating to phishing emails.
- Unauthorized or unusual system changes: Track registry changes, focusing on the most sensitive registry keys and critical system files. Compare system changes with regularly updated baselines.
- Detecting unusual file behavior: Look for file bundles whose locations lack a proper business justification. Use file integrity monitoring tools to detect unusual archived files that may indicate the presence of malware. Document file creation processes with SIEM. Use tracking tools to detect high-volume compression by privileged accounts.
How to use indicators of compromise in cybersecurity
IOCs are powerful forensic tools. However, organizations must gather and deploy indicators of compromise strategically to achieve their security goals. Here are some best practices to follow when using IOCs in incident response processes:
Integrate IOCs into your incident response plans
When security tools detect IOCs, incident response plans use them productively. Robust response plans plot the next steps, including gathering additional indicators of compromise to enrich alert data and automating mitigation actions to contain threats.
Develop a consistent incident response plan that maps the process from initial detection to analysis, mitigation, and post-incident audits. Define roles and responsibilities, timescales, and metrics used to determine whether the incident has been contained.
Create secure environments to analyze incidents
Immediately isolate compromised assets from the wider network to prevent threat escalation and enable measured, secure responses.
Use scanning tools to map contaminated devices. Establish the scope of ongoing attacks and apply sandboxing techniques to quarantine affected devices. This creates a secure environment for analyzing data integrity, user activity, and issues like malware infections.
Use IOCs to analyze threats in forensic detail
The critical benefit of using indicators of compromise is their ability to dive deep into security incidents and cover every angle. Use the full spectrum of IOCs when analyzing threats.
Determine the identity and source of the attack, leverage threat intelligence platforms to establish their goals, and use every available IOC to determine the severity of each alert. Log exposed databases, compromised accounts, and damage to network resources.
Verify mitigation with IOCs
IOCs play a critical role when eliminating cyber threats. Use indicators of compromise to verify the remediation of data exfiltration, malware infections, account hijacks, and other indications of attacks.
IOCs also enable comprehensive documentation of mitigation measures. Use this information to supplement compliance reporting and breach notifications if necessary. Leverage IOCs in routine security audits to test systems and improve your security posture.
Analyze cyber-attacks forensically with IOCs
Examples of indicators of compromise (IOCs) include data transfers, user account changes, registry edits, and malware signatures. These data types enable security teams to investigate ongoing and historical cyberattacks in forensic detail. Used strategically, IOCs help mitigate and contain attacks while preventing future security incidents.
However, security teams should not use IOCs in isolation. Indicators of compromise are reactive. They do not address threats before they strike or at an early stage. Assess IOCs in combination with indicators of attack to ensure comprehensive cybersecurity.
