In the cybersecurity battle zone, the cyber kill chain provides a strategic map for understanding and countering adversary actions. First formulated by military planners, the kill chain model breaks down attacks into eight stages. This allows targets to move from detection to active threat prevention and attack disruption. This article introduces the eight stages of the cyber kill chain model, before offering accessible best practices to implement the cyber kill chain in your security operations.
What is the cyber kill chain in cybersecurity?
The cyber kill chain is a threat management framework that explains how to identify and eliminate adversaries. The kill chain framework adapts military concepts, providing a series of steps found in common cyber-attacks. The chain generally includes eight steps, from reconnaissance to achieving attack objectives.
Each stage presents opportunities to detect, analyze, and remove active threats. In particular, the kill chain model helps counter advanced threats and complex attacks involving deep planning and multiple attack vectors.
Stages of the cyber kill chain
The cyber kill chain was originally devised by Lockheed Martin in 2011. The eight-stage framework remains relevant and relates to most contemporary cyber-attacks. Since 2011, experts have added an eighth stage: monetization. Let's explore the different stages and explain how they fit into a coherent attack chain model.
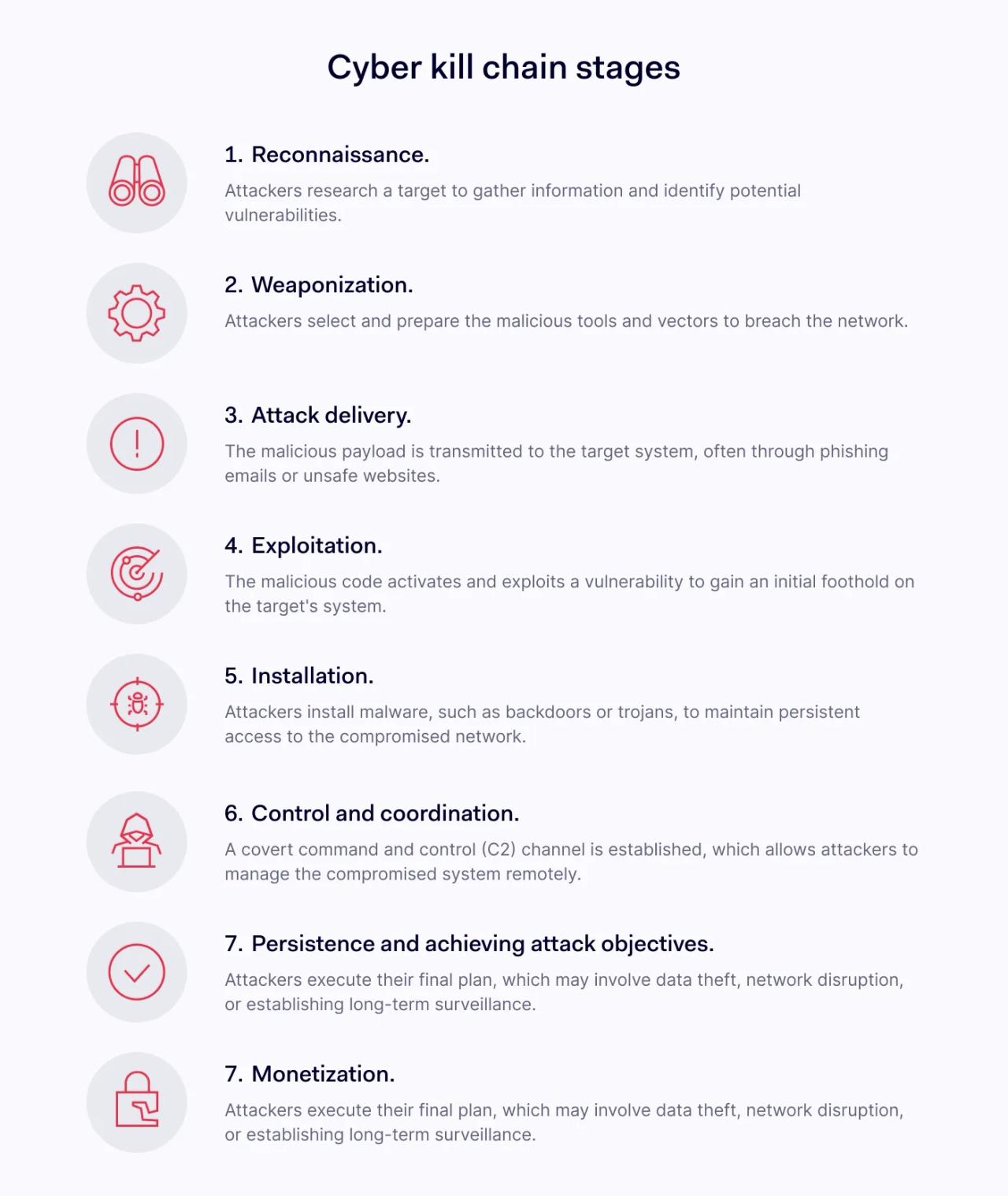
1. Reconnaissance
The cyber kill chain begins before attackers strike as threat actors research their targets. Attackers take weeks or months to gather information about targets for use during the attack.
For example, social engineering attacks rely on extensive use of open-source intelligence. Attackers monitor social media and websites to profile targets.
Alternatively, criminals may explore the attack surface to detect weak points. Attackers use WHOIS lookups, packet sniffers, network mapping bots, ping commands, and port scanners to map target networks. Reconnaissance enables attackers to identify poorly-defended devices and discover network access points.
Attackers may harvest login credentials via phishing techniques or purchase stolen credentials from third-party brokers. They may also scan cloud deployments for unsecured assets or endpoints. The goal is to gather any data that assists their preferred attack technique.
2. Weaponization
The second stage in the cyber kill chain involves selecting attack vectors to breach networks and achieve attack objectives. Simple attacks use a single vector, although sophisticated actors employ multiple techniques.
Common attack vectors include:
- Credential theft and access escalation
- Phishing
- Man-in-the-Middle attacks (MitM)
- Ransomware
- Trojans and worms
- SQL injection
- Remote access compromises
- Denial-of-Service (DoS) attacks
- Misconfiguration issues
- Insider threats
For instance, a cyber collective may weaponize user profiles to create convincing phishing emails. The same group embeds malware within email attachments. This malware deploys ransomware on targeted devices and surveillance agents to move within the victim's network. Attackers may also use backdoors and concealment techniques to extend their access and achieve their goals.
Attackers choose their vectors strategically. Groups consider the best tools and tactics to achieve their objectives. They assess the cost and complexity of techniques to determine which methods deliver the highest return on investment (ROI).
3. Attack delivery
In the third stage of the cyber kill chain model, malicious actors deliver weaponized payloads and launch attacks.
Threat actors typically activate scripts or malware to execute their chosen attack vectors. Victims often unwittingly activate the delivery phases by clicking unsafe email attachments or providing credentials to fake portals, or receiving drive-by downloads from unsafe websites.
Malware could act immediately, wait for trigger events, or activate after a certain period of time. Attackers may strike once, extract information, then leave. Or they may create backdoors for prolonged data exfiltration and surveillance.
The delivery phase presents opportunities for security teams. For instance, organizations can filter emails, use intrusion and endpoint detection systems, or block malicious web content.
4. Exploitation
At this stage of the kill chain framework, attackers execute malicious code and facilitate further activities. Obfuscation often accompanies exploitation, concealing malware and data extraction tools from network security measures.
The exploitation stage enables attackers to execute their plans, setting the stage for network damage and data extraction.
5. Installation
Attackers now secure their presence and gain maximum freedom to move laterally within targeted networks. They also seek ways to extend their activity and revisit compromised networks during future attacks. This amplifies the scope of attacks from basic network breaches to more serious cyber incidents.
To achieve their aims, attackers install backdoors and remote access trojans (RATs) via rootkits and exposed user credentials. With backdoors in place, attackers have free access to target systems. They can monitor network traffic, harvest credentials, and explore network assets via lateral movement.
6. Control and coordination
The sixth stage of the cyber kill chain model is also known as the Command and Control (C2) stage. At this stage, attackers establish a covert communication channel with the compromised system**.**
Attackers use a range of tools to seize control, including ransomware, encryption, spyware, and network monitoring bots. They implant C2 malware, which enables remote control of compromised devices.
C2 modules establish a position of privilege. Criminals can now send instructions, seek high-value targets for data exfiltration, and transfer data to secure remote servers for sale or use in future attacks.
At the same time, techniques such as protocol blending and domain generation algorithms (DGAs) obfuscate malicious traffic. Security teams struggle to detect and mitigate harmful activities and must concentrate their attention on disrupting the C2 connection.
7. Persistence and achieving attack objectives
The cyber kill chain continues in two ways: attackers execute their chosen actions and achieve their objectives, or they establish a persistent presence, extracting data over the long term.
Many things can happen at this stage. Attackers can launch Distributed Denial-of-Service (DDoS) attacks that cripple network resources. They can execute ransomware agents that encrypt data until victims make ransom payments. Or they may covertly extract data for monetary gain.
Advanced Persistent Threats (APTs) operate in the background for months or years. APTs monitor network traffic for evidence of new vulnerabilities, exposed user credentials, or sensitive data (such as intellectual property or strategic documents).
8. Monetization
The eighth stage in the cyber kill chain does not apply to all attacks. However, as data theft becomes more financially rewarding, monetization is becoming an integral element of the chain.
Attackers seek to convert stolen data or privileged access into financial gain. Cryptocurrency payments often follow successful ransomware attacks, while collectives routinely sell harvested credentials and customer data on dark web marketplaces.
How does the cyber kill chain affect cybersecurity?
The cyber kill chain model is a powerful tool for understanding and mitigating cyber-attacks. The kill chain helps security teams understand how attacks work and how to implement prevention measures. Security teams can also use the kill chain model to proactively identify threats early in the attack lifecycle and intervene effectively.
For instance, threat intelligence platforms help security teams detect stolen credentials or chatter about upcoming attacks. Companies can strengthen perimeter security measures to safeguard user identities and detect malicious activity. These measures potentially stop attacks at stages 1-3 of the cyber kill chain, before execution becomes possible.
Early detection matters because attack risks rise lower down the chain. Removing APTs and breaking command and control relationships is technically demanding and may follow data extraction or network damage. The kill chain framework helps you find a security solution before damage occurs and remediation costs rise.
The cyber kill chain also assists the international cybersecurity community. Lockheed's eight-stage model provides a common framework for describing and documenting emerging attacks. Security experts can correlate indicators of attack with threat intelligence, enabling them to counter specific threats.
Note: The Lockheed cyber kill chain model first appeared in 2011. While the linear progression model fits many conventional attack playbooks, it may not effectively capture faster-burning or automated attacks. Companies should combine the kill chain framework with MITRE ATT&CK to cover critical threat types.
How to implement the cyber kill chain
The cyber kill chain provides a valuable description of cyber-attacks, but how can the framework reinforce security measures and prevent cyber-attacks? Here are some brief best practices to leverage the kill chain in your security operations.
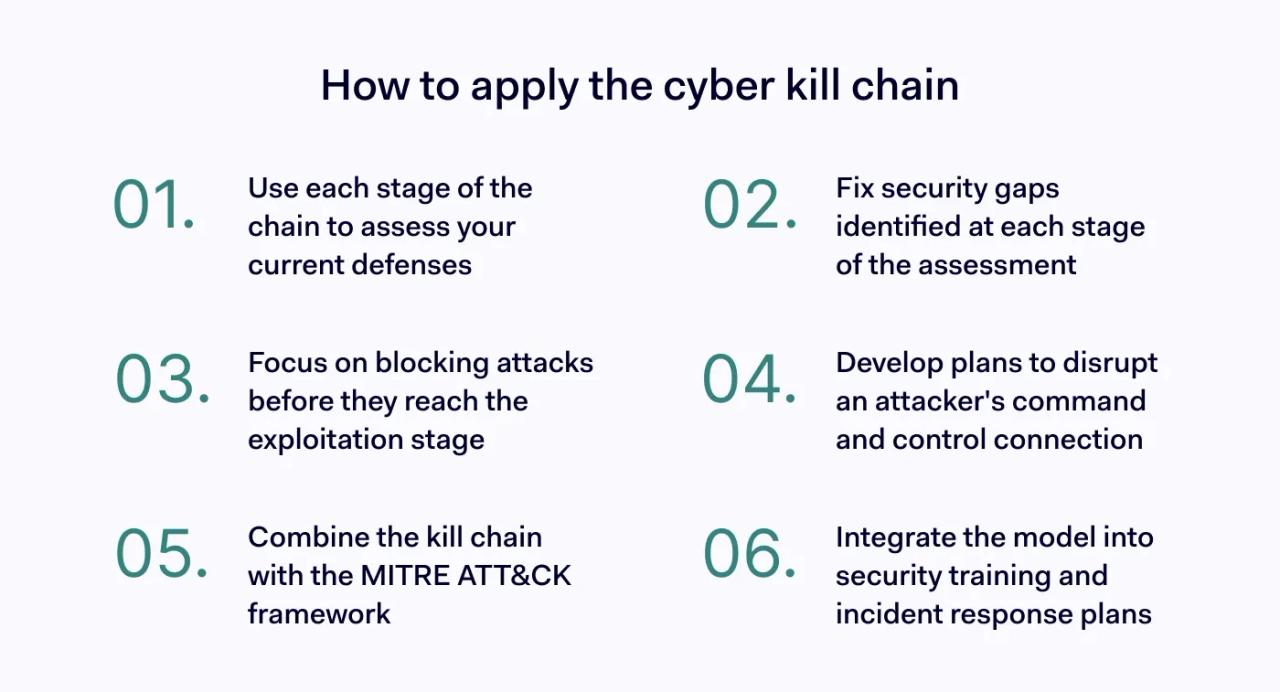
- Use each kill chain stage to assess your security: For example, does network segmentation block lateral movement and intelligence gathering (reconnaissance)? Do your EDR tools block malware installation or insecure endpoints (the installation and exploitation stages)?
- Fix security vulnerabilities at each kill chain stage: Use the outcome of the kill chain assessment to mitigate security gaps. For instance, applying patch management to reduce exploit risks or implementing email filtering to block phishing attacks.
- Block attacks before the exploitation phase: Stage 4 (exploitation) is a critical cybersecurity threshold. Try to block attacks before they reach that stage. Focus on anti-phishing measures, endpoint security, and detecting compromised user credentials.
- Workshop command and control disruption: Stage 6 (control) is a critical opportunity to disrupt attacks and limit damage. Implement plans to detect C&C agents and sever the connection with the attack servers. Use tools like egress filtering to sanitize outbound traffic until the connection is broken.
- Combine kill chain analysis with MITRE ATT&CK: The cyber kill chain helps you identify how attacks progress. MITRE ATT&CK provides in-depth guidance about how to mitigate threats at different kill chain stages. Using both frameworks together provides a more robust security solution.
- Integrate the kill chain into security training: The cyber kill chain is a great tool for simulating cyber-attacks. Use the model to test perimeter security, access controls, and cloud security measures. Similarly, use the chain as a template for incident response processes.
Model real-world attacks with the cyber kill chain
The cyber kill chain model provides an invaluable guide to cyber-attacks, outlining eight stages from reconnaissance to monetization. The kill chain helps security teams understand critical risks, model attacks, and identify threats before attackers steal sensitive data or damage network infrastructure.
