Without IP addresses, getting around the internet would be virtually impossible. These unique addresses identify every device that connects to the internet, allowing smooth routing worldwide.
This article explains what IP addresses are and how they work. We will examine different types of IP addresses, provide tips on identifying your own address, and outline some best practices to secure your IP address from malicious attackers.
IP address definition
An IP address or Internet Protocol address is a unique code assigned to each device connected to the Internet. Every router, computer, smartphone, or Internet of Things device with an internet connection must have an IP address to interact with other devices.
IP addresses use strings of numerical characters to identify devices. These unique codes enable devices to communicate with each other via a standard format-a critical component of online infrastructure.
How does an IP address work?
IP addresses are like a specialized language spoken only by internet-connected devices. Like other languages, Internet Protocol addresses use a set of standard rules to communicate information. This allows geographically distributed devices to "speak" with each other without the need for inefficient translation.
Devices do not store IP addresses locally. Instead, internet service providers (ISPs) assign Internet Protocol (IP) addresses when devices log in to their services. This IP address generally remains constant for static users in both homes and workplaces.
However, there are ways to change your IP address if desired. For example, resetting your modem router or making a specific request to your service provider. You can also anonymize your address via virtual private networks (VPNs).
Your IP address also changes depending on your location. For instance, your device will be assigned a fresh IP address if you use public wifi at hotels or airports. This is because the wifi network uses a different ISP, which assigns a new address for each user.
Note: IP addresses differ from MAC addresses. A MAC address is a local identifier, while an IP address is a unique universal identifier. MAC addresses help to transfer data packets within a local computer network at the data link layer. IP addresses make connections across the entire internet at the network layer.
IPv4 vs IPv6
IP addresses come in more than one format. In particular, it's important to understand the differences between IPv4 and IPv6.

IPv4
IPv4 is the older of the two IP address formats, having been active since 1981. This notation employs a 32-bit address space to identify devices. This means that IPv4 IP addresses consist of 32 binary numbers (or bits).
We divide these 32 bits into 8 "octets". Each octet corresponds to a more familiar decimal number. From the user's perspective, an IPv4 address features four separate numbers.
For example, the binary address "11001001.10001010.01010001.10000001" becomes "201.138.81.129."
This form of IP address notation provides room for 4.3 billion unique addresses. This seemed like a vast amount in the 1980s, but has since been challenged by the expansion of the internet.
IPv4 has other critical limitations. Importantly, IPv4 also used a 5-class system to structure network-host relationships (classes A, B, C, D, and E). This "classful" networking arrangement determines the number of devices a network can support by toggling the first octet of each address.
For example, the largest class (Class A) always starts with a binary 0. The remaining seven octets make up the available pool of IP addresses. Class A provides scope for 17 million hosts, but comes with a catch: the IPv4 system could only cater for 126 Class A networks in total.
IPv4 is also extremely inflexible. Networks often fall between different classes, resulting in a lack of capacity (and the need for additional infrastructure) or wasted addresses.
IPv6
IPv6 first appeared in draft form in 1995, but was formalized as the Internet Protocol Standard RFC 8200 in 2017. IPv6 emerged as an evolution of IPv4, providing scope for even more connected devices.
The updated IP address variation creates a 128-bit address space, with scope for 340 undecillion addresses (2 to the power 96). This represents a vast increase in the number of available addresses. With so many options, we are unlikely to exhaust these possibilities in the future.
IPv6 achieves this by employing eight 16-bit groups for each address. Instead of standard digits, IPv6 uses hexadecimal to display the address. For example, your address could look something like this: "1557:64be:f535:662e:fe7f:86a2:14dc:ce45."
IPv6 has other advantages over IPv4 aside from the number of possibilities. Headers now have a standard length (40 bytes), unlike variable IPv4 addresses. The new format also simplifies routing by including only essential fields.
There is also no need for Network Address Translation (NAT) when connecting to local networks. NAT arose because of the finite nature of IPv4. Local routers needed additional addresses to connect multiple local devices to a single IPv4 address.
IPv6 generates so many possibilities that NAT is essentially obsolete. Local network devices can connect directly with devices located elsewhere. This direct connectivity has benefits for peer-to-peer networking, video conferencing, and generally improves speeds by reducing latency.
The table below summarizes the differences between IPv4 and IPv6 to clarify how the standards differ:
| IPv4 | IPv6 |
|---|---|---|
Address length | 32-bit | 128-bit |
Max number of addresses | 4.3 billion | 340 undecillion (essentially limitless) |
Notation | 4 decimal numbers separated by dots | 8 groups of four hexadecimal digits |
Local network connection | Requires NAT | Direct connections, NAT not needed |
Architecture | Uses 5 class architecture to connect network and host portions. | Abandons class-based architecture. Far more flexible for local area networks and internet users. |
Packet headers | Relatively complex: Variable length (20-60 characters), 13 fields, relies on checksums and broadcast groups. | Simplified. Standard 40 character format with 8 fields. More efficient due to higher-level checksums and uses multicast groups. |
Packet fragmentation | Allows routers to fragment packets. | Ues sPath MTU discovery that does not require packet fragmentation. |
Security | No native security features. | Caters for IPSec in protocol suite. Simplified header makes it harder to conceal malicious payloads. Fragmentation attacks less likely to evade firewalls. |
Configuration | Requires manual configuration. Relies on DHCP (Dynamic Host Configuration Protocol). Configuring routers can be tedious and complex. Inefficient stateful process for managing local address pools. | Uses more efficient SLAAC (Stateless Address Autoconfiguration) and supports auto configuration. Simplified router interaction with minimal need for server involvement. |
Types of IP addresses
Alongside the distinction between IPv4 and IPv6, IP addresses come in several varieties. Common IP address classes include:
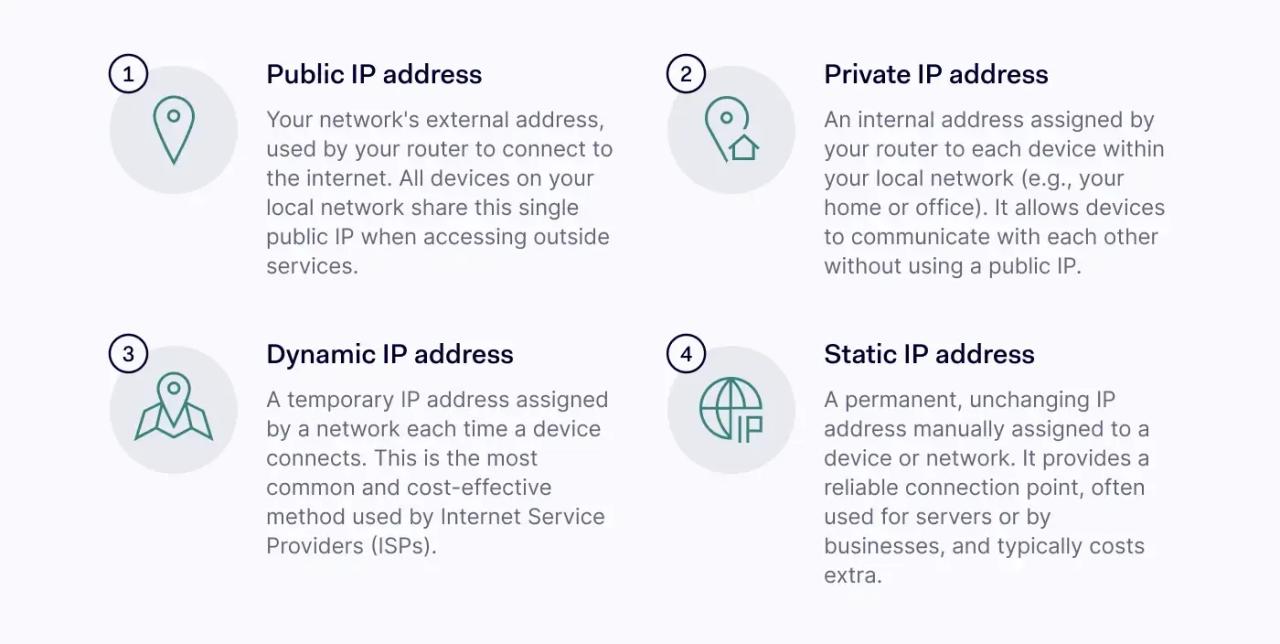
Public IP address
A public IP address is an address used to connect local devices to an internet service provider. This is why we also refer to public IP addresses as external-facing IP addresses.
Most of the time, the public IP address relates to the local router, which establishes a connection to the ISP. Devices connected to the router have the same public IP address as long as they connect to the ISP.
External devices must know your public IP address to open ports and establish reliable connections. For example, when playing online games, transferring data between remote devices, or streaming video media.
Private IP address
Private IP addresses (also known as internal-facing IP addresses) perform a slightly different function. These IP addresses are allocated within local settings such as offices or larger home networks.
Local routers assign private IP addresses to each connected device. The router links these private addresses to a public IP address when connecting to the external internet.
Private IP addresses arose due to the scarcity of IPv4 addresses. Private Internet Protocol addresses can be reused in many settings, reserving IPv4 addresses for external connections. IPv6 makes this need less urgent. In the updated IP system, local area networks assign a unique prefix for every device.
Dynamic IP address
Dynamic IP addresses are allocated automatically when users set up network routers. The DHCP protocol assigns a pool of dynamic IP addresses for all network users.
Users log into the network, receive a dynamic IP from the pool, and connect to the internet. In this system, IP addresses are not linked directly to devices, and users can use multiple IPs across different sessions.
Dynamic IPs are the most common form of IP address due to the scarcity of IPv4 addresses. ISPs maintain restricted pools of dynamic addresses under a rotating door model. This model is both efficient and cost-effective for ISPs, at least while IPv4 remains popular.
Static IP address
Static IP addresses are manually set up by users or ISPs. This IP address is defined as "static" because it is permanently linked to a router or network.
The ISP may assign a static IP, which remains constant for each session. Users typically pay an additional fee for each static IP address. ISPs tend to offer them as an additional service, not a routine feature.
How to find your IP address
Few people could quote their IP address from memory, or even look up their address regularly. However, you may need to know your IP address when configuring networks or troubleshooting technical issues.
Fortunately, it's easy to find your IP address. However, keep in mind the differences between private and public IP addresses, as discovery processes vary.
Users can discover their current IP address by visiting NordVPN's IP checking tool. The website automatically retrieves your active IP and shows its current location.
This is your public IP address. Locating private IP addresses is a little more complex, but still very simple.
- Windows: Open the command line and type "IPCONFIG". This will display all active connections on your computer network, including any IPv4 or IPv6 addresses.
- Linux: Open the shell terminal and type "ip addr show".
- MacOS: Open the terminal and type "IFCONFIG".
Security threats linked to IP addresses
IP addresses are crucial components of the modern internet. However, they are also linked to several security threats. Understanding how IP addresses relate to these threats can help you detect and neutralize vulnerabilities before attackers strike. Here are some critical threats to consider:
- DDoS attacks: Malicious actors can direct floods of traffic at your public IP. This flood of data packets can take down your server and render websites or network assets unavailable.
- IP spoofing: Attackers can use IP address spoofing to imitate your online identity and disguise malicious traffic.
- Data theft: Access to your IP address may enable attackers to access your network account and steal sensitive information.
- Cyberstalking: Standard IP addresses include location data. This data is not precise (attackers cannot derive your home address). However, they can identify your neighborhood and monitor your general movements.
- Phishing: Attackers can also use your IP to track the websites you visit. This provides valuable intelligence for phishers, who craft targeted emails containing infected attachments or links to malicious websites.
How to protect your IP address?
Whether you are using the internet for business or personal reasons, securing your IP address is always a best practice. The tips below will help you conceal your address from potential adversaries and browse the web securely.
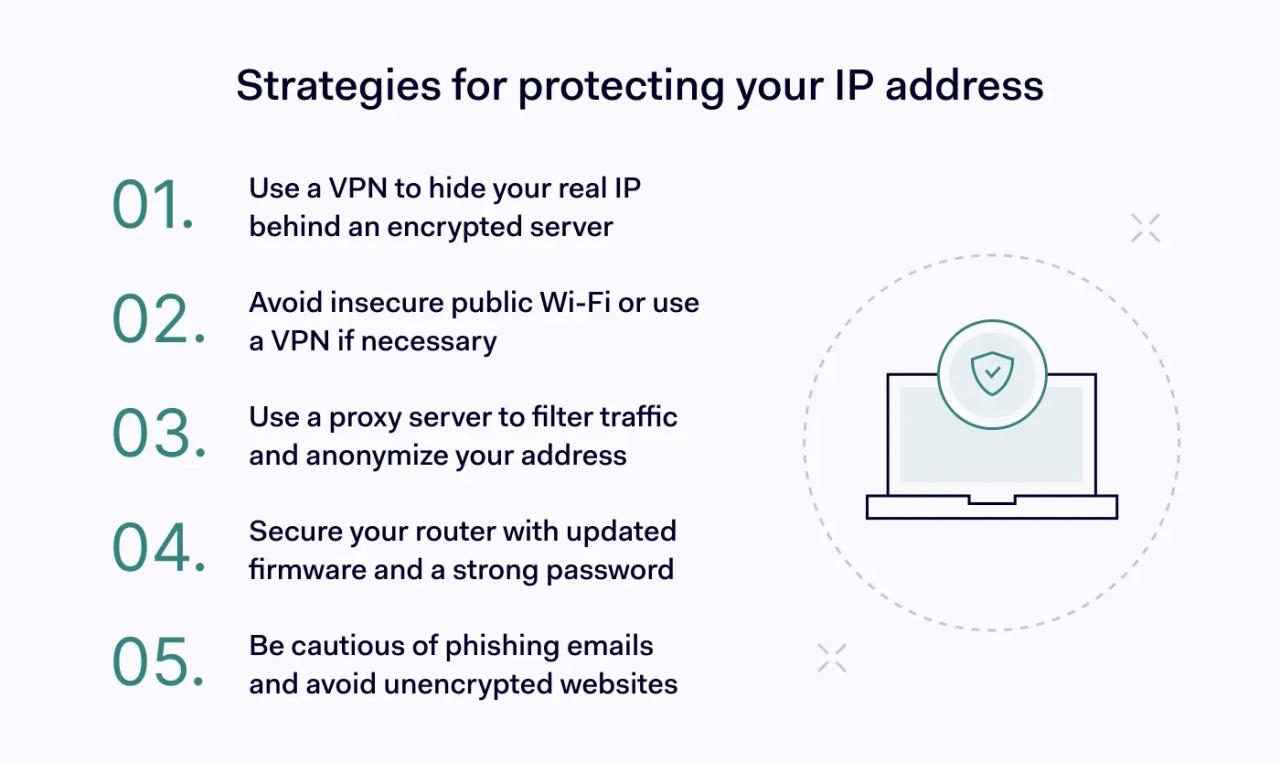
Use Virtual Private Networks (VPNs)
VPNs route traffic from your device through encrypted tunnels to private servers. These servers assign you a fresh IP address from a pool of available identities. External observers now "see" that assigned address, not your actual public IP address.
Only use secure wi-fi networks
Avoid insecure public networks when sending private emails or transferring work data. Public networks are generally unencrypted, exposing the IP addresses of users. Criminals also target wi-fi hotspots, enabling them to track users and exploit exposed addresses.
Only use secure networks that require password authentication (and preferably multi-factor authentication tools). If you need to connect while travelling, use a VPN first.
Install a proxy server
Proxy servers are less effective than VPNs when concealing IP addresses. However, they place an extra layer of defense between local devices and the external internet. Proxies on network routers help to filter web traffic and anonymize the IP addresses of local users.
Secure your router
Ensure your router firmware is up-to-date and change the default password if you have not already done so. Make sure you disable remote management features without authorization and manage router settings to prevent unsecured third-party connections.
Improve your phishing awareness
Be cautious when opening attachments or clicking embedded links in suspicious emails. A single click can install malware that scans for device information and IP address data. Also, avoid unencrypted websites (look for the HTTPS format and the padlock symbol).
Secure your IP address for seamless connectivity
IP addresses are unique IDs that allow internet-connected devices to interact. IPs come in many forms, including dynamic and static variants, as well as IPv4 and IPv6. Understanding the differences between IP address types is critical to optimizing connectivity and securing your online activity.
