Traditionally, firewalls are appliances that protect networks from malicious traffic. However, they can also run as a service on a computer by blocking harmful traffic from the device itself. This setup is called a host-based firewall, as they are hosted on a workstation, server, or network-connected device. Most modern operating systems already come with built-in firewall capabilities.
They offer granular controls to protect individual hosts against unwanted traffic, so they're quite popular among businesses. Let's take a deeper look at host-based firewalls.
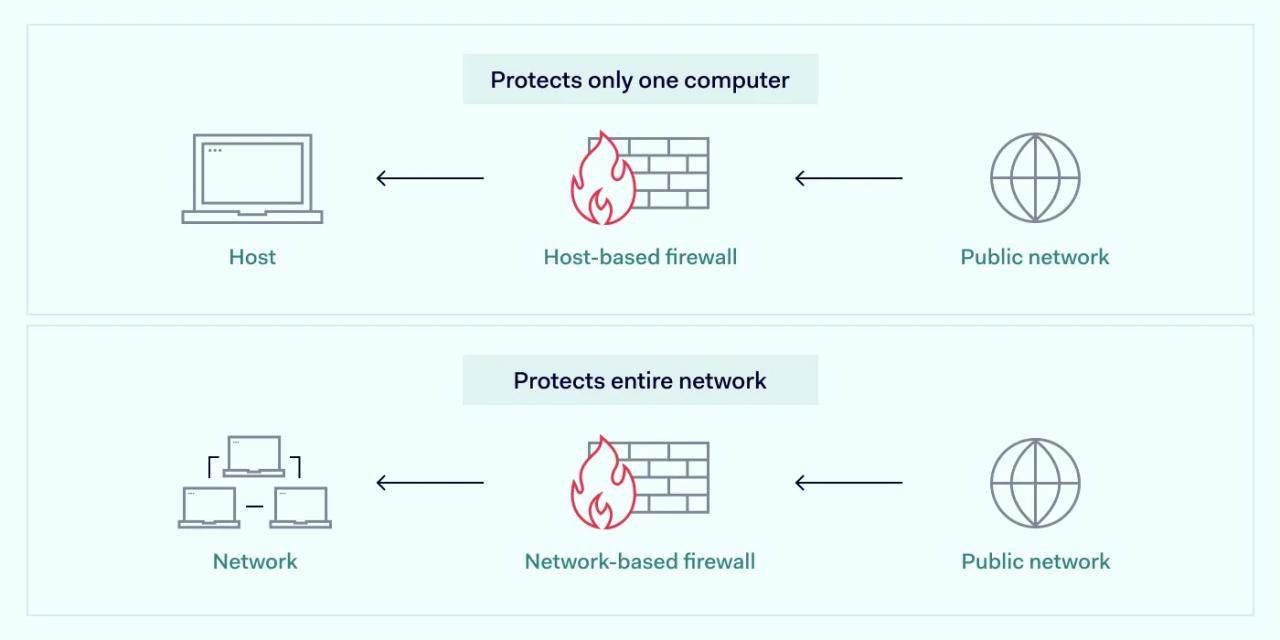
Host-based firewall definition
Host-based firewalls monitor the incoming and outgoing traffic of a single device, workstation, or server. Monitoring traffic that passes through a network interface controller can prevent various intrusions.
Many organizations add host-based firewall for each device as a supplement to perimeter-based firewall. This can add a layer of security within an individual device level. As they support various configurations, they can be customized to control what traffic is allowed.
How a host-based firewall works
Host-based firewalls need to be set up on an individual device. After this is done, they enforce rules, specifying which traffic is allowed and which isn't. Traffic identified as malicious is blocked to prevent malware from being installed on a single computer.
An example of a host-based firewall rule could be a requirement to block all traffic from known malicious IP addresses. When browsing and stumbling upon a denylisted website, it wouldn't load as the firewall would deny its IP address.
The main benefit is that host-based firewalls stay active even when switching networks. That's why they're so prominently used on portable user devices. This provides device protection which travels with a device.
Some host-based firewalls are advanced enough to protect against application attacks. It can add an additional piece of mind for both users and enterprises.
Benefits of using a host-based firewall
Host-based firewalls offer protection against viruses and malware. However, this isn't the only benefit that this type of firewall brings to its users.
Layered protection model
Having a host-based firewall and a network-based firewall creates two separate filtering mechanisms. While a network-based firewall examines data packet headers and block addresses or ports, host-based firewall functions act as an independent safeguard. Several layers of protection help to secure endpoints against a diverse range of threats.
Easy setup
Host-based firewalls are much easier to configure than network firewalls. The fact that frequently they're already built-in into the device's operating system means almost no deployment is needed. The setup involves just adding required configurations to a system already in place.
Security against various threats
Host-based firewalls can protect against threats originating from within the internal network. Additionally, only host-based firewalls can block network connections associated with specific programs and prevent malicious scripts from email attachments. This can be an invaluable tool for stopping worms — self-multiplying malware. Such firewall software can block outbound connection ports for associated applications like Excel, Word, Notepad, etc.
Portability
Host-based firewalls help ensure continuous protection even when a device changes the network. The rules are applied per device, which means they are independent of the network. It allows a stable basis for security policies with mobile devices and laptops without interfering with the company's network firewall.
Additional internal network controls
The main idea is that intra-subnet traffic is extremely difficult to control without host-based firewalls. This gives network administrators additional leverage when denying workstation communications. It could also backfire in a data breach, so limiting excessive interconnectivity is better.
How to set up a host-based firewall
Host-based firewalls need to be directly installed on individual computers, although most consumer operating systems come with them built-in. For instance, Windows and macOS systems already have firewall software allowing traffic filtering. It's also an option to turn to third-party providers.
Enterprise network administrators can manage Windows host firewalls via Group Policy Management, which allows them to apply settings across all endpoints easily. Users must rely on proprietary software like Mobile Device Management for macOS systems to apply host-based firewall settings across all employee devices.
What rules should or shouldn't be enabled will depend on your organization's goals. Here are several good tips on how a host-based firewall could be set up:
- Create floating rules based on the connected network. Most modern host-based firewalls can memorize which networks are organizations and which aren't. This allows you to apply different security rules depending on what network your user is connected to. For instance, all intra-subnet traffic can be restricted when connected to an internal network. Meanwhile, when connected to a public network, everything can be restricted to the point that only HTTP/HTTPS can be allowed — forcing users to use a VPN for everything else.
- Add restriction rules for specific binaries. There exist many binaries that hackers could exploit to stage an attack by pushing them to perform actions beyond their intended purpose. However, host-based firewalls can be expanded by various binary libraries to recognize and block them. Setting up alerts when these binaries are used may also be a good idea — it can be a sign that something suspicious is underway.
- Restrict access to the server environments. Endpoint devices should be denied access to server environments and administrator dashboards. The focus should be on the ports with the best yield for hackers, i.e., 139, 445, 80, 443, 3389, and 22. Allow only a small number of workstations to access them and block all the rest — it will function as a local implementation of the least access privilege.
Closing thoughts
Unlike network-based firewalls, host-based firewalls are localized instances working within a device's perimeter. They protect personal computers and smartphones, monitoring traffic coming in and out of a device.
It allows enhanced internal network security to supplement the network firewall while providing enough customizability options for network administrators. Host-based firewalls are among the best security controls and communications protection solutions within the same VLAN.