Without extensions, a browser is a lonely application. Browser extensions enrich our web browsing experience, delivering essential services from spellchecking to password management.
We often need browser extensions to navigate the web. Many websites require plug-ins to function as designed. Teams also rely on add-ons to collaborate via browsers. Extensions are convenient and powerful, but they have a dark side. Malicious extensions can steal data, implant malware, and launch network-wide attacks.
This article will explore how browser extensions work, why we need them, and how they create security risks. We will finish with a set of best practices for using extensions safely while enjoying the benefits they deliver.
Browser extension definition
A browser extension is an application that adds functionality to a web browser. Also called plug-ins, extensions access browser APIs to deliver services. These include blocking ads, checking text, storing passwords, and processing images.
But not all browser extensions are safe. Some are built to look legitimate while hiding serious threats. Malicious extensions often target browsers with specific attacks, including:
- Cross-Site Scripting (XSS). Injecting harmful code into web pages to steal data or redirect traffic
- Man-in-the-Browser (MitB). Intercepting traffic to steal credentials or perform unauthorized actions
- Data exfiltration. Sending browsing history, cookies, or credentials to external servers
- Content manipulation. Changing how websites appear to mislead users or inject ads
- Keylogging. Recording keystrokes to capture sensitive information like passwords
These threats require strong tools to detect and block unsafe extensions, while still allowing trusted plug-ins.
How do browser extensions work?
On its own, a web browser usually doesn’t offer all the features needed for daily work. Installed extensions let users customize their experience and add useful functions to the browser.
Extensions use CSS, HTML, or JavaScript to ensure compatibility with web page components and browsers. Users install extensions within their browser application. They then grant permission to access aspects of the browser's functionality via the extension's Application Programming Interface (API).
Content scripts then modify webpages, intercept content before the user sees it, save data, or change the content of browser tabs. Extensions may create pop-up user interfaces or websites to customize their operations, but they often function invisibly in the background.
The Chrome Web Store and the Mozilla add-ons portal are the largest distribution platforms for browser extensions. These platforms screen plug-ins for malicious content. However, you can obtain unscreened extensions from many repositories—or even via phishing emails.
What are browser extensions used for?
Extensions are a huge segment of the online world. The Google Chrome Store hosts approximately 140,000 extensions, while there are also 36,000 Firefox extensions.
The most familiar extensions serve individuals. Plug-ins allow us to control web content by blocking pop-ups or extracting images from websites. Website owners also use extensions to deliver more value to visitors. For example, an extension may allow users to personalize the look and content of sites, or remove unwanted content like pop-up ads.
Extensions also play a critical role in professional contexts. Web designers and coders use browser extensions to edit layouts and debug pages. Companies also use password managers like LastPass or threat detection tools to manage web security risks.
Productivity tools like Evernote and Grammarly use browser APIs to suggest email edits or record data from websites. Many Customer Relationship Management tools also use extensions to integrate web browsers with enterprise systems.
Given these many functions, hundreds of extensions may be active on a corporate network. Security teams must balance user experience and business needs with security—checking installed extensions for malware or exploits.
Common browser extension security risks
Browser extensions are far from harmless, and require careful monitoring.

Security risks connected to unsafe browser extensions include:
- Malware infections. Extensions install directly into browsers. This potentially enables access to the user's browsing history and web traffic. Criminals design extensions that appear authentic and persuade users to grant extensive permissions. However, the spoofed plug-in conceals a malware payload, which uses those permissions to harvest data or spread infections to connected devices.
- Exploits. Legitimate extensions can also pose a security risk if improperly coded. Extensions may contain exploits that represent an open door for opportunist threat actors. Exploit risks rise higher if many network users install the extension. In that case, attacks quickly spread throughout network resources.
- Data theft. Extensions can also steal data without the knowledge of users or the developer. For example, in the 2024 Cyberhaven attack, phishers posed as Google and threatened to delist the cybersecurity app from the Chrome Web Store. The developer granted permission to upload a fake app version to the store, compromising the data of 2.6 million account holders.
- Email compromises. Extensions can also steal email data and monitor communications. For example, in 2022, researchers discovered an agent called SHARPEXT. Installed covertly via phishing emails, SHARPEXT extracts webmail data until manually removed by the user.
- Adware delivery. Adware infection is one of the most common consequences of malicious extensions. Attackers deploy fake extensions like WebSearch that track user behavior and deliver targeted pop-ups. Adware is usually annoying but can also extract confidential data for sale or use in secondary cyber-attacks.
- Brand spoofing. Extensions pose a reputational risk to digital businesses. For example, spoofers have used Facebook to distribute fake ChatGPT extensions that steal cookies and other browsing data. Businesses that use extensions to reach customers must ensure their products are secure and remove imposters as quickly as possible.
Best practices to manage risks linked to malicious extensions
Malicious browser extensions expose your browsing activity, open the door to unwanted ads, and put sensitive data at risk. Fortunately, there are ways to use browser extensions safely that balance user experience and security.
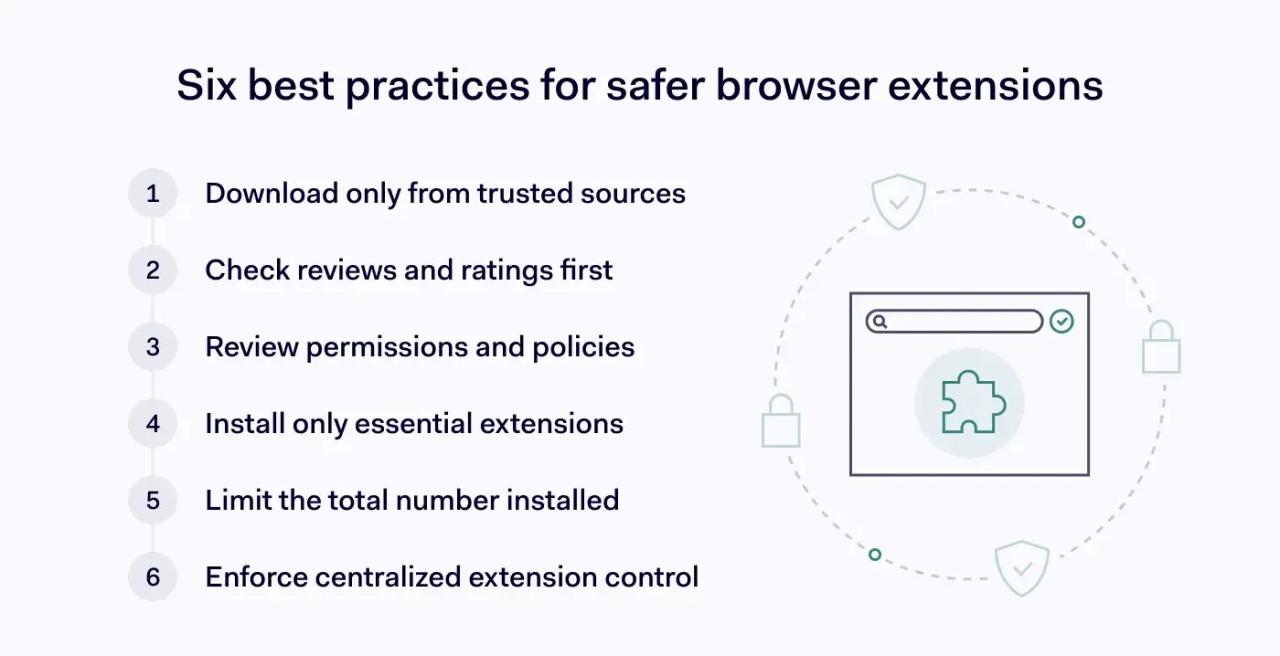
The best practices below should help you secure browsers and keep sensitive information safe:
Only download browser extensions from trusted sources
Most essential extensions are available on the Chrome Web Store or Mozilla's repository. If not, software vendors often make browser add-ons available via their business websites. Use these trusted download sources wherever possible.
However, even the Chrome Store is not 100% secure. Sometimes spoofed extensions appear in the listings. Guard against potential threats by checking for multiple extensions with similar names.
Many versions are a red flag. Ask yourself whether you are downloading the correct version. If you aren't certain, check with the extension vendor.
Check download feedback carefully
Extension download sites usually include space for user reviews and ratings. User feedback provides valuable information about possible scams or browser extensions with known exploits. Always check under the download for large volumes of negative feedback.
Overwhelmingly positive feedback is not necessarily good news, though. Threat actors often place five-star reviews under fake extensions, accompanied by phony feedback.
Read the privacy policy to understand browser permissions
All browser extensions request permission to access data and browser features. Permissions should only relate to functions the extension needs, but this is not always true. Malicious extensions request wide-ranging access to sensitive data or services like webmail that have little to do with their stated functions.
Verify the permissions you grant by reading the extension's privacy policy. This should be included with the download listing or the install process. If privacy information is lacking, do not add the tool to your installed extensions.
Add as few browser extensions as possible
Adding extra browser extensions amplifies cybersecurity risks. Every plug-in you install could be compromised or fake. Exploits can also appear over time, turning previously safe extensions into security risks. Too many add-ons also sap your browser speed.
Strictly limit extensions to critical business tools. When installing an add-on, ask yourself how it enhances your working processes. If you don't need it, don't install it.
Centrally manage installed extensions
Businesses benefit greatly from centralized browser management to reduce extension-related risks. Enterprise browsers run across all workstations, giving admins the power to enforce strict security policies.
Admins can allow only approved extensions or block all by default. They can also limit downloads to a short list of trusted plug-ins. Every download becomes visible, helping teams react fast when users install something suspicious.
Security teams can push rules to every endpoint, creating a uniform defense. These policies prevent data leaks, stop unauthorized extensions, and reduce the chance of a major cyber-attack.
Conclusion: Mitigate browser extension risks on all network endpoints
Browser extensions offer helpful features, but they also expose networks to real cyber threats. Malware infections, exploits, and stolen data are all common outcomes of using unsafe plug-ins.
To reduce these risks, companies should use enterprise browsers with built-in controls for managing extensions. This setup supports consistent policy enforcement and tight control over what users can install.
With clear rules and centralized tools, businesses can reduce exposure, keep sensitive data safe, and maintain strong cyber-resilience across every endpoint.
