When we browse the web, we assume that we are in control. Unfortunately, that is not always the case. Browser hijackers can take control of browser applications, enabling criminals to deliver ads, divert our searches, and even steal sensitive data.
Every web user needs to understand hijacking risks. This article will explain how browser hijackers work, what they do, and how to protect your online activity.
Browser hijacking definition
Browser hijacking is a type of cyber-attack where unwanted software changes your browser settings without permission. Browser hijackers often redirect victims to fake websites, change their start page, or add unasked for toolbars and ads. Attackers aim to earn revenues from ad clicks or—in some cases—gather data via surveillance malware.
How does browser hijacking work?
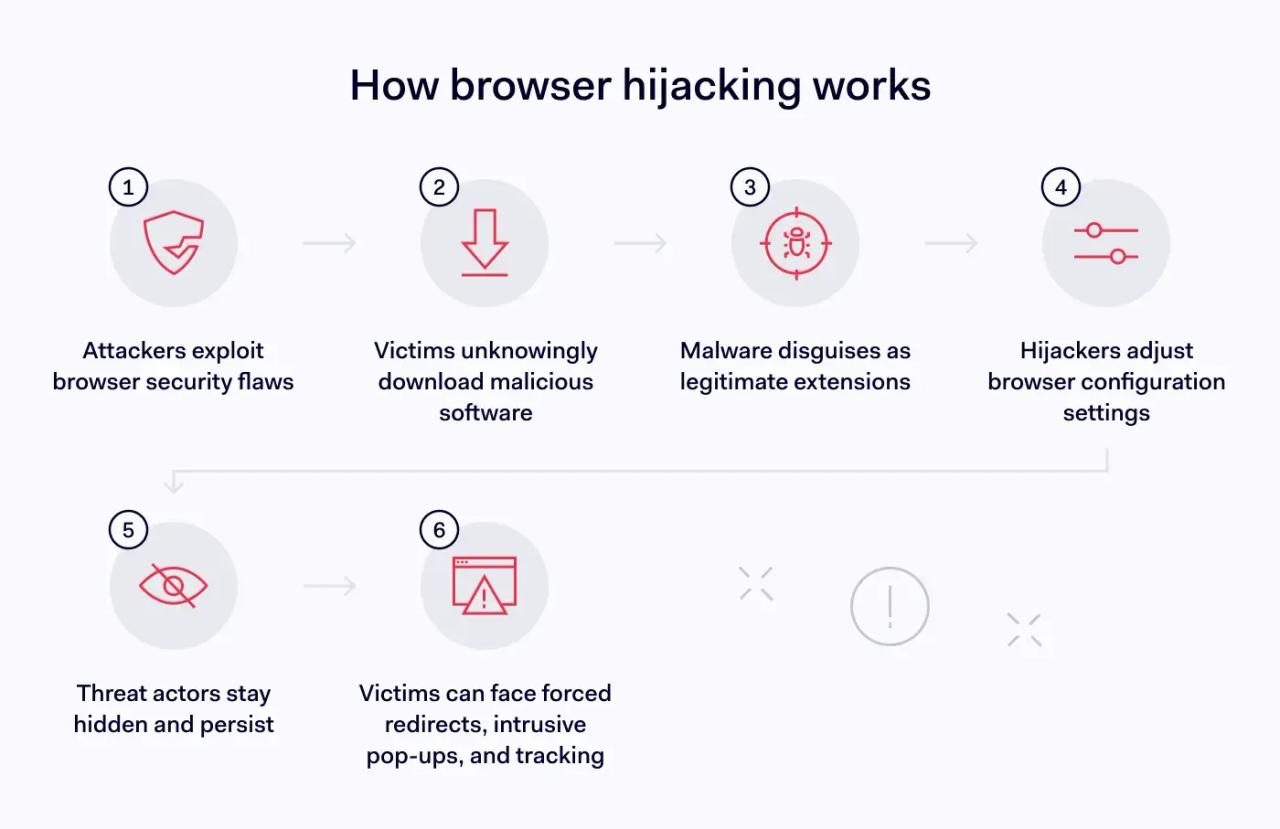
Browser hijacking uses malicious software to infect web browsers and execute criminal activity. Threat actors take control by exploiting common browser vulnerabilities, such as outdated browser versions, insecure plugins, or unpatched security flaws.
Browser hijacking starts with infiltration. Threat actors deceive targets into downloading malware. They may use phishing emails that encourage users to download infected attachments. However, attackers can also use code injection to execute scripts on malicious or compromised sites.
Targets unwittingly download browser hijacking software. This malware becomes embedded in the browser application, often by assuming the disguise of a legitimate extension.
When hijacking tools are in place, cybercriminals can freely amend browser settings. They can alter download settings, DNS preferences, start pages—and much more. Moreover, hijackers exploit browser flaws to evade detection and conceal their activities.
What are the consequences of browser hijacking?
The effects of browser hijacking range from mild annoyances to severe data security risks. Common consequences of browser hijackers include:
- Amended home pages and bookmarks. Attackers lock browser home pages to malicious sites, forcing targets to interact with dangerous forms or downloads.
- Malicious toolbars. Attackers add search bars to browser interfaces. When users interact with these tools, criminals gather data and redirect users to the sites of their choice.
- Pop-up ads. Browser hijacking commonly floods target devices with pop-up ads, leading to impaired performance.
- Website redirects. DNS changes can redirect browser users to fake websites that resemble legitimate versions but harvest data from site visitors.
- Surveillance. Attackers implant spyware within the browser. This malicious software collects information about browsing activity and may include keylogging capabilities.
Signs you've been targeted by a browser hijacker
Browser hijackers cause many unwanted consequences. Understanding the symptoms of hijacking attacks is critical to identifying malware and securing your browsing activity. Common signs of a browser hijack include:
- Inaccurate or low-quality search results. Browser hijackers often redirect web searches to prioritize their websites. Search results may resemble Google and other search engines, but the results are often inferior (or completely irrelevant).
- Website redirects. Users may see links they want to click. When they do so, their browser redirects them to a malicious website. If this happens, malware is almost certainly to blame.
- Slow speeds. Adware and spyware often affect computer performance. As a result, browser hijacking often slows down browsers. Hijackers may also use your system as part of a botnet or cryptojacking network, reducing speeds even more.
- Unfamiliar plug-ins. Browser hijacking uses extensions to deliver malware and control browsers. Check your extensions registry. New or unknown extensions could well be part of browser hijacks.
- More pop-ups than usual. One of the most common symptoms of browser hijackers is a deluge of pop-up ads on your internet browser. When you see more pop-ups than usual, the cause is probably malware infection.
How to remove browser hijackers
Cybersecurity best practices advise the prompt removal of browser hijackers. However, removing these persistent agents is not always simple. The steps below should erase most hijackers and ensure secure web browsing:
- Use reliable antivirus software to scan your system and identify resident threats. Choose antivirus software with a robust track record in removing spyware and specific browser-scanning functionality. If possible, set up automated security scans to sanitize your extensions registry and block hijackers at the source.
- Clear the browser's DNS cache. This should remove DNS modifications that redirect users to fake websites.
- Check your browser settings and restore them to their original state. For instance, you may need to restore your internet browser's home page or delete malicious bookmarks. In persistent hijacking attacks, resetting to defaults may not work. Fully removing the hijacking software may require a fresh browser installation.
- Explore other removal options. Sometimes, the steps above are not effective. In that case, you can often manually remove a browser hijacker via the Windows Control Panel. Go to the Program Manager tool and scroll down the list of installed programs. If you find the browser hijacker on the list, uninstall the app and reboot your system.
How to prevent browser hijacking
Browser hijackers can steal data, slow devices, and disrupt workflows. Preventing them requires strong security measures beyond basic browser settings. To prevent browser hijacking, you should:
Use a secure browser
Mainstream browsers like Chrome and Edge include security features, but enterprise browsers offer stronger protection. They provide centralized security management, allowing administrators to enforce policies across all users. Enterprise browsers screen links and downloads in real time, using current threat intelligence to detect and block threats. This reduces the risk of browser hijackers and malware without relying solely on extensions.
Avoid unsafe download sites
Downloading extensions is often essential to enhance browser functionality. However, not all download sites are safe. Avoid freeware download repositories or download sites without HTTPS encryption. Only use verified sites and app marketplaces or source software from vendor home pages.
Install threat detection software
Antivirus software and malware scanners should extend to browsing activity. Configure your device to assess every downloaded file before allowing execution. Consider wide-ranging endpoint defense tools that include anti-phishing measures.
Minimize employee privileges
Companies can limit the ability of employees to download and execute malicious software. Restrict downloads on work devices to those with administrative privileges. Regularly audit staff privileges to remedy temporary privileges escalations.
Train employees to understand browser hijackers
Human error is the main entry vector for browser hijackers. Employees often open unsafe emails, download files from unknown sites, and fail to detect the signs of browser hijacking. The only solution is comprehensive cybersecurity training that explains browser hijacking risks.
In summary: Neutralize browser hijackers to ensure a safe browsing experience
Browser hijackers pose a serious threat. They allow criminals to monitor activity and steal sensitive data. Even minor intrusions can slow computers and impact performance.
Basic prevention and malware removal help, but they may not stop advanced hijacking techniques. Enterprise browsers provide proactive defense with centralized management, real-time threat screening, and automated security policies. These tools help effectively block hijackers and protect sensitive information.
