We leave traces of ourselves wherever we go, in both the physical and digital world. Browser fingerprinting detects the unique evidence we leave as we browse the web. It separates legitimate users from imposters, allowing websites to block fraudsters without affecting the general user experience.
This article will explain what browser fingerprinting is and explore some common use cases. We will explore fingerprinting techniques, and suggest ways to use browser fingerprinting in your cybersecurity strategy.
Browser fingerprinting definition
Browser fingerprinting is a way of identifying online threats and authenticating web browsers by creating a unique identifier for each browser user. Metrics captured by fingerprinting include screen resolution, keyboard layout, access times, time zones, and the operating system.
When combined, this information creates a unique fingerprint or hash. Security tools use this fingerprint across browsing sessions to approve connections or respond to cyber-attacks.
Examples of browser fingerprinting
Browser fingerprinting is critical in securing connections to web applications and payment processing portals. It complements traditional browser cookies, providing a more in-depth picture of each user's security credentials.
How does this work in real-world scenarios? Use cases show why browser fingerprinting is indispensable and technically suitable for online businesses.

Fraud detection
Fraudsters often run many windows on a single device when mounting cyber-attacks. In this situation, each window tends to have a slightly lower resolution than a standard browser window. Fingerprinting techniques detect unpopular resolutions that may indicate fraudulent activity.
Fraud detection also leverages other metrics. For example, fingerprinting tools assess browser versions. Criminals may use vulnerable older browser iterations that have since received patches. Security tools also identify Virtual Machine environments—a common way of running multiple windows. Installed plug-ins also feed into risk scores, particularly adblockers known to interfere with fingerprinting methods.
Online marketing
Companies use browser fingerprinting in website optimization to profile potential customers. Companies collect browser data to understand who visits their sites and target product promotions.
For example, merchants may segment their sales strategy by location. Fingerprinting techniques can identify a user's general location. Sellers combine this with information about the area's demographics and wealth to determine suitable offerings.
Web application authentication
Browser fingerprints create a stable record that extends across login sessions. Companies can use fingerprinting techniques to identify legitimate users such as clients and employees. Security teams assign profile matches with a lower risk score while focusing threat assessments on users who deviate from their known browser fingerprint.
Note: browser fingerprinting is not a substitute for other authentication systems. Companies should use it with multi-factor authentication and firewall barriers to strengthen their security perimeter.
How does browser fingerprinting work?
Browser fingerprinting generally uses JavaScript to gather connection-related data points. Data includes:
- User-agent strings (browser type, version, and operating system)
- Screen resolution
- Installed plug-ins
- Time zone
- Preferred language
- Installed fonts
- Touchscreen settings
- Cookie storage settings
- IP addresses
- Hardware information (including the user's GPU, CPU, hardware drivers)
Fingerprinting techniques then bundle together this data to create a unique hash, which is stored in a secure database. This is an anonymized profile relating to a specific user and device. Browser fingerprinting does not include anything that can identify the user (such as their name or gender). It relies only on native browser features.
Nevertheless, every hash contains slight differences in installed fonts, screen resolutions, and language settings. This digital fingerprint stays constant across sessions, even if the user empties their cookie cache. Because of this stability, the hash provides a stable reference point to assess user and device behavior.
When users try to connect to web resources, security tools compare the stored unique fingerprint with real-time data. Departures from the hash may trigger manual or automated reviews. Reviews check whether the user has changed devices, or whether account takeovers are in progress.
Comparing fingerprinting vs. cookies
Fingerprinting techniques and tracking cookies are related digital technologies, but they perform slightly different roles.
Cookies are web tracking tools that create unique hashes when users visit websites for the first time. This hash identifies visitors when they return, allowing the website to serve targeted content or apply the user's unique settings.

Cookies are useful in web tracking but are of limited use as security tools. Users seeking anonymity can easily block cookies via browser extensions. Several factors make browser fingerprinting a more robust alternative:
- Browser fingerprinting techniques identify users with a high degree of accuracy by storing device and browser characteristics. Website owners can be more certain that users are who they claim to be.
- Browser fingerprinting is harder to block. Fingerprinting draws on a diverse range of data points and uses standard browser features. There is no cookie cache to empty.
- Companies can use device fingerprinting to track users between devices or browsers, provided the underlying user profile remains constant.
In practice, many companies prefer to use cookies and fingerprinting together. This enables businesses to personalize online services while guarding against spoofing and other fraudulent activity.
Browser fingerprinting techniques
So far, we have discussed browser fingerprinting as a broad family of profiling and tracking technologies. However, this is slightly misleading as there are many different browser fingerprinting techniques.

Consult the list below and choose a range of methods to suit your user base and online operations.
Audio fingerprinting
Audio fingerprinting analyzes how devices and software process audio content. We may not perceive it in everyday web browsing, but devices generate sounds differently. Fingerprinting tools use audio outputs to detect browser versions, audio cards, and even CPU architecture.
Security tools analyze these outputs and create a unique audio fingerprint for every device. This is valuable when securing audio collaboration tools (such as customer service lines). Companies also use audio fingerprinting in Digital Rights Management (DRM) to combat illegal music sharing.
Cross-browser fingerprinting
One of the main challenges in browser fingerprinting techniques is tracking users who employ multiple browsers or devices.
For instance, users may install Edge, Chrome, and Firefox on the same laptop. They may log into the same service via a workstation, laptop, or mobile device. Cross-browser fingerprinting solves this problem by creating hardware-based user profiles.
Cross-browser fingerprinting collects data on devices, plug-ins, browser versions, screen resolutions, and operating systems relating to individual users. This creates a hash that identifies users on multiple devices and browsers.
TLS fingerprinting
The Transport Layer Security (TLS) protocol encrypts web traffic when you visit sites and send information via browsers. TLS relies on handshake techniques to authenticate both parties to a transaction. These processes apply encryption algorithms and exchange keys to ensure secure data transfers.
TLS fingerprinting analyzes the handshake process. Fingerprinting tools assess how clients and servers interact, and can derive useful information about the user's device and software.
Canvas fingerprinting
Canvas fingerprinting uses HTML5 canvas elements to analyze user behavior. This type of analysis is particularly valuable because it provides insights into the user's device features such as the graphics card, drivers, and GPU of site visitors.
Canvas fingerprinting works by creating test images within the user's browser. Fingerprinting tools assess how the browser renders the image and overlaid text. Every device renders in different ways, depending on its configuration and components. The test image looks and appears subtly different for every user.
When the image is complete, browser fingerprinting tools create a unique hash which becomes the user's canvas fingerprint. Users are not aware of the process and it should not be resource intensive.
WebGL fingerprinting
Web GL fingerprinting leverages the Web Graphics Library to analyze user profiles. Fingerprinting scripts render 3D images inside user browsers that do not appear on screen. Browser fingerprinting tools monitor the rendering process, gathering data points about the user's graphics and processing hardware.
The WebGL fingerprinting process is similar to canvas fingerprinting. However, it analyzes how user devices execute WebGL instructions—which varies between GPUs, graphics drivers, and operating systems.
Media device fingerprinting
This browser fingerprinting technique collects information about media devices connected to a user's PC. Data points include all installed components, such as headphones, video cards, audio cards, cameras, and external media players.
Media fingerprinting is valuable for services that rely on access to microphones or webcams. However, it is less common than other fingerprinting varieties as users must grant access to devices before collecting data.
Mobile device fingerprinting
Employees increasingly access web browsers via smartphones or tablets—particularly email servers. Mobile browser fingerprinting is a form of device fingerprinting that identifies user devices and authenticates remote connections.
Fingerprinting tools gather information about mobile device models, Android or iOS versions, screen resolution, browser apps, battery data, and network settings. This information builds a unique fingerprint based on the device's inherent attributes.
Behavior tracking
Advanced forms of browser fingerprinting monitor user behavior to understand how they move their cursor, type words, and navigate the web. For instance, everyone scrolls websites with a slightly different pace and rhythm.
AI algorithms generate a digital fingerprint based on user activity and compare this profile with real-world behavior. Deviations from normal activity are often robust evidence of criminal activity and compromised web browsers.
Ways browser fingerprinting helps us combat online fraud
Browser fingerprinting enables us to create extremely detailed profiles of users and devices. Companies have many reasons to employ unique fingerprints, including access control and digital marketing. However, the most important application of browser fingerprinting is cutting online fraud risks.
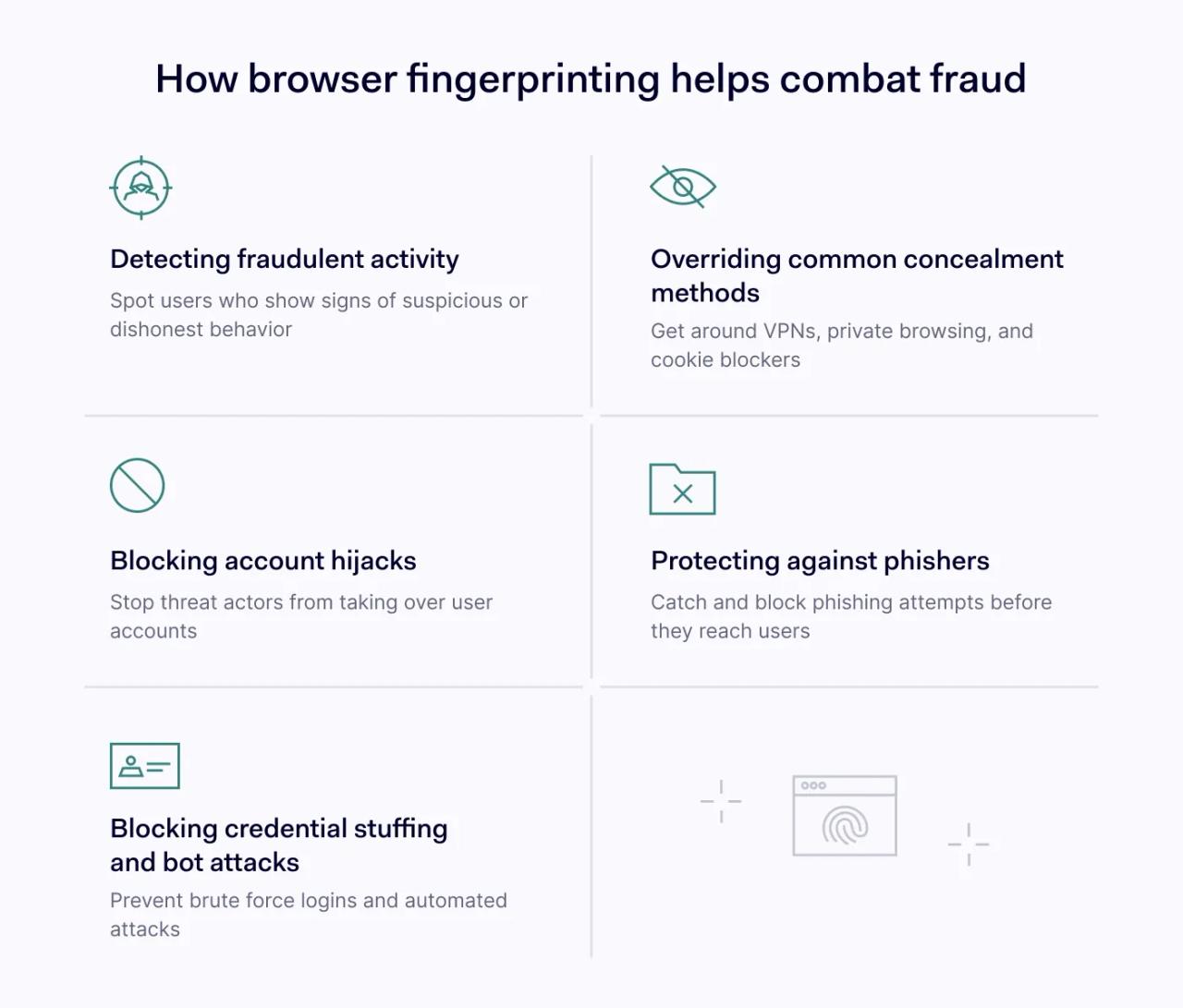
Browser fingerprinting helps us defeat fraudsters in several ways:
Detecting fraudulent activity
Digital fraud is an ever-present cyber threat, but only a few users visit websites with fraudulent intent. Most users want a smooth, fast experience—but companies must identify those intending harm.
Browser fingerprinting is one way to achieve this business goal. Fingerprinting assigns every legitimate visitor a unique identifier. Websites can allow entry if users and fingerprints match. If not, security teams can add suspicious users to their block list.
Companies can use browser fingerprinting to identify connected accounts. Accounts with similar hashes may indicate multi-accounting attacks, allowing security teams to take appropriate countermeasures.
Fingerprinting works well for this purpose because it does not impose additional authentication steps on ordinary users. Authentication and security controls operate in the background. There should be no ill effects on the user experience and site performance.
Overriding common concealment methods
Fraudsters try to conceal their activities and bypass security checks. For example, criminals may use VPNs to hide their IP addresses. They might block tracking cookies, spoof legitimate users, or employ a form of Incognito mode.
Websites need to work around these techniques without impairing the experience for legitimate users. Browser fingerprinting is an effective solution.
Fingerprinting techniques do not need IP addresses to profile users. Cookies are also not essential. Site owners can use accurate device and user-based profiles to identify and authenticate users—even when criminals use concealment methods.
Blocking account hijacks
Cybercriminals often use identity theft techniques to assume the identity of victims. They may then visit business websites under an assumed identity and make transactions or try to access sensitive network resources.
Browser fingerprinting combats account takeovers—a common form of web-based identity theft. Websites refer to a unique identifier created when a legitimate user signs up for their services. Log-in portals can detect differences between fingerprints and hijacked accounts, and block access to untrusted traffic.
Protecting against phishers
Phishing scams often obtain user credentials via fake websites or downloaded malware. Attackers can use these stolen credentials to access banking apps or business networks.
Browser fingerprinting can cut phishing risks by detecting suspicious traffic. Phishers may obtain log-in details, but criminals and victims will likely use different devices and browsers.
Browser fingerprinting detects this mismatch. Combined with multi-factor authentication, this provides robust protection against many phishing scams.
Blocking credential stuffing and bot attacks
Fingerprinting also helps block brute forcing and credential stuffing attacks where criminals seek to overwhelm log-in portals. Access systems detect malicious log-in attempts by noting deviations from stored user profiles.
The same applies to bot-based denial-of-service attacks. Browser fingerprinting can detect whether bots are exploiting a user's browser, and block access requests until the device data matches the user's stored fingerprint.
In summary: Use browser fingerprinting to secure your online activity
Browser fingerprinting and other fingerprinting techniques are indispensable tools in modern cybersecurity strategies. Unique digital identifiers based on device and browser characteristics enable businesses to sort legitimate users from malicious actors, enhancing fraud detection and prevention.
Browser fingerprinting is not a standalone measure. It complements cookies and traditional security measures like encryption and multi-factor authentication. Digital fingerprinting is a robust and reliable way to authenticate web users and protect against cyber threats like account hijacking, phishing, and bot attacks.
