Broken access control definition
Broken access control vulnerability is the restriction of access to applications and data. Organizations control access by authenticating connection requests and authorizing users to access the required functionality. Users only have access to the resources they need. All other data and applications are restricted according to the principle of least privilege.
Broken access controls occur when this process is compromised. Systems can fail to authenticate users securely. Improperly authenticated users can also escalate privileges, accessing resources that should be off-limits.
Many data breaches start with broken access controls, leading to reputational damage, loss of business data, and huge regulatory penalties.
A simple code error on a web page can open the door to scripting attacks. With a little knowledge, attackers can pose as legitimate users by taking control of orphaned accounts that should no longer be active. When that happens, it doesn't take long for intruders to gain access to financial or personal data.
This article will cover some of the most common access control faults. We will provide useful tips about how to guard web applications and network assets - helping you secure your network assets without hampering legitimate users.
Types of access control
Before we can understand how access controls break, we need to grasp the three main types of access control systems:
Vertical access control
Vertical access controls limit application or data access for different user types. User access varies depending on their role or classification. For instance, an admin user can add, remove, or change user profiles.
Ordinary employees do not have the power to carry out these functions. And because admin functions carry so much power, it's good practice to limit administrative privileges as much as possible.
Horizontal access control
Horizontal access controls limit application or data access to users with the necessary permissions. User access restrictions are not based on seniority. Instead, users at the same privileges level have different access levels to the same resources.
This is a common tool in financial companies seeking to comply with PCI-DSS regulations. Customers will have access to their accounts, where they can check balances and make transfers. But they do not have access to the accounts of others.
Context-dependent access control
Context-dependent access controls restrict access based on attributes of the application or the user connecting to it. Users can carry out actions if they meet specific conditions. Otherwise, access is denied.
For example, in e-commerce websites, it is important to ensure customers follow the correct order. Payments should be the final stage, and customers should not be able to change their order after that point. Contextual controls make this possible. Stores can verify the state of the user at every stage, regulating the purchasing process.
Examples of broken access control attacks
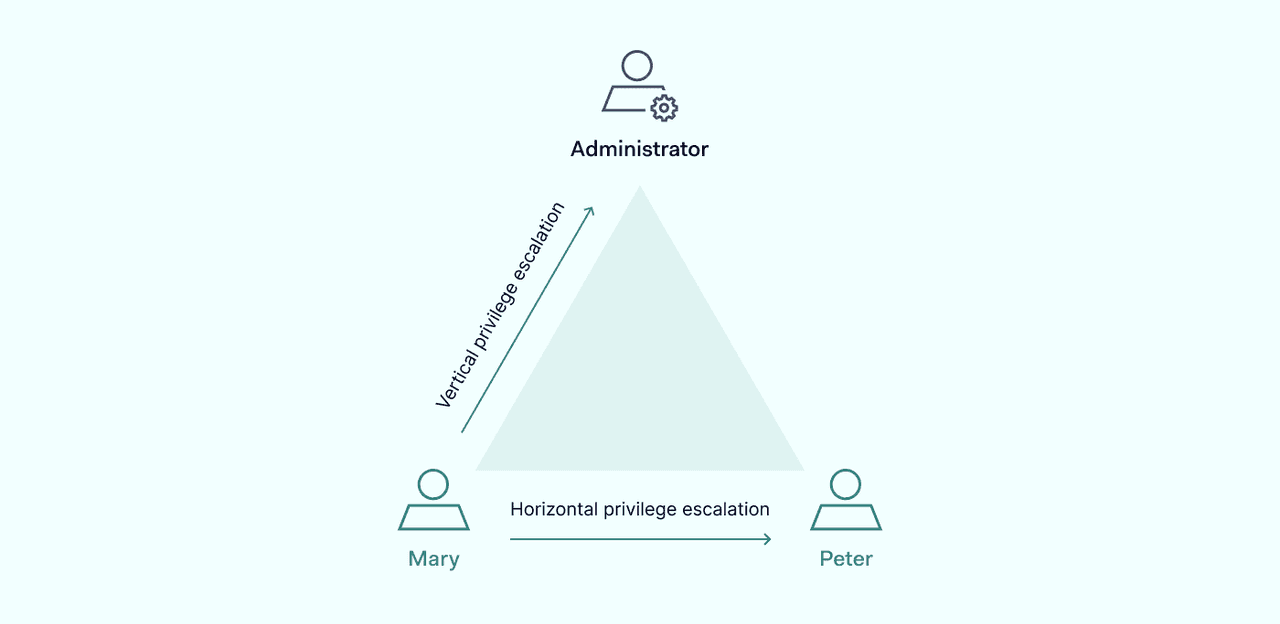
Privilege escalation is the most common type of broken access control vulnerability. There are two main types: vertical and horizontal privilege escalation.
Vertical privilege escalation
Vertical privilege escalation involves users gaining access to functions or data without the required privileges. Vertical privilege escalation can occur via:
- URL manipulation. Gaining access to privileged pages or functionality by directly manipulating URLs/parameters without proper authorization checks
- Exploiting Application Programming Interfaces (APIs). Certain API endpoints may not enforce proper access controls, allowing unprivileged users to perform privileged actions by directly calling APIs
Attackers or insiders may use standard customer or employee accounts to obtain administrative privileges. This gives them far more power to manipulate application settings and extract confidential data.
Horizontal privilege escalation
Horizontal privilege escalation involves users gaining access to other users' accounts at the same privilege level. Horizontal privilege escalation can occur via:
- Session manipulation. Gaining access to another user's session by hijacking/guessing session tokens/cookies or exploiting insecure session management
- Context switching errors. Bypassing access controls by changing user context/identifiers in the URL or via impersonation tokens without re-authenticating
Attackers may use “pass the hash” techniques to obtain password hashes and gain access by posing as another user. Or they might be able to guess the identifiers of other users. In the most basic cases, attackers can simply escalate their privileges by changing a target URL's identifier.
Horizontal privilege escalation is generally harder to detect than vertical privilege escalation. Security teams can usually see when ordinary users start exercising admin privileges. However, anomalies are much harder to detect when users mimic accounts at the same privilege level.
The two main examples of broken access control are not mutually exclusive. Horizontal privilege escalation can also lead to vertical escalation if attackers target users with additional privileges. So security teams need to remain vigilant about both broken access control varieties.
Privilege escalation is the main form of broken access control vulnerability. But it’s important to note that escalation can occur in various ways.
Networks and websites face many threats that break access controls and allow malicious actors to gain access. Let’s move on to detection, and discuss how to identify potential weaknesses.
How to detect broken access control vulnerabilities?
Detecting a broken access control vulnerability requires knowledge of common attack methods. Here are some common vulnerabilities to double-check when setting up access control defenses:
Not limiting URL access
Developers may specify user IDs in the web address. After logging in properly, attackers can substitute the ID of another user for their own. This is a basic flaw but allows easy access to accounts at the same privilege level.
Problems with insecure direct object references (IDOR)
Direct object references in URLs can open the door to the extraction of source code data. Attackers can use null byte code after Insecure Direct Object References. This makes it possible to obtain the source code of the original URL. Malicious users can then leverage the extracted code. With a few commands, they can gain unauthorized access to critical assets like a website admin page.
URL matching violations
In some cases, websites will allow access to addresses that are inconsistently capitalized. But access control systems may not be as tolerant. If attackers enter a lowercase address, control systems may see it as a separate endpoint. And the website may not apply access restrictions to this unrecognized location.
Insecure session management
Websites may store user access data in cookies or hidden fields while users browse or work. In this case, attackers can access the hidden data and gain horizontal access by stealing user credentials.
Security by obscurity
Some poorly implemented websites choose obscure identifiers for user IDs and admin page references. The identifier may be hard to guess. But attackers can often obtain the information needed via JavaScript requests. Obscuring web information is not a substitute for in-depth authentication and authorization processes.
Weak passwords
Attackers can escalate their privileges by guessing simple passwords or brute forcing more complex terms. The use of “admin” for administrative accounts is a classic example. Or “default” for router firmware. Strong, regularly changed passwords are essential.
Over-privileged user profiles
Access controls can also break when administrators lose sight of the user lifecycle. For example, employees with administrative privileges might leave a company while their login identity remains active. Attackers could gain unauthorized access by using those now-obsolete credentials.
XSS and injection attacks
Injection access control attacks use forms and fields that provide an entry point for malicious code. This grants access to intruders. XSS scripting uses insecure website output to execute scripts that breach online defenses. Both attack types rely on poorly calibrated access controls.
Focusing on these core broken access control issues allows organizations to reinforce their access systems. Regular security audits should use this broken access control vulnerability list to detect points of weakness before attacks occur.
How to prevent access control vulnerabilities?
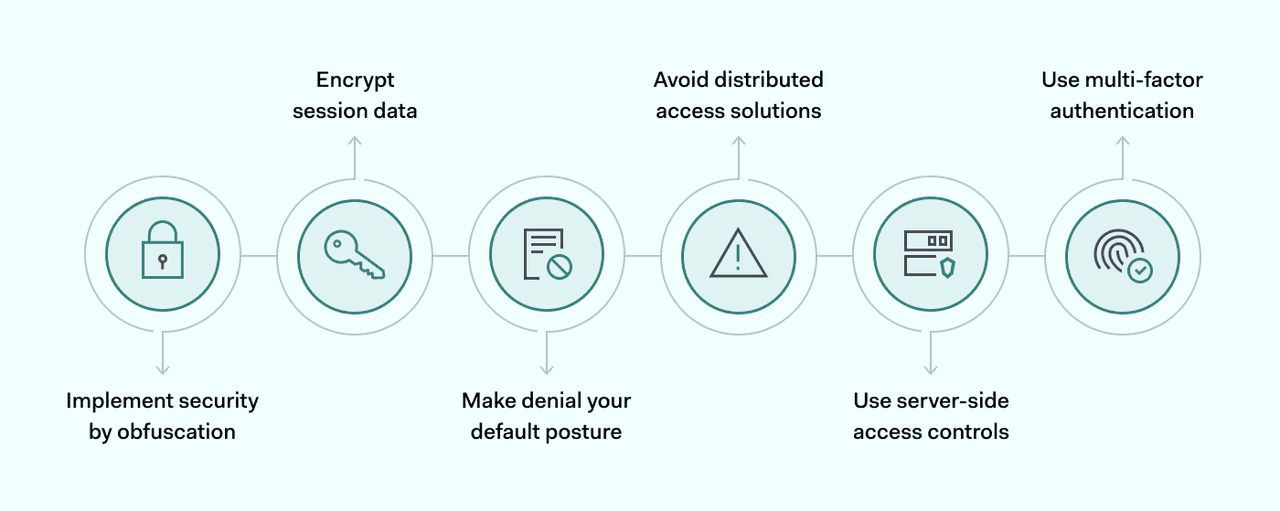
A single broken access control can compromise security and put sensitive data at risk. But by following access control best practices, companies can make their controls as secure as possible. Measures to think about include:
- Implement security by obfuscation. Properly implemented authentication and authorization controls are a much better solution.
- Encrypt session data to keep user credentials secure.
- Make denial your default posture. Unless resources are public, restrict access tightly. Employees should only be able to gain access for professional purposes.
- Build access into the codebase of all apps. Require developers to specify access rights and deny access by default.
- Avoid distributed access solutions. Control user access via a single authentication and authorization solution.
- Use server-side access controls and minimize the use of client-side caches.
- Use multi-factor authentication (MFA) to guard network resources. Add extra authentication factors to restrict access to sensitive data.
- Put in place role-based access controls based on the least privilege principle. Limit the number of users with admin privileges.
- Train employees to avoid phishing attacks and to use passwords safely.
- Audit access controls to verify they are working as planned.
Detecting broken access control vulnerabilities is a critical cybersecurity task. This applies to customer-side websites and access to corporate networks. Poorly designed access controls put sensitive data at risk, raising the risk of data breaches and reputational damage.
Dealing with broken access control issues involves understanding access control classifications. It also requires awareness of the security best practices outlined above. With the right defenses, organizations can ensure secure access to important resources. But it’s important to monitor access control vulnerabilities, as problems can emerge at any time.
