Summary: Explore how VPN blockers protect enterprise networks from unauthorized access and data exfiltration. Uncover the techniques and risks behind VPN use.
VPNs are often marketed as privacy tools, but in business environments, they can be a liability. Consumer-grade or free VPNs pose a significant blind spot. They can obscure user behavior, bypass corporate controls, and open doors to data exfiltration, compliance risks, and unauthorized access. This is where a VPN blocker becomes an essential layer of the enterprise cybersecurity stack.
This article explores the growing need for blocking VPN connections in business environments, the technologies that enable VPN detection, and how advanced techniques like deep packet inspection and IP blocking help counter VPN-based threats. We’ll weigh the pros and cons of blocking VPNs in corporate networks and explain why consumer VPNs, while designed for privacy, are often unsafe in business settings.
For organizations looking to maintain control, enforce policy, and secure every internet connection, understanding how VPN blockers work is critical.
What is a VPN blocker?
A VPN blocker is a network security tool or service that detects and prevents the use of unauthorized VPN connections within a network. It works by identifying traffic patterns, IP addresses, and other indicators commonly associated with VPN services, then blocks or restricts access accordingly.
VPN blockers can operate through methods such as IP blocking, filtering based on known VPN protocols, or using deep packet inspection to detect encrypted tunnels. The goal is to stop users from masking their real location or identity, switching servers, or using mobile data and free VPN tools to bypass security controls. By blocking these connections, organizations can ensure greater visibility, compliance, and overall control of their virtual private network infrastructure.
Why are VPNs blocked?
As mentioned above, VPNs are often associated with online privacy. But in many environments, they pose operational, legal, and security challenges. That’s why VPN blocking has become standard practice across sectors, from streaming platforms to corporate networks.
1. Geographic restrictions
Content providers and streaming services use VPN blockers to enforce regional licensing agreements. A VPN connection can mask a user's real location by routing traffic through a different country. To uphold contracts and control distribution, these platforms detect and block VPN connections, often using IP blocking and traffic pattern analysis.
2. Security and compliance
In business environments, unauthorized VPN services create visibility gaps. Employees using consumer VPNs, or mobile data paired with VPN apps, can bypass corporate firewalls, proxies, and other monitoring tools. This undermines network security and complicates compliance efforts, especially when sensitive data is involved.
3. Preventing misuse
VPNs can also obscure malicious activity. Threat actors or insider risks may rely on virtual private networks to conceal their IP address, evade detection, or exfiltrate data. Blocking these tools reduces the risk of VPN bypass techniques being used to hide unauthorized access or lateral movement within the network.
Across all these cases, the motivation to block VPNs comes down to control: control over content, over user behavior, and over network security.
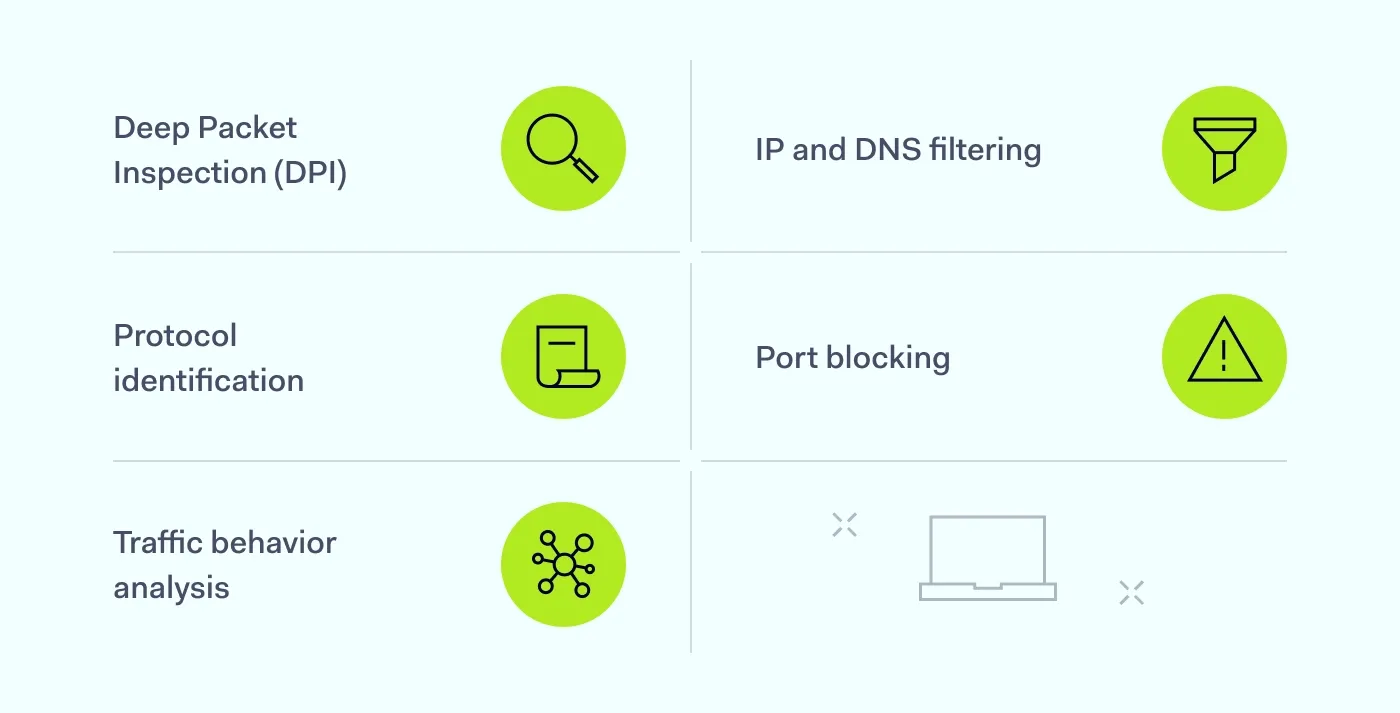
Techniques used to block VPN traffic
Blocking VPNs requires more than just a blacklist of IPs. Modern VPN services use encryption, dedicated IP addresses, and server obfuscation to avoid detection. To stay ahead, organizations use a combination of methods to enforce VPN blocking at the network level. Below are the most common techniques for detecting and blocking unauthorized virtual private network traffic.
Deep Packet Inspection (DPI)
DPI analyzes data packets beyond their headers, allowing administrators to inspect the contents of encrypted traffic in real time. By examining patterns in payloads and behaviors typical of VPN protocols, DPI can flag and block suspicious internet connections that indicate VPN use—even when standard ports or encryption are in play. This method is highly effective, but resource-intensive, and often reserved for environments where network security and data control are non-negotiable.
IP and DNS filtering
This technique blocks access to known IP addresses and DNS endpoints associated with VPN services. Many consumer VPNs operate on shared infrastructure, making them easier to detect and restrict. However, more sophisticated services use dedicated IP addresses, which makes this method less effective unless paired with others. DNS filtering also helps stop users from reaching VPN domains in the first place, disrupting the connection setup process.
Protocol identification
Different VPNs rely on specific tunneling protocols, like OpenVPN, IKEv2, or WireGuard, to create encrypted channels. By recognizing the unique signatures or negotiation handshakes of these VPN protocols, firewalls and security tools can block or throttle the connection before the tunnel is established. This method supports granular VPN blocking policies, allowing admins to allow certain protocols while restricting others.
Port blocking
While simple, port blocking is still useful in many environments. Common VPN services use standard ports (e.g., UDP 1194 for OpenVPN). Blocking these ports at the firewall level can disrupt VPN connectivity. However, modern VPNs often implement port forwarding or automatic fallback mechanisms, making this method more of a speed bump than a full barrier.
Traffic behavior analysis
Some advanced solutions use machine learning or behavioral analytics to flag anomalies in internet connection patterns, such as sudden latency changes, regular intervals in packet transmission, or encrypted traffic with no identifiable protocol. This technique is especially useful in spotting obfuscated VPN traffic or unusual activity from users with dedicated IPs to mask their activity.
Should businesses block VPNs?
For enterprise environments, VPN blocking isn't about restricting privacy. It's about managing risk. Unauthorized VPN services can create blind spots in your network security, making it harder to enforce policy, monitor activity, and respond to threats in real time. But blocking VPNs outright can have unintended consequences if not done with precision.
Below is a breakdown of the key advantages and challenges of implementing VPN restrictions in a business context:
Pros and cons of blocking VPNs
| |
|---|
Greater control over inbound and outbound network traffic | May disrupt legitimate remote access workflows |
Improved Data Loss Prevention (DLP) and threat visibility | Requires exceptions for approved or corporate-managed VPNs |
Reduces risk of shadow IT and insider threat activity | Can create friction for global teams or third-party collaborators |
Strengthens compliance with industry or regulatory mandates | Potential for false positives and increased support overhead |
Enhances overall cybersecurity | Complexity increases with BYOD and hybrid work environments |
Tip: Instead of blanket bans, organizations should implement policy-based VPN blocking. Focus on detecting and restricting unauthorized VPNs, while allowing secure, approved remote access solutions with centralized control, logging, and network security integration.
Why consumer VPNs are unsafe for businesses
Consumer VPN apps, whether free or paid, do not provide the enterprise-grade protection modern organizations require. Allowing their use within a business network risks introducing unmanaged infrastructure, reduced visibility, and compliance gaps.
Key risks associated with consumer VPN use:
Unverified server ownership: Many free or low-cost VPNs route traffic through untrusted jurisdictions. The infrastructure may be opaque, exposing your network traffic to legal environments with weak protections.
Lack of visibility: When employees install consumer VPNs on corporate or
BYOD devices, IT and security teams lose oversight. That makes it difficult to monitor traffic, receive alerts, or identify anomalous behavior.
No compliance guarantees: Most consumer VPNs don’t support audit logging, MFA, or retention policies needed for enterprise compliance frameworks.
Related articles

Joanna KrysińskaOct 24, 202410 min read

Andrius BuinovskisJul 15, 20246 min read
Real-world evidence: enterprise concerns and incidents
According to Zscaler’s VPN Risk Report (2023), 45% of organizations reported experiencing at least one cyberattack that exploited VPN vulnerabilities in the past 12 months; one in three confirmed VPN-related ransomware incidents. Overall, 88% of organizations expressed concern that VPNs threaten their network security, particularly when third-party consumer VPNs are involved.
While individual breaches linked directly to consumer VPN use are less often disclosed publicly, these statistics spotlight real-world damage associated with unmanaged VPN adoption, making clear why allowing such tools in your network is risky.
Preventing untrusted VPN use with NordLayer
Blocking unsafe or unauthorized VPNs is about ensuring secure, policy-aligned remote access. NordLayer offers several tools that help IT and security teams eliminate the risks of consumer VPNs without disrupting productivity.
1. Application Blocker— available with the Premium plan
NordLayer’s Application Blocker feature enables organizations to detect and restrict unauthorized VPN services by analyzing traffic at the application level. Unlike basic IP blocking, Application Blocker can identify VPN protocols and tunneling behavior even when traffic is encrypted or obfuscated.
Available under the Premium plan, Application Blocker lets businesses enforce VPN restrictions intelligently, flagging suspicious traffic, preventing VPN bypass attempts, and maintaining full network security visibility.
2. Dedicated IP— $40/month company-wide
To ensure secure, consistent connections that don't trigger false positives or geo-restrictions, NordLayer offers a dedicated IP address solution. It helps organizations maintain stable access to internal resources, implement strict access controls, and simplify IP-based policies.
A server with a dedicated IP is enough for the entire company, and costs an additional $40/month. It’s available for Core (from $11/user/month) and Premium (from $14/user/month) plans, making it an accessible and strategic upgrade for businesses managing hybrid or remote teams.
3. Network segmentation and access control
NordLayer also provides granular network security controls through features like Cloud LAN and Identity-Based Access. These ensure that only authorized users and devices can reach sensitive resources, whether working from an office, home, or traveling.
VPNs are not enough: modern businesses need layered cybersecurity
Using a standalone VPN, whether consumer or business-grade, isn’t really enough anymore. Teams are working from everywhere, cyber threats are getting smarter, and there are more rules to follow when it comes to data. To stay secure, businesses need more than just an encrypted connection. They need multiple layers of protection that work together.
NordLayer offers a complete security stack tailored for modern enterprises. In addition to VPN and VPN blocking capabilities, organizations can enable:
These features are available through flexible plans and centralized management, with fast deployment and minimal overhead. NordLayer makes it simple to scale your cybersecurity without overcomplicating your infrastructure.
If you're looking for more than just a VPN—something that strengthens your entire network security model—NordLayer delivers.
Contact sales to see how NordLayer can help your organization.

Aistė Medinė
Editor and Copywriter
An editor and writer who’s into way too many hobbies – cooking elaborate meals, watching old movies, and occasionally splattering paint on a canvas. Aistė's drawn to the creative side of cybercrime, especially the weirdly clever tricks scammers use to fool people. If it involves storytelling, mischief, or a bit of mystery, she’s probably interested.