As cyber threats become more common, selecting an effective security tool becomes increasingly important, as modern solutions offer granular control that goes beyond the traditional network firewall. The ideal solution depends on multiple factors, including required features, pricing, and the resources available within your IT team. One notable option available is Tailscale, which provides attractive features based on Zero Trust Network Access (ZTNA).
In this article, we'll explore secure network access tools, VPN solutions, and other Tailscale alternatives by looking at competitors similar to Tailscale. We'll provide a detailed comparison of different solutions and highlight popular options, helping you decide which tool best matches your organization's needs.
Disclaimer: This article is based on publicly available user feedback gathered on June 12, 2025, from platforms including Gartner Peer Insights™, G2, and vendor websites. For each competitor, we manually reviewed approximately 10–15 user reviews from the past 12 months, prioritizing recent and “most helpful” feedback on Gartner (where available), and the newest reviews on G2. Both positive and negative reviews were included to reflect a balanced view, though the number of relevant reviews varied by vendor. Brief or uninformative entries were excluded. As competitor offerings and user sentiment may evolve, NordLayer does not guarantee the accuracy or completeness of this information and recommends verifying details directly with each provider.
Overview of Tailscale
Tailscale is a network access solution built around the WireGuard protocol. It’s designed to create secure, direct connections between devices, potentially reducing latency compared to traditional VPN setups.
The platform aims to align with the Zero Trust model by integrating identity providers for managing permissions and verifying access. Organizations can use it to set up private overlay networks, segment private resources, and manage remote connections across their IT infrastructure. Additionally, Tailscale includes tools like access controls and audits to help teams keep track of who’s connecting to what.
Most mentioned product strengths
According to user reviews, Tailscale stands out for these key features:
Detailed access control policies, allowing admins to set precise permissions.
Audit capabilities, making it easier to enforce least-privilege principles.
Optimized network routes, often resulting in faster connections compared to standard VPNs.
Device sharing, useful for remotely troubleshooting user access issues.
Most mentioned overall product benefits of Tailscale
Users often highlight these benefits:
Easy setup with minimal technical effort required.
Fast performance due to direct WireGuard-based connections.
Quick onboarding for new users.
Wide platform compatibility, working on multiple operating systems.
Good scalability, suitable for teams as they grow.
Tailscale's drawbacks
Users also pointed out some downsides:
Dependence on tailnet DNS (Magic DNS) makes integration with existing DNS setups tricky.
The ACL interface could be simpler to streamline policy management.
Limited multi-tailnet options, making it harder to separate distinct environments.
No support for custom WireGuard exit nodes, limiting deployment flexibility.
Complex third-party admin setup (Headscale), challenging for users with less technical experience.
iOS app usability needs improvement, impacting user experience on mobile.
Disclaimer: This review is based on publicly available user-generated content from review platforms like G2, specifically focusing on recent user feedback accessed on June 12, 2025. This content is provided for informational purposes only and doesn't imply an endorsement or warranty. Readers should perform their own research before making purchasing decisions.
Let’s look now at Tailscale alternatives.
1. NordLayer
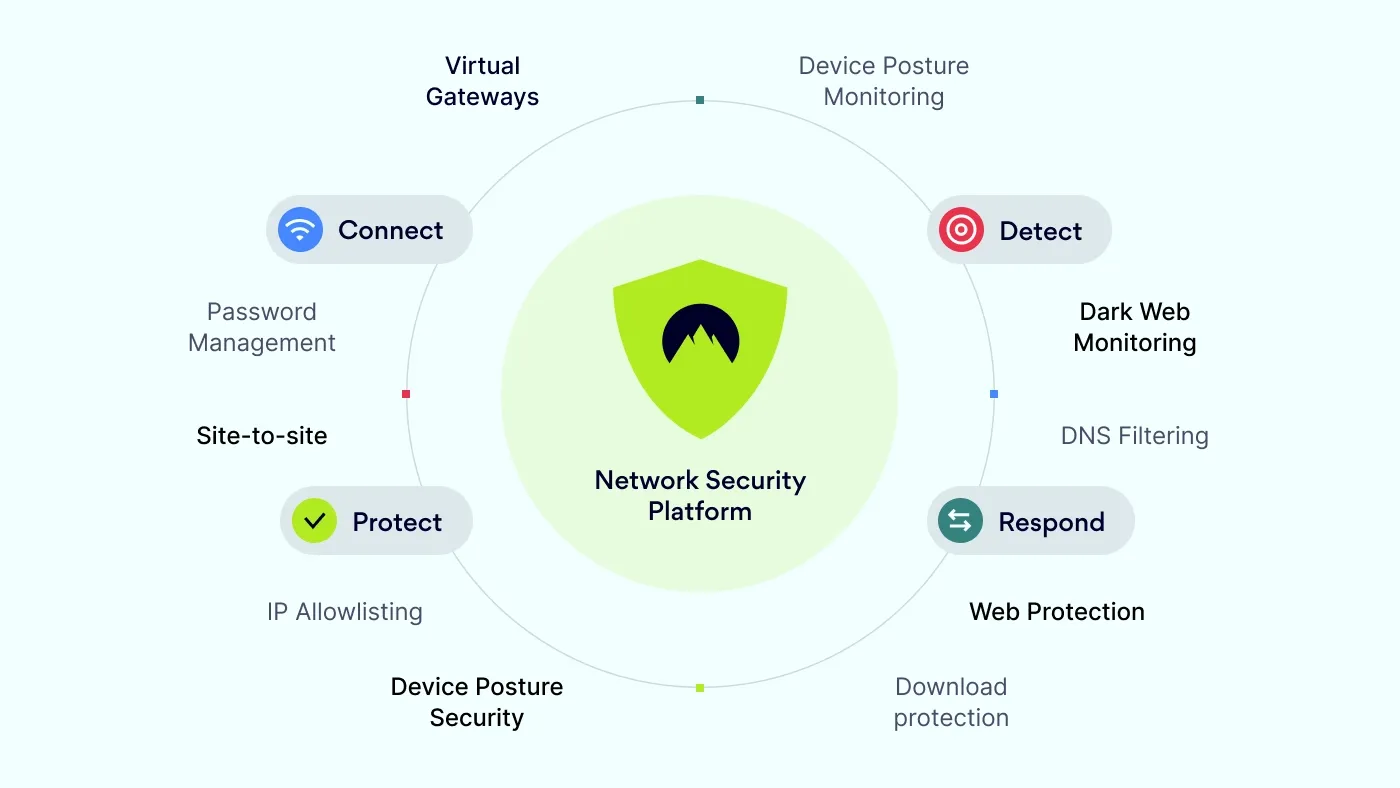
NordLayer is a toggle-ready network security platform designed to connect, protect, detect, and respond to threats. It leverages the same dependable security foundations behind NordVPN, allowing integration into existing infrastructure and services to provide comprehensive network security. According to users, with a focus on prompt and helpful customer support, fast setup, and robust security measures, NordLayer simplifies network protection.
Most mentioned NordLayer product strengths
Users consistently mention several key strengths when reviewing NordLayer. The most praised product strengths include:
Secure remote access, which allows teams to safely connect from any location.
Centralized control simplifies network security management from a unified interface.
Threat detection quickly identifies and addresses security risks.
Automatic reconnection, made possible by features like Auto-connect and Always On VPN.
Together, these strengths simplify robust network security and enable reliable, secure remote access, helping teams stay connected across locations.
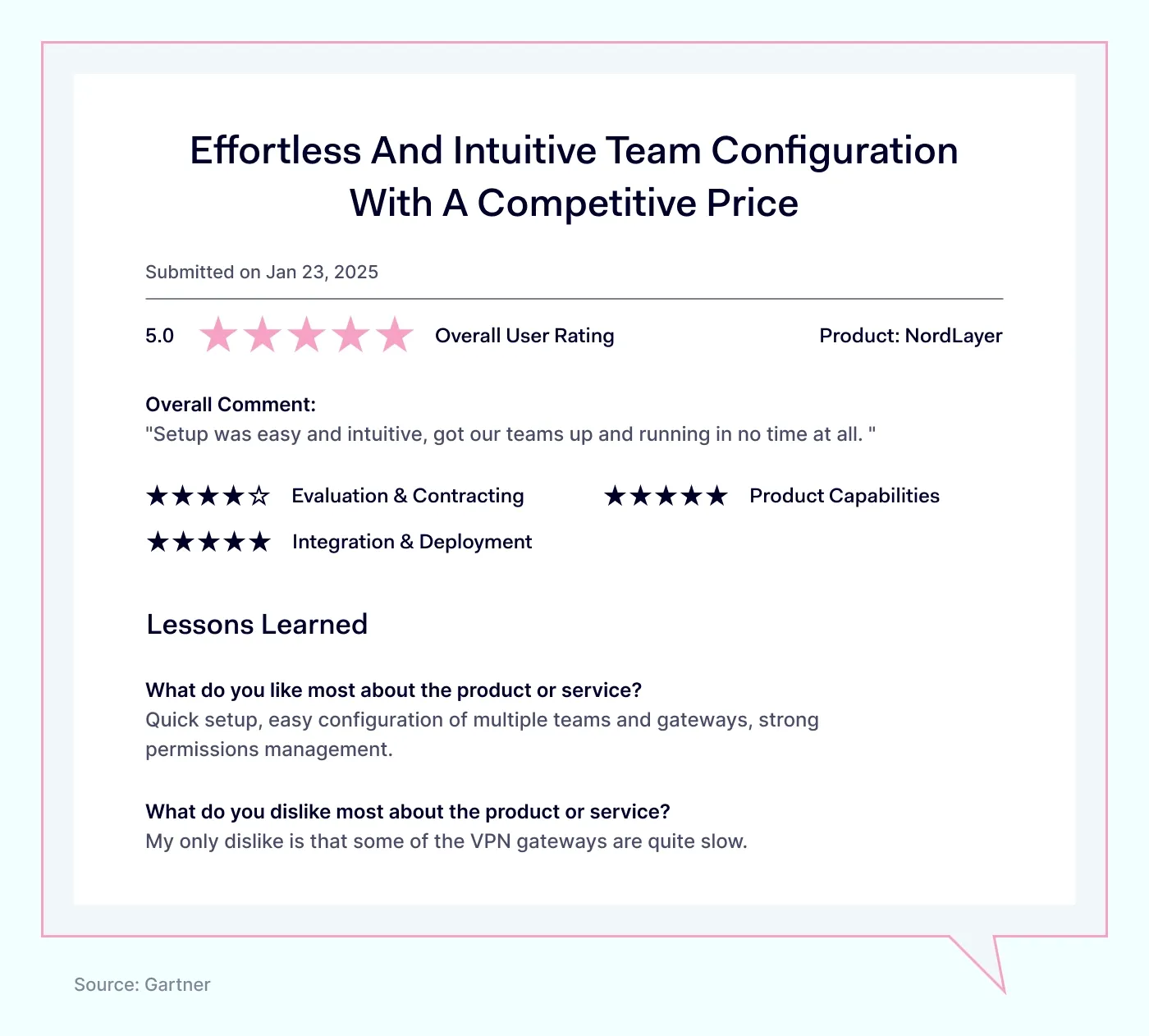
Most mentioned overall NordLayer benefits
Users frequently highlight these core NordLayer benefits:
Responsive support, a team that quickly and effectively resolves user issues.
Fast speeds, reliable network performance even during busy periods.
Quick setup, installations often require only around 5 minutes from start to finish.
Multi-platform compatibility, the platform runs smoothly across different devices and operating systems.
User-friendly implementation, users can easily set up the platform without technical expertise or significant effort.
These overall benefits demonstrate NordLayer's focus on usability and dependability, positively influencing user experience and satisfaction.
What makes NordLayer unique?
According to NordLayer’s website, NordLayer includes several advanced features that combine strong security with simplicity and speed:
NordLynx VPN protocol, which delivers rapid and reliable network connections with end-to-end encryption.
Browser Extension, which provides immediate protection while users browse online.
Web Protection, a feature that acts as a DNS firewall to proactively block unsafe websites and threats.
Download Protection, designed to identify and remove malware.
Potential drawbacks of NordLayer
Users mention certain limitations in their reviews of NordLayer:
Occasional drops in connection or speed, occurring mainly when users switch between servers.
License changes require contacting support, since users cannot manually reduce the number of licenses they have.
Limited availability of languages: Some common languages, such as Spanish, are not currently supported.
While these issues do not frequently arise, it is important to consider them when considering NordLayer.
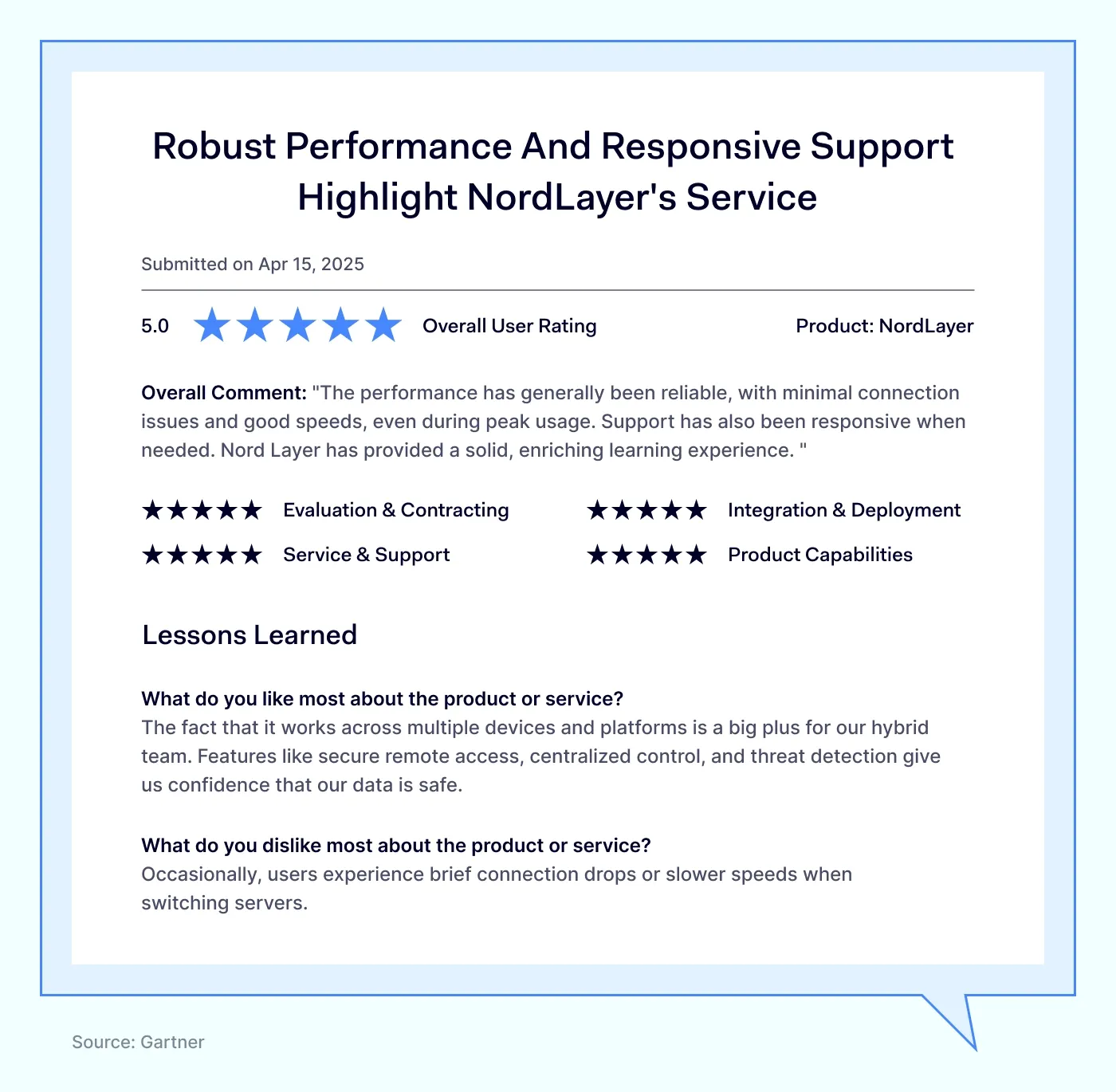
NordLayer user reviews
User feedback emphasizes NordLayer's ease of use combined with solid network protection.
NordLayer currently holds these ratings on industry review websites:
4.6 out of 5 on Gartner, one of the most respected technology review platforms.
4.3 out of 5 on G2.
These scores indicate that users generally appreciate NordLayer's balanced combination of intuitive usability and robust security features.
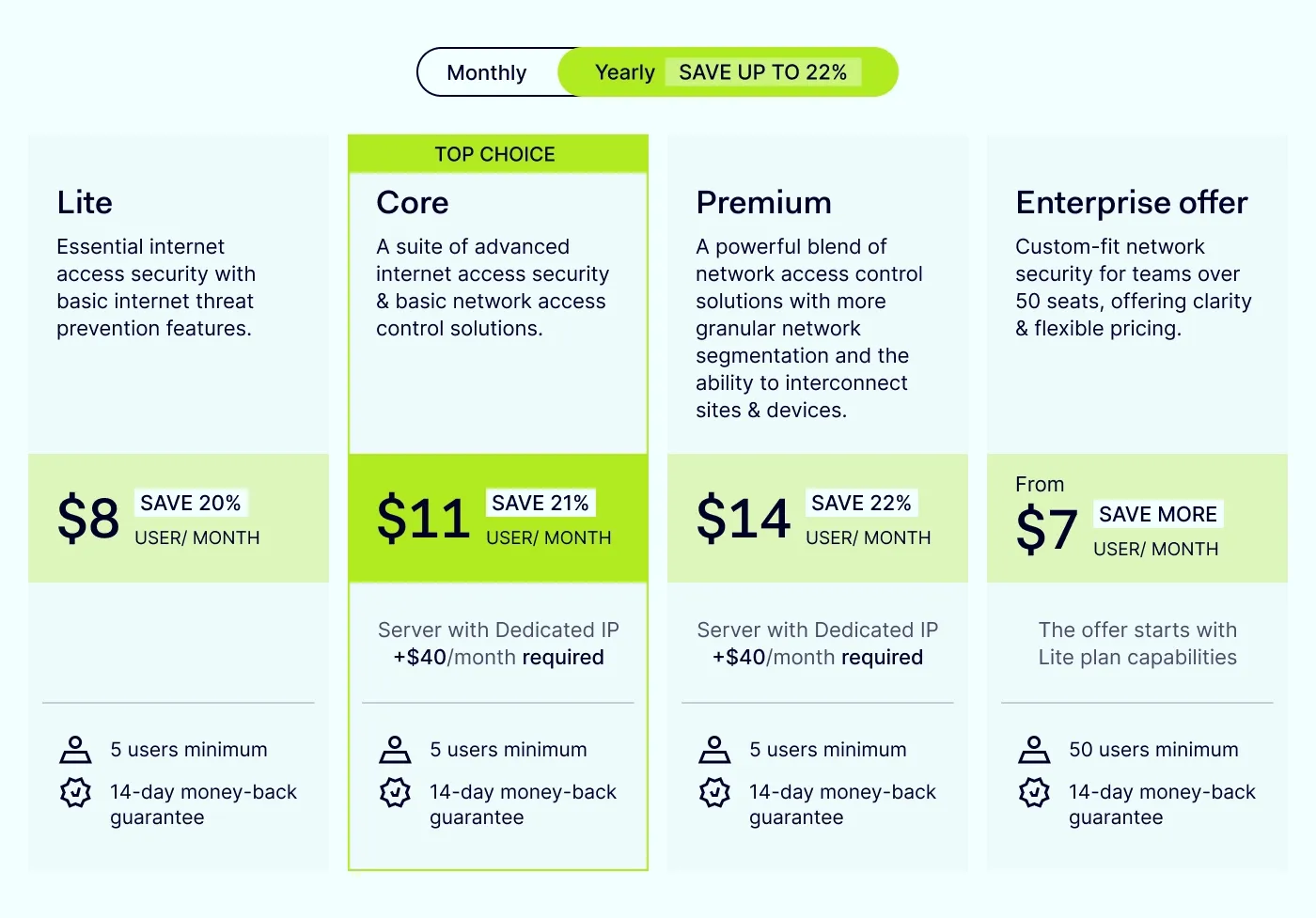
NordLayer pricing
NordLayer provides several different pricing options, including options for custom pricing on enterprise plans. All plans come standard with the following:
Server connection speeds reaching 1 Gbps.
Access to shared gateways located in more than 40 countries around the world.
Session duration control is a feature that logs users out automatically after a defined period of inactivity.
Essential security features such as Web Protection, multi-factor authentication (MFA), Always On VPN, and Single Sign-On (SSO).
Compatibility with various VPN protocols, including NordLynx, OpenVPN (UDP), and OpenVPN (TCP).
NordLayer plans require a minimum of 5 users per organization.
Disclaimer: This information is based on NordLayer’s website and third-party user reviews from Gartner and G2, accessed on June 12, 2025. NordLayer aims to provide accurate and up-to-date information but is not responsible for any inaccuracies from third-party sources.
2. GoodAccess
GoodAccess describes itself as a Zero Trust Architecture as a Service platform, primarily designed for small to medium-sized businesses. It offers a suite of security services, including a business VPN, Zero Trust Network Access, software-defined perimeter, and secure web gateway features. The solution also supports compliance needs, providing tools such as DNS filtering, multi-factor authentication, and split tunneling.
Most mentioned product strengths
Users frequently highlight these strengths:
A wide range of Single Sign-On (SSO) providers, particularly beneficial in premium plans.
Easy integration with SAML-based authentication providers enhancing security and convenience.
SCIM provisioning, available from the premium tier, simplifying user account management.
Static IP addresses, useful for stable and secure remote connections.
REST API availability, making it simpler to export and utilize data externally.
Most mentioned overall product benefits of GoodAccess
Customers appreciate GoodAccess primarily for these reasons:
Easy-to-use platform, straightforward even for non-technical users.
Detailed reporting, helping track network and resource utilization clearly.
Responsive support team.
GoodAccess's limitations
Reviewers also note several areas needing improvement:
Limited logging features and a maximum of 500 users per gateway, restricting visibility.
No option for concurrent connection licenses, limiting flexibility in licensing.
The pricing model can lead to high scaling costs when additional gateways are added.
Credential viewing issue, as checking credentials in the portal resets user passwords.
Restrictive renewal process, with limited negotiation flexibility for annual subscriptions.
Missing exclusion routing, causing unnecessary site blocking (e.g., Reddit).
Complex integration with Azure Virtual Desktop requiring additional effort.
Inconvenient cancellation process, as reducing licenses requires email communication.
Disclaimer: This review is based on publicly available user feedback from Gartner and G2 review platforms, focusing specifically on recent user experiences as of June 12, 2025. The information presented here is for informational purposes only and does not imply endorsement or guarantee. Readers should independently verify details before making purchase decisions.
Related articles

Anastasiya NovikavaJul 4, 20247 min read

Anastasiya NovikavaJul 26, 20257 min read
3. Twingate
Twingate positions itself as a Zero Trust platform designed as an alternative to traditional VPNs that rely on a perimeter firewall for security. According to the company, the platform uses software-based Zero Trust Network Access to simplify secure remote access without requiring additional hardware. It emphasizes a modern security approach—including least-privilege access controls, DNS and content filtering, and network visibility—to enhance security while keeping implementation simple.
Most mentioned product strengths
Users most often highlight these strengths of Twingate:
Easy connector deployment, which allows administrators to install connectors exactly where they are needed.
Granular ACL controls providing precise management over user permissions.
Resource alias feature, to help manage identical IP schemes across multiple networks.
Detailed audit capabilities, which offer valuable data for troubleshooting purposes.
Multiple available authentication methods, allowing flexible login and access configurations.
Clear activity monitoring, providing admins visibility into user actions, resources accessed, and login times.
Support for DNS-based routing simplifies tasks for administrators.
Terraform integration, enabling automated infrastructure setups.
Straightforward troubleshooting, supported by detailed reports and the "recent activity" dashboard.
Most mentioned overall product benefits
Reviewers frequently highlight these general benefits associated with Twingate:
Easy deployment and setup, making implementation straightforward even without deep networking experience.
Transparent user access, with end-users accessing protected resources without complication or disruption.
Versatility, meaning the platform adapts effectively across various use cases and environments.
Reliable and secure performance, combining stability with robust security controls.
Good pricing, offering cost-effective functionality.
Fast performance, delivering consistent and rapid connection speeds.
Security-focused approach, designed to restrict access through precise protocol-level and time-based rules.
Limitations mentioned by users
Despite these benefits, reviewers noted some common limitations of Twingate:
The user interface can feel unintuitive, and dashboard items are not always logically ordered or sufficiently detailed.
Support availability barriers, making it challenging to convince business stakeholders to approve product purchase without having easily accessible support channels.
Occasional stability issues, with sporadic connectivity problems experienced by global users.
Client installation may be complex, involving scripts and commands that can require extensive troubleshooting, despite simple initial instructions.
No official Arch Linux repository package, which adds complexity during setup for users of that OS.
Limited bulk management in the admin portal increasing the effort required when admins need to onboard or adjust multiple resources at once.
Disclaimer: This product review is based on information provided on VPN review sites such as Gartner and G2 and assessed customer feedback shared on these platforms, accessed on June 12, 2025.
4. OpenVPN
OpenVPN positions itself as a flexible VPN and secure access solution available in two deployment modes: a self-hosted "Access Server" solution and a cloud-delivered alternative called "CloudConnexa." The self-hosted version allows IT teams to control access policies on their infrastructure, run private tunnels, and host servers across platforms like Linux, Docker, VMware ESXi, and various cloud providers. CloudConnexa, its cloud-based option, aims to simplify connectivity between remote users, networks, applications, and IoT devices. The company highlights key capabilities of Zero Trust security controls, domain-based routing, content filtering, and IDS/IPS.
OpenVPN lists typical scenarios: remote access, IoT protection, site-to-site VPN solutions, secure DNS, restricted internet access, and enforcing the Zero Trust model.
Most mentioned product strengths
Users commonly emphasize these strengths when reviewing OpenVPN:
Effective balancing and access control making the solution practical in managing user connections.
Ability to tunnel IP subnetworks, allowing flexibility for advanced network scenarios.
Built-in firewall, providing an extra security layer for VPN traffic.
Smooth SAML integration, simplifying connections for users and admins.
SAML-based authentication, compatible with popular providers like Microsoft and Google Authenticator.
High connection speeds are described by some reviewers as significantly faster than other VPN solutions.
Most mentioned overall product benefits
Users frequently highlight the following product benefits:
Reliable customer support, assisting users efficiently.
Simple installation process, allowing setup without significant effort.
Easy-to-use interface, enabling intuitive and straightforward operation.
Simplified user management, making it easy for admins to manage VPN access.
Efficient network isolation, simplifying how admins segment and control subnet access.
Limitations mentioned by users
Although users generally appreciate OpenVPN, they cite these drawbacks as well:
Limited built-in reporting, meaning detailed analytics often require external software to generate meaningful insights.
Resource-intensive operation, particularly when deployed at larger scales, consuming more system resources compared to alternative VPN solutions.
Lack of official support for Ubuntu 24.10, forcing users to deploy via Docker, which complicates IP configuration tasks.
Outdated AWS CloudFormation documentation, causing difficulty during AWS deployments.
Limited license and pricing management autonomy, requiring sales team interaction when adjusting licenses.
Steep learning curve on Linux systems, making initial setup and configuration complex for users less familiar with Linux or Ubuntu OS.
Disclaimer: This product review is based on information provided on VPN review sites such as G2 and assessed customer feedback shared on these platforms, accessed on June 12, 2025.
5. Absolute Secure Access
Absolute Secure Access describes itself as a resilient Security Service Edge (SSE) platform optimized specifically for hybrid, field, and remote workers. According to the company, its solution leverages Zero Trust Network Access, dynamic policy enforcement, and proactive threat detection to protect remote workers and safeguard access to applications and internal services.
Most mentioned product strengths
Users commonly highlight these strengths when reviewing Absolute Secure Access:
Zero Trust Network Access, helping maintain strict security controls.
Support for MFA, enhancing identity validation.
Geo-fencing capabilities, offering additional context-driven access limitations.
Device compliance and enforcement, verifying that devices meet security policies before allowing access.
Split tunneling support, accommodating complex internal network configurations.
Comprehensive DNS leak protection, securing DNS queries effectively.
Robust user activity auditing and network insights, providing useful reports and visibility into operations.
Cross-platform support, offering compatibility with various devices and operating systems.
Wide range of customization options, meeting diverse organizational security requirements.
Device profiling and grouping, simplifying administration tasks for IT teams.
Reliable failover capabilities, addressing connectivity interruptions.
Network optimization features, improving performance for bandwidth-intensive applications like video calls and VoIP, even under less stable network conditions.
Most mentioned overall product benefits
Users frequently mention these overall benefits:
Easy implementation process, making initial deployment quick and straightforward.
User-friendly experience, simplifying administration and daily usage.
Responsive and helpful customer support, providing assistance quickly when needed.
Limitations mentioned by users
Despite generally positive feedback, users noted certain drawbacks of Absolute Secure Access:
Manual effort required for policy, compliance, and NAC additions, creating extra workload.
Occasional inaccurate component failure alerts, stemming from web server errors in the management portal.
Client upgrades can cause disruption, sometimes requiring physical device intervention if upgrades fail.
License reclaiming issue, where licenses don’t automatically become available when devices are removed from Active Directory.
No FIDO2 authentication support as of yet, limiting options for YubiKey users.
Outdated management interface, causing usability issues from an admin's perspective.
Challenges during remote troubleshooting, as remote connections to consoles aren't always reliable.
Difficult integration process with Duo MFA, complicating authentication setups.
Integration complexities with FortiAuthenticator, requiring additional administrative effort.
Pricing and licensing can get complicated, making license management more challenging over time.
Disclaimer: This section is based exclusively on publicly available user feedback collected from the Gartner and G2 review platforms, filtered by recency as of June 12, 2025. This information is provided for general informational purposes only and does not imply endorsement, guarantee, or ongoing completeness and accuracy. Readers are advised to independently verify product details directly with vendors before making purchasing decisions.
Finding the best fit among the many Tailscale alternatives to secure local networks and keep your team protected isn't always straightforward. It's common for decision-makers to feel unsure about the right first step.
To simplify this process, NordLayer has created a free Decision Maker’s Kit. This guide clearly outlines each step required—from initial planning to final selection—helping you choose the solution most appropriate for your organization's needs. The kit helps remove guesswork, ensuring confident, informed decisions.
Disclaimer: This article is authored and published by Nord Security Inc. as a comparative overview of network access solutions based on publicly available third-party reviews and user feedback accessed on June 12, 2025. The views presented reflect aggregated user opinions and are not endorsements.
The information in this article is provided for informational purposes only, and should not be considered definitive or permanent. While we strive for accuracy and completeness, Nord Security Inc. and its affiliates make no guarantees regarding the information's accuracy, completeness, or suitability. We do not undertake, warrant or represent that any product, or its feature, is or will remain publicly regarded as better or worse than other options, serve any purpose, has mentioned features, benefits, strengths, and limitations for any period of time. Product features, pricing, and other details may change, and we advise readers to verify these directly with vendors. We disclaim liability for any errors, omissions, or actions taken based on this information. The inclusion of competitor products does not imply affiliation, or endorsement, and all trademarks mentioned are the property of their respective owners. Readers should conduct their own research and seek independent advice before making purchasing decisions.

Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.