Summary: Healthcare companies can effectively defend against cyber threats with solutions like encryption, VPNs, and multi-factor authentication.
In this day and age, when a cyber-attack happens roughly every 40 seconds, no industry is safe from threats. Every organization, regardless of what it does, faces some level of risk.
That said, some industries are targeted far more than others. Healthcare, unfortunately, is near the top of that list. First, let us explain why that’s the case. Later, we’ll discuss what healthcare facilities and institutions can do to better protect themselves against hacking attempts.
Why the healthcare industry is particularly vulnerable to cyber-attacks
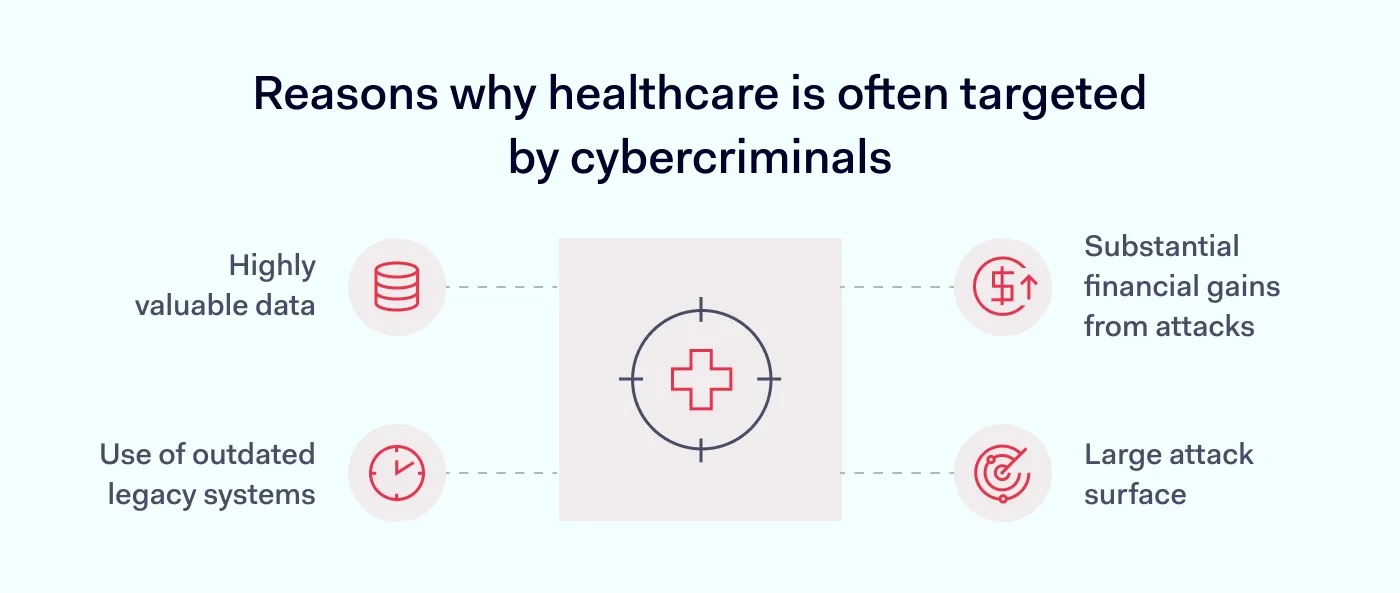
The key reason why healthcare is often targeted by cybercriminals is that it deals with highly valuable data. To provide their services, healthcare companies must store and manage large volumes of electronic health records, sensitive patient information, and other confidential files. We’re talking ID documents, Social Security numbers, medical histories, insurance papers, and more. All of those, as you can guess, are highly sought after on the dark web.
And that’s only part of the problem. We also need to consider that many healthcare organizations still rely on outdated computer systems and legacy infrastructure. Yesterday’s technologies simply can’t keep up with today’s cybersecurity threats—and attackers know this all too well.
Add to that the growing number of connected devices used in hospitals and clinics—many of which lack proper security—and you get a large attack surface. In this scenario, every device creates a potential risk that cybercriminals can exploit to break into the system.
The consequences of cyber-attacks for healthcare organizations
Let’s start with this: if sensitive data—personally identifying information, electronic health records, insurance details, and so on—gets leaked, the consequences can be far-reaching. For instance, attackers can use it to file fake insurance claims. They might also get prescription drugs illegally. In some cases, they could even blackmail patients or medical institutions to keep medical records private.
Of course, the impact of the breach on an organization can be profound. It can lead to severe financial losses and big damage to its reputation. Regular and potential customers may lose trust and run off to competitors.
And if you think incidents like this are probably rare, we hate to tell you otherwise. Cyber-attacks on healthcare companies have been on the rise over the last few years.
In 2024, the Department of Health and Human Services (HHS) reported that the average number of healthcare breaches was two per day. That’s millions of medical records compromised each year. This explains why healthcare organizations cannot afford to rely on half-measures when it comes to cybersecurity.
How to defend against cyber-attacks in healthcare
Just because the healthcare industry is a frequent target for cybercriminals doesn’t mean organizations in this sector should feel helpless. There are plenty of effective strategies and solutions available. If you’re part of this sector, here’s how you can improve your defenses:
Control who has access to electronic medical records
One way to boost healthcare cybersecurity is by adopting the Zero Trust model. Maybe you’ve heard the phrase “Never trust, always verify”—that’s what it’s all about. It means you double-check everyone’s identity every time they need to access sensitive resources, even if you’re 100% sure they work at your company. It may sound strict, but it’s one of the best methods to stop unauthorized access.
Also, just because someone is part of the team doesn’t mean they should have unlimited access to all sensitive information. You want to make sure people only access the apps and data they actually need, based on their role and responsibilities. That’s why it’s important to set up proper access permissions for each user in your organization.
Tools like Zero Trust Network Access (ZTNA) solutions can help you put this framework into practice. They let you set up proper identity checks and control access effectively, so employees only reach what they need for their work—and nothing more.
And one more thing. While focusing on digital access, remember to also control physical access to areas where servers and patient records are stored. Limiting this access helps prevent damage to equipment and data theft.
Related articles

Agnė SrėbaliūtėAug 7, 202415 min read

Joanna KrysińskaJun 12, 20257 min read
Divide your network into smaller parts
Speaking of controlling access to resources, you can take that concept further by breaking up your company’s network into smaller elements called “segments.” This process is called network segmentation. Basically, by using firewalls, gateways, and internet protocols, you create separate areas of the network for specific user groups to operate in—without giving them access to the other parts.
How does this help? For one, if a security incident occurs, it will be contained within that one particular segment. This means it won’t spread across the entire network. This not only helps you identify and resolve the issue faster but also protects the rest of your IT environment.
Use encryption to protect all patient records
When you encrypt sensitive information like medical research and patient records, you ensure that even if someone gets hold of this data, it will appear as a scrambled mess when they try to open it. All the information stays unreadable until the correct decryption key is provided.
Encryption is especially useful when you’re sharing sensitive information online, particularly between remote sites or workers. To keep data secure in transit, end-to-end encryption is often used. This means the data is encrypted right on the sender’s device and stays encrypted until it reaches the intended recipient, where it’s decrypted.
Because the data remains encrypted throughout its entire journey, even if someone intercepts it while it passes from point A to point B, they won’t be able to read or misuse it. Just remember that this protection requires using strong algorithms like AES-256 or XChaCha20 for encrypting your data—some weaker ones can still be cracked with modern hacking tools.
Get everyone to use only strong passwords
No matter how much you invest in healthcare cybersecurity, all that effort can go to waste if employees are using weak passwords. Verizon reports that web attacks happen mostly due to stolen credentials (77%) and easily guessable passwords (21%). That’s why it’s so important to make sure everyone on every team uses strong, hard-to-guess credentials.
To make this happen, you can use an advanced business password manager that allows you to enforce a strong password policy. Plus, it can help employees easily create, manage, and securely store strong passwords for all their work accounts. This way, they won’t have to struggle with coming up with long, random strings of characters or keep passwords written down in notebooks.
Add more protection layers to your online accounts
Considering how advanced threat actors’ methods have become for cracking passwords, one thing’s for sure—passwords alone might not be enough to keep work accounts safe. That’s why it’s important to add extra layers of security, like multi-factor authentication (MFA).
By implementing MFA, you require users to prove their identity with something beyond a password. This can be a code sent to their phone or a biometric scan. Access is granted only after that second step is verified. That way, even if someone does get hold of an employee’s password, they still won’t be able to break into their account.
Educate your employees
You can’t expect your team to follow security rules if you don’t explain why those rules exist in the first place.
That’s why investing in cybersecurity training is essential. In these sessions, the team should learn the basics of cyber threats and how to respond to attacks. For example, they should find out what a ransomware attack is, what types of information they can handle online, and what to do if they accidentally click on a phishing link.
By clearly explaining the threats, how they work, and how to avoid them, you greatly increase the chances that employees won’t make the human errors that can lead to security breaches. Also, if you need a knowledge base to refer to, you can check out our Cybersecurity Learning Centre. It covers everything from basic security frameworks to HIPAA compliance.
Update and monitor all software and devices regularly
Most of the software and hardware used in hospitals and clinics receive regular patches and updates, which are specifically designed to strengthen system and device security. With cyber-attacks becoming more and more sophisticated, staying on top of these updates is one of the simplest, most effective ways to protect mobile devices and improve IoT security.
Outdated software can create major vulnerabilities and weaken your device posture security. That’s why it’s so important not to skip updates, not even one. It might not seem urgent at the time, but missing that update could leave your systems exposed when you least expect it.
It’s also crucial that you continuously monitor all devices and platforms within your IT infrastructure. Why? To stay aware of everything connected to your company’s network, ensure each one complies with your security policies, and quickly identify any unusual behavior before it leads to potential vulnerabilities.
With NordLayer, you’re covered on key cybersecurity fronts
NordLayer is a toggle-ready network security platform that checks all the right boxes—especially for healthcare organizations looking to strengthen their defenses. In fact, it delivers on many of the key cybersecurity practices we’ve covered in this article.
For starters, it offers a cutting-edge Business VPN to ensure your team can safely access your network from anywhere. But that’s just the beginning. NordLayer also allows you to segment your network and control who can access what, while monitoring user activity. What’s more, it enables you to apply Zero Trust principles, so every user’s identity is checked before each login. It also helps maintain strong device posture security by allowing you to keep tabs on all devices in your network. Throw in multi-factor authentication, DNS filtering, malware prevention, and strong encryption, and you’ve got a tool built for serious protection.
Bottom line? NordLayer is designed to be an all-in-one solution for many of the cybersecurity challenges healthcare companies face. If you’re in the healthcare industry and want to learn more about our product, just contact our team. We’ll be happy to show you what NordLayer can do to protect your organization.

Maciej Sikora
Senior Copywriter
A man on a mission to engage audiences with creative wordplay, Maciej knows every complex idea can be broken down into simple words—and that’s his driving force. When he’s not writing, you’ll find him making music, taking a walk with his dog, or watching yet another movie.