As cyber threats grow more advanced and frequent, protecting sensitive data and ensuring secure remote access are top priorities. Reports show that cyber-attacks are becoming more complex and widespread, a trend that shows no signs of slowing down.
IT administrators must provide secure access amid challenges such as budget constraints, the need for easy-to-use solutions, scalable systems, and reliable customer support. To address these issues, many companies offer solutions that replace or improve traditional VPNs with more secure options.
This guide to Twingate alternatives compares various remote access solutions, breaking down their features, strengths, and drawbacks. It focuses on ease of use, scalability, and customer satisfaction to help you find a secure alternative that fits your needs. Whether you’re upgrading from a traditional VPN or exploring new options, this guide aims to provide a practical overview of key options to consider.
Disclaimer: This article is based on publicly available user feedback gathered on June 6, 2025, from platforms including Gartner Peer Insights™, G2, and vendor websites. For each competitor, we manually reviewed approximately 10–15 user reviews from the past 12 months, prioritizing recent and “most helpful” feedback on Gartner (where available), and the newest reviews on G2. Both positive and negative reviews were included to reflect a balanced view, though the number of relevant reviews varied by vendor. Brief or uninformative entries were excluded. As competitor offerings and user sentiment may evolve, NordLayer does not guarantee the accuracy or completeness of this information and recommends verifying details directly with each provider.
Twingate overview
Twingate positions itself as a Zero Trust network access solution, aiming to replace traditional VPN setups. According to the vendor, their software-based approach helps manage access to private resources and internet traffic without hardware deployment or intensive maintenance. The solution focuses on limiting lateral network movement, improving application access control, removing open inbound ports, and enforcing least privilege policies.
Most mentioned Twingate product strengths
VPN alternative built on Zero Trust principles.
Detailed access control lists (ACLs) for granular permission management.
DNS-based routing to simplify resource management across networks.
Complete auditing capabilities to streamline troubleshooting.
Support for multiple authentication methods for flexibility.
Terraform integration for automating infrastructure deployment.
Most mentioned overall Twingate benefits
Simple deployment with a straightforward setup process.
Transparent experience for end-users accessing resources.
Versatility across different network environments.
Stable and secure connections, reported by users.
Cost-effective pricing compared to some competitors.
Fast performance, reducing user issues related to speed.
Drawbacks of Twingate
User experience: Interface reported as sparse and not logically organized.
Support limitations: Difficult to get support without opting for higher-tier plans.
Network stability: Occasional connectivity issues from users in different regions.
Complex installation process: Client setup involves scripts that can complicate troubleshooting.
Admin interface limitations: Lacks bulk resource creation and editing, making onboarding tedious.
Disclaimer: This review is based on third-party user reviews from Gartner and G2, accessed on June 6, 2025. NordLayer is not responsible for the accuracy or completeness of competitor information, which may change over time.
Now, let’s look at Twingate alternatives.
1. NordLayer
NordLayer overview
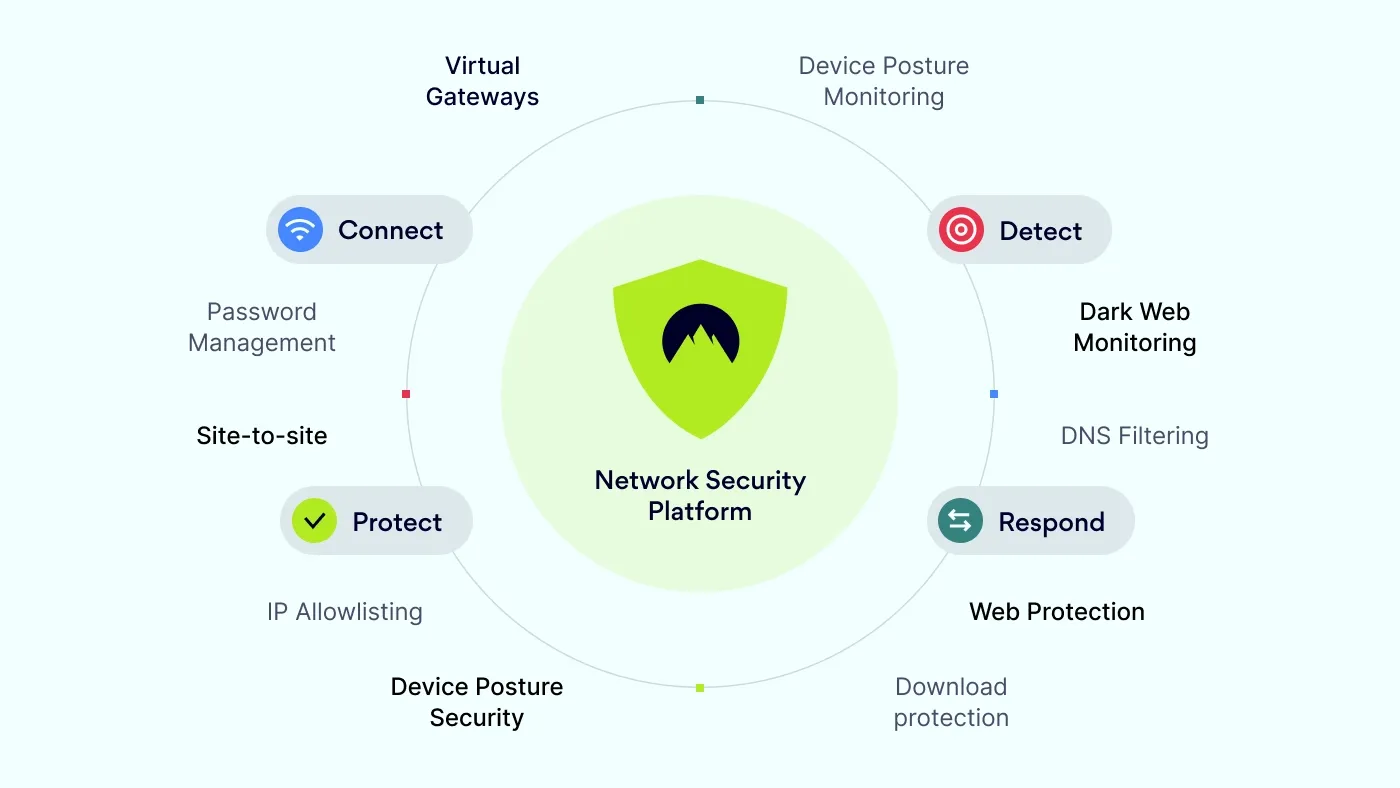
NordLayer is a toggle-ready network security platform designed to connect, protect, detect, and respond to threats. It’s built on NordVPN’s trusted security standards, enabling seamless integration into your existing network infrastructure. NordLayer emphasizes quick implementation, strong threat protection, and responsive support.
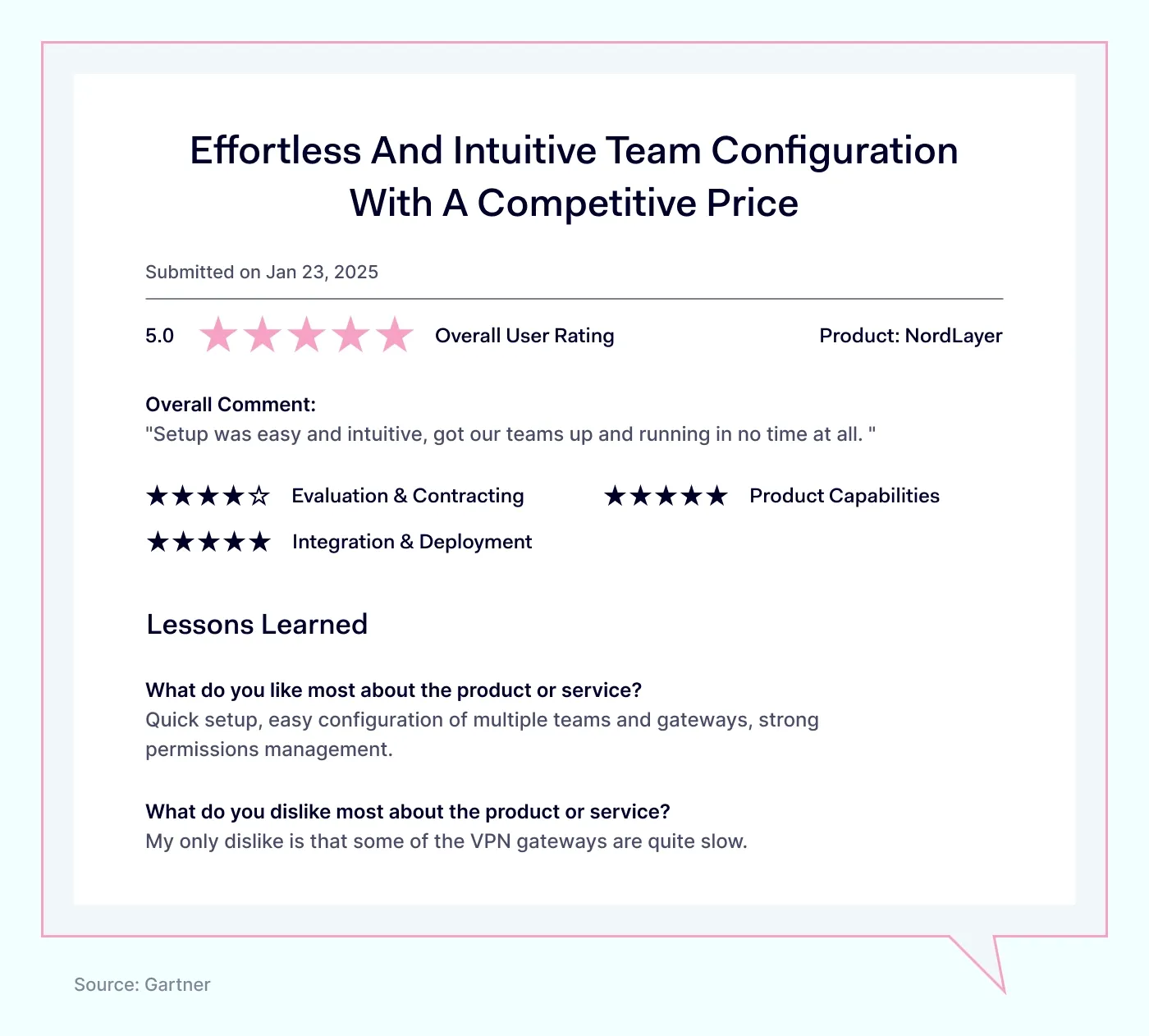
Most mentioned NordLayer product strengths
Here are the top strengths users mention most:
Secure remote access, helping teams safely connect from anywhere.
Centralized control, simplifying the management of network security from one place.
Threat detection, quickly spotting and responding to potential issues.
Automatic reconnection with Auto-connect and Always On VPN features.
Most mentioned overall NordLayer benefits
Users frequently highlight these benefits:
Responsive support, providing quick and precise assistance whenever issues occur.
Fast speeds, maintaining reliable connections even during peak hours.
An easy setup process, taking only about 5 minutes to install and use.
Multi-platform compatibility, working easily across various devices and operating systems.
A simple implementation process as a user-friendly solution.
What makes NordLayer unique?
According to NordLayer’s website, the platform offers robust Zero Trust Network Access (ZTNA) features as well as traditional VPN functionality, emphasizing that these technologies complement each other to strengthen overall security.
NordLynx VPN protocol, providing extremely fast connections.
Browser Extension, offering quick and easy protection when browsing the internet.
Web Protection, actively blocking malicious websites and online threats.
Drawbacks of NordLayer
Users noted these occasional limitations:
Brief connection drops or speed issues, especially when switching between servers.
License adjustments require support, meaning licenses can't be reduced directly by the user.
Limited language support, with certain languages like Spanish currently unavailable.
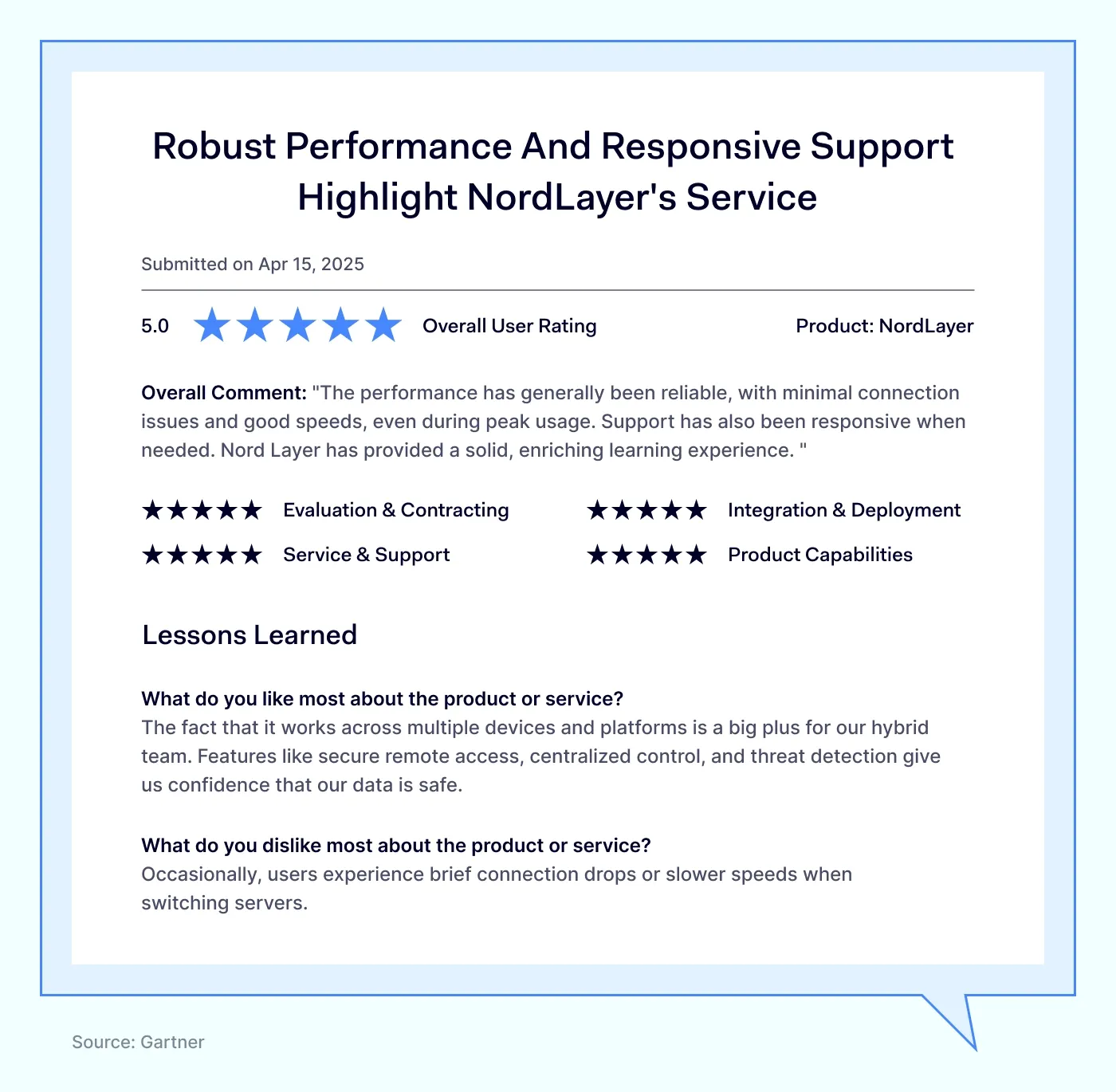
NordLayer reviews
NordLayer receives strong positive feedback as an SSE provider that contributes to the SASE framework. Users appreciate its effective security combined with straightforward usability.
NordLayer is rated:
4.6 out of 5 on Gartner, a top resource for trusted tech reviews.
4.3 out of 5 on G2
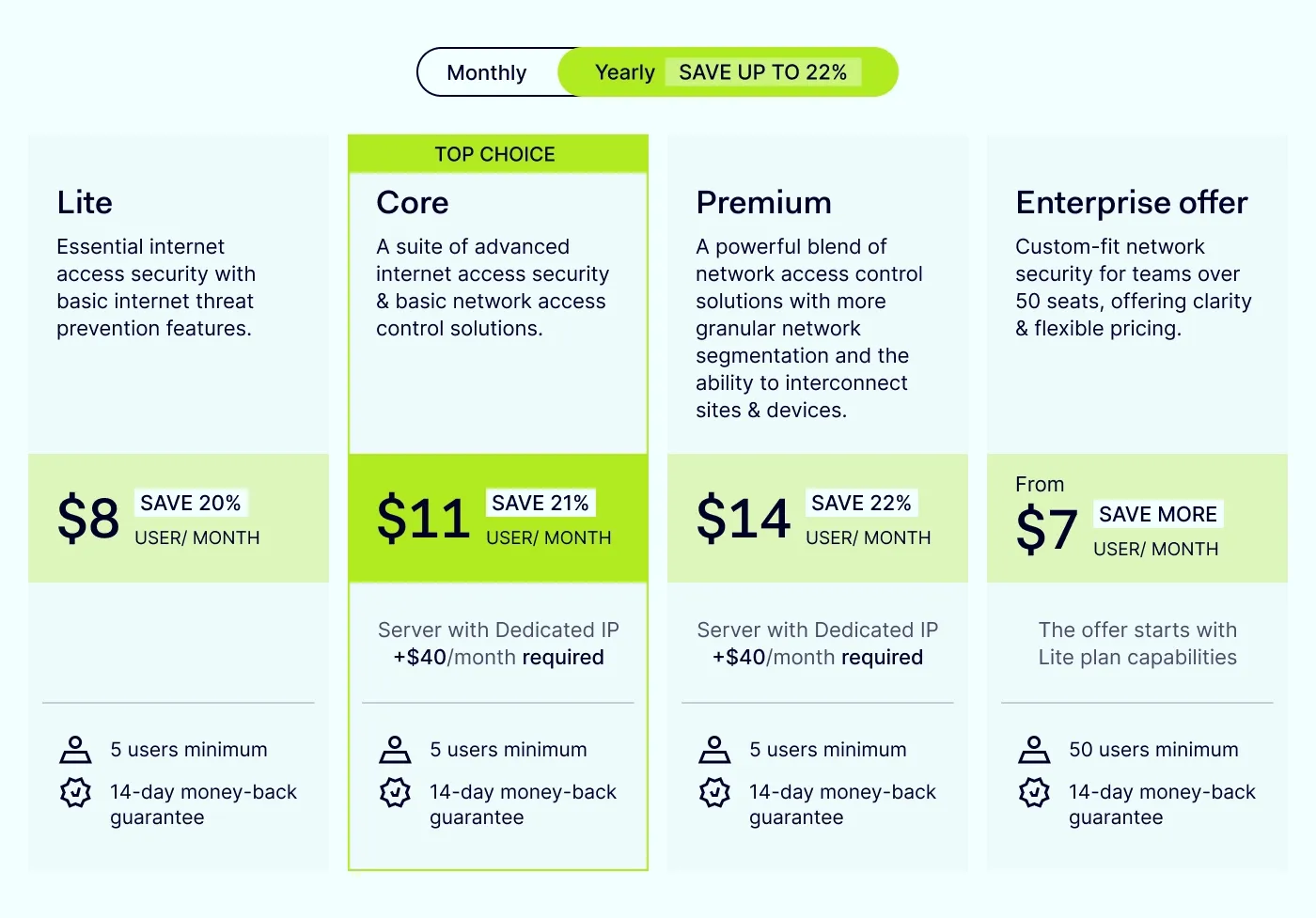
NordLayer pricing
NordLayer offers several pricing plans, all including features such as:
Server speeds up to 1 Gbps.
Shared gateway locations in over 40 countries.
Automatic user logout after a set period (Session Duration Control feature).
Security features include Web Protection, multi-factor authentication (MFA), Always On VPN, Download Protection, and Single Sign-On (SSO).
Support for multiple VPN protocols: NordLynx, OpenVPN (UDP), and OpenVPN (TCP).
NordLayer plans require a minimum of 5 users per organization.
Disclaimer: This information is based on NordLayer’s website and third-party user reviews from Gartner and G2, accessed on June 6, 2025. NordLayer aims to provide accurate and up-to-date information but is not responsible for any inaccuracies from third-party sources.
2. Check Point Harmony SASE (formerly Perimeter 81)
Overview of Check Point Harmony SASE
Check Point Harmony SASE markets itself as a unified SASE platform that combines security and network management into a single solution. According to Check Point, it simplifies how organizations provide secure access to cloud resources, applications, and remote networks from one centralized place.
Most mentioned Harmony SASE product strengths
These are the strengths users most commonly highlighted:
A high malware blocking rate prevents threats effectively.
Robust threat prevention provides thorough protection against various cyber threats.
Unified security and network management reduces complexity by centralizing security functions.
Smooth cloud VPN connectivity simplifies secure remote access.
Reliable Zero Trust Network Access (ZTNA) and secure web gateway features enable user authentication and access control.
Integration with third-party SD-WAN providers like Azure and Cisco ensures flexible network management.
Most mentioned overall Harmony SASE benefits
Users often mentioned the following benefits:
Easy deployment simplifies initial setup.
Effective multi-cloud integration allows easy management across cloud platforms.
High scalability supports from small to large organizations.
Reliable, layered security protects against multiple types of cyber threats.
Continuous protection runs without interrupting user workflows.
Automated policy synchronization simplifies managing security policies.
Drawbacks of Harmony SASE
Users reported the following concerns or limitations:
Complex initial setup requires substantial time and expertise.
Higher pricing compared to similar solutions.
Lack of an intuitive search feature forces administrators to remember exact terms.
Limited customization options for dashboards and the user interface.
Non-transparent pricing structure complicates budgeting decisions.
Inconsistent customer support reported in users' experiences.
Policy tuning requires advanced knowledge, making ongoing management challenging.
Limited AWS Transit Gateway integration requires extra modules.
Lack of advanced automation features like a kill switch or a comprehensive API.
Designed mainly for enterprises prioritizing security, often needing expert-level configuration.
Disclaimer: This review is based on third-party user reviews from Gartner and G2, accessed on June 6, 2025. NordLayer is not responsible for the accuracy or completeness of competitor information, which may change over time.
Related articles

Anastasiya NovikavaJul 4, 20247 min read

Anastasiya NovikavaJul 26, 20257 min read
3. Tailscale
Tailscale overview
Tailscale describes itself as a modern VPN solution and a secure alternative to traditional corporate VPNs, built on the WireGuard protocol. It creates secure mesh networks, enabling devices to communicate directly rather than through central servers.
Most mentioned Tailscale product strengths
Users frequently highlight these strengths:
Powerful access control policies (ACLs) enable detailed permission management.
Effective auditing features help security teams easily track access and enforce least privilege.
Optimal routing between devices, typically faster than standard self-hosted VPN solutions like OpenVPN or WireGuard.
The device sharing feature, particularly useful for troubleshooting purposes.
Most mentioned overall Tailscale benefits
Commonly noted benefits by users include:
Easy setup process.
Fast connection speeds across the network.
Simple onboarding experience for new users.
Wide platform support, compatible with many operating systems.
High scalability, suitable for businesses of varying sizes.
Drawbacks of Tailscale
Users noted these limitations:
Dependence on tailnet DNS names complicates integration with existing services.
ACL configuration could be improved for greater ease of use.
Lack of a multi-tailnet feature, limiting flexibility when managing separate environments.
No support for arbitrary WireGuard exit nodes, reducing options for advanced networking scenarios.
Headscale setup requires a third-party admin console, adding complexity.
iOS app needs substantial improvements for a better user experience.
Disclaimer: This review is based on third-party user reviews from G2, accessed on June 6, 2025. NordLayer is not responsible for the accuracy or completeness of competitor information, which may change over time.
4. Zscaler Internet Access
Zscaler Internet Access overview
Zscaler Internet Access (ZIA) is a cloud-native Secure Web Gateway (SWG). According to Zscaler, it protects users, data, and devices by inspecting encrypted web traffic and enforcing Zero Trust security. The solution is designed to replace traditional hardware-based firewalls with a fully cloud-based model.
Most mentioned Zscaler Internet Access product strengths
Here are the strengths users often highlight:
Effective web security, catching threats like malware, phishing, and viruses.
Accurate URL filtering for better control over user access.
Detailed access control, allowing rules based on user roles, device types, and locations.
Detailed activity logs, useful for investigating security incidents.
Real-time threat detection, helping to enforce security policies immediately.
User activity monitoring, providing visibility into web usage.
Most mentioned overall Zscaler Internet Access benefits
Users commonly mention these benefits:
Simple agent installation and removal.
Detailed device information, showing user status and device health clearly.
Fast and effective tech support, resolving issues promptly.
Easy-to-use admin interface, simplifying day-to-day management.
Drawbacks of Zscaler Internet Access
Users pointed out these limitations:
Internet speed reduction, slowing down browsing or application performance.
Limited choice of data centers, complicating SD-WAN integration.
Connectivity issues, disrupting work on unstable internet connections.
Conflict with other VPN software, causing failures when running multiple clients.
Aggressive security policies, sometimes blocking internet access on external Wi-Fi.
Complex pricing structure, complicating budget planning.
Advanced expertise requirements, complicating initial setup and management.
Limited reporting options, restricting customization for teams.
Overly strict filtering, causing unnecessary blocks on busy days.
Complicated initial setup, making policy tuning harder for new users.
Disclaimer: This review is based on third-party user reviews from Gartner and G2, accessed on June 6, 2025. NordLayer is not responsible for the accuracy or completeness of competitor information, which may change over time.
5. Palo Alto Prisma Access
Palo Alto Prisma Access overview
Palo Alto Prisma Access is a cloud-based solution. According to Palo Alto, it uses Zero Trust principles to secure application access for users and data, connecting with your existing identity providers to make traditional firewall setups unnecessary. It helps teams manage security from a central platform.
Most mentioned Palo Alto Prisma Access product strengths
Users frequently highlighted these strengths:
Strong Zero Trust security, clearly controlling access by user identity, device status, and context.
Comprehensive threat protection, including firewall, malware detection, and data loss prevention.
Seamless integration with SD-WAN, simplifying network visibility and traffic management.
Scalability, suitable for small teams or large global organizations.
Centralized management, simplifying policy management across multiple locations.
Detailed traffic control, clearly identifying apps, users, and content.
Most mentioned overall Palo Alto Prisma Access benefits
Commonly noted benefits include:
Simple policy setup, with straightforward alerts and configurations.
Complete security coverage, including consistent policies and threat prevention.
Easy integration with other Palo Alto products like Panorama and Cortex.
Reliable global performance, supporting remote and hybrid teams smoothly.
Optimized user experience, improving application speeds and connection stability.
Drawbacks of Palo Alto Prisma Access
Users pointed out these limitations:
Complex initial setup, which can be challenging without experienced help.
High cost, making it expensive for smaller organizations.
Steep learning curve, requiring extra training or extensive documentation reading.
Performance delays, causing occasional latency issues in global networks.
Confusing license structure, making subscription selection difficult.
Mixed customer support experiences, sometimes slow or unhelpful; no premium plans.
Limited reporting, with users asking for clearer, more detailed analytics.
Complex troubleshooting, especially with advanced setups.
Slow admin interface, noticeable during large policy changes.
Limited availability of experienced specialists, making local support and fine-tuning tough.
Disclaimer: This review is based on third-party user reviews from Gartner and G2, accessed on June 6, 2025. NordLayer is not responsible for the accuracy or completeness of competitor information, which may change over time.
Choosing the right remote access solution depends on your company's size, budget, and security needs. Most products share common strengths like strong Zero Trust security, easy setup, centralized control, and good scalability. However, they often come with drawbacks such as complex initial configurations, occasional connection issues, and varying levels of customer support quality.
For teams prioritizing a user-friendly solution with quick setup and responsive support, options like NordLayer and Tailscale may be more appealing. On the other hand, Check Point Harmony SASE, Zscaler, and Palo Alto Prisma Access are typically chosen for larger enterprises that need detailed control and extensive security features, but they often come with higher costs and steeper learning curves.
Disclaimer: The information in this article is provided for informational purposes only, is based on publicly available user reviews, product documentation, and online sources accessed on June 6, 2025, and should not be considered definitive or permanent. The views presented reflect aggregated user opinions and are not endorsements.
While we strive for accuracy and completeness, Nord Security Inc. and its affiliates make no guarantees regarding the information's accuracy, completeness, or suitability. We do not undertake, warrant, or represent that any product, or its feature, is or will remain publicly regarded as better or worse than other options, serve any purpose, has mentioned features, benefits, strengths, and limitations for any period of time. Product features, pricing, and other details may change, and we advise readers to verify these directly with vendors. Readers should conduct their own research and seek independent advice before making purchasing decisions. We disclaim liability for any errors, omissions, or actions taken based on this information. The inclusion of competitor products does not imply affiliation or endorsement, and all trademarks mentioned are the property of their respective owners.

Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.