Summary: Understand how lateral movement enables deep network compromise, the techniques behind it, and how to stop it.
Even the most secure perimeter means little once an attacker is inside. That’s where lateral movement begins, and understanding how to prevent lateral movement is a must.
While phishing attacks and endpoint breaches dominate headlines, it's the post-intrusion maneuvering—when threat actors quietly escalate privileges, pivot across systems, and harvest credentials—that often determines the true impact of a breach.
Lateral movement definition
Lateral movement refers to the techniques cyber attackers use after initial compromise to move deeper within a network, often with the goal of gaining access to high-value systems or data. Rather than striking immediately, bad actors exploit internal tools, credentials, and trust relationships to move stealthily between endpoints—avoiding detection while gaining more access and control.
This phase of a cyber-attack is especially dangerous because it unfolds inside the network perimeter, where traditional defenses like firewalls and antivirus solutions offer limited visibility. Detecting lateral movement often requires a combination of behavioral analytics, access control enforcement, and visibility into how users and systems interact—especially around privileged accounts and critical assets like the domain controller.
The attack chain: how lateral movement typically unfolds
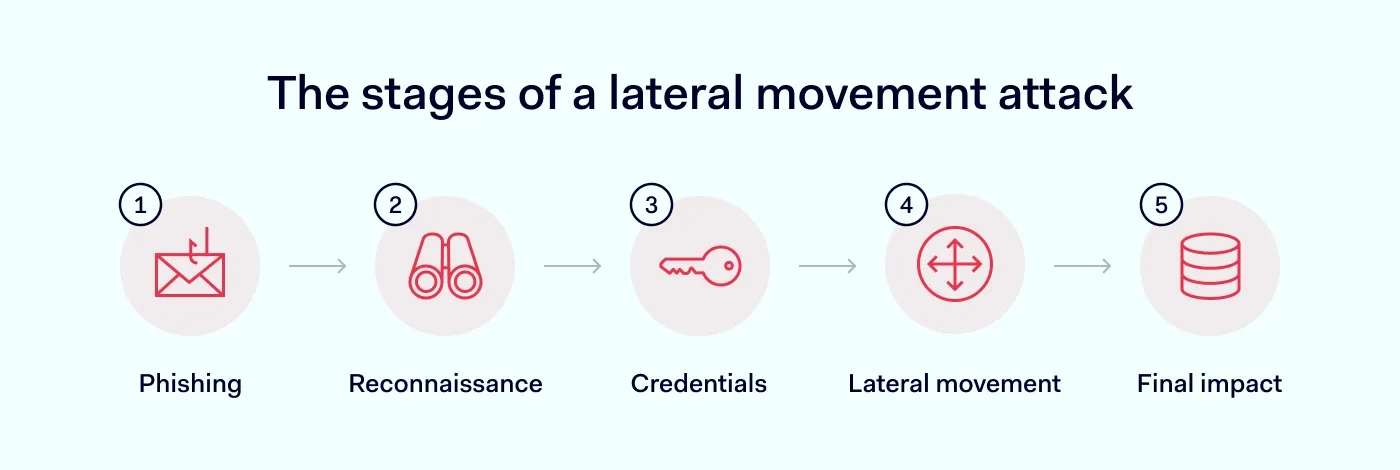
Lateral movement attacks don't happen in a single step—they unfold over a series of calculated moves designed to escalate access and maintain stealth. Here are the stages of lateral movement:
Stage 1: Initial access
The attacker breaches the perimeter through methods like phishing attacks, exploiting remote services (e.g., RDP or VPN), or targeting unpatched vulnerabilities. Once inside, attackers establish a foothold but remain limited in scope—often landing on a low-privilege endpoint.
Common techniques: Phishing, brute-force attacks, vulnerable public-facing apps
Defensive response: Multi-factor authentication, endpoint detection, access control policies
Stage 2: Reconnaissance and enumeration
With a foothold established, the attacker begins mapping the internal environment. They collect information about user accounts, system architecture, network shares, and potential targets such as the domain controller or privileged accounts.
Common techniques: Netstat, PowerShell scripts, built-in OS tools
Defensive response: Least privilege enforcement, intrusion detection systems, user behaviour analytics
Stage 3: Credential dumping and privilege escalation
To move further, malicious actors seek elevated access. They use tools to dump credentials, exploit privilege escalation vulnerabilities, or abuse poorly protected password management systems to access accounts.
Common techniques: Mimikatz, token manipulation, credential reuse
Defensive response: Endpoint detection, password management best practices, privilege segmentation
Stage 4: Lateral movement
Now armed with valid credentials and internal knowledge, the cybercriminal begins accessing various systems in the network. They use lateral movement techniques, such as exploiting SMB, WMI, or remote desktop protocol (RDP) to access additional machines and data.
Common techniques: Pass-the-Hash, Pass-the-Ticket, WMI, RDP, PsExec
Defensive response: Network segmentation, monitor remote services, restrict internal movement with Zero Trust solutions
Stage 5: Target acquisition and impact
The final goal is usually exfiltration, encryption, or business disruption. The attacker reaches high-value assets (e.g., network controller, file servers, customer databases), and carries out their objective—often undetected if lateral movement hasn’t been flagged.
Common techniques: Data exfiltration, ransomware deployment, system sabotage
Defensive response: Threat detection via machine learning, monitoring of unusual activity, real-time response
Key techniques attackers use for lateral movement
Once inside a network, bad actors rely on various lateral movement techniques to gain higher-level access and quietly move between systems. These methods often abuse legitimate tools and protocols, making them difficult to detect:
Pass-the-Hash (PtH): Reuses hashed credentials captured from memory to authenticate on other systems without needing plaintext passwords.
Pass-the-Ticket (PtT): Relies on Kerberos tickets (TGTs or service tickets) to access services across the domain.
Remote Desktop Protocol (RDP): Uses remote services to gain access to other machines via legitimate remote desktop functionality.
Windows Management Instrumentation (WMI): Executes commands and scripts remotely, often without triggering alerts.
PsExec: Runs processes on remote systems—commonly abused for executing commands across hosts.
Credential dumping: Extracts credentials stored in memory or the registry using tools like Mimikatz.
Shared network access abuse: Moves through shared drives, mapped folders, or misconfigured file shares.
Token impersonation: Hijacks access tokens to impersonate users—especially high-privilege accounts.
Internal spear phishing: Sends malicious content to users within the network to steal further credentials or plant malware.
Exploitation of poor password hygiene: Takes advantage of reused or weak credentials, especially when password management practices are lacking.
Related articles

Joanna KrysińskaOct 31, 20249 min read

Agnė SrėbaliūtėNov 6, 20248 min read
Real-world example: SolarWinds attack (2020)
One of the most devastating lateral movement attacks to date occurred during the SolarWinds supply chain breach. After compromising the Orion software update mechanism, cybercriminals gained initial access to multiple US government and enterprise networks.
Once inside, they used credential dumping, token impersonation, and customized lateral movement techniques to silently traverse systems for months—targeting domain controllers and cloud environments.
Estimated impact: ~18,000 organizations received the malicious update
Dwell time: Up to 9 months undetected
Threat group: APT29 (Cozy Bear), linked to Russian intelligence
How to detect lateral movement
Detecting lateral movement is particularly difficult because attackers often mimic legitimate user behavior and exploit trusted internal systems. However, several strategies and technologies can help expose suspicious activity before it leads to a full-blown compromise:
Behavioral analytics: One of the most effective ways to detect lateral movement is to analyze user behavior over time to identify sudden deviations—like a user accessing unfamiliar systems or logging in at odd hours—that may signal compromise.
Endpoint monitoring: Deploy
Endpoint Detection and Response (EDR) tools to track processes, login attempts, and access to sensitive assets. Watch for signs of credential dumping or remote command execution.
Unusual access patterns: Monitor for activity that falls outside normal user roles or workflows— such as PsExec or RDP use between endpoints that don’t typically communicate.
Multi-factor authentication (MFA) alerts: Watch for failed or bypassed MFA attempts, which can serve as early indicators of a lateral movement attack in progress.
Threat detection systems: Use machine learning-based threat detection to flag low-and-slow attacks that traditional defenses might miss. These systems can correlate subtle anomalies across the network to detect lateral movement.
Audit privileged account usage: Closely monitor high-level accounts for unusual activity, especially after initial compromise. Lateral movement often involves attackers attempting to escalate their own privileges and abuse these accounts.
Track remote service usage: Investigate unexpected or unauthorized use of internal remote services, which can be leveraged to pivot across systems.
Shrink the attack surface: While not a detection method in itself, limiting lateral access through segmentation and access control boosts visibility and raises red flags when violations occur.
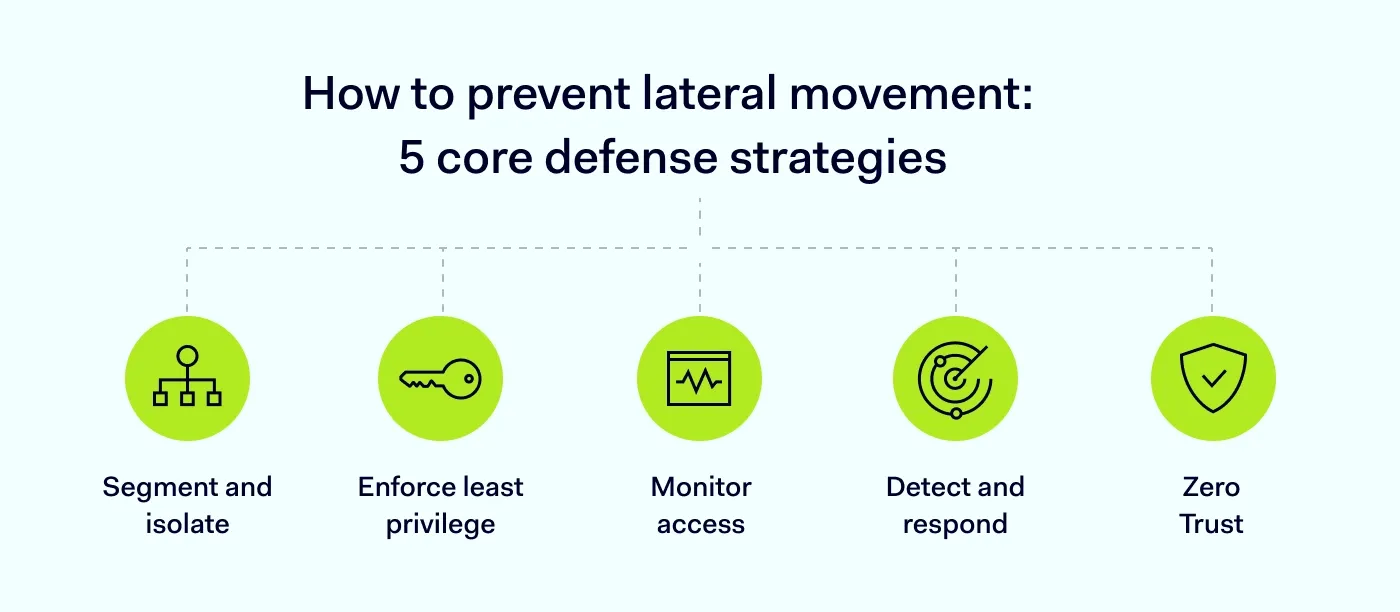
Steps to preventing lateral movement
1. Segment and isolate the network
Flat networks make lateral movement easy. Implement internal segmentation to limit access between departments, teams, and resources. Isolate sensitive assets—like network controllers and critical servers—within protected zones that can only be accessed under strict conditions. Technologies like software-defined perimeters and microsegmentation can help reduce exposure and enforce contextual access boundaries.
2. Enforce least privilege access
Users should only have access to the systems and data they absolutely need. Overprivileged accounts are a key enabler of lateral movement. Apply the principle of least privilege (PoLP) across all identities—users, admins, and services—and ensure privileges are continuously reviewed and revoked when no longer needed.
3. Monitor identity and access
Track who is accessing what, from where, and when. Continuous monitoring of identity and access helps surface abnormal behavior—like a standard user accessing sensitive systems or credentials being used in new geographies. Integrate single sign-on (SSO), strong password policies, and Role-Based Access Control (RBAC) to maintain visibility and reduce risk, and align with network monitoring best practices.
4. Detect and respond in real-time
Lateral movement is often subtle and slow. Use detection tools that combine behavior analysis, anomaly detection, and response automation to spot threats before they escalate. Visibility across endpoints and cloud services is essential to correlate signals and trigger rapid remediation actions.
5. Implement Zero Trust architecture
Adopting a Zero Trust approach ensures no user or device is inherently trusted—even inside the network. Authenticate every session, verify device posture, and validate contextual risk before granting access. This architecture effectively disrupts lateral movement paths by requiring continuous verification.
NordLayer’s role in lateral movement defense
Preventing lateral movement requires more than visibility—it demands control over how users interact with your network from the inside out. NordLayer is designed to give IT teams that control, combining intelligent access policies with modern network architecture to block lateral paths and contain threats before they escalate.
A key part of this strategy is segmentation. With NordLayer’s network segmentation tools, organizations can create secure, logically separated environments that limit movement between users, departments, and critical infrastructure. Whether your team is fully remote, hybrid, or distributed across multiple locations, segmentation ensures attackers can’t freely pivot once inside.
Identity and access management is just as essential. NordLayer supports granular access controls and SSO integration, allowing administrators to define exactly who can reach what—and under which conditions. This level of control makes it easier to flag anomalies, shut down credential abuse, and enforce least-privilege policies across the board.
At the core of NordLayer’s approach is Zero Trust Network Access (ZTNA), which eliminates the assumption that anything inside your network should be trusted by default. Every user, device, and request is authenticated continuously, with access granted only if context, location, and risk level align. This disrupts the internal freedom lateral movement attacks rely on—stopping threats at the access point, even after initial compromise.
For organizations, the stakes are high: lateral movement attacks don’t just steal data—they threaten operations, reputation, and compliance. NordLayer empowers IT leaders, CISOs, and security architects to go beyond detection and actively architect environments that are resilient by design. When attackers can’t move freely, they can’t succeed—and that’s where NordLayer gives you the edge.
Contact sales to see how NordLayer can help your organization.

Aistė Medinė
Editor and Copywriter
An editor and writer who’s into way too many hobbies – cooking elaborate meals, watching old movies, and occasionally splattering paint on a canvas. Aistė's drawn to the creative side of cybercrime, especially the weirdly clever tricks scammers use to fool people. If it involves storytelling, mischief, or a bit of mystery, she’s probably interested.