
Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.
Data & information security
Summary: Most leaks happen from human error and misconfigurations. Limit damage with least privilege access, strong policies, and monitoring.
To prevent data leaks, companies must secure access control to sensitive data, monitor user behavior, and control how information moves across devices, networks, and cloud or SaaS platforms.
But while that sounds simple, it’s a bit like saying, “To bake a perfect cake, just mix the right ingredients and put it in the oven.” The truth is, the recipe for effective data leakage prevention is complex, the timing is critical, and one wrong move can turn your prized creation into a frustrating, burnt mess.
In cybersecurity, that mess is a catastrophic event with financial, legal, and reputational consequences.
This guide will walk you through the real recipe, moving beyond the simple summary to give you the actionable steps you need to protect your business.
Let's clear something up right away, because words matter in cybersecurity. You’ve probably heard the terms “data leak” and “data breach” used interchangeably, but they’re not the same thing.
A data leakage is the accidental or intentional exposure of sensitive information. It’s the open window, the unlocked door. It’s when a company’s internal sensitive data becomes accessible to people who shouldn't have access to it. Maybe an employee misconfigured a cloud server, leaving a database of customer data open to the public internet. Or perhaps someone accidentally emailed a spreadsheet of employee salaries to the entire company instead of just the HR department. The data is out there, but it hasn't necessarily been stolen yet.
A data breach, on the other hand, is the confirmed theft. It’s when a cybercriminal walks through that unlocked door and steals the TV. A breach is an active, malicious event where an attacker exploits a leak to infiltrate a system and exfiltrate confidential data. So, a data leakage can lead to a data breach, but they aren't one and the same.
The key takeaway? Preventing a breach often starts with preventing the initial data leakage. Plug the holes, and the intruders have a much harder time getting in.
“Okay,” you might be thinking, “so some data got out. Is it really that big of a deal?”
In a word: yes. In a few more words: it’s a multi-headed hydra of a problem that can cripple a business from every angle.
Ignoring the threat of data leakage is like ignoring a crack in your foundation—it might seem small at first, but it will eventually compromise the entire structure. This is why a robust data leakage prevention strategy is not just an option, but a necessity.
Here’s why you have to take this seriously:
Ultimately, a strong data leakage prevention plan isn’t just an IT issue; it's a fundamental business continuity strategy.
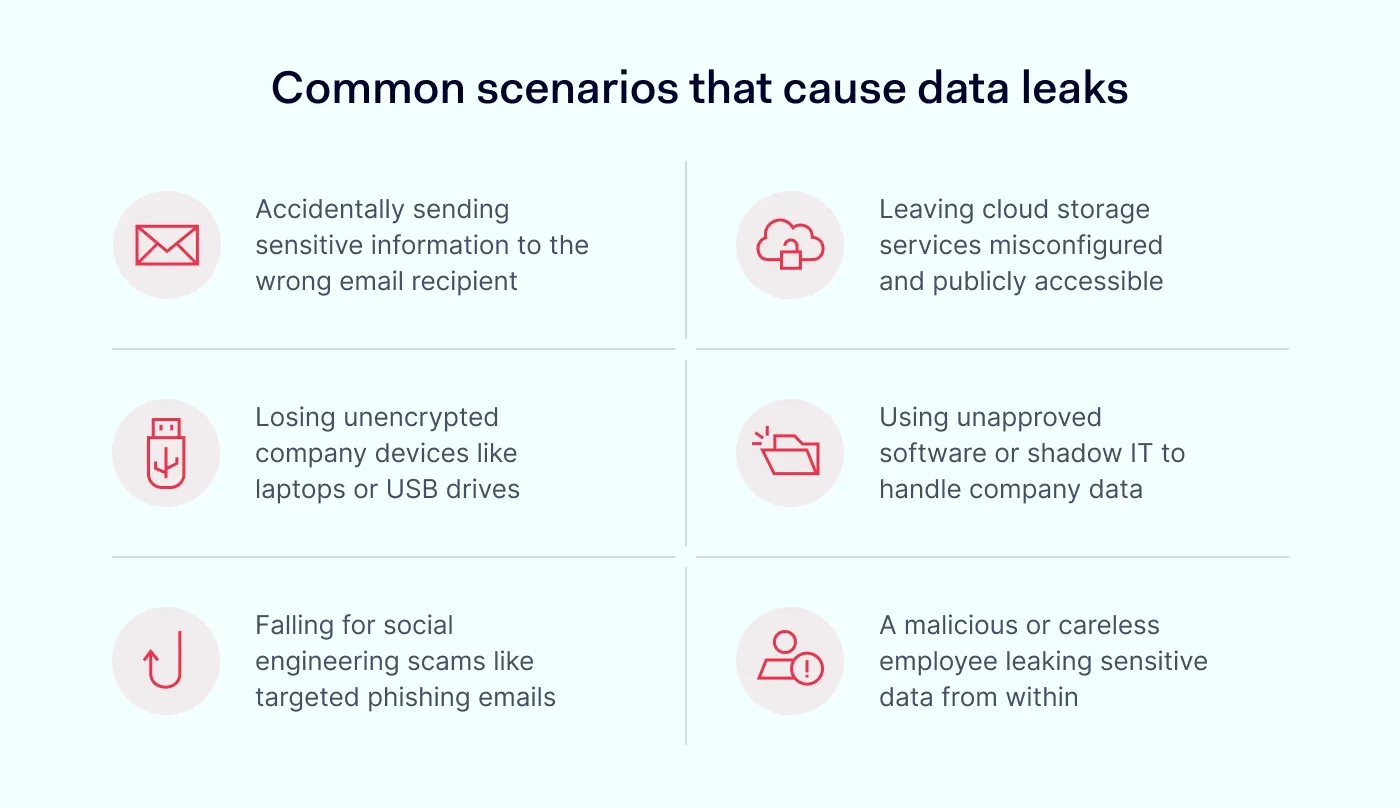
Data leaks aren’t always the work of a shadowy cybercriminal in a hoodie. More often than not, they happen in mundane, everyday situations. 74%–95% of incidents involve the human element. Here are some of the most common culprits:
When we talk about leaked data, it’s not all created equal. The severity of a leak depends heavily on what was exposed. The most valuable and damaging types of sensitive data fall into three main categories.
This is often the crown jewel for cybercriminals. Customer data includes Personally Identifiable Information (PII) like names, addresses, and social security numbers. It can also include financial information like credit card numbers or protected health records. Leaking this type of sensitive data not only triggers massive regulatory fines but also causes direct harm to the individuals whose privacy has been violated.
This category covers the internal workings of your business. Think of financial reports, strategic business plans, employee records (salaries, performance reviews), and legal documents. When this type of sensitive information leaks, it can be used by competitors to undercut your business, by lawyers in legal disputes, or by attackers to craft even more convincing phishing schemes.
For tech companies and any business that develops its own technology, source code is the blueprint of their intellectual property. Leaking source code can expose proprietary algorithms and security vulnerabilities that rivals or cybercriminals can exploit data leaks with, potentially destroying a company’s core value proposition.
Understanding how data leaks happen is crucial for building the right defenses. We can generally sort leaks into three buckets based on intent.
This is the most common type of data leakage. It’s pure human error. No malice, no evil plan—just a mistake. This includes everything from sending an email to the wrong recipient and losing a work laptop to misconfiguring a cloud database. While unintentional, the consequences are just as severe, making a strong data leak prevention framework essential.
This is when an employee or contractor with legitimate access to sensitive data intentionally steals and leaks it. Their motives can range from financial gain (selling the data on the dark web) to revenge (a disgruntled employee wanting to harm the company). These are particularly tricky to stop because the person already has authorized access; the challenge is detecting when they use that access for nefarious purposes.
This is the classic scenario where external attackers are actively trying to breach your defenses. They might exploit a software vulnerability, use stolen credentials, or trick an employee into giving them access. Once inside, they hunt for valuable data to steal. Their goal is to turn a data leakage (a vulnerability) into stolen data (a breach).
Alright, enough with the doom and gloom. Let's get to the good stuff: the actionable plan. Knowing how to prevent data leakage isn't about finding a single magic bullet. It’s about building layers of defense—a strategy essential for effective data leak prevention.
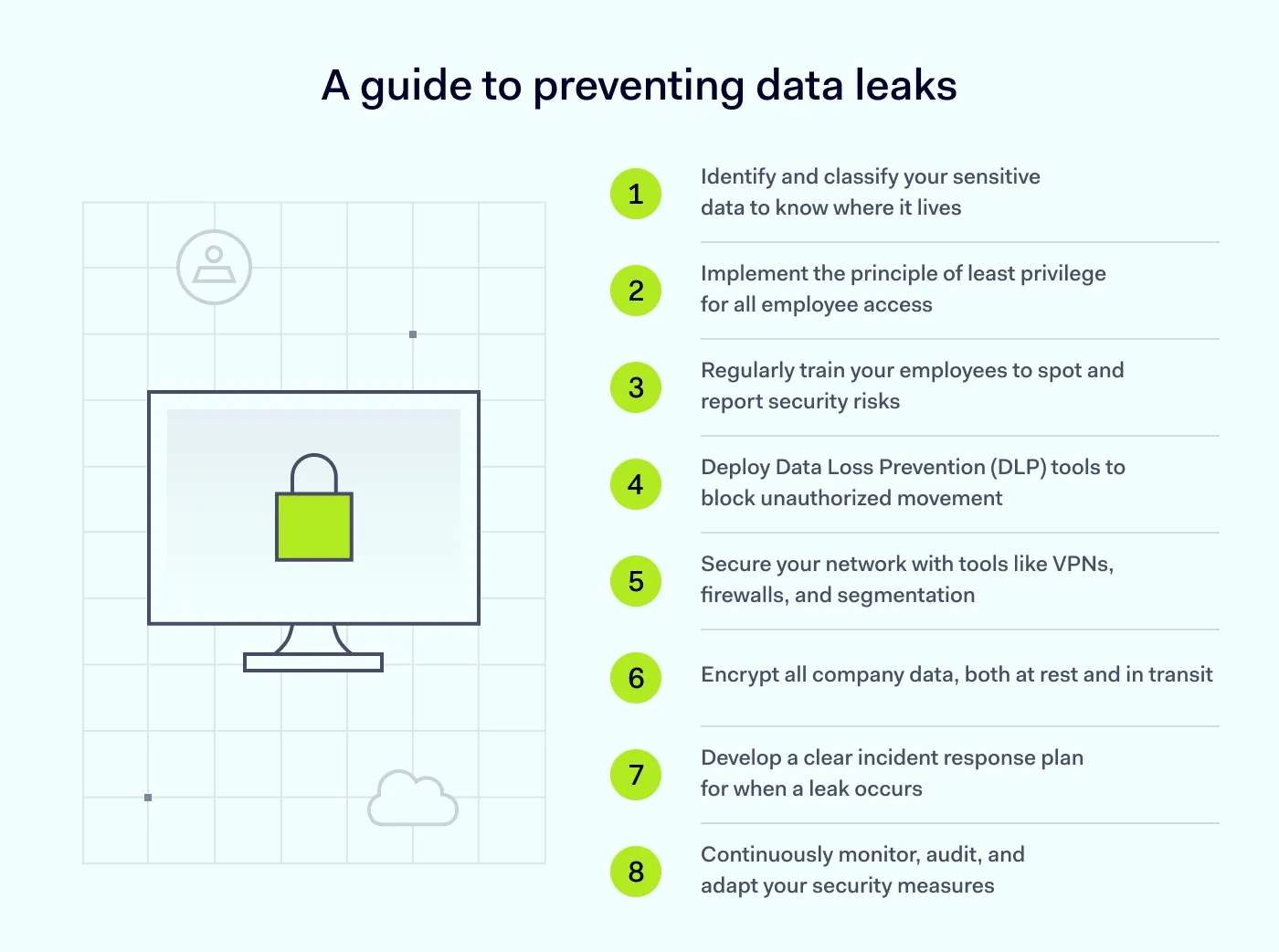
You can't protect data if you don't know what you have or where it is. The first step is to conduct a data discovery and classification audit.
This is a cornerstone of modern security. PoLP means giving employees the minimum level of access control necessary to perform their jobs. This extends beyond simply restricting access to different systems (for example, an accountant doesn't need source code, and a developer doesn't need payroll files) to also cover varying rights and roles within the same platform.
For instance, a standard user might not be able to install new applications or change security policies, while an “administrator” or “owner” role within the same system can. This shrinks the potential attack surface by limiting both where a user can go and what they can do, making it a key pillar of any data leakage prevention plan.
Your employees are your first line of defense. Regular, engaging security awareness training is non-negotiable. Teach them how to spot phishing, use strong passwords and MFA, handle sensitive data properly, and report suspicious activity. Make it interactive, ongoing, and part of your culture.
This is where technology enforces your policies. Data Loss Prevention (or DLP) solutions are tools that monitor, detect, and block the unauthorized movement of sensitive information. A good DLP tool can prevent users from emailing confidential files externally or copying sensitive data to unapproved locations. A DLP system is a critical technological layer for any serious data leakage prevention strategy.
Your network is the highway for all your data. Securing network access is critical.
Encryption scrambles your data into an unreadable format. If encrypted sensitive data is leaked or stolen, it's essentially useless. Choose only reliable encryption products and encrypt data in transit and at rest. For especially sensitive workloads, consider emerging “data-in-use” protections like confidential computing.
Prevention is the goal, but perfection is impossible. You need a plan for when a data leakage happens. An incident response plan outlines containment, eradication, and recovery, as well as communication with stakeholders, customers, and regulators. Practice it so your team is ready.
Security is an ongoing process. You must continuously monitor your systems for unusual activity, conduct regular audits and penetration tests to find new vulnerabilities, and adapt your appropriate security measures as threats evolve.
At NordLayer, we help companies tackle data leakage head-on by implementing modern zero-trust solutions. This framework operates on a “never trust, always verify” principle, treating every access request as a potential threat until proven otherwise. By requiring strict verification for every user and device, our solution provides the granular access control necessary for a robust data leakage prevention strategy.
Recognizing that many risks now originate in the web browser, we're taking endpoint security a step further with our upcoming Business Browser. This tool is purpose-built for data leak prevention, giving you direct control over how users interact with web-based applications and sensitive data. It provides a crucial layer of data loss prevention (DLP) right where work happens most. Secure your company's most-used application and join the waiting list for the NordLayer Business Browser today!
Subscribe to our blog updates for in-depth perspectives on cybersecurity.