It is often tough for both IT admins and companies to enable remote access. IT admins struggle to establish secure connections and manage remote personal devices. Companies, on the other hand, worry about security risks, high costs, and keeping up with regulations.
These challenges are even greater for businesses with strict device security policies that require devices to stay in the office while allowing remote working. Organizations that outsource their workforce also face increased security risks of data breaches and difficulty controlling devices.
That's why remote work security is key. In this article, we’ll explain how NordLayer’s Cloud LAN functionality secures authorized device access, protects data with encryption, and simplifies remote device management.
What is remote work security?
Securing a remote workforce means putting strong security measures in place to protect company devices and company data from being accessed by the wrong users. This strategy helps protect your data and systems when employees, including outsourced or temporary ones, work from outside the office. That’s why super strict device security is a must. This way, you can prevent unauthorized access and ensure that only approved devices can connect to the company network.
The challenge is finding a balance between strict security and remote work. Businesses can use security measures that fit remote setups. One practical approach is implementing solutions that control device access and ensure compliance with security policies. In other words, you need to cover all bases while securely enabling remote device access.
3 pillars of remote work security
To keep your employees, data, and systems safe, focus on three main areas. These key elements will help you stay ahead of potential threats and ensure smooth remote operations:
Pillar 1: Securing access to SaaS applications
Remote work security is all about protecting collaboration and productivity tools, along with any other tools that store sensitive business, employee, or customer data. Make sure that only authorized users can access them.
Pillar 2: Defense against web threats
Safeguard against security risks from general web access, such as malware and phishing attacks, by implementing a Secure Web Gateway (SWG) framework.
Pillar 3: Managing applications via ZTNA
Manage company software, whether hosted on-premise or in the cloud, using solutions that contribute to Zero Trust Network Access (ZTNA) for secure and controlled access.
By covering these bases, you'll keep your remote work environment secure and running smoothly.
Most common remote work security risks
As remote device access becomes more common, businesses face several critical threats. From unauthorized access to phishing and malware infections, these risks can severely impact security. Weak password policies, regulatory non-compliance, unmanaged personal devices, and insecure cloud access contribute to the growing list of challenges.
To put it plainly, it’s like trying to fix a flat tire with a piece of string—it's not going to hold up without a proper solution. Let’s have a closer look at these challenges:
Unauthorized access
One of the biggest risks businesses face with remote work is unauthorized access, which often results in data breaches.
Phishing
Attackers send fake messages and emails to trick users into revealing confidential information using social engineering techniques.
Malware infections
Remote personal devices are always at risk if not well-protected. If a remote device gets malware, it could infect the entire network and compromise far more sensitive data than expected.
Weak password security
Poor password policies can lead to unauthorized access.
Unsecured cloud and SaaS access
Using insecure alternatives to VPN endangers your data security and exposes it to cyber-attacks.
Best practices for remote work security
Can employees (and their devices) be 100% secure while working remotely? Can they have secure access to company resources? It's tough, but following these steps can help reduce security risks.
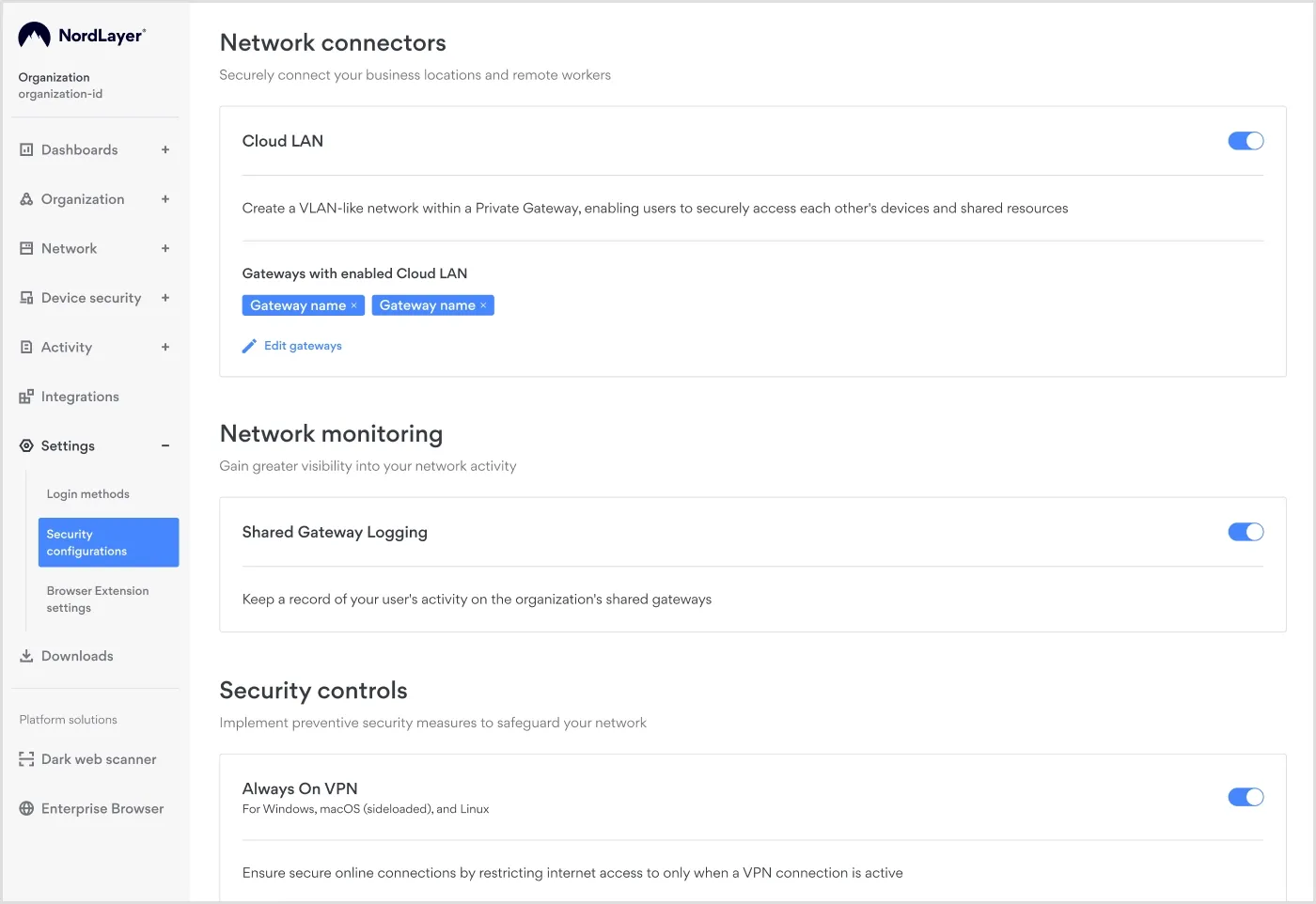
Choose Cloud LAN for remote device control
With Cloud LAN, IT admins create a secure connection policy that provides virtual access to a specific company device. Cloud LAN makes managing diverse devices easier. For example, it helps troubleshoot devices, install or delete apps, or change a remote user’s laptop settings. It also ensures compliance with company security policies and industry regulations.
What’s great about using Cloud LAN is that it is intuitive and user-friendly. To enable it, simply add gateways in the Cloud LAN settings in the Control Panel.
Next, to set up secure connections, just connect to the same gateway, name your devices, and make a few configuration changes. choose a Virtual Private Gateway and click Enable.
Once you enable the feature for your Virtual Private Gateway, a local network (LAN) will be set up between all devices connected to that private gateway. This makes it easy for team members to collaborate on projects or share files securely.
Boosting remote work security
Cloud LAN allows you to create secure connection policies to access company resources easily. What’s the best way to create an even more robust security framework that protects remote work environments? Combine Cloud LAN with multi-factor authentication (MFA). These two solutions contribute to the Zero Trust Network Access (ZTNA) framework and enhance overall security.
MFA adds an extra security layer by requiring multiple verification factors for access. Cloud LAN ensures that only authenticated and authorized users can access specific applications and resources.
Cloud LAN and RDP/VNC: Why encryption matters
Virtual Network Computing (VNC) allows users to remotely access and control another computer's desktop interface over a network. RDP, or Remote Desktop Protocol, developed by Microsoft, lets users connect to another computer over a network. With RDP, you can see and interact with the remote computer’s desktop as if you were sitting right in front of it.
Now, what’s the difference between Cloud LAN, RDP, and VNC? Cloud LAN uses robust encryption protocols, ensuring data integrity and confidentiality during remote access. It also integrates VPN technology, adding extra protection. This setup protects sensitive data and prevents unauthorized device access. That’s why Cloud LAN is a better choice than basic RDP and VNC.
It also helps you avoid “naked,” unprotected connections and gives you peace of mind when it comes to secure remote device access.
How NordLayer can help
NordLayer offers solutions to secure your remote workforce, integrating advanced security measures like encrypted connections, multi-factor authentication (MFA), Virtual Private Network (VPN) technology, and Identity and Access Management (IAM) to ensure robust protection against cyber threats and data breaches.
Cloud LAN is key to securing remote work environments. By addressing common risks and following best practices, businesses can protect their sensitive data and keep operations running smoothly in an increasingly remote world.
Want to try out our adaptive and user-friendly solutions? Contact our team to find out more.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she has dedicated her life to simplifying complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.