
Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.
Cybersecurity
Summary: Branch offices need strong defenses. Use VPNs, segmentation, and SASE to build a secure remote site connection.
Your business is growing. That's fantastic! But with that growth comes complexity, especially when you start opening new branch offices or managing teams in different locations. Suddenly, you’re not just protecting one office; you're trying to defend dozens.
Ensuring a secure network connection at a remote site is a fundamental business requirement. One weak link in a remote location can compromise your entire corporate network.
Figuring this all out can feel overwhelming. You've got acronyms like VPN, ZTNA, and MPLS flying around, and all you want is a straightforward way to keep your data safe and your business running.
This guide will cut through the noise. We'll break down the challenges, explore the best practices, and introduce modern solutions that make securing your remote sites simpler and more effective than ever before.
Imagine your branch office is a digital extension of your headquarters. It accesses the same sensitive data, from customer information and financial records to intellectual property.
The stakes are high:
In short, securing your remote sites is not an extra; it's part of your business's survival strategy.
To understand how to secure these connections, we first need to understand how they’re built.
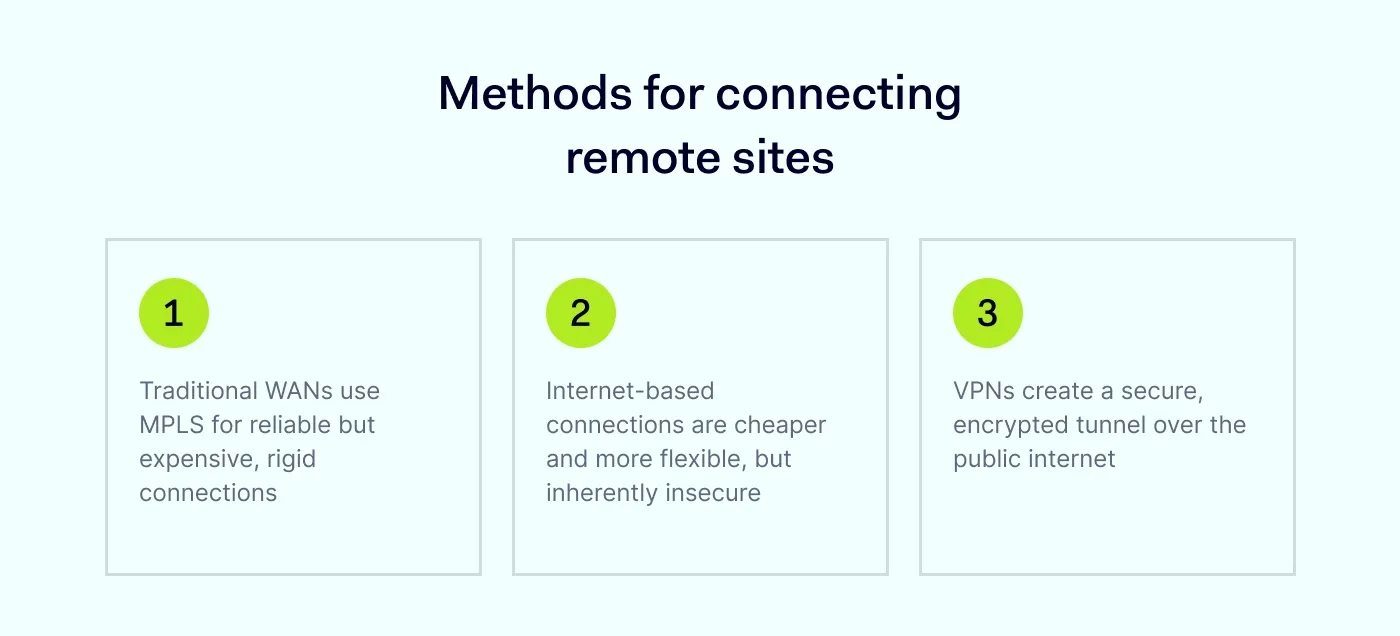
For a long time, the gold standard for connecting multiple offices was a Wide Area Network (WAN), often built using Multi-Protocol Label Switching (MPLS). MPLS uses a provider-managed backbone that isolates your traffic from the public internet, but it isn’t a dedicated private circuit and doesn’t encrypt by default.
Today, most businesses use standard business internet connections (broadband, fiber, or even 4G/5G LTE) to connect their remote sites. It's the “public road system” for data.
This is where the virtual private network (VPN) proves its value. A VPN creates a private, encrypted connection over the public internet. It essentially builds a secure tunnel for your data to travel through, shielding it from anyone who might be snooping around. This has long been the go-to method for creating a secure connection for remote work and site-to-site links.
Connecting remote sites is one thing; securing them is another. As your business expands, you'll run into several common, and frankly, frustrating challenges:
Feeling a little overwhelmed? Don't be. You can improve your network security with a set of proven best practices. Here are seven fundamental steps to lock down your remote connectivity.
A firewall sits at the entry point of your remote site's network and inspects all incoming and outgoing traffic. It blocks malicious traffic based on a set of predefined security policies. A modern, next-generation firewall (NGFW) can even identify specific applications and threats, which gives you much more granular control.
A password is no longer enough. You must implement multi-factor authentication (MFA) wherever possible.
MFA requires users to provide two or more verification factors to gain access, such as a password and a code from their smartphone. This means that even if a cybercriminal steals a password, they can't get in.
Just as important is the principle of least privilege (PoLP): users should only be given access to the specific data and applications they absolutely need to do their jobs, and nothing more.
A VPN is a foundational tool for secure remote access. It creates that essential secure tunnel between your remote site and the corporate network. There are two main types:
This is the modern evolution of network security. The old model was "trust but verify": once on the traditional VPN, you could access large parts of the network. The Zero Trust model is "never trust, always verify."
With ZTNA, access is not granted based on being on the "trusted" network. Instead, every single request to access an application is verified. A user's identity, device health, and location are all checked before they are granted a secure connection to only that specific resource.
This dramatically shrinks the attack surface. If a breach does occur, it's contained to that one application, not the entire network.
This sounds simple, but it's one of the most critical and often overlooked security tasks. Software developers are constantly releasing patches to fix security vulnerabilities. Failing to apply these updates is like knowing about a broken lock on your door and doing nothing about it. Automate patching and updates whenever possible across all your remote locations.
Don't put all your digital eggs in one basket. Network segmentation involves dividing your corporate network into smaller, isolated sub-networks. For example, you can put your guest Wi-Fi on a separate segment from your sensitive financial data. If one segment is compromised, the isolation prevents the attacker from moving laterally across your network to access more critical assets.
Technology alone is not enough. You need clear, written security policies that every employee understands and follows.
These policies should cover everything from password complexity and acceptable use of company devices to procedures for reporting a suspected security incident. Regular training ensures that your team remains your strongest defense, not your weakest link.
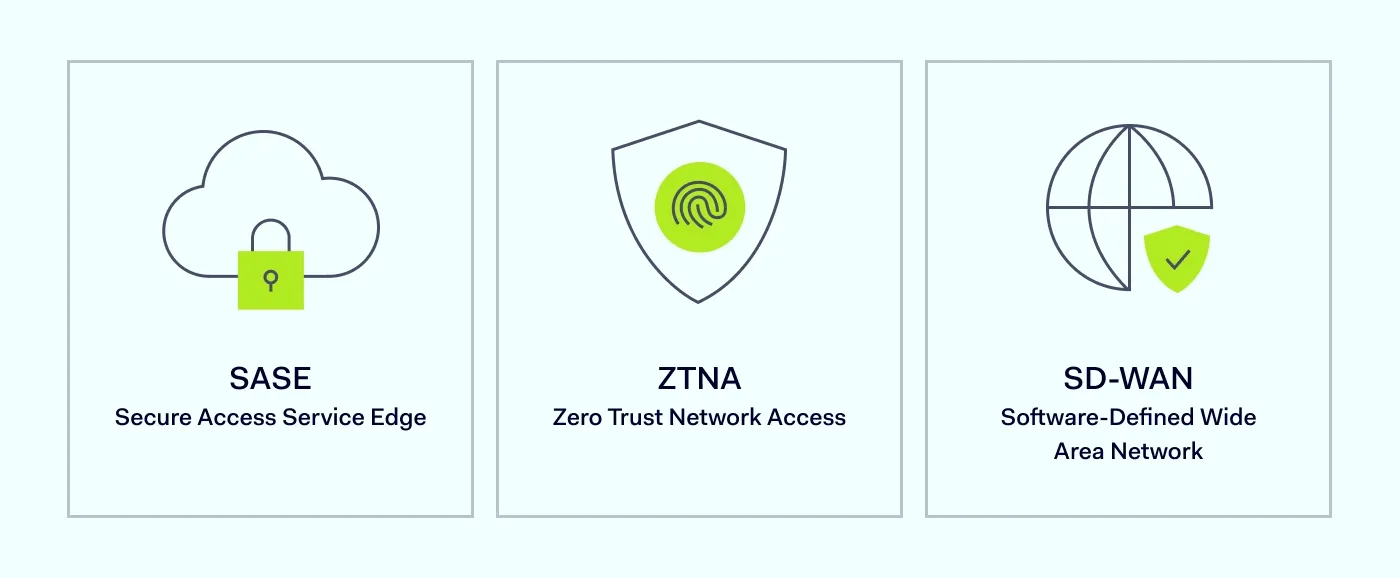
While the best practices above are essential, modern technology offers more integrated and efficient ways to implement them. The industry is moving away from bolting together a dozen different security products and toward unified platforms.
This isn't just theoretical. Businesses across every industry are using these solutions to solve real-world problems.
A retail chain needs to connect thousands of point-of-sale (POS) systems, inventory management terminals, and employee devices across hundreds of stores back to the corporate network. A secure remote access solution ensures that customer credit card data is protected (for PCI DSS compliance) and that daily sales data syncs reliably with headquarters.
A hospital system with numerous outpatient clinics and labs in different locations handles an immense amount of sensitive patient data (ePHI). A secure connection that complies with HIPAA is non-negotiable. ZTNA is particularly effective here: it ensures that a doctor at a clinic can only access the patient records they are authorized to see, and nothing more.
Manufacturing companies have valuable intellectual property (product designs, proprietary processes) and increasingly connected operational technology on their factory floors. Securing the connection to these plants prevents industrial espionage and protects against attacks that could halt production lines and cause millions in losses.
Banks and investment firms with regional branches require an incredibly high level of security for transactions and customer data. A site-to-site VPN or a SASE architecture can provide secure access between branches and data centers.
Navigating the world of network security can be complex, but the right partner can make all the difference. NordLayer offers a secure remote access solution designed to address the challenges of the modern, distributed business.
NordLayer provides a single, unified platform that integrates key security technologies. It’s easy to provide secure access for your entire workforce, whether they are at home, in a branch office, or on the go.
Here's how NordLayer aligns with the best practices we've discussed:
Instead of wrestling with multiple vendors and complex hardware, NordLayer offers an easy cloud-based solution that scales with your business.
With modern security solutions, the lines between these two concepts have started to blur, but they still solve different problems.
A site-to-site VPN creates a secure entry point into a private network. It connects a remote network (like your branch office or a cloud-based server environment) to your private corporate network, such as the one managed by NordLayer.
Once that office network is securely linked, individual employees (remote work users) who are part of the secure network can then access the resources located at that site. In this sense, individuals use the site-to-site connectivity to reach the company's remote physical or cloud-based networks.
So while a remote access VPN traditionally described the individual's connection and site-to-site described the network's connection, they now work together. An individual uses their secure connection to access the central platform, which then routes them to the resources available via the site-to-site link.
A virtual private network is still a crucial tool, especially for creating an encrypted connection. However, a traditional VPN solution is no longer considered the best or most complete solution.
Modern security demands a more granular, identity-aware approach. That's why frameworks like ZTNA and SASE, which often use VPN principles for the connection itself, are now the gold standard, as they add critical layers of access control on top.
For years, AES-256 (Advanced Encryption Standard with a 256-bit key) has been the industry standard for data encryption, and it remains incredibly strong. Modern VPN protocols like OpenVPN and IKEv2/IPsec frequently use it. Newer protocols like WireGuard® (and its derivatives like NordLynx) are also gaining widespread adoption due to their excellent combination of top-tier security and superior performance.
A traditional VPN works like a key to the building. Once you're inside, you can roam many of the hallways.
Zero Trust Network Access (ZTNA) works like a key card that only opens one specific door. It assumes no one is trustworthy by default. Instead of granting broad network access, ZTNA grants access only to specific applications after verifying the user's identity and device. This dramatically limits potential damage if an account is ever compromised.
For many use cases, SD-WAN/SASE over business internet can replace MPLS, though some workloads still justify MPLS. SASE and SD-WAN allow businesses to use multiple, inexpensive internet connections to create a resilient and high-performing network with security built in rather than bolted on.
Subscribe to our blog updates for in-depth perspectives on cybersecurity.