Summary: This article explains what a cloud security gateway is, how it works, its main features, top use cases, benefits, and limitations.
Your network has constant traffic from users, apps, and data. Without the right controls, this activity creates vulnerabilities. As cloud-based tools and remote work reshape the way teams connect, organizations need more than a firewall to protect what matters.
Every unmonitored transfer is a potential entry point for attackers, which can lead to unauthorized access, hidden threats, and data loss. A cloud security gateway acts as your digital checkpoint. It inspects every connection, enforces your controls, and keeps your operations secure.
Let’s break down what a cloud security gateway is, how it works, and why it’s becoming essential for modern businesses.
What is a cloud security gateway
A cloud security gateway (CSG) is a network security service that filters, monitors, and controls device traffic between users, cloud, and on-prem applications. It enforces security policies, prevents data loss, and blocks threats before they reach your systems.
In simple terms, a cloud security gateway sits between users, the internet, and cloud resources. Every request—from loading a website to accessing a SaaS platform—passes through it. The gateway checks for web-based threats, applies your organization’s rules, and ensures only safe, compliant data flows through.
A CSG combines multiple security services, including data protection, threat prevention, and secure access management. It’s often referred to as a secure web gateway (SWG) when deployed as part of a cloud-based solution.
How cloud security gateways work
Cloud security gateways inspect, filter, and manage every data exchange between endpoints and cloud applications. It ensures secure connectivity and consistent protection for all users, whether they’re in the office or working from home.
Here’s what happens under the surface:
Traffic inspection: Every request or data transfer is analyzed in real time. The secure web gateway detects malicious content, phishing attempts, or policy violations before data leaves or enters your network.
Policy enforcement: The system applies your organization’s rules, such as blocking unsafe sites, limiting access to risky apps, and maintaining compliance with regulations.
Threat prevention: Using advanced analytics and machine learning, it identifies suspicious activity,
malware, or
zero-day attacks, stopping them before they spread.
Data loss prevention (DLP): The gateway monitors sensitive information that moves across the network, preventing accidental or intentional leaks through uploads, email, or chat.
These combined layers of threat protection and data loss prevention make the CSG the axis of modern cloud security.
Keep your data safe: get the DLP guide
Simple steps to protect sensitive data, prevent breaches, and stay compliant
Main features
A cloud security gateway has several critical functions that work in sync to protect users, data, and apps. Here are the core features it has:
URL and content filtering. Controls internet access by allowing or blocking specific categories of websites. This helps reduce web-based threats and maintain productivity.
Application control. Identifies and manages access to cloud apps, such as Google Workspace, Slack, or Salesforce. It ensures that only approved applications are used within your organization.
Malware and phishing protection. Scans every file and link for malicious behavior, offering real-time
threat prevention that stops attacks before they impact users.
SSL/TLS inspection. Decrypts and inspects encrypted web traffic for hidden threats, maintaining visibility across all data flows.
DLP. Prevents sensitive data from leaving your network unintentionally. This feature is critical for maintaining data protection and regulatory compliance.
User and device authentication. Verifies identity and device posture before granting access—a key capability for supporting hybrid and remote teams.
Together, these features deliver the foundation of a secure web gateway that adapts to the modern, mobile workforce.
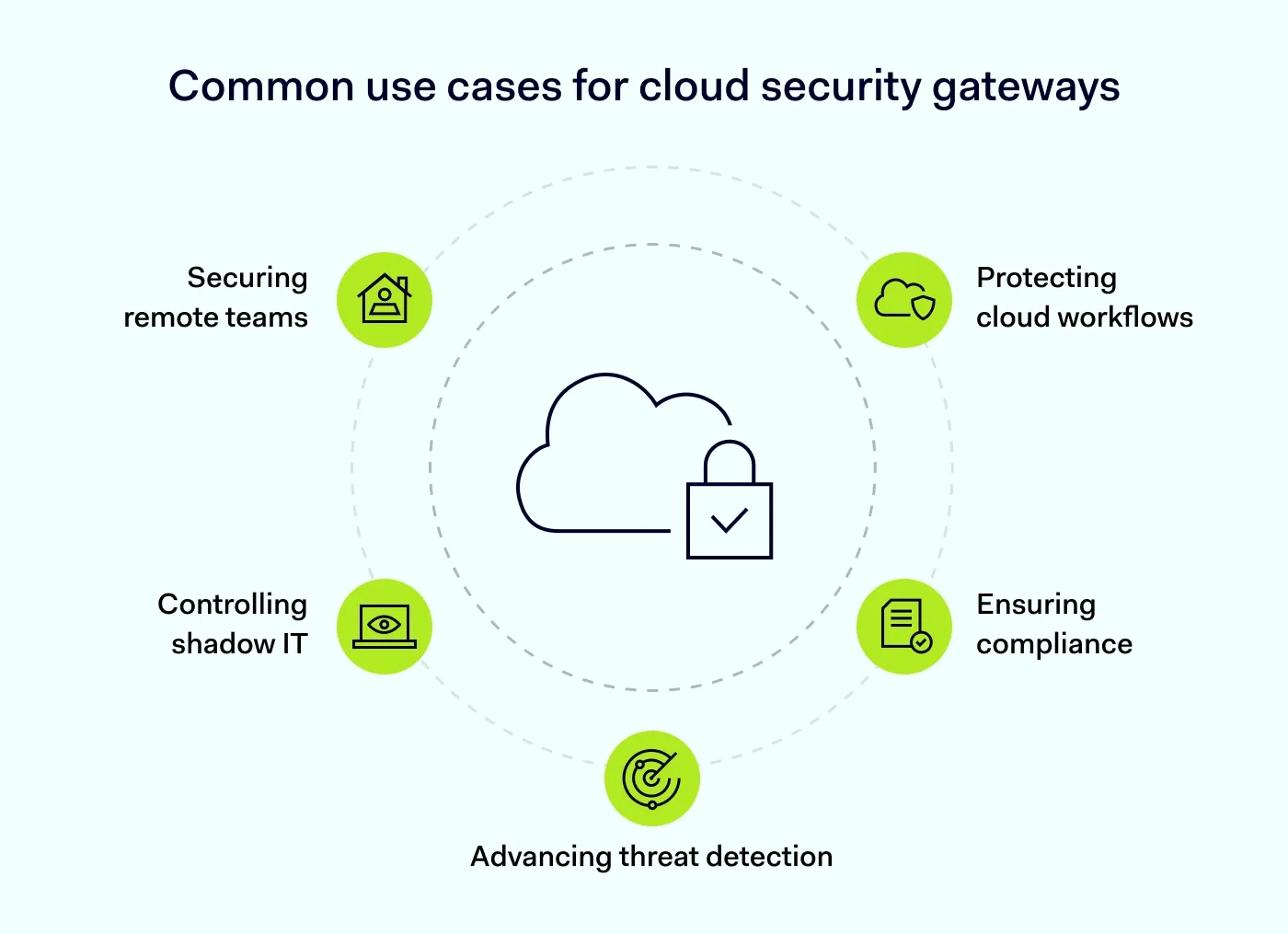
Top use cases for cloud security gateway implementation
Every organization uses cloud services differently, but security challenges are universal. You may be managing remote teams or protecting sensitive client data. A cloud security gateway adapts to your environment and provides flexible protection for any business scenario.
1. Securing remote and hybrid teams
As employees access corporate data from multiple locations, a cloud security gateway ensures secure remote access and consistent protection across all devices and networks. A secure web gateway keeps traffic encrypted, verified, and monitored, giving IT teams full visibility into user activity without disrupting productivity.
2. Protecting cloud-based workflows
For businesses relying on SaaS tools, gateways provide continuous monitoring of cloud apps, preventing leaks and unsafe data transfers. An SWG filters and inspects all web traffic coming from these applications. This ensures sensitive files never leave safe, approved environments. It’s a safety net that lets teams collaborate online without exposing confidential data.
3. Controlling shadow IT
A CSG detects and blocks unapproved apps, enforcing your organization’s security policies and maintaining compliance. By routing traffic through a secure web gateway, IT administrators can identify hidden cloud services, track usage trends, and stop risky behavior before it turns into a data breach. This visibility helps maintain control over every corner of your digital ecosystem.
4. Improving compliance efforts
Gateways help meet data privacy and compliance standards by providing detailed visibility and logging for web traffic and user activity. An SWG makes audits simpler by generating detailed reports on who accessed what, when, and how. It ensures data protection policies are enforced consistently across users and regions, which is critical for meeting regulations like GDPR or HIPAA.
5. Advancing threat detection
By centralizing security services on a single platform, IT teams gain faster insights and can respond to web-based threats more efficiently. A secure web gateway collects traffic analytics, making anomalies easier to spot and react to in real time. This approach strengthens threat prevention and incident response, minimizing the window for attackers to act.
Understanding where and how cloud security gateways add value allows to see the broader impact they have on performance, protection, and compliance.
Key benefits of cloud security gateways
Beyond technical capabilities, cloud security gateways deliver measurable business value. They improve security, IT operations, and overall user experience, all while ensuring data remains protected wherever it travels.
Improved security and threat prevention
A cloud security gateway continuously scans for malware, ransomware, and phishing links across all internet access points. Analyzing inbound and outbound traffic helps prevent attackers from exploiting vulnerabilities.
Enhanced performance and user experience
Unlike traditional firewalls that slow down connections, cloud-based solutions distribute filtering and inspection tasks across global networks. This ensures faster response times and uninterrupted secure web access, even for remote users.
Simplified management and reporting
Managing multiple security tools is a costly and complex affair. A secure web gateway centralizes control, allowing IT teams to enforce consistent security policies, generate compliance reports, and visualize network activity—all from one dashboard.
While the benefits of a gateway are substantial, no single solution can cover every threat vector. Understanding its limitations helps you design a layered security strategy to patch any remaining gaps.
Related articles

Joanna KrysińskaAug 27, 20258 min read

Joanna KrysińskaFeb 5, 20268 min read
Limitations of cloud security gateways
While powerful, cloud security gateways aren’t a complete solution on their own.
Limited visibility into non-web traffic: A traditional SWG focuses on web traffic—it can’t monitor internal app communications or unmanaged endpoints.
Potential latency issues: Deep inspection of encrypted data can sometimes introduce delays, though modern cloud-based solutions minimize this with a distributed architecture.
Integration complexity: When added to legacy systems, configuration can be challenging. Pairing a gateway with identity management and endpoint security tools is key for full coverage.
Recognizing these limits helps businesses build a stronger, layered defense strategy that extends beyond the gateway itself.
Strengthen cloud security with NordLayer
NordLayer’s cloud security solutions—including Secure Web Gateway (SWG), Zero Trust Network Access, and Cloud Firewall—deliver comprehensive protection for modern organizations. Built for flexibility, it helps secure users, devices, and cloud applications, no matter the location or network.
Here’s how NordLayer improves your network security:
Advanced threat prevention: NordLayer’s SWG filters web traffic in real time to detect and block web-based threats, phishing attempts, and
malicious downloads. Combined with Cloud Firewall, it ensures threats are stopped at both the network and application levels.
Data protection: Keep sensitive information secure at all times. By
masking your IP address and controlling access to internal resources, NordLayer ensures that data stays protected, even when employees connect from untrusted networks.
Secure remote access: NordLayer’s ZTNA enables employees to connect safely from any network, ensuring secure access to company systems and cloud applications, without compromising performance.
Policy-based control: Admins can enforce security policies globally, defining rules by user group, device, or location. This ensures consistent compliance and easy scalability.
Cloud-based architecture: As part of NordLayer’s cloud-based solutions, the SWG offers high availability, low latency, and smooth integration with SASE frameworks, ideal for growing businesses embracing hybrid work.
With NordLayer, organizations gain a secure cloud gateway that simplifies management, improves visibility, and integrates easily with modern IT infrastructure. It’s a smarter, more scalable way to secure access and maintain trust in every connection.
A cloud security gateway has become the backbone of secure digital operations. NordLayer brings these capabilities together in one platform, helping businesses protect data, defend users, and optimize performance.

Agnė Srėbaliūtė
Senior Creative Copywriter
Agne is a writer with over 15 years of experience in PR, SEO, and creative writing. With a love for playing with words and meanings, she crafts content that’s clear and distinctive. Agne balances her passion for language and tech with hiking adventures in nature—a space that recharges her.