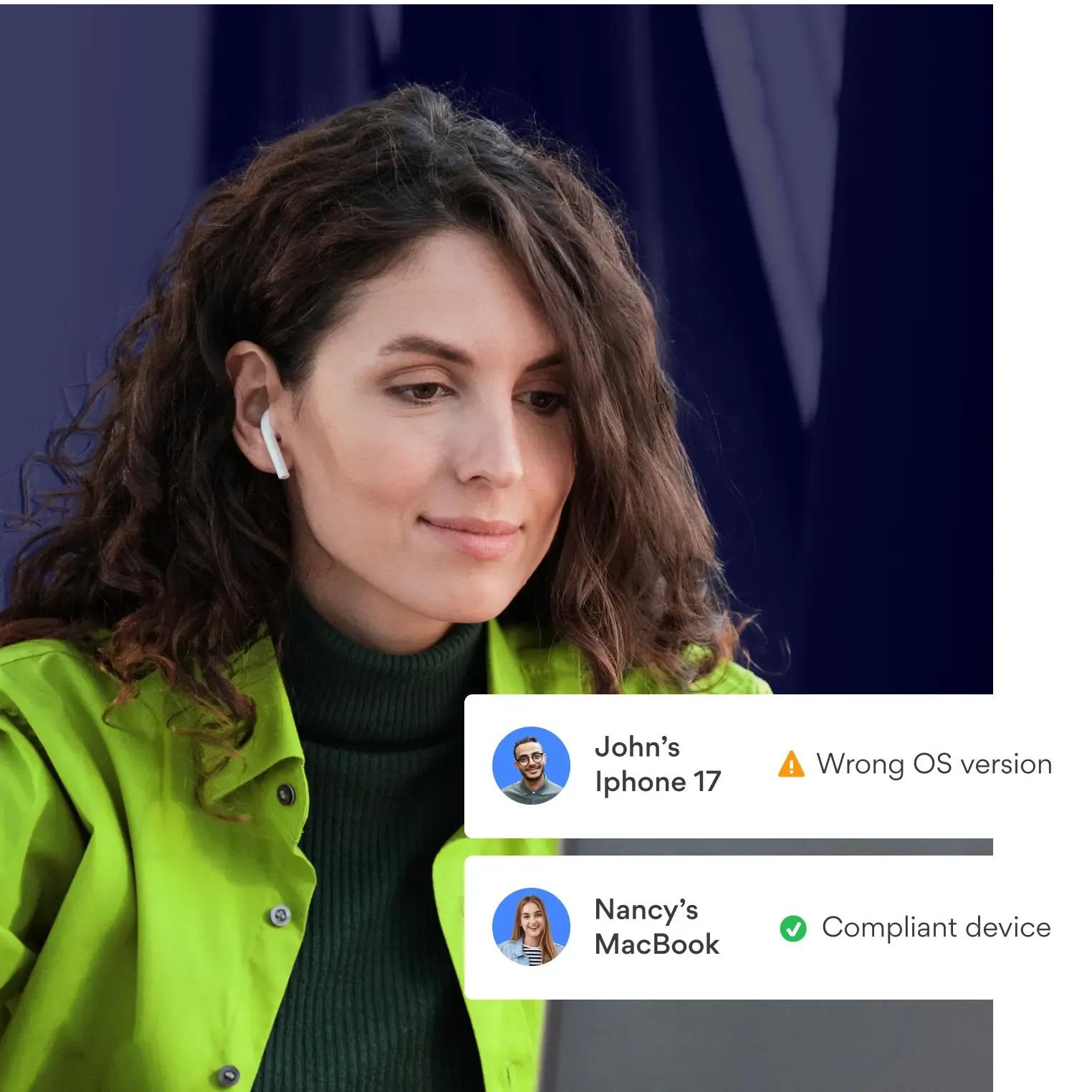
Simplify your security compliance journey
Step up your organization’s compliance alignment with NordLayer. Our solutions will actively contribute to your security checks and help mitigate potential security threats for both on-site and remote employees. All for an easier compliance journey.
We're trusted by
EVALUATION
Do you know your compliance management level?
Compliance standards can be overwhelming, but assessing your current security state and planning is key to meeting global regulations. With the right tools, NordLayer helps simplify the process, supporting your compliance journey.
Protect patient privacy and comply with HIPAA
The NordLayer platform encrypts sensitive data, enforces role-based access, and blocks any unauthorized network access attempt that could put your organization and reputation at risk.
Take the guesswork out of ISO 27001 compliance
NordLayer’s reliable, cloud-native platform helps you control access, encrypt traffic, monitor network activity and meet ISO 27001 standards swiftly and consistently.
Support all 5 pillars of the Cyber Essentials framework
The NordLayer platform offers access control, firewall protection, and malware prevention in one centralized hub, helping you stay on track with your security management.
EU businesses trust NordLayer to stay GDPR compliant
Control access, encrypt data, and track user activity in real-time with a cloud-first, enterprise-grade network security platform that’s built to scale.
Feel confident in your next PCI-DSS audit
The NordLayer platform encrypts cardholder data in transit, monitors and logs network activity in real-time, and enforces strict access control to help you get and maintain PCI-DSS certification.
Reduce risk and stay SOC 2 compliant
With ZTNA, strong authentication, and real-time visibility into network activity, the NordLayer platform provides the tools you need to strengthen security and support your SOC 2 journey.
Simplify NIS2 compliance with NordLayer
Built by the team behind NordVPN, NordLayer delivers trusted, enterprise-grade access controls, real-time encryption and monitoring in one reliable, cloud-native platform.
Get a real-time look at how NordLayer protects businesses
Explore features like Custom DNS, a dedicated IP, VPN Split Tunneling, and more, all in real-time with our interactive Control Panel demo.
NECESSITY
Why do you need to comply with security regulations?
MANAGEMENT TRIGGERS
The challenges of security compliance control
Evolving security environments
Security threats change quickly, which requires an active response from organizations to combat new threat levels and address key issues.
Distributed workforce & endpoints
Network infrastructures are becoming more dispersed as employees move towards hybrid and remote setups. Tracking and managing all of these endpoints is a challenge for any organization.
Larger teams
Coordination of teams and infrastructures across a larger working environment increases the complexity of compliance management. Larger teams mean more difficult access control, which makes meeting compliance requirements harder.
Multi-country presence
Regardless of their size & industry, many businesses today have employees spread across multiple countries. And some countries might have varying regulations, making compliance management a real challenge.
Manual processes
In the past, spreadsheets, file shares, and documents were the only tools available to manage compliance. However, these tools cannot keep up with constantly changing industry regulations, and updating them manually takes a lot of time.
BENEFITS
How can NordLayer contribute to your organization’s compliance?
With the growing trend of hybrid and remote work, ensuring regulatory compliance on a larger scale is now more challenging than ever. As part of Nord Security, our sole focus is providing a wide range of top-notch cybersecurity solutions to help you meet, maintain, and surpass compliance requirements.
Free guide: master security compliance management—stay ahead of evolving requirements
SOLUTIONS
Achieving compliance made easy: tools that work
Network Access Control
NordLayer's NAC solutions go beyond just mitigating security risks, helping your business meet certain network access requirements under regulations like HIPAA, SOC, and PCI-DSS.
Remote Access VPN
A remote access Virtual Private Network helps meet conformity standards by providing a secure and encrypted connection between your employees and company resources, ensuring the confidentiality and integrity of data.
Identity & Access Management
Implement strict IAM solutions to enforce access control policies, allowing only authorized users or user groups to access critical resources and networks. This contributes to establishing a solid basis for enhancing cybersecurity compliance measures.
Secure Remote Access
The SRA approach provides a crucial layer of security in today's hybrid working environments. By preventing unauthorized access and reducing the risk of data loss, it helps businesses safeguard sensitive information & achieve regulatory consent easier.
Network Segmentation
Most regulatory frameworks require to ensure data’s inaccessibility to unauthorized users. Network Segmentation is a perfect & cost-effective way to achieve that, as it helps to keep processes such as auditing and payment processing separate from the rest of the network.
Let us be part of your compliance journey
INDUSTRY FRAMEWORKS
Secure your business environment with modern security strategy
OTHER USE CASES
More ways to secure your business
Secure Internet Access
Secure online connections while accessing and browsing the internet
Secure private access control
Control, secure and customize remote workforce access to internal company resources
OUR INSIGHTS
Security & compliance resources
This content has been prepared for general informational purposes only and is not legal advice. We hope you will find the information informative and helpful; however, you should use the information provided in this article at your own risk and consider seeking advice from a professional counsel licensed in your state or country. The materials presented on this site may not reflect the most current legal developments or the law of the jurisdiction in which you reside. This article may be changed, improved, or updated without notice.
Additional info
Frequently asked questions
NordLayer helps its clients by providing a handful of cybersecurity solutions and adhering to regulations as a service provider so that NordLayer's clients can pursue various information security certifications. However, regulatory compliance is a complex topic, and our tools alone will not be sufficient to make you fully compliant, but they will still contribute to your bigger compliance picture.
The primary purpose of security compliance is risk management and meeting industry standards. The first step towards this is equipping your business with suitable safety tools that could help you control access and safeguard your resources from potential cyber threats on the internet.
Companies should continually monitor and review their systems to ensure security and industry standards compliance. Following a few necessary steps will help your organization make strides toward full security compliance:
- Identify any practices or systems that are vulnerable or currently non-compliant.
- Create the next steps towards compliance based on the resource needed and potential impact or severity.
- Efficiently action those steps and address any system issues that require immediate action.
- Log the applied changes and monitor the results.