Secure Private Access: Connect your team to essential resources
Secure and manage how your team connects to company systems—wherever they work.
- Protect cloud, on-premise, and SaaS access
- Enforce Zero Trust access
- Manage users and devices from one dashboard
14-day money-back guarantee
OVERVIEW
What is Secure Private Access, and why is it important?
Secure Private Access is a security framework that controls how employees and devices connect to company resources. It ensures that only verified users can gain remote access to sensitive data, whether stored in the cloud or on-premises. Limiting access based on identity and context helps prevent unauthorized entry, data leaks, and lateral movement within your network.
Without Secure Private Access, networks are exposed to potential breaches, service disruptions, and reputational damage.
BENEFITS
Build a safer, more efficient network architecture with Secure Private Access
Secure Private Access uses key elements of the SSE framework, such as ZTNA and FWaaS, to secure both internal and remote access to company resources and enforce least privilege access. This approach is a fundamental part of modern security architecture. It helps companies control access with multilayered authentication. It also divides the network into segments, allowing only authorized users secure connectivity.
Keep it safe from unauthorized users
By using our Dedicated IP features and IP allowlisting practices, you’re letting only approved users access your network. This significantly lowers the risk of cyberattacks and online threats.
Connect to multiple sites and resources
Allow users to securely connect to multiple sites and company resources, ensuring safe data transfer and reducing the risk of breaches.
Set up secure connections between remote devices
Use Cloud LAN to interact with your endpoints through a secure, VPN-like connection—without any physical LAN limitations.
Segment the user base and allocate resource access
Apply network segmentation policies to limit user permissions and movement within your network, significantly reducing the impact of potential breaches.
Automate user on and offboarding
By setting up User Provisioning, you can efficiently manage user accounts and prevent unnecessary access to your internal network, saving valuable time and resources.
Improve security beyond a username and password
To enhance security and prevent identity breaches, enforce an extra layer of protection—like 2FA, biometrics, and SSO—to support Zero Trust access and keep your data safe.
Try before you buy: Explore NordLayer in an interactive demo
EXPLORE
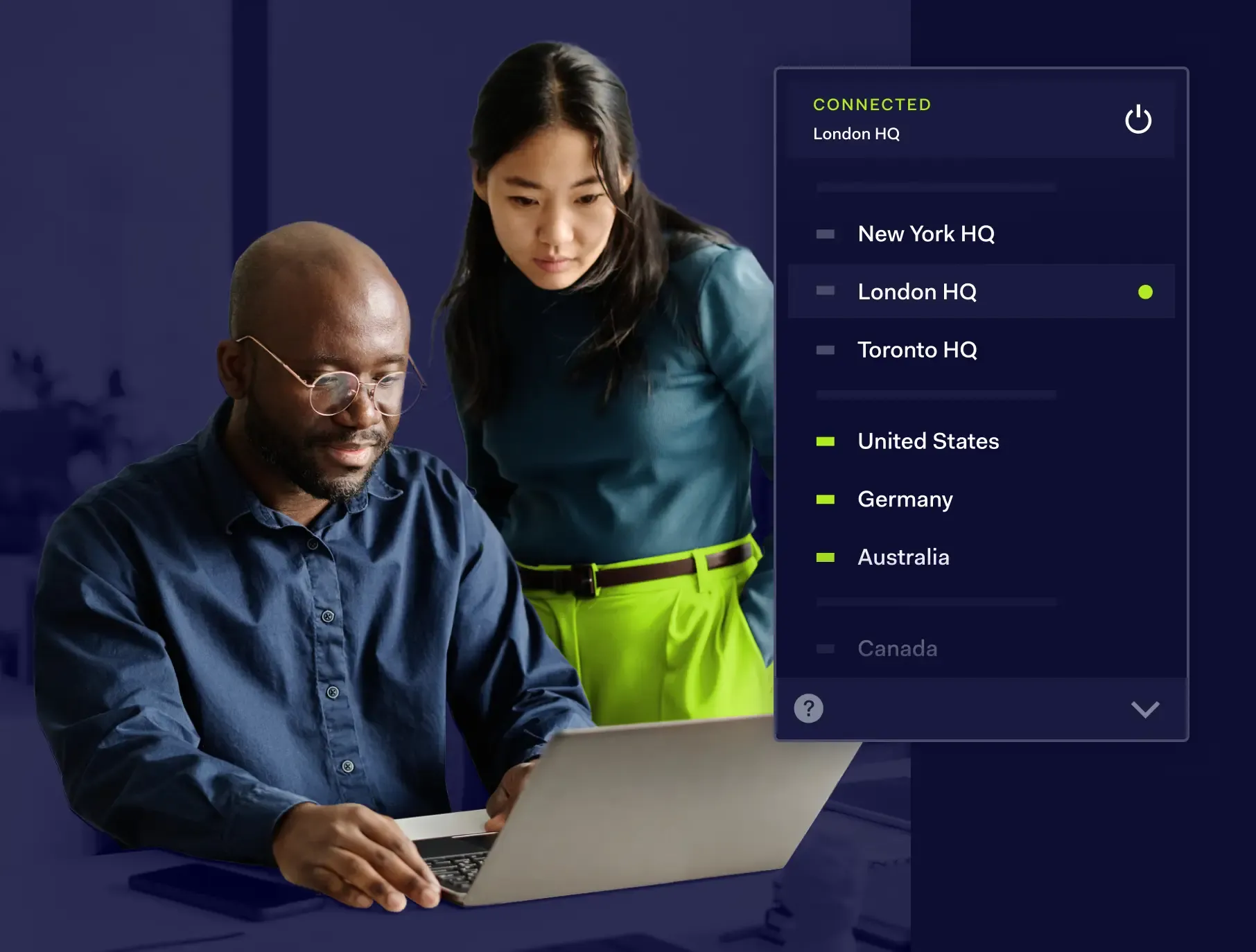
How does NordLayer Private Access work?
We use a Zero Trust model in NordLayer to grant precise access to your organization's cloud, on-premise resources, SaaS, and private applications. Our advanced network access control technologies ensure that only authorized personnel or devices can access the network. With continuous multilayered identity authentication and robust encryption of all connections, we maintain a secure environment. These solutions work together to support modern network security frameworks, such as ZTNA and FWaaS, and ensure your data and devices get the highest level of protection.
KEY CAPABILITIES
The critical role of Secure Private Access in network & resource management
Implementing Zero Trust access to your organization's cloud tools and sensitive data significantly reduces the attack surface and minimizes cyber threats.
Controlled access to cloud tools and resources
By managing and restricting access to your organization's cloud tools and sensitive data, you effectively minimize the potential surface for cyber-attacks and unauthorized activities.
Team-based segmentation for safer accessibility
Network segmentation tools enable your employees & contractors to access only the resources required for their roles, ensuring a secure and efficient work environment.
Cloud LAN deployment
Cloud LAN provides a secure way to access and connect remote devices for file sharing, remote control, or other work tasks—creating a private, direct network over the public internet.
Remote access to different offices and devices
When operating across multiple offices and regions, it’s important to keep remote connections securely encrypted while ensuring smooth, reliable access for all users.
All-round data breach prevention
Rising malware and phishing threats make advanced network security measures essential to protect data, prevent breaches, and safeguard your digital assets.
Malicious content filtering
Certain advanced filtering solutions help strengthen your company’s data security and protect your team from malicious websites and harmful online content.
SOLUTIONS
Private Access solutions
Remote Access VPN
Ensure that both in and out-of-office employees can easily and securely connect to your business network.
Network Access Control (NAC)
Efficiently control and keep unauthorized users and devices out of your business network.
Network Security
Improve your security architecture to protect your business against advanced threats and malware with adaptable solutions tailored to organizations of any size.
Identity and Access Management (IAM)
Rest assured that every user is thoroughly verified and properly authorized before accessing your company’s network and sensitive business resources.
Secure Remote Access
Enable secure access to your organization's network for all employees, regardless of their geographical location.
Network segmentation
Use segmentation to ensure employees and contractors access only the data and resources they need to perform their roles.
FEATURES
Explore our Secure Private Access features
NordLayer’s range of adaptive security tools will help you assemble a custom Zero Trust identity and access management solution for your organization’s needs.
Virtual private gateways
IP allowlisting
Cloud Firewall
Device Posture Security
Site-to-site VPN
Cloud LAN
MFA, SSO, Provisioning
OTHER USE CASES
More ways to secure your business
Secure Internet Access
Secure online connections while accessing and browsing the internet
Achieving regulatory compliance
Kickstart your path to security compliance
Private Access: Your gateway to a protected network
CUSTOMER REVIEWS
Why leading teams worldwide choose NordLayer
in In Security Service Edge category
NordLayer in numbers
15,000+
Businesses protected
10 min
Average time to deploy
40+
Global service locations
KNOWLEDGE HUB



