Security that works wherever your remote team does
NordLayer is a toggle-ready security platform that protects your company’s data, devices, and access—wherever your team logs in. From home offices to airport Wi-Fi, stay in control without slowing your work down.
14-day money-back guarantee
ENTERPRISE-GRADE SECURITY MADE SIMPLE
All-in-one security platform built for remote work
NordLayer brings all your essential network security tools into one cloud-native platform to protect your remote team with a single, toggle-ready solution.
14-day money-back guarantee
RISKS
New ways of working create new vulnerabilities
Keeping things secure while working from home is now a crucial part of protecting businesses all over the world. This means embracing hybrid work security practices that tackle the problem from every angle.
With so many people working from different locations, there are millions of new connections that must be carefully examined and protected. Employees need safe methods to reach company resources from wherever they are, and this might mean updating outdated systems and technology.

Main risks when working remotely
Phishing
Emails that trick employees into downloading malware that steals sensitive data.
Ransomware
Harmful software that gets into connected systems and then demands money to fix the problem.
Spyware
Harmful software designed to collect data which fraudsters or competitors could then use.
Zero-day attacks
Targeted attacks on unpatched computer systems and apps that might be difficult to keep an eye on when working remotely.
Data theft
Stealing login information to get into databases with customer and employee information or breaking into them directly.
Sabotage
Unsupervised employees either intentionally or accidentally damage property that belongs to the company.
14-day money-back guarantee
SECURE REMOTE WORKERS
Remote workforce security solutions
When one of your users leaves the safety of your network perimeter, you lose a significant amount of visibility and control over their security. The problem gets worse when employees connect from unprotected locations, public Wi-Fi, and crowded spaces where others can easily see their screens. The attack surface expands, and data breaches may occur.
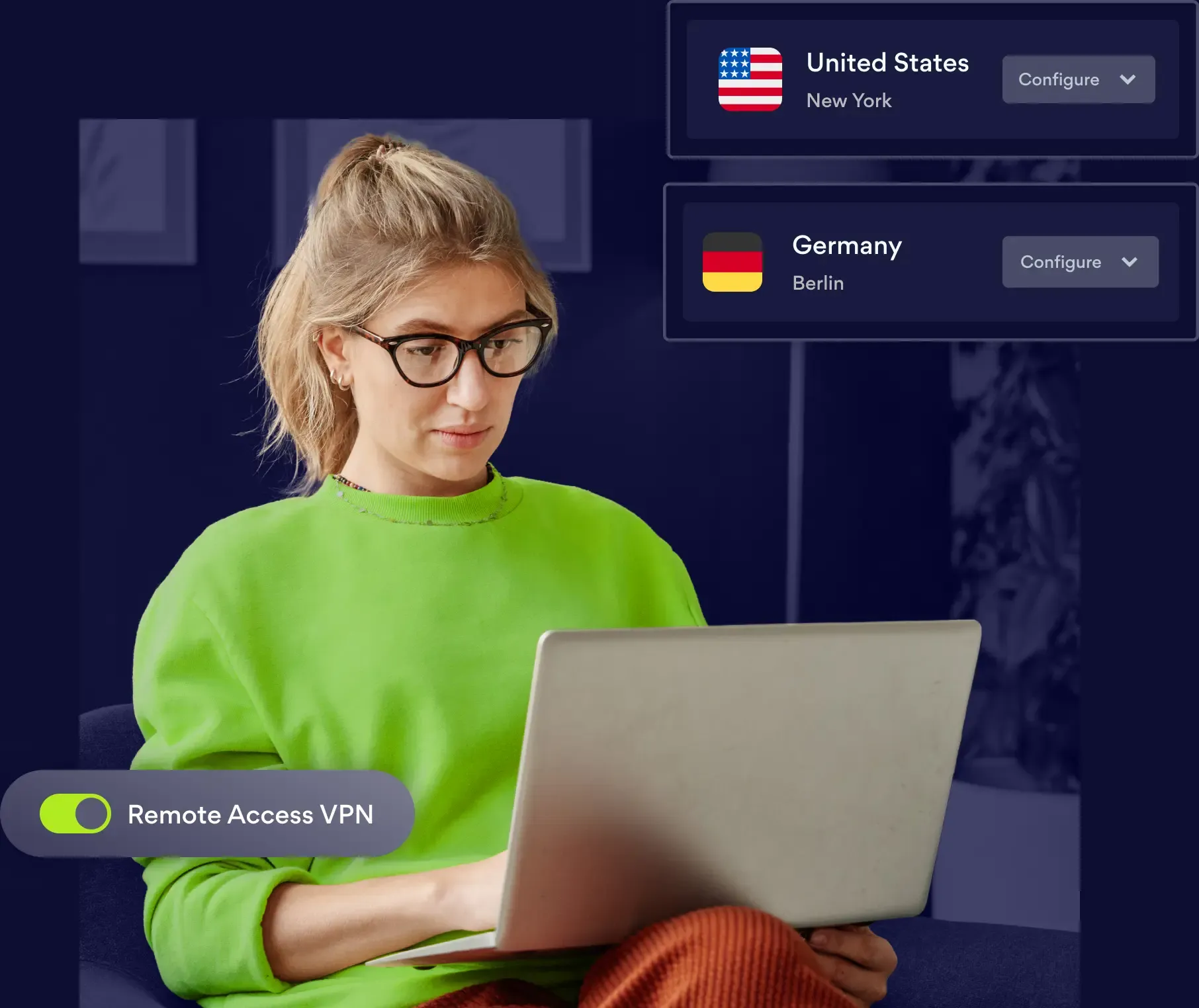
Remote Access VPN
A remote access VPN creates an encrypted tunnel between your organization’s resources, endpoints, and the employees using them—shielding all online activity from outside users, and safeguarding sensitive areas of the network.
Zero Trust
Adopt a cybersecurity solution focused on removing implicit trust from any user or device that attempts to gain entry to a company network. With a “trust none, verify all” principle, business network segmentation can be achieved.
Secure Web Gateways
Think of Secure Web Gateways (SWGs) as online security guards. They scan web traffic, remove threats, and ensure your organization stays compliant. NordLayer's Web Protection does exactly that—keeps you shielded from malware, ransomware, and viruses.
Security Service Edge
Secure business data, resources, and all users in your network by adopting the Security Service Edge (SSE) framework. SSE is a blueprint for better business security, combining user-centric authentication, access control, and seamless integration across the cloud.
HOW WE HELP
How NordLayer can help your hybrid workplace
Your employees trust that you have the tools to keep their data secure, no matter where they work. Strengthen that trust with a comprehensive hybrid work security solution that combines technologies like identity proofing, multi-factor authentication, single sign-on, virtual private networks, adaptive authentication, and visitor management.
Cloud LAN
Share files endpoint-to-endpoint when multiple user devices are connected to NordLayer
Remote access VPN
NordLayer’s VPN capabilities allow for safe working, data transfer, and file sharing.
Cloud integrations
NordLayer integrates with platforms such as AWS, Azure to provide seamless security across your entire business.
AES 256-bit encryption
NordLayer utilizes military-grade tunnel encryption to hide your traffic and online activity from users on the open internet.
Network access management
Set permissions and security policies for users and apps to ensure only authorized staff can reach sensitive and confidential data.
Site-to-site
Site-to-site VPNs act as protected tunnels between two or more networks, providing safe pathways to exchange private data—away from outside users.
Browser extension
Our browser extension lets you easily and securely connect to your organization's networks, including VPNs and hosted resources, using just your browser.
BYOD security
NordLayer provides security to personally-owned devices needed to enter business networks.
Jailbroken device detection
NordLayer detects devices that are vulnerable to attack and alerts admins immediately.
Device posture security
Monitoring devices for suspicious activities helps you detect security breaches early on, enabling quick action to prevent potential damage or data loss.
Network segmentation
Create teams and private gateways each with a dedicated IP, enabling admins to segment their local networks and restrict certain data to those who really need it.
IP Allowlisting
It allows access to a network or system only from specific, trusted IP addresses, thereby providing an additional layer of protection against unauthorized access.
2FA
Multi-factor authentication is used to validate a user's credentials, ensuring only trusted employees can access their device - and in turn - the network.
User provisioning
In addition to creating user identities in cloud apps, automatic provisioning also includes the maintenance and removal of such user identities as status or role changes.
SSO
Single sign-on allows you to use one set of security credentials to access your multiple cloud applications.
Biometrics
Address security concerns by authenticating users based on fingerprint scanning and facial recognition, allowing secure access to only trusted users.
Easy to scale your licenses
Add, remove, or transfer user licenses in accordance with how your business grows or evolves.
Seamless integration
Expand NordLayer secure protection to cover your offices, branches, or local networks.
High performance
No matter the number of users connected to the network, speed and performance remain high and unaffected.
Simplify license scaling for users & servers
Add, remove, or transfer user and server licenses with ease, adapting to the growth and evolution of your business.
pricing
Choose the best plan for your business needs. All plans include free malware protection
Enjoy a 14-day risk-free trial
Lite
Essential internet access security with basic internet threat prevention features.
$8
USER/ MONTH
SAVE 20%
TOP CHOICE
Core
A suite of advanced internet access security & basic network access control solutions.
$11
USER/ MONTH
SAVE 21%
Premium
A powerful blend of network access control solutions with more granular network segmentation and the ability to interconnect sites & devices.
$14
USER/ MONTH
SAVE 22%
Enterprise offer
Custom-fit network security for teams over 100 seats, offering clarity & flexible pricing.
From
$7
USER/ MONTH
SAVE MORE
VAT, sales tax, or other mandatory tax applicable to your purchase in your country will be calculated additionally.
Protect your remote workforces
Start securing your hybrid workplace today, or contact our specialist if you have any more questions.
14-day money-back guarantee