Decluttering cybersecurity terminology
It is no secret that the definitions of cybersecurity solutions have become overwhelming to business-related communities. Online reports, corporate blogs, email marketing, infographics, podcasts, and white papers: these content pieces can become a real rabbit hole if you seek to outline what cybersecurity is. The credibility and consistency of that information is also debatable in some cases. Therefore, even though there is plenty of available information about cybersecurity, it is not tailored for specific roles or knowledge levels and thus can lead to bigger confusion and unwillingness to dig deeper rather than to clarity and needed awareness.

Concise glossary with essential industry terms explained in a simple language
WHAT IS IN THIS TOOL?
Decluttering terminology
In a perfect world, everyone would be fully on-board on cybersecurity terminology and solutions, however, this hardly is the case. Therefore, it is essential to at least make sure that the roles involved are familiar with the topic to the extent needed to make informed decisions or efficiently use solutions.
Levels of knowledge
Because of increasing cases of miscommunication, we have prepared a concise glossary to make laying the foundation for understanding the essential cybersecurity terminology in your organization easier. We believe that successful cybersecurity related communication requires aligning the definition’s complexity with previous personnel experience in cybersecurity. Due to this, descriptions are divided into three general levels of knowledge:
- entry level to give the required basics to understand key concepts
- medium level to dive a little bit deeper and explore various solutions
- professional level to be able to compare different solutions and features
Entry level definitions
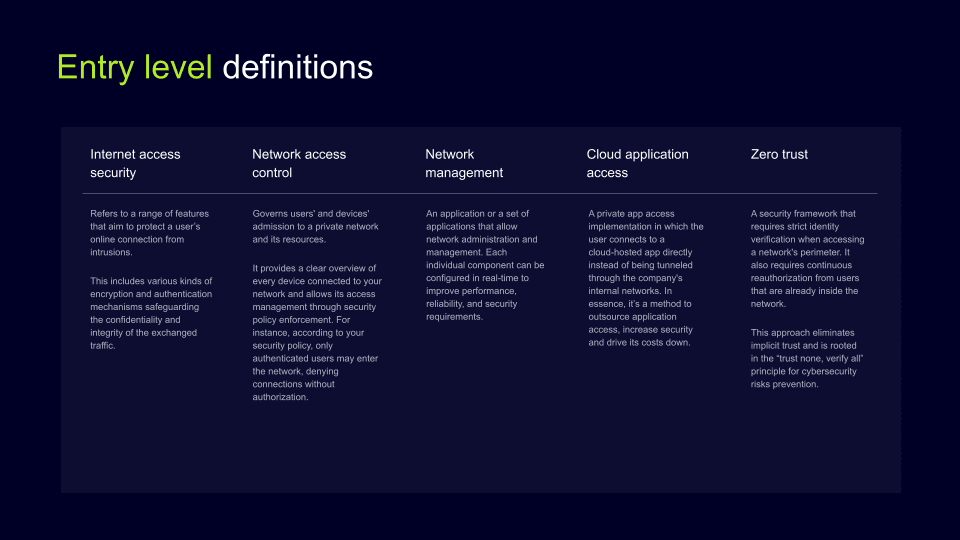
It would help if you had a conversation while using terms that your organization would understand. Basic definitions shed some light on key cybersecurity concepts and give enough knowledge for everyone to communicate clearly and with confidence in the organization. Definitions such as internet access security and network access control might be helpful and enough for someone who only has an entry-level understanding. They explain the basic solution and provide understanding on how the solution works without going in too much detail and behind-the-scenes technology.
Medium level definitions
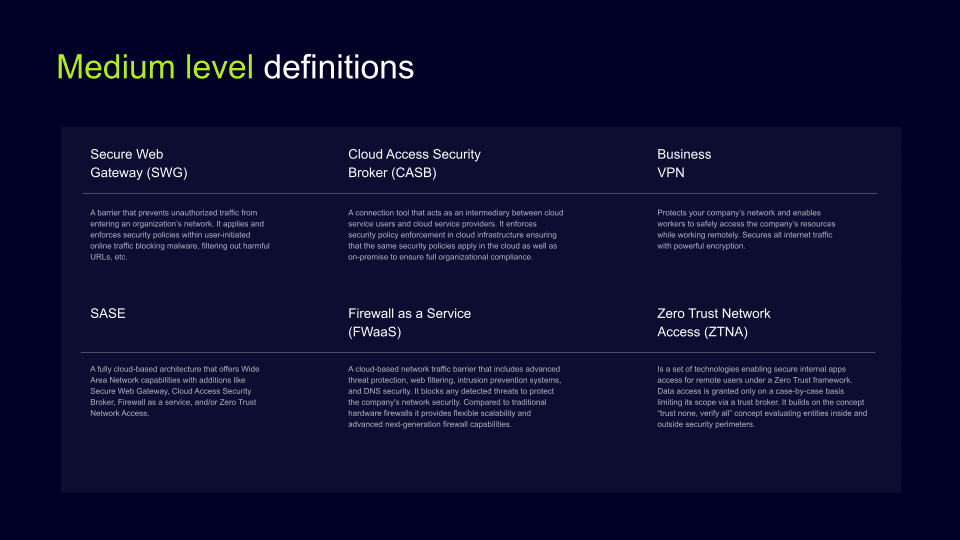
For more advanced users we suggest getting acquainted with even bigger variety of tools such as Secure Web Gateway (SWG) or Cloud Access Security Broker (CASB). In this section, we cover more advanced solutions used and recommended for business cybersecurity.
Pro level definitions
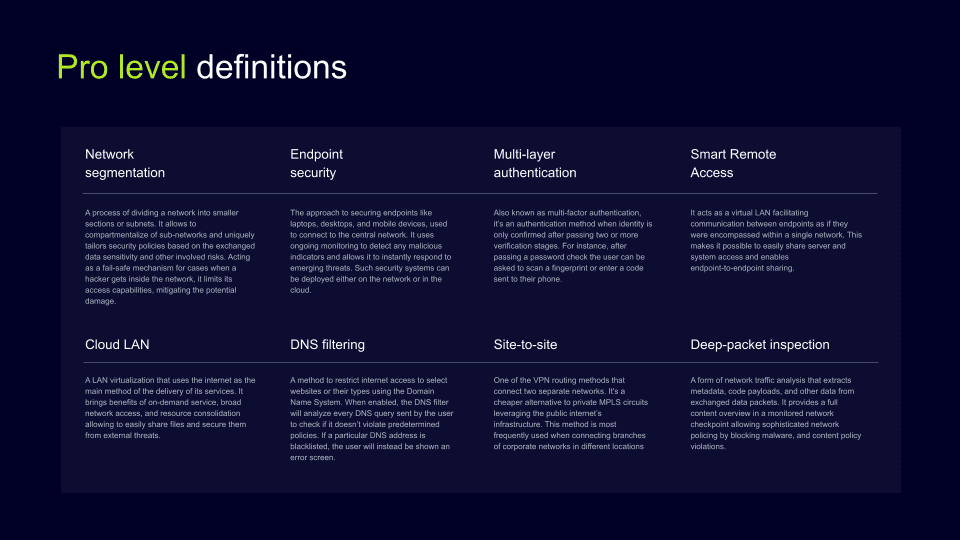
Pro level definitions provide the most technical and functional terms to give enough knowledge to independently understand, compare and choose the best solutions and features. For example, endpoint security is the approach to securing endpoints like laptops, desktops, and mobile devices that are used to connect to the central network. This approach uses ongoing monitoring to detect any malicious indicators and allows to instantly respond to emerging threats. Such security systems can be deployed either on the network or in the cloud.
Expected results
When it comes to results, you might see the positive impact of this concise glossary quite shortly. Think about more efficient troubleshooting. The managers, team leaders, counterparts — all of the team members may equally assist you with indicating what exactly is not working. The more your team understands potential dangers, cybersecurity, and mitigation, the better prepared you will be. Furthermore, having essential knowledge also tends to increase the support of management for the further development of cyber security measures and trust in your expertise.
Do not hesitate to check out the ready-to-use glossary. Here, you’ll find definitions of critical terms commonly used in the security industry. Regardless of an employee’s role in an organization, this set of cybersecurity terms should improve the quality of internal communication and facilitate the process of cybersecurity like troubleshooting, implementing IT policies, and many others.
If you have any open questions about cybersecurity solutions, get in touch with our experts.
Concise glossary with essential industry terms explained in a simple language
Discover