Introducing a new solution
Investing in an adaptive network security tool is only a part of the answer to your need to improve your organization’s security posture. We find that the implementation process without personnel support has a relatively small influence on network security. However, the synthesis of both aspects leads to a better success rate in handling the organizational change that is otherwise hard to manage end-to-end.

Introduce internal cybersecurity solutions
WHAT IS IN THIS TOOL?
Solutions for end users
How can IT managers handle it more successfully? Our expert team identified the two most prominent approaches to introducing a solution to end-users.
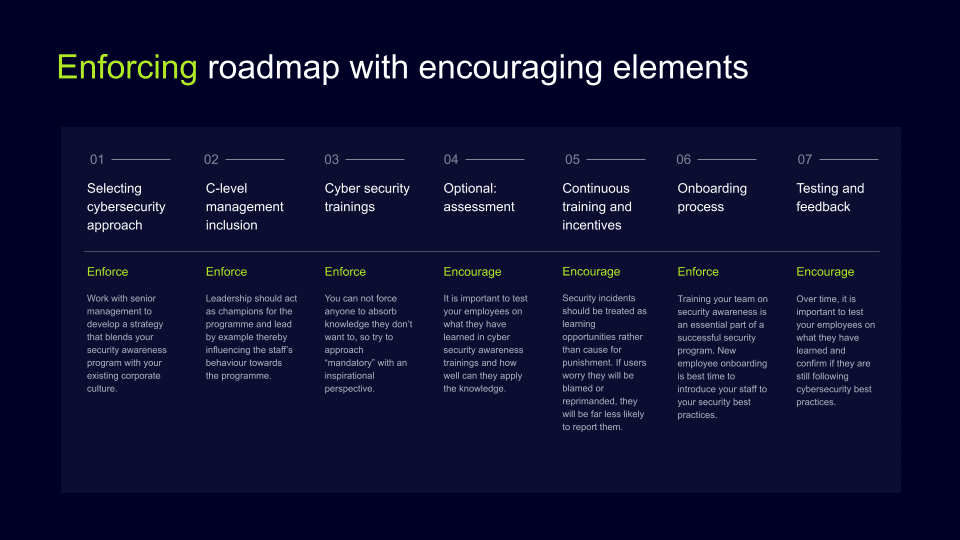
Enforcement
The first is an approach to introducing new solutions related to policy enforcement. In this case, IT managers do not compromise the network security tools with the employees. Instead of involving the team, the persons responsible for cybersecurity implementation explain the circumstances that might affect the management’s finances to get the buy-in. The training to adopt a settled solution usually follows.
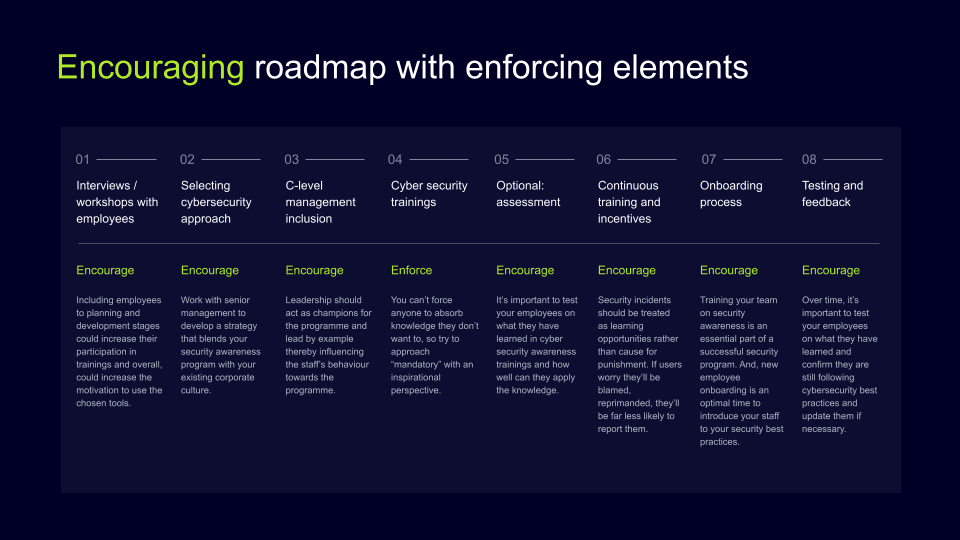
Encouragement
The second approach to onboarding end-users is encouragement. In some cases, things end poorly when the personnel senses that an IT manager wins over full support from the management and uses this power to enforce the fierce usage of the solution. So, IT professionals act like mediators and initiate workshops and early employee inclusion to seek agreement between management and employees.
Still, it would be helpful to consider drawbacks and limitations before applying these approaches to your organizational onboarding process. We notice that enforcing the solution in the organization might result in a faster implementation process, however, with lower employee motivation. Meanwhile, encouraging employees to adopt new cyber security tools might be slower but will likely result in continuous use with a higher cause.
This tool is designed for anyone responsible for cybersecurity solutions and suggests onboarding guidance and a clear interpersonal communication strategy. Moreover, it translates perfectly into demonstrating the management of the rare capabilities of the IT team, sharing the holistic approach towards the internal changes. These approaches are compatible with various organizations regardless of size: small and medium-sized enterprises or even large companies.
No ‘one size fits all’ approach
There is no magic trick for guaranteeing higher workforce motivation within a corporation’s walls. But you might consider combining enforcement and encouragement or choosing separate fragments of both to reach a better implementation success rate. Experience suggests looking for the answer in your company’s culture and psychological climate to determine it accurately.
Explore more on introducing solutions in our materials. We provide an overview of roadmaps and illustrate how each journey could look. The final setup may be relatively quick and intuitive, but the implementation journey insists on feedback and correction. If you seek further assistance, feel free to contact our professionals. We will help you with onboarding the team without any delay.
Introduce internal cybersecurity solutions
Discover