Summary: Endpoints are the primary gateway for cyber threats. Discover how to secure your devices and prevent a single compromise from becoming a network-wide crisis.
If you were asked where threat actors usually launch their attacks, what would you say? You might point to the firewall. And you would be wrong.
The real target is the endpoint. IBM’s Cost of a Data Breach Report suggests that up to 90% of successful cyber-attacks originate from devices such as laptops, servers, and mobile phones.
With the average data breach costing $4.4 million, endpoint security is a business necessity. As remote work and IoT expand, securing your endpoints serves as your first line of defense. Let’s explore how endpoint security works and how to prevent a single compromised device from becoming a network-wide crisis.
What is endpoint security?
Endpoint security covers all measures taken to defend user devices from direct and indirect threats. It aims to prevent unauthorized access.
What counts as an endpoint?
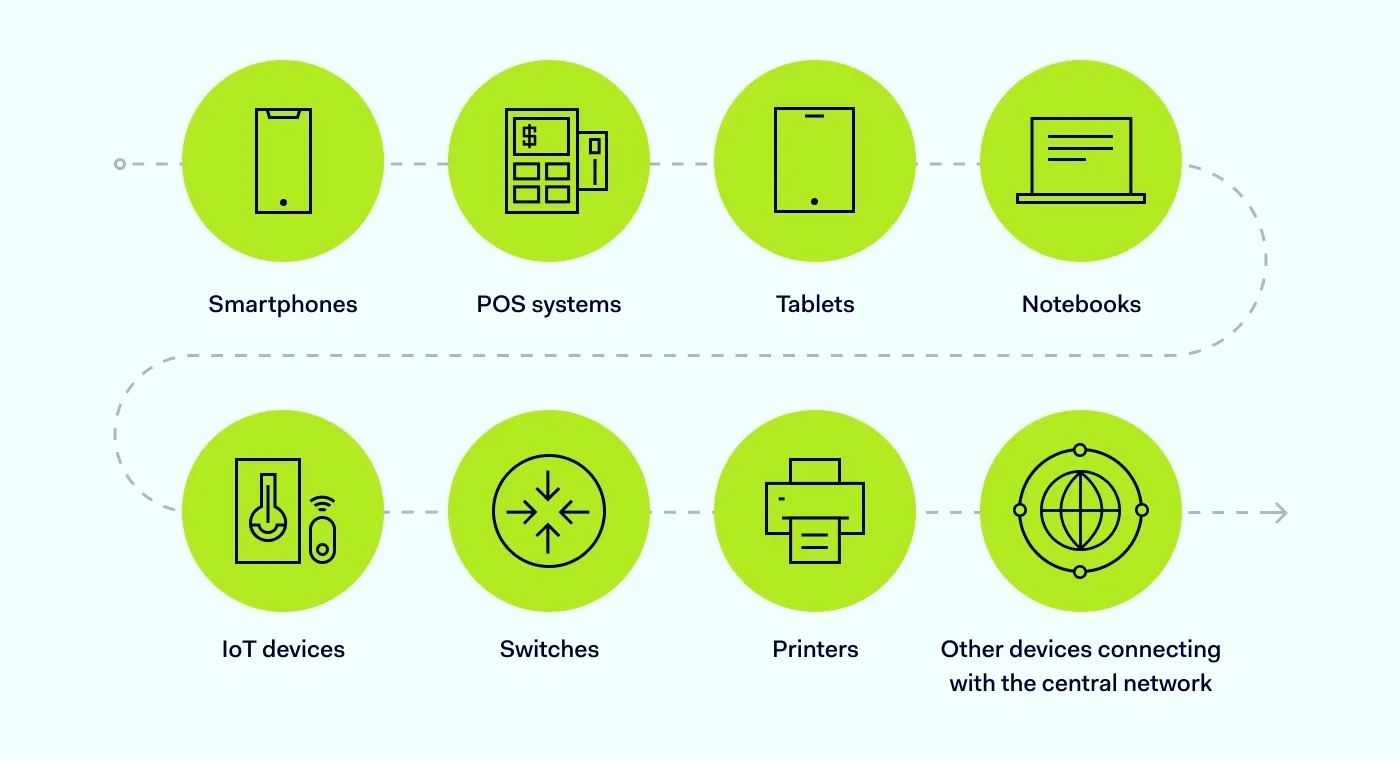
Endpoints are hardware devices and applications connected to a network outside its firewall. Here are examples of endpoints:
Notebooks
Tablets
Smartphones
IoT devices
POS systems
Switches
Printers
Other devices connecting with the central network
It's important to note that a virtual environment could also be considered an endpoint. If an application or service provides a shared operating environment, it functions as an endpoint. Since every connected device acts as a potential gateway for a breach, securing the entire inventory is essential.
How does endpoint security work?
Endpoint security relies on centrally managed tools to protect against external threats. It examines files, processes, and systems to scan for malicious activities that could compromise enterprise endpoints. This system is constituted of two main parts:
Endpoint protection platform: Software installed on devices to prevent malware intrusion. Usually, EPP is used in combination with detection and monitoring tools to stop cyber-attacks in their tracks.
Centralized management console: An interface that allows for the monitoring, investigation, and response to cyber threats. The console can be deployed on-premises, in the cloud, or via a hybrid approach.
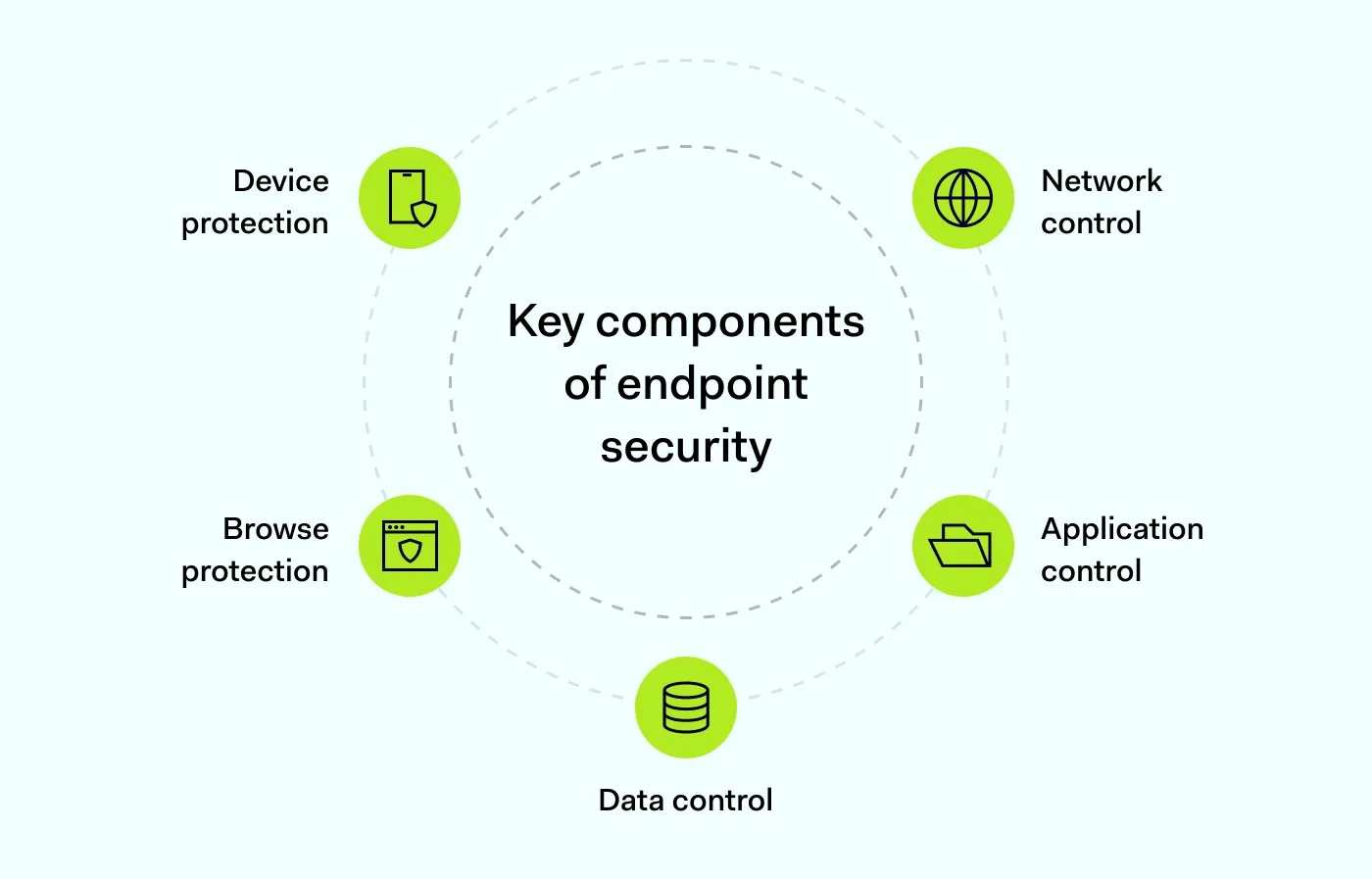
Together, EPP and the management console form an endpoint security system. However, the protection is often delivered through specific functional components.
1. Device protection
The device protection module identifies suspicious activities on endpoint devices by tracking and analyzing endpoint event logs. IT security teams can use endpoint protection as a remote antivirus solution.
2. Network control
An effective endpoint security strategy should secure devices before malware can infect them. For this reason, network control tracks, monitors, and filters inbound traffic, acting as a filter. When something suspicious is detected, inbound traffic is blocked. This bridges the gap between individual device safety and broader network security, keeping cyber threats at a distance.
3. Application control
Enterprise applications are frequent targets for attack. Consequently, server access and software installation require strict supervision. Application control monitors usage and blocks unauthorized activity. Because unpatched software creates security holes, some endpoint security platforms include application hardening to reduce the attack surface and eliminate applications as an entry point.
4. Data control
This component handles all data transfer operations to its storage. Various tools prevent data leaks and enforce security mechanisms, such as encryption.
It’s the most effective way to secure data against unauthorized access and help avoid potential data breaches. Well-put endpoint security solutions should offer full disk encryption and secure communication tunnels
5. Browser protection
Browser protection uses web filters to strictly define what users can access, automatically denying access to all other content. Since malicious links and phishing sites are common infection vectors, browser protection provides granular control over endpoint devices, blocking dangerous websites to minimize risk.
Why is endpoint security important?
Remote and hybrid work models have become the new standard, and organizational cybersecurity has shifted its focus. The traditional perimeter has dissolved, leaving endpoints as the primary gateway to internal networks. This development has made endpoint protection a critical priority, as bad actors often exploit devices as their primary means of an attack.
The risks associated with endpoints threaten organizational stability. Data loss or ransomware attacks can devastate operations and erode customer trust. However, the surge in connected devices—including the Internet of Things (IoT)—makes effective endpoint protection a challenge for administrators.
Employees are using their own devices
Bring-your-own-device (BYOD) policies have extended the workplace beyond the traditional enterprise perimeter. When employees use personal laptops and mobile devices for work, the organization’s attack surface naturally expands.
This approach introduces BYOD security risks, as these endpoints are often used for personal browsing and online activities, opening the network to various external cybersecurity threats. Endpoint security solutions can address these risks.
The issues of remote work
Decentralized workforces are no longer an exception. However, employees frequently connect via vulnerable public Wi-Fi or outdated home routers that may be compromised (or already belong in zombie botnets). Without proper safeguards, these unsecured connections leave the door open to cyber-attacks.
Cybercriminals are always targeting the weakest link
Public hotspots, such as cafés or transportation, are prime hunting grounds for threat actors. This significantly increases the risk of a breach. This means your employees are your perimeter.
Businesses of all sizes are targets
A common misconception is that only large organizations face data breaches. In reality, no business is too small to be attacked. Smaller companies often lack robust defenses, making them attractive targets for cybercriminals exploiting unpatched vulnerabilities. Modern endpoint security solutions provide the network visibility and control necessary to close these gaps.
Close the endpoint-to-network gap for SMBs with ease
Endpoint security, firewalls, and antivirus software
While both sound very similar, antivirus software is more common among home users, while businesses focus more on endpoint protection. One of the reasons is its scope: endpoint protection acts as a distributed antivirus for several computers, whereas home users usually secure one device at a time.
For this reason, antivirus software is installed on individual devices to remove malicious programs that may bypass other security measures. Traditional antivirus solutions are effective against a wide range of malware, including keyloggers, rootkits, worms, adware, and spyware. Yet, they aren’t as flexible in enterprise environments with multiple devices.
Endpoint security extends beyond basic malware removal. It uses advanced endpoint detection to identify threats before they compromise sensitive data. Modern endpoint protection platforms are installed across networked machines, allowing administrators to manage endpoint security centrally. This ensures consistent protection across the entire organization.
It differs from firewalls, which are network security devices designed to prevent unauthorized external access to the network. While some endpoint security software may have firewall-like capabilities, they are limited compared to dedicated firewalls. Firewalls focus on data packet inspection and monitoring which ports are accessed. Traditional firewalls typically operate only at the network layer.
To recap, endpoint security is a much broader discipline within cybersecurity. A firewall is a network or host traffic control tool, while antivirus software is a cybersecurity solution at the device level.
4 steps for building your endpoint security strategy
An effective endpoint security strategy is key to protecting your business against hacking attempts. Conversely, if a data breach occurs, an endpoint security strategy minimizes the damage or helps make sensitive data inaccessible to cybercriminals. Therefore, a robust security plan is a great way to improve network security and resilience. Here are four simple steps you can take to bolster your defenses.
Step 1: Encourage best practices
It's easy to forget that the biggest cybersecurity threat lies within your company's walls. Users are the primary guardians of endpoint devices. You must foster security habits throughout your organization, particularly among remote employees. Brief your team on protocols and encourage caution when using endpoint devices for work.
Step 2: Encryption
Ensure employees encrypt their traffic. Installing NordLayer on all endpoint devices reduces Wi-Fi breach risks and keeps sensitive data from being exposed. As an adaptive network security solution, it solves the challenge of company-wide implementation. NordLayer also comes with a range of benefits, giving users secure access to company resources wherever they are.
Step 3: Remote application control
Outdated systems contain vulnerabilities. Endpoint protection platforms must secure endpoints not only against malware but also against these software flaws. Legacy software should be sandboxed to limit contact between vulnerable applications and sensitive data.
You will find a wide range of endpoint security solutions on the market. Select a program that allows you to track and limit user activity. This includes blocking high-risk websites or restricting downloads to prevent malware infections.
Step 4: Antivirus software
While it’s an old cybersecurity staple, downloading antivirus software can be a strong last line of defense when malware bypasses other security checks. An antivirus system is a low-cost solution that effectively removes identified malware types (some of which, like ransomware, are common in businesses).
When used in tandem with other cybersecurity solutions, users receive comprehensive endpoint protection, as threats can be stopped at every stage. This is an effective way to increase endpoint protection and fortify the frontline of your network.
How can NordLayer help?
NordLayer provides IT security solutions to strengthen your endpoint security within the Zero Trust Network Access (ZTNA) framework. With cloud-hosted and hardware-independent tools, every single device within the network can be secured. This enables remote work without compromising security.
From data encryption to access control implementation, NordLayer can support your digital infrastructure transformation. Finally,integrations with services such as AWS or Google Drive enable seamless deployment within your current infrastructure.
Endpoint security doesn't have to be expensive or complicated. To find out more, contact NordLayer today.
Frequently asked questions
What is endpoint protection?
Endpoint protection focuses on preventing known threats from compromising devices, such as laptops, smartphones, and tablets. It acts as a shield for these network entry points.
How do endpoint security and protection differ?
The difference lies in their scope. Endpoint protection is just one part of the overall security strategy—it specifically targets the prevention of known, direct threats. Endpoint security, however, is a comprehensive approach that includes protective measures and also defends against indirect threats, such as network vulnerabilities and human error.
What is the difference between endpoint protection and antivirus?
Endpoint security software protects physical, virtual, and cloud-based devices from breaches. Antivirus is typically just one component of this broader security solution. Unlike antivirus alone, endpoint security provides centralized, cloud-based management to prevent sophisticated threats, such as vulnerability exploits, phishing, and fileless malware.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she has dedicated her life to simplifying complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.