
Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.
Cybersecurity

Summary: A weak security posture invites attacks. Improve it with SSE tools, segment networks, and use MFA to stay ahead.
The question isn’t if you will face a cyber threat, but when. The sophistication and volume of cyber-attacks, and the resulting risk of data breaches, continue to grow. A reactive approach to security is now obsolete and dangerous. Proactive defense is the new imperative. This requires building and maintaining a strong security posture.
This article will serve as your guide to understanding, evaluating, and enhancing your organization's cybersecurity posture. We will define what a security posture is, explain why it's critical for business survival, and provide ten actionable security best practices you can implement.
Your organization's cybersecurity posture is its overall cyber health. It's a comprehensive snapshot of your ability to prevent, detect, and respond to security threats.
Your security posture includes:
A weak posture, with numerous security gaps and vulnerabilities, is an easy target for attackers. In contrast, a strong security posture means your defenses are solid, monitored, and resilient against a wide range of attack vectors.
Treat a strong security posture not just as an IT concern, but as a fundamental business priority. The consequences of a weak stance can be devastating. They extend far beyond a temporary system outage.
A strong security posture is also a competitive advantage. It demonstrates to customers, partners, and stakeholders that you take cyber risk management seriously. This makes your organization a more reliable and trustworthy entity to do business with.
Before you can improve your security posture, you must first understand its current state. This begins with a security posture assessment—a systematic process that identifies and evaluates your organization's security readiness.
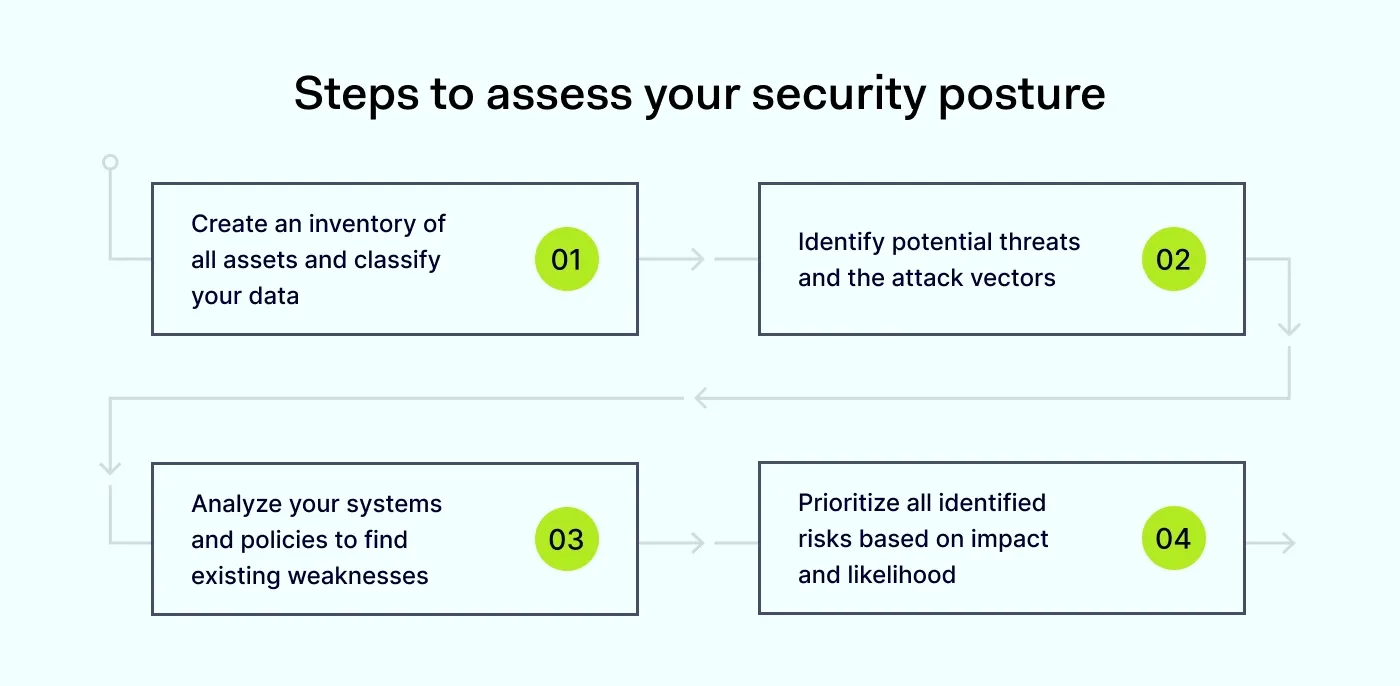
Once your assessment is complete, you will have a clear picture of where to focus your efforts. Here are ten essential security best practices to help you close security gaps and build a strong security posture.
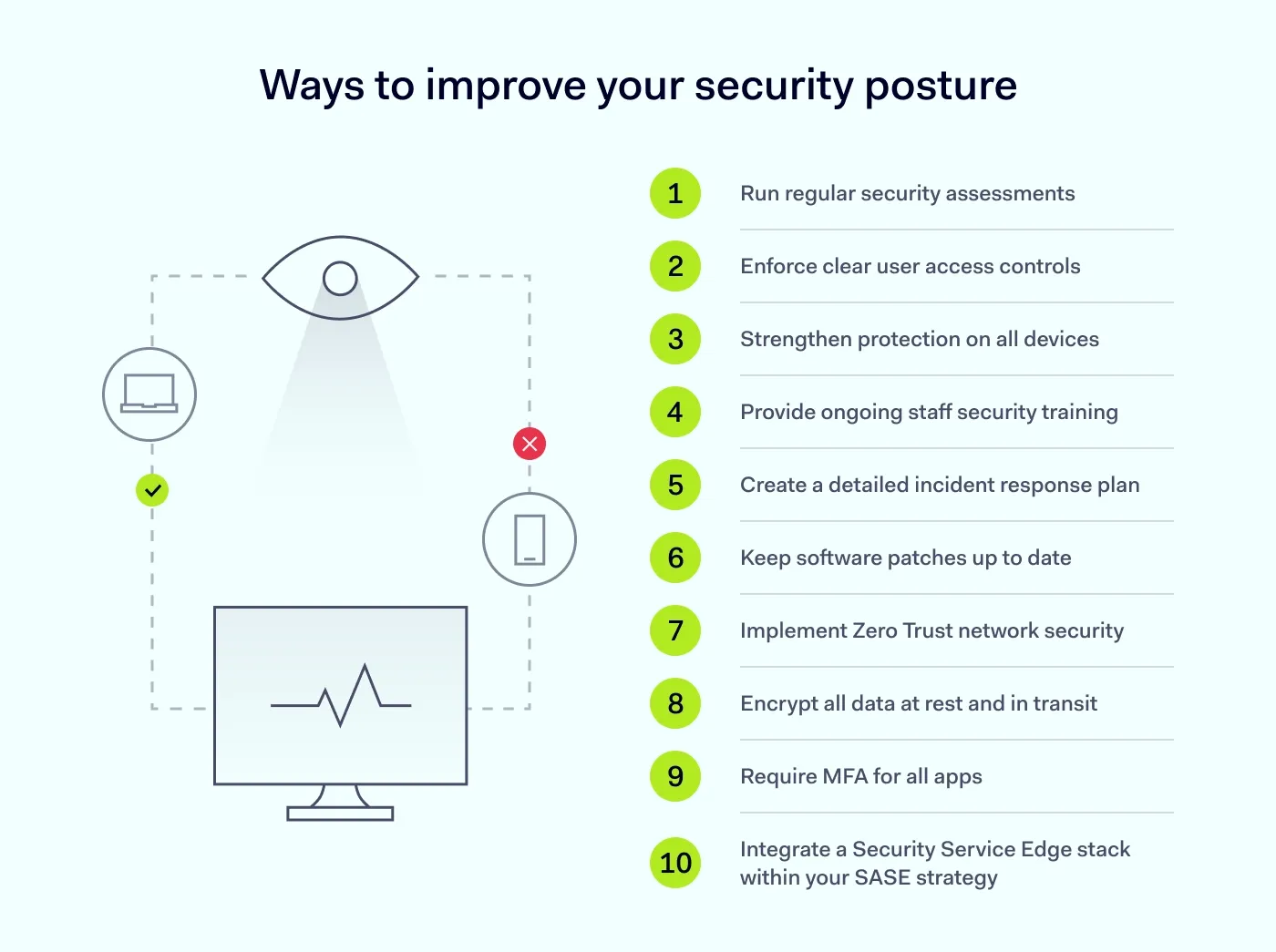
A security posture assessment is not a one-time project; it is a continuous process. Threats change, new technologies appear, and your attack surface expands. Schedule regular assessments at least annually, or quarterly for high-risk organizations, to keep your security strategy effective. This ongoing diligence is fundamental for a resilient defense.
The principle of least privilege (PoLP) must be the cornerstone of your access management. This principle dictates that users receive only the minimum level of access necessary for their job functions. Role-based access control (RBAC) is an effective way to apply this principle and assign permissions based on job roles rather than individuals. This drastically limits an attacker's ability to move laterally within your network if a user account is compromised.
Every laptop, server, or mobile phone connected to your network is a potential entry point for attackers. Your strategy must include strong endpoint protection. Deploy and maintain endpoint detection and response (EDR) tools, antivirus software, and firewalls on all relevant devices. Furthermore, device posture security checks confirm that only compliant and healthy devices can access your network resources.
Technology alone cannot stop all threats. Your employees are your first line of defense, but without proper training, they can be your weakest link. Establish a continuous security awareness program that trains staff to recognize and report phishing emails, social engineering tactics, and other common security threats. Regular training is one of the most cost-effective ways to improve cybersecurity and build a security-conscious culture.
It's a matter of when, not if, a security incident like a data breach occurs. A well-documented and practiced incident response (IR) plan is essential to minimize damage. Your IR plan should clearly define roles and responsibilities and outline the specific steps for an incident:
Unpatched software and systems are one of the most common security gaps exploited by attackers. Vendors discover vulnerabilities in software all the time and release patches to fix them. Your organization must have a formal process to promptly test and deploy these patches, especially for critical systems. You can significantly reduce your window of exposure and increase security posture if you automate patch management where possible.
The traditional security model is no longer effective. A Zero Trust framework fundamentally shifts your security mindset to "never trust, always verify." This model assumes that threats can exist both inside and outside the network. Every access request is authenticated, authorized, and encrypted before being granted, regardless of its origin. This is the gold standard for a strong security posture.
Encryption renders data unreadable to anyone without the proper decryption key. It is a critical control to protect sensitive information. You must use encryption for:
Compromised credentials are a common cause of cyber-attacks and data breaches. Multi-factor authentication is one of the single most effective defenses against them. MFA requires users to provide two or more verification factors to gain access to a resource, such as:
Enforce phishing-resistant MFA (FIDO2/WebAuthn) for all relevant accounts.
With remote work and cloud services, managing a fragmented collection of security tools can be complex and inefficient. Secure Access Service Edge (SASE) is an architectural framework that unifies networking and security services into a single, cloud-delivered platform. SASE simplifies management, provides consistent policy enforcement for all users regardless of location, and improves visibility. This unified approach helps eliminate security gaps and builds a scalable foundation for a truly strong security posture.
To achieve a strong security posture, you need a strategic blend of technology and policy. NordLayer provides an SSE solution that supports a SASE roadmap. It is designed to help organizations apply many of the best practices discussed above with ease and efficiency.
NordLayer allows you to improve your security posture:
Do not wait for a cyber-attack to expose your vulnerabilities. Take a proactive stance: build a strong security posture starting today.
Subscribe to our blog updates for in-depth perspectives on cybersecurity.