The internet is not a private place. Without protection, anyone can monitor your online activity. Malicious actors can track every website you visit, the videos you watch, and the emails you send. Governments can log the articles you read or the people you interact with. Competitors can steal your ideas and sabotage your marketing strategies.
The good news is that achieving internet privacy is possible. Businesses and individuals can use various techniques to conceal their identities online. And IP masking is a basic starting point for most of these privacy solutions.
This article will explore how IP anonymization works and discuss how to change your IP address.
The role of IP masking in internet anonymity
Masking your IP is the key to online anonymity. This is because IP addresses are the basis for our digital identities.
Your IP address locates you geographically and provides information about your Internet Service Provider (ISP). This information is like a digital street address and passport rolled into one. If attackers know your real IP address, they can assume your identity or trace your browsing activity. Concealing this address makes life much harder for attackers.
The privacy benefits of masking your IP are real and important. But it does have a darker side.
Online fraudsters use masked IPs to channel fake clicks to target websites. Also known as ad fraud, this type of crime generates revenue by fooling ad networks into thinking that sites are more popular than they are.
Secure your online identity and enhance safety by hiding your IP address with NordLayer's fixed IP
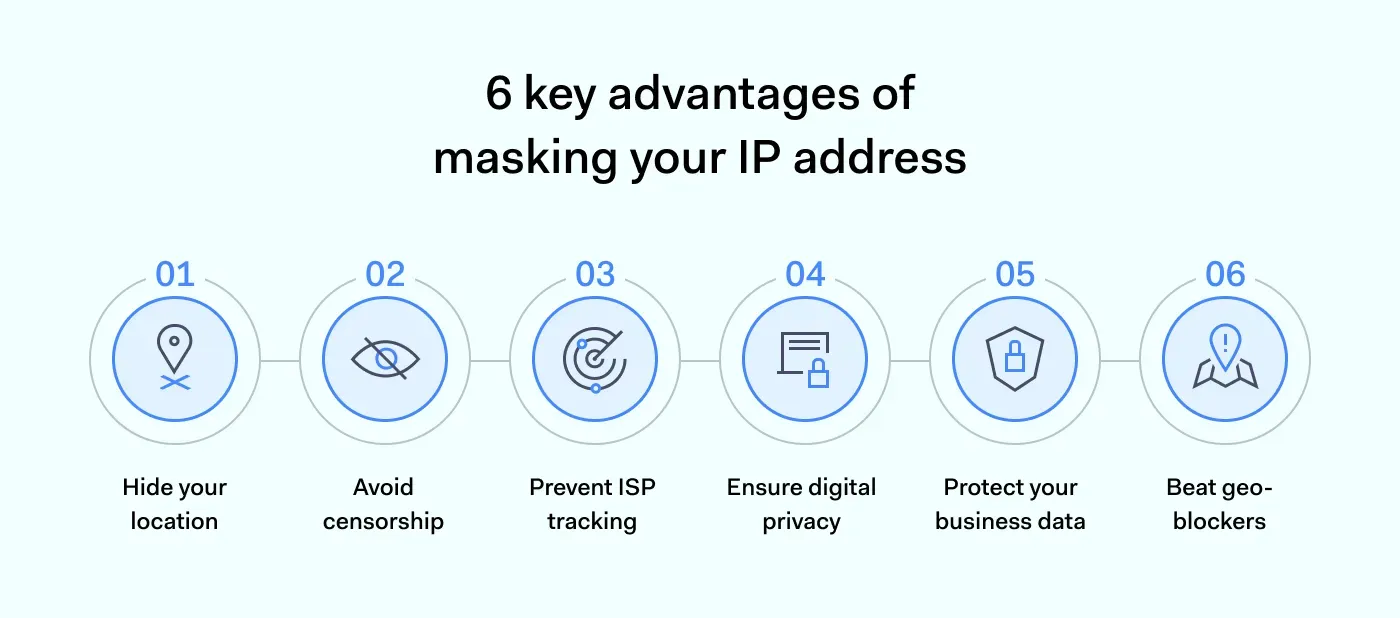
Six reasons why you should mask your IP
1. Concealing your location
IP information locates your device in the real world. If you want to remain anonymous and evade location-based filters, masking your IP is essential.
2. Avoiding censorship
Governments around the world seek to log the online activity of citizens. Masking your IP makes this much harder.
3. Preventing ISP throttling and tracking
ISPs may collect browsing data for internal purposes or supply the government with data if requested. If the ISP knows your IP address, it can also throttle your traffic. This restricts speeds for high-volume data consumers.
4. Digital privacy
Website cookies won’t be able to create profiles based on your browsing activity. Attackers will struggle to track your browsing, even on public Wi-Fi. And your communications with others will be anonymous.
5. Protecting business data
Competitors may track your employees to harvest sensitive information or project files. This is not possible if workers routinely mask their online identities.
6. Beating geo-blockers
Many online services filter traffic by the user's location. For example, Netflix varies the content available in different countries. When you hide your IP address, you can evade geo-blockers by posing as a user from another region.
What is an IP address?
Internet Protocol (IP) addresses are strings of numbers separated by periods or colons. Every device connected to the internet has an IP address. This is used to locate that device when communicating with servers worldwide.
Your IP information lets servers know where you are, making sending data to the right destination possible. Without it, browsing the web would be impossible, and the internet would collapse.
IP addresses can be classified as IPv4 or IPv6. IPv4 addresses have four numbers. IPv6 addresses have 8 four number codes separated by colons. Both perform the same role. IPv6 is simply more advanced and offers more potential addresses. This will allow the web to expand as more devices come online.
IP addresses can also be dedicated or shared.
Dedicated IPs belong to specific devices or websites. It won’t change over time and provides a fixed connection reference point.
Shared IPs are available for many devices to use. They are commonly used by VPNs or other masking services to assign new identities to users.
Choosing between a dedicated IP and a shared IP depends on your organization’s specific needs. Shared IPs are more affordable and practical for small businesses, while dedicated IPs are ideal for businesses that need more control over their online presence.
What is IP masking?
IP masking replaces your real IP address, giving you a new online identity. When users change their IP address, bad actors cannot easily detect their physical location or track their online activity. This guarantees enhanced internet privacy while allowing access to geo-blocked services.
How to hide your IP address
How can you disguise IP address data and assume a new online identity? Let’s quickly explain the most common methods and establish which solution works for you.
Use a VPN
Virtual Private Networks (VPNs) are servers that encrypt internet traffic and assign anonymous IP addresses for internet traffic. A Virtual Private Network lies between a user's device and the external internet.
The VPN usually owns a pool of shared IP addresses. When users connect with their original address, their data receives a shared IP. External observers and websites only see this new IP address. They cannot detect the identity of the user.
Benefits:
VPNs are one of the most reliable ways to hide your IP address. Your identity will remain private. Tracking your activity will be very hard.
The best services match privacy and speed. Users can stay safe without compromising application performance.
VPNs are well-suited to remote work. They are ideal for use on public Wi-Fi or during global travel.
Challenges:
VPNs can track user activity. Some keep logs and share user data with third parties.Pick a provider that prioritizes privacy and keeps logging to an absolute minimum.
VPNs can lead to performance issues. Routing traffic through a VPN server may reduce transfer speeds. This is particularly common with free VPNs.
Companies seeking watertight privacy should also choose a business VPN service. Personal VPNs are fine for handling consumer needs. But business VPNs can accommodate large numbers of remote users. That’s a core security issue as working from home becomes mainstream.
Use the TOR browser
The Onion Router (TOR) is famous as the gateway to the “dark web.” However, the TOR browser is freely available. It offers a powerful way to hide your IP address.
TOR routes traffic through a series of nodes run by TOR network volunteers. At every node, the TOR system peels off a layer of encryption. This also reveals the location of the next stage in the transmission. The route is unknown from the start, and the user’s real IP address is not exposed.
Benefits:
TOR network architecture delivers maximum privacy. That’s why dissidents in repressive countries often rely on TOR to evade censors and surveillance.
Challenges:
Privacy has a cost. In practice, TOR is much slower than its alternatives. This makes it a non-starter for many work applications.
TOR's slow performance can also cause privacy issues. In some cases, ISPs can detect TOR usage by monitoring lag times. Even though your IP information remains private, the ISP may respond by throttling traffic.
Users need to download and get familiar with the TOR browser.
Use a proxy server
Like VPNs, proxy servers lie between networks and the external internet. Unlike VPNs, proxy servers do not encrypt data. Instead, proxies mask IP addresses by assigning a fresh identity for packets passing through the proxy server.
Proxy servers forward requests from local devices and process responses. This creates a shield between the local network and external actors.
Benefits:
Speed. Proxies are usually very fast, so people often use a proxy to access streaming services.
Proxies also attach easily to most network architecture or home workstations. Just install a client and get started.
Challenges:
Proxies are generally the most risky way to change your IP. Proxies do not hide your IP address as data passes between local devices and the proxy server.
Because they lack encryption, proxies are also less dependable than VPNs when hiding user identities and guarding sensitive information.
Use dynamic IP addresses
A private IP address can be static or dynamic. A dynamic IP address is temporary, while a static private IP address is fixed. ISPs generally assign a dynamic IP address to private residential users. But business users can use specialist services to assign new addresses for each network connection.
Benefits:
Using dynamic addresses to hide your IP information is simple and fast. No installation is required.
Challenges:
Whoever provides the dynamic IP address will know your original identity.
Users do not benefit from encryption, making dynamic IPs a less secure way to anonymize online activity.
Use IP scrambling
IP scrambling is similar to proxy usage but with an important difference. Internet Protocol scramblers use a different proxy for every connection request. In other words, this technique usesrotating proxies to hide your IP address.
Benefits:
Scrambling IP information is a more secure alternative to proxy servers.
Challenges:
IP scrambling does not match VPNs for reliability and security.
Applying IP scrambling can be complex if users choose manual solutions. But this is less of a problem with automated scramblers.
Use Shared Gateway from NordLayer
Shared gateways use encrypted tunnels to connect remote users and internet servers. Companies can route remote traffic through the gateway and benefit from both encryption and IP masking.
NordLayer’s Shared Gateway pools IP addresses. Every user receives a fresh IP identity when they connect. This IP address is routed through one of NordLayer’s global servers.
Benefits:
Address assignment is randomized for each connection. This effectively masks your IP address while using the
gateway.
Shared gateways are a good alternative to proxies or standard VPNs. They are adapted for business needs and are fast to use.
Challenges:
The main drawback is that IP addresses can repeat at times. This may allow ISPs or websites to detect when users are logged into the gateway.
Use NordLayer’s Virtual Private Gateway
Virtual private gateways are more powerful than shared gateways. NordLayer’s Virtual Private Gateway routes data through secure tunnels to its destination. It also gives every packet an anonymized IP address.
The difference with shared gateways is that virtual gateways are private. Users do not share VPN servers with others, which adds an extra security level.
The virtual private gateway servers can be configured to access on-premise networks and cloud assets and also caters to remote workers. Users can set up network segments and apply DNS filters. They can combine IP masking with Deep Packet Inspection and Network Access Control.
Benefits:
Virtual private gateways are ideal for companies that want to integrate IP anonymization into their cybersecurity architecture.
Private IP addresses are not available to outsiders, making data transfers difficult to track.
You can create and extend a safe network perimeter for all your business information.
Challenges:
Virtual private gateways are not ideal for consumer users.
IP masking: key takeaways
Hiding your IP offers numerous benefits, allowing you to evade surveillance and beat geo-blockers. It is useful for both private individuals and business users.
Criminals can use IP anonymization to commit ad fraud and pose as legitimate users. TOR is the most reliable way to hide your IP address, but it is too slow for most situations. Proxy servers are fast but lack encryption. VPNs and related services blend TOR’s security with the efficiency of proxies.
Even with a masked private IP address, users are not completely secure. Encrypt data and install antivirus and malware scanners. And put in place access control solutions for sensitive data.
How can NordLayer help?
Privacy is a priority for individuals and businesses on today’s internet. IP masking is part of the privacy puzzle. If you hide your IP address, you can browse without worrying about external snoopers. However, masking solutions vary. Some are secure and reliable, but others are much less robust.
Virtual private networks are the best option for business users who want a private IP address. A good virtual private network delivers high speeds, encryption, and IP anonymization. That’s ideal for home use or while you travel.
Businesses requiring a centralized solution should look to encrypted gateways. NordLayer offers both Shared and Private Gateway. Both systems encrypt internet traffic and assign fresh IP addresses. And they are tailored for communities of remote and on-premises workers.
To find out more, get in touch with the NordLayer team. We'll find a way to anonymize your traffic from any external observers.
FAQ
How can I hide my IP address on a mobile phone?
Installing a VPN app is the best way to hide your IP address on a mobile phone. The NordLayer browser extension allows users to route traffic through servers in 33 countries. You can change your IP address instantly. That way, you can browse anonymously and work around geo-blockers with ease.
How can I hide my IP address on a browser?
Most VPNs let you hide your IP address when using web browsers. But you can also install extensions that only process browser traffic. For instance, NordLayer’s browser extension works with Chrome, Microsoft Edge, and Firefox. Employees can add the extension and securely access their company’s Virtual Private Gateway whenever they open their browser.
Does IP masking slow down internet speed?
Sometimes, but the slowdown isn’t always noticeable. TOR will slow down your internet connection significantly. But a good VPN or proxy server will hide IP data without slowing down the apps you use.

Agnė Srėbaliūtė
Senior Creative Copywriter
Agne is a writer with over 15 years of experience in PR, SEO, and creative writing. With a love for playing with words and meanings, she crafts content that’s clear and distinctive. Agne balances her passion for language and tech with hiking adventures in nature—a space that recharges her.