
Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.
Trends & statistics

Summary: The biggest 2025 data breaches show how identity abuse, misconfigured tools, and vendor access expose people at scale.
Paradox: attackers are becoming both more visible and harder to spot. Ransom notes and leaked sites often make headlines, while quiet mistakes and stolen tokens put sensitive data at risk for years.
This list of the biggest data breaches in 2025 keeps things straightforward, focusing on the facts. We’ll continue updating it until the end of the year as new numbers and investigations come in.
These are the biggest security failures of the year so far. Each one shows how simple mistakes or overlooked gaps can expose millions of people.
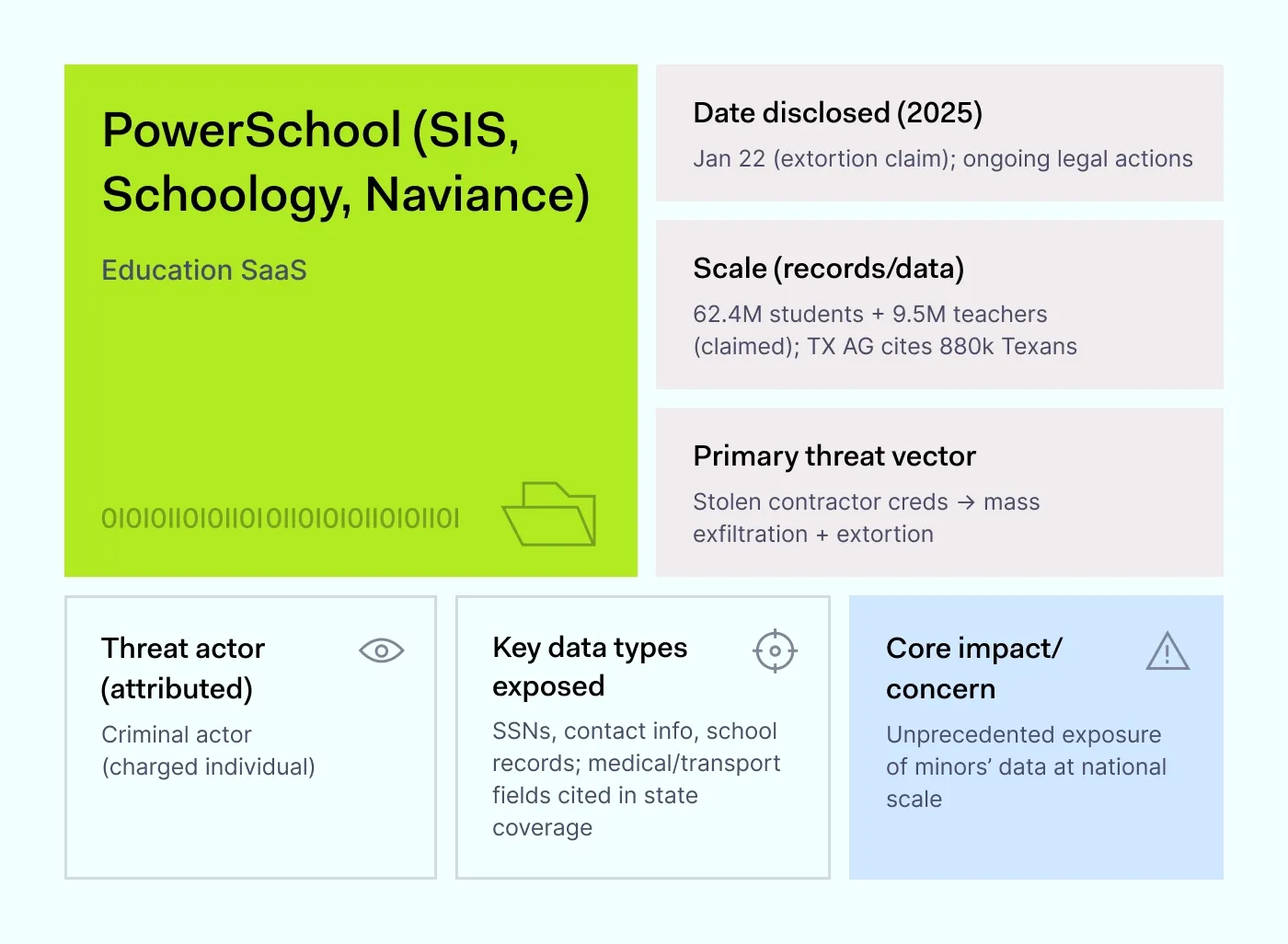
How it happened: In January 2025, someone claimed they had copied data for more than 62 million students and nearly 10 million teachers from PowerSchool’s systems. A few months later, Texas confirmed that 880,000 state residents were caught up in the breach. Investigators say the attackers got in using a contractor’s stolen login, which opened the door to school records nationwide.
By September, the Texas Attorney General filed a lawsuit against PowerSchool, calling it a major data breach that put minors’ personal information at risk. In some states, public filings mention names, contact details, and Social Security numbers. In other areas, school transportation and medical information may also have been exposed.
Why it matters: PowerSchool isn’t just one app; it’s a student information system that schools use to track enrollment, grades, bus routes, and family contacts. When attackers get inside, the damage spreads fast. Districts that link PowerSchool to other apps may now have to rotate passwords, check logs for strange activity, and clear out old accounts before those links become the next problem.
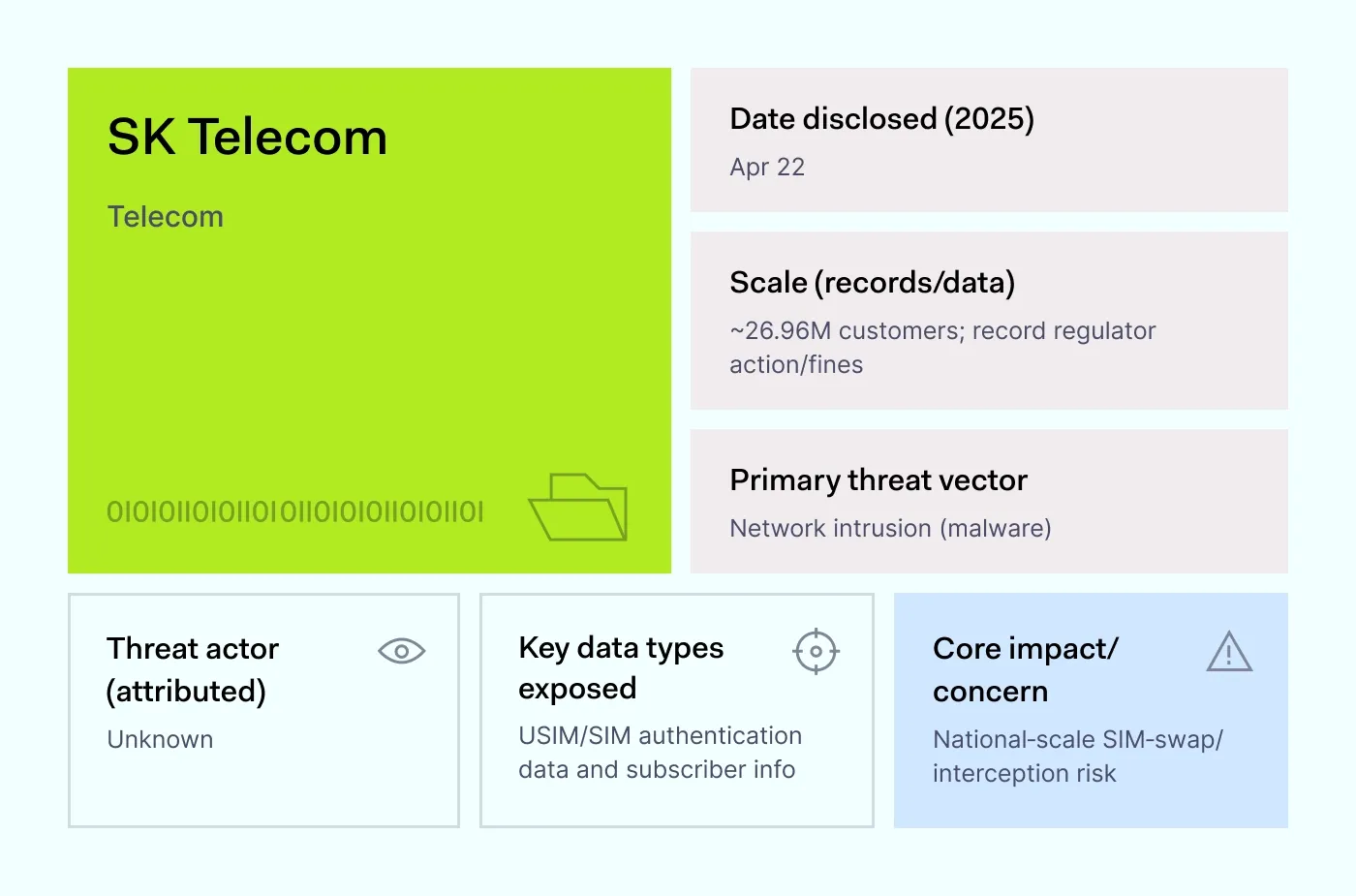
How it happened: In April 2025, South Korea’s biggest telecom provider admitted that attackers had stolen authentication records tied to USIM (Universal Subscriber Identity Module) cards. A USIM is the tiny chip inside a phone that lets the carrier verify your identity on the network. Regulators later said malware had been present in SK Telecom’s systems for years before the company caught it.
The exposed records could allow criminals to clone SIM cards, hijack text messages, and take over online accounts. Officials described the case as nationwide in scale, with 26.96 million customers affected. The government fined the company and ordered it to improve controls and monitoring.
Why it matters: SIM data may not sound dramatic, but it’s powerful. Banks, email providers, and social apps often send log-in codes by SMS. If attackers can duplicate a SIM, they can grab those codes and bypass account protections. Even partial leaks become dangerous when combined with sensitive data already traded on the dark web.
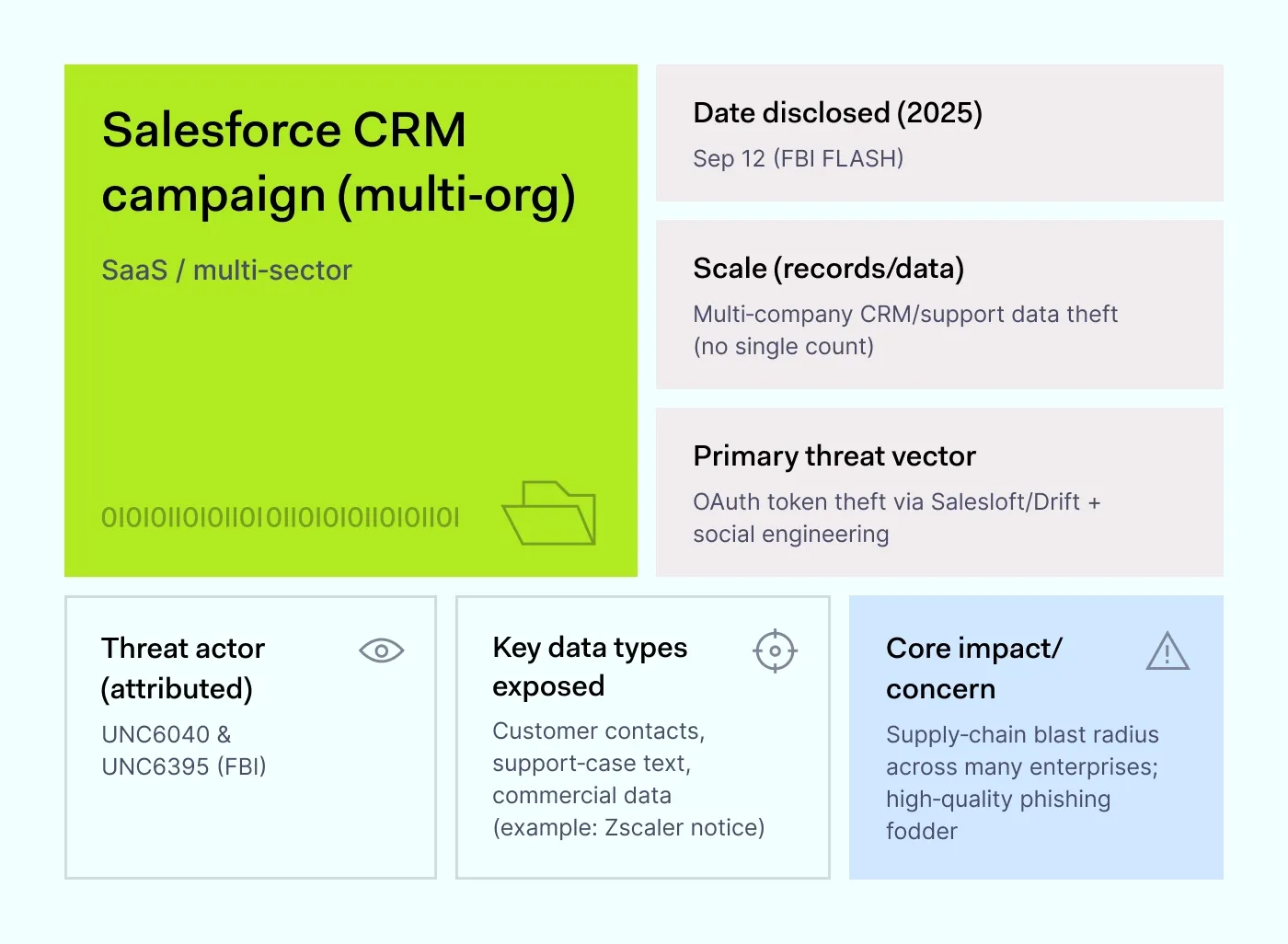
How it happened: In September 2025, the FBI issued a warning about two groups it tracks, UNC6040 and UNC6395. Both were quietly stealing customer data from Salesforce tenants. One group used vishing—phone calls that trick employees into giving up multi-factor codes—and then ran Salesforce’s own Data Loader tool, which is normally used by admins to bulk import and export data.
The other group relied on stolen OAuth tokens, which are digital keys that let connected apps (like Salesloft or Drift) act on a user’s behalf without asking for another password. With those tokens, the attackers could query Salesforce data directly. Multiple companies later confirmed they were affected and notified customers.
Why it matters: This wasn’t ransomware with loud lock screens. It was the quiet theft of CRM records: names, phone numbers, emails, business contacts, and support tickets. Because many companies use the same third-party apps, one compromised token can ripple across dozens of organizations. What looks like a small slip can easily become another entry in the growing list of recent data breaches.
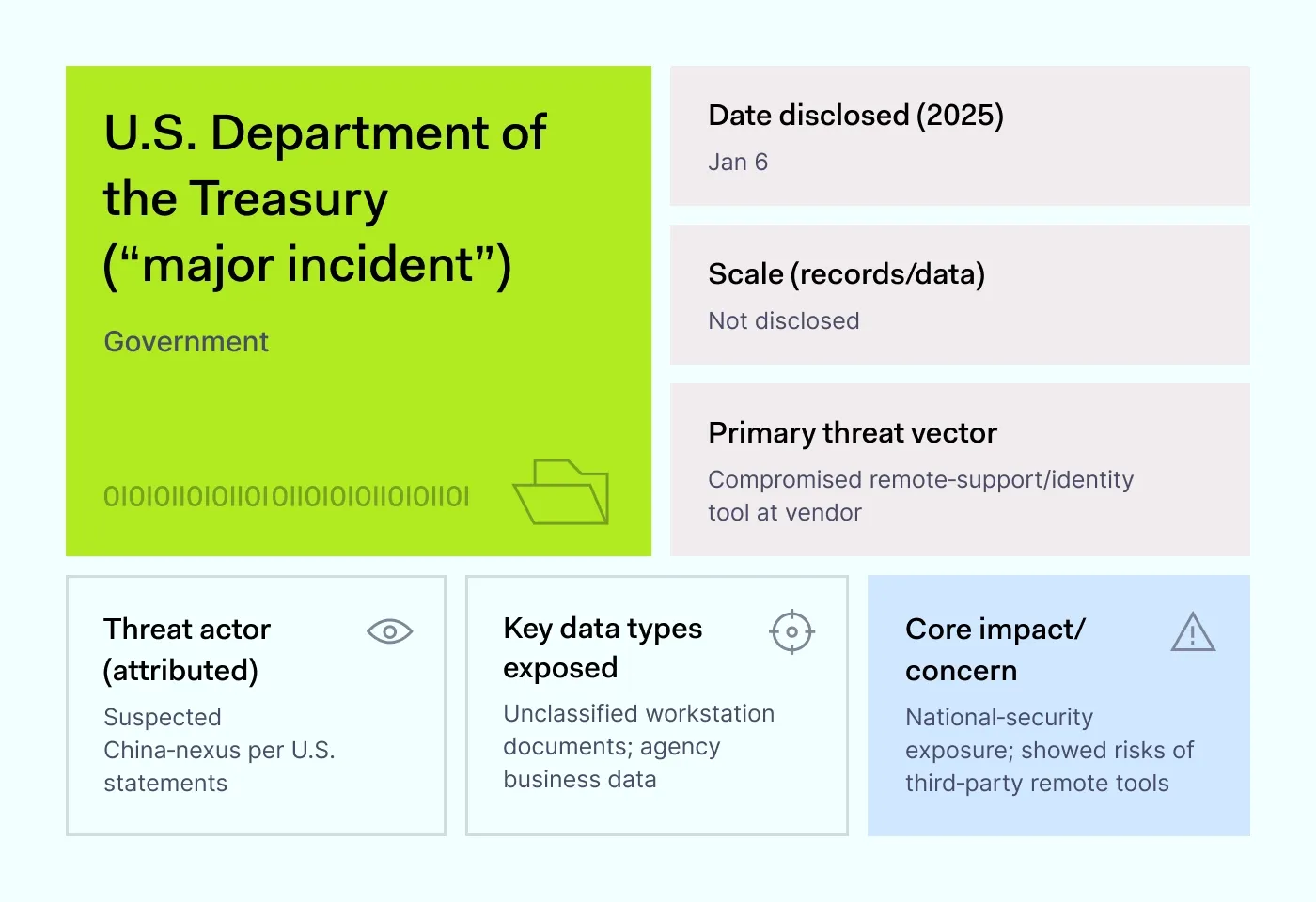
How it happened: In late December 2024, the U.S. Treasury learned that cybercriminals had broken into a contractor’s remote support tool. These tools let outside vendors log in and fix systems as if they were sitting inside the office. In this case, the attackers used that door to reach unclassified Treasury computers and documents.
The incident became public around the New Year and carried over into 2025, with investigations pointing to a group linked to China. It matters for a data breach 2025 list because this vendor tool is everywhere. A single weak login or too much access can give outsiders control over a whole agency.
Why it matters: One small help desk session can turn into control of hundreds of machines. Businesses that rely on contractors face the same risk. Stronger logins, verified devices, and limits on what vendor tools can touch are key to reducing exposure.
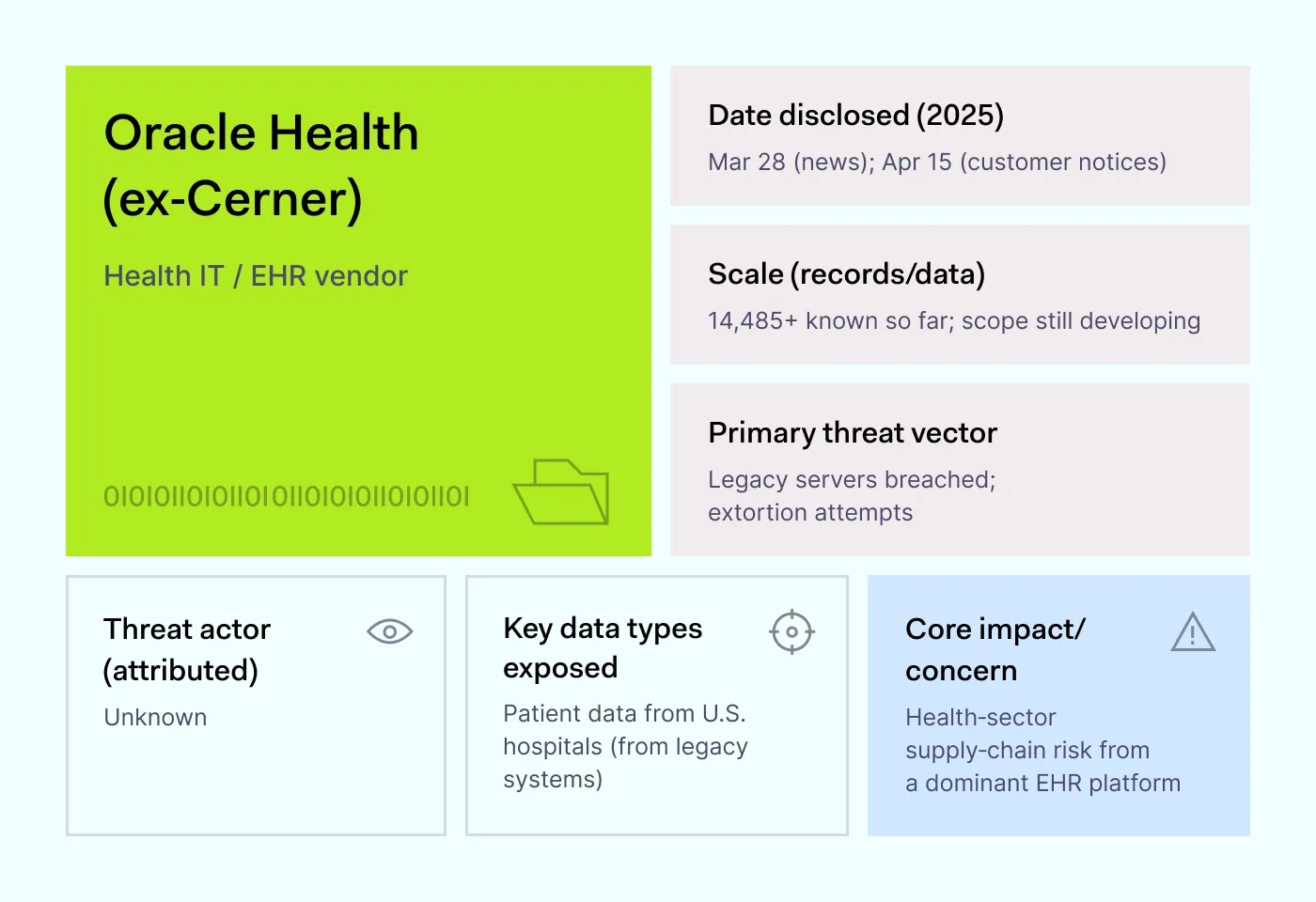
How it happened: At the end of March 2025, hospitals reported that threat actors had broken into old Cerner “data migration” servers. These were outdated, on-premises systems that some facilities still used to move patient information into newer platforms. Oracle Health later confirmed that these obsolete servers were compromised, but insisted its cloud systems were not.
Notices through the summer named at least 14,485 affected individuals, though the real number is likely higher. Because Cerner is connected to many hospital environments, the breach spread risk far beyond one location. Even when only old servers are hit, the mix of names, IDs, and medical details creates a long-term privacy headache.
Why it matters: Health data lasts for life, and attackers know it. Old servers and forgotten accounts often sit unpatched, waiting for someone to exploit them. One weak system at a big vendor can ripple through dozens of hospitals at once.
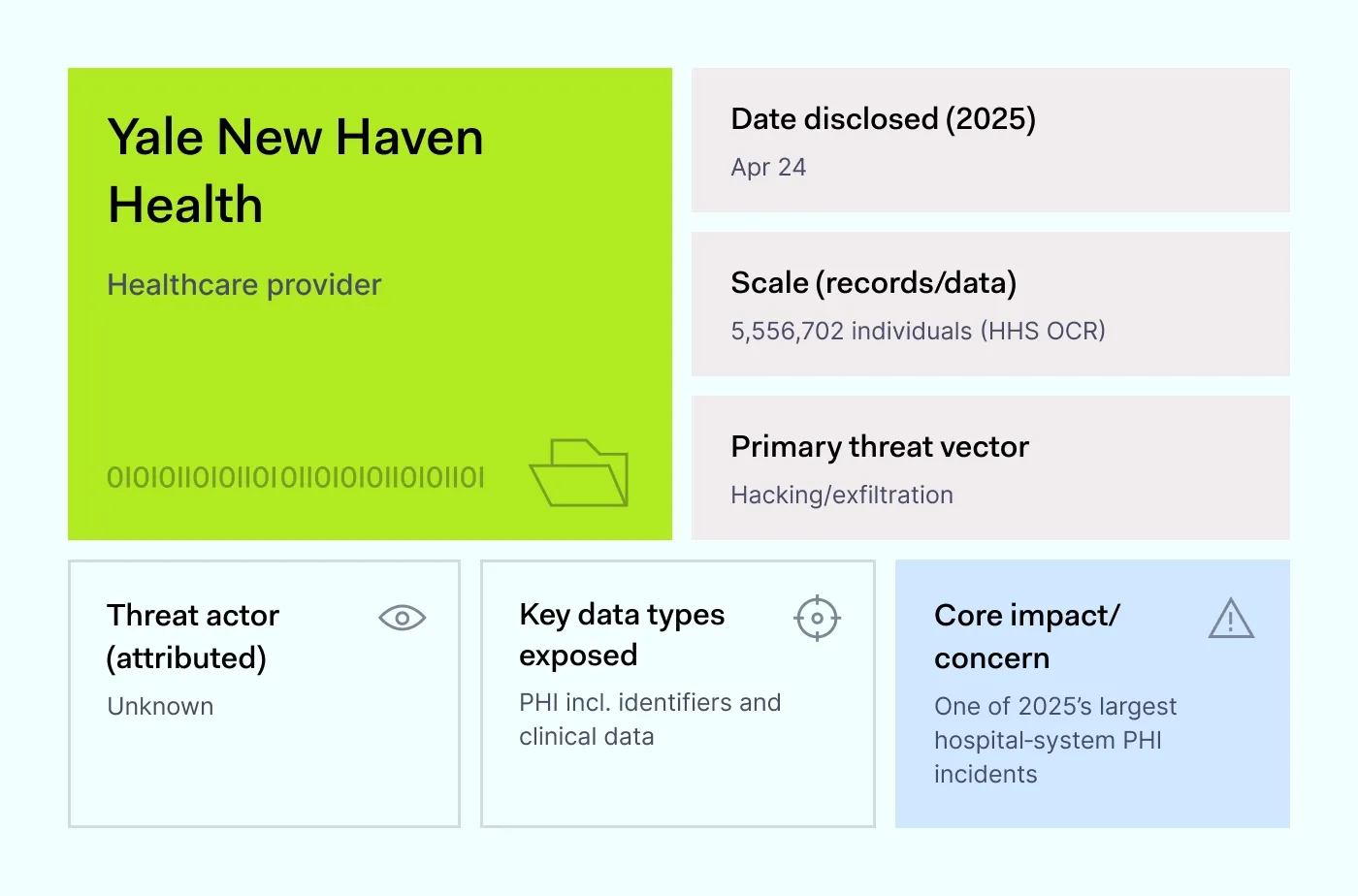
How it happened: On April 11, 2025, Yale New Haven Health said hackers had been inside its systems since March 8. The disclosure put 5.56 million people on the federal breach portal. The leaked files included demographic details and other protected health information, the kind of data that fuels scams and identity theft.
Patients quickly filed lawsuits, and by late summer, the health system was already in settlement talks. For context, 5.5 million people are equivalent to the population of a small U.S. state. Losing that much personal information in one go makes this one of the biggest hospital breaches of the year.
Why it matters: Hospitals can’t simply turn off systems to fight cybercriminals. They must continue treating patients while responding, which makes containment harder. That constant pressure leaves cracks open, and attackers exploit them.
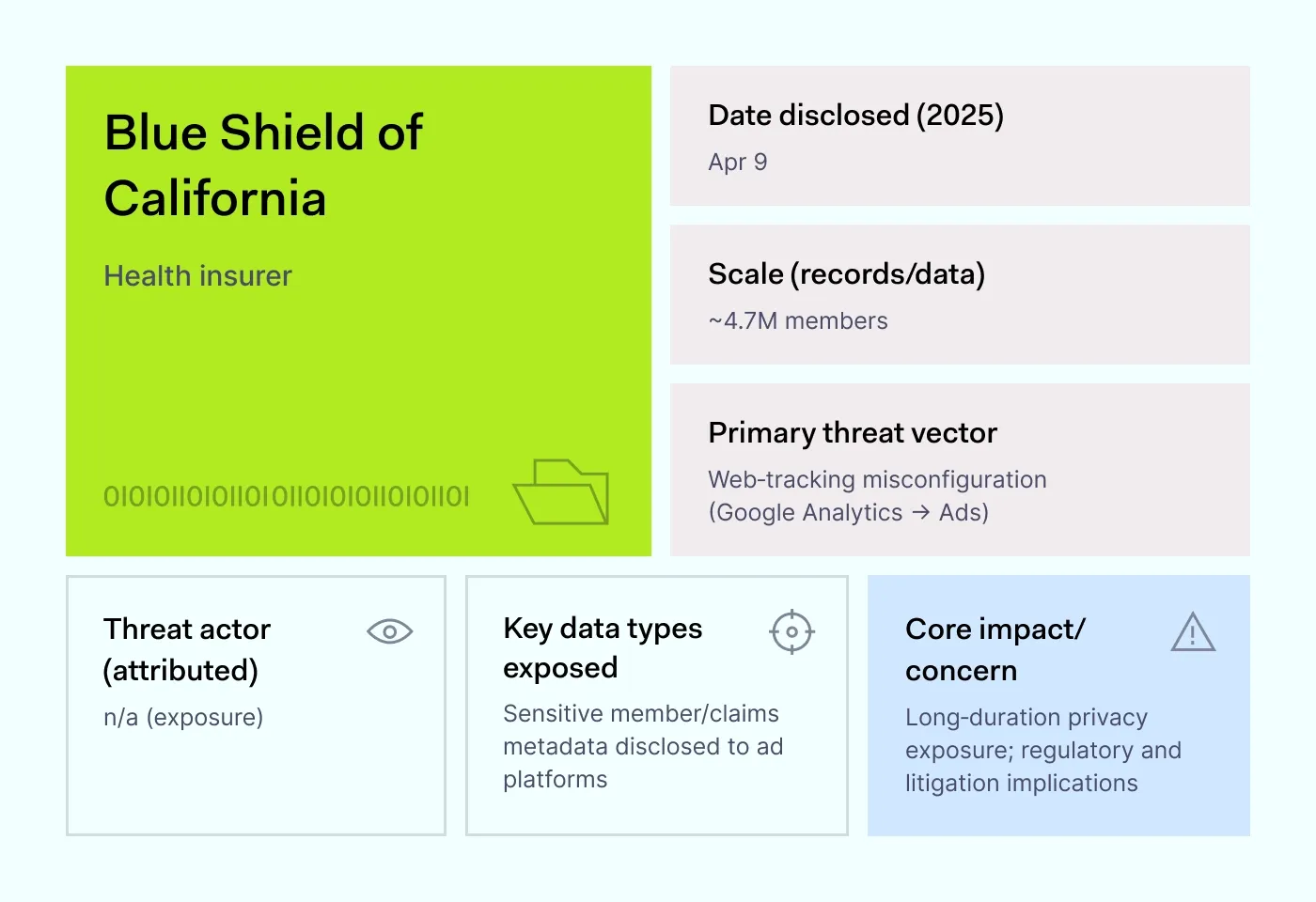
How it happened: On April 9, 2025, Blue Shield of California admitted that a misconfigured Google Analytics setup had been quietly leaking member data to Google Ads for years. No cybercriminals were involved. Instead, a tracking tool meant for marketing accidentally sent private information to advertising systems.
About 4.7 million people were affected. While full medical charts and payment cards weren’t exposed, browsing histories, plan details, and claims data slipped out. That information can still be valuable for profiling and targeted ads.
Why it matters: Not all breaches involve a break-in. Sometimes the problem is a tool left in the wrong place with the wrong settings. These hidden leaks rarely set off alarms, which makes them even harder for companies to spot.
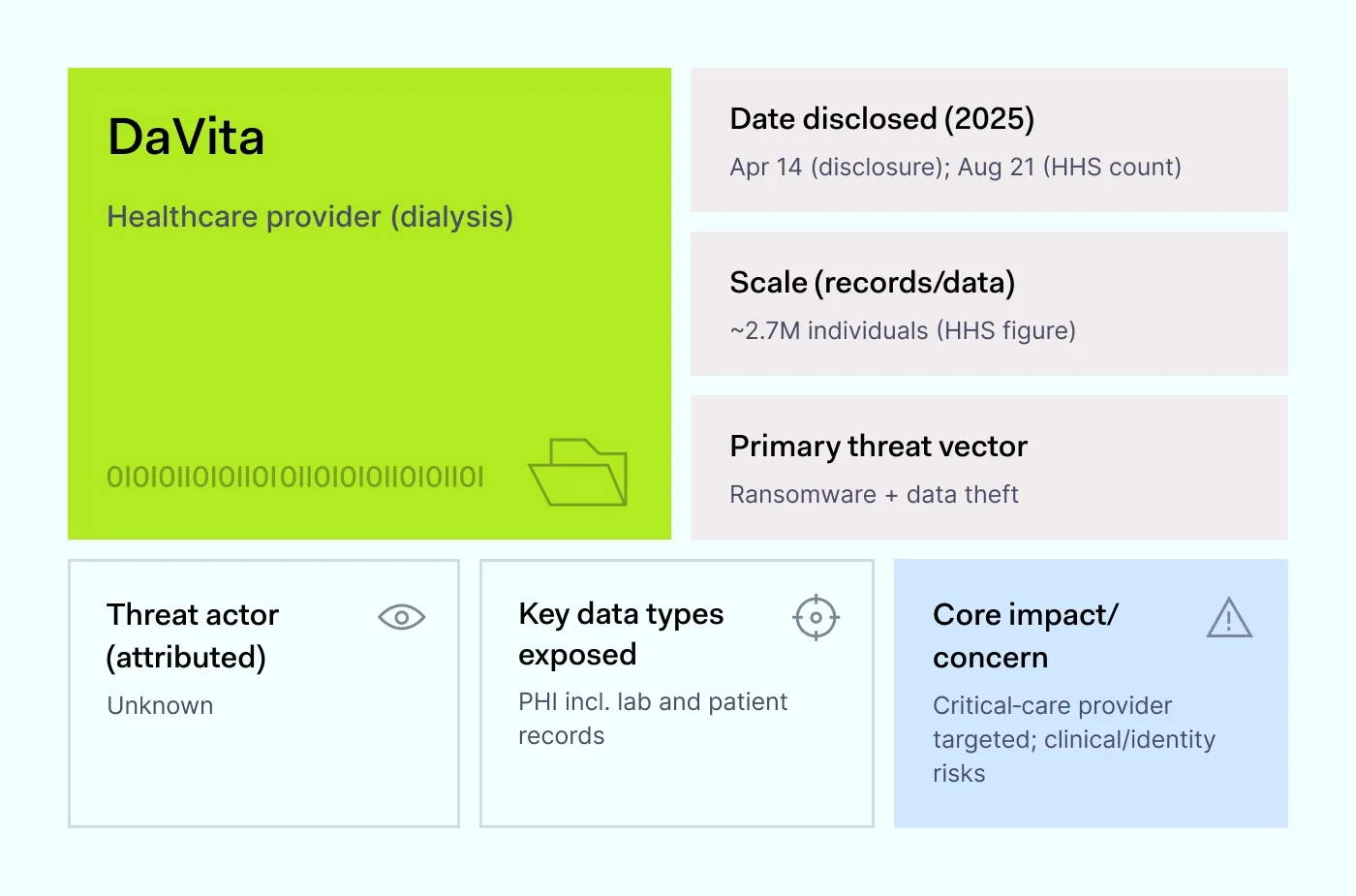
How it happened: In mid-April 2025, DaVita, a large dialysis provider, reported a major ransomware incident. The attackers not only encrypted systems but also exfiltrated patient records. Federal data later showed that about 2.7 million individuals were affected.
Reports indicated laboratory databases among the compromised systems. Clinics kept operating, but the exposure of medical details and identifiers created lasting privacy and fraud risks.
Why it matters: Modern ransomware is a two-step threat: copy the data first, then lock the systems. Even when backups restore operations, the stolen files often resurface on leak sites or the dark web. For healthcare providers, the cost is not just downtime but years of monitoring and dealing with lawsuits.
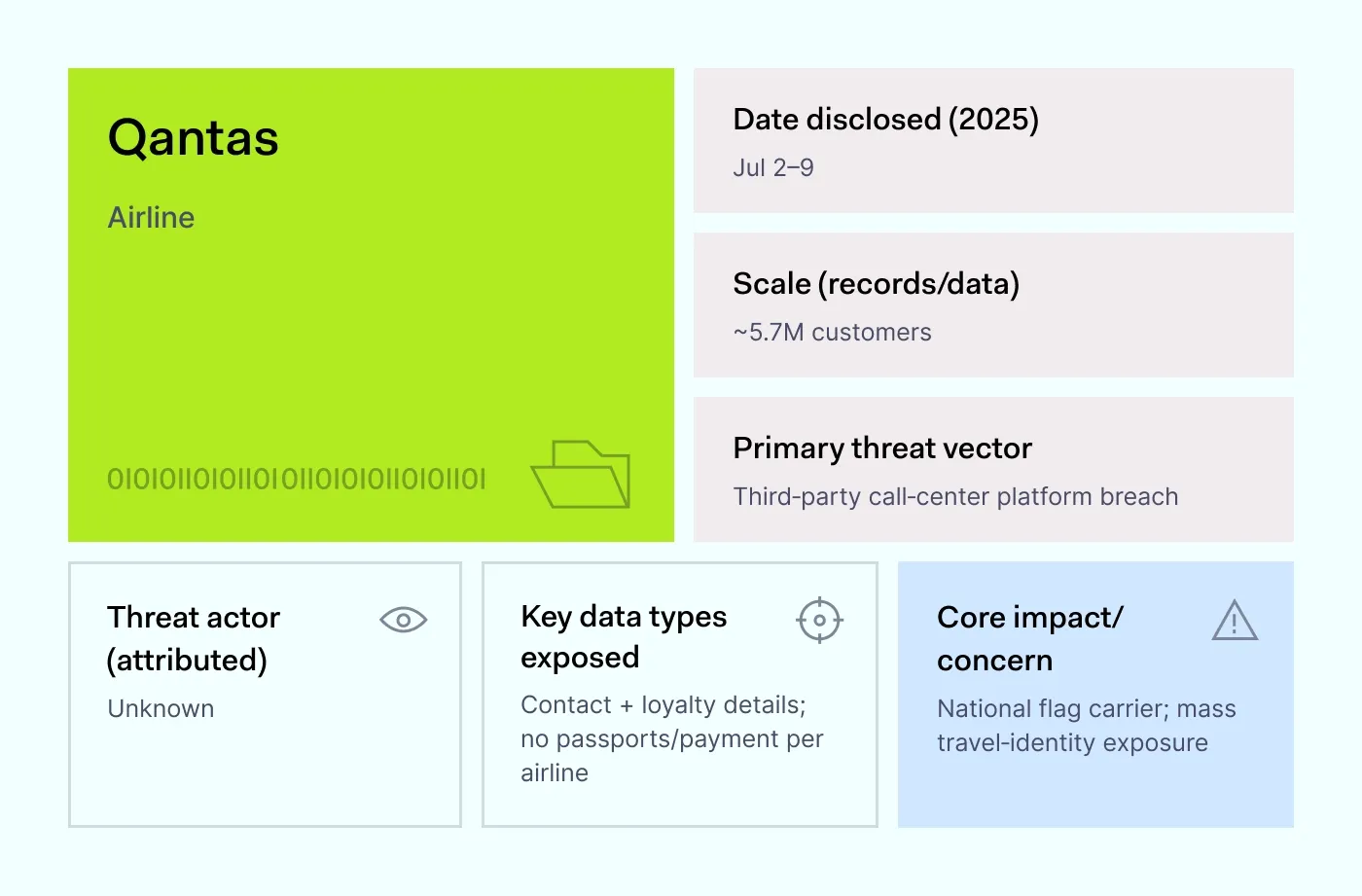
How it happened: Between July 2 and July 9, 2025, Qantas confirmed that a third-party contact center platform exposed data on 5.7 to 6 million customers. The information included names, emails, phone numbers, birth dates, and loyalty numbers. The airline emphasized that no passport or payment details were part of the breach.
The fallout was serious enough that executives saw bonuses cut, a measure aimed at showing accountability. For attackers, travel data is highly useful. It allows phishing campaigns that mimic real flights or loyalty offers, luring customers into giving away even more information.
Why it matters: Airlines rely on many outside providers for customer support, booking, and loyalty programs. A single weak vendor can compromise passengers across the network. This case mirrors other recent data breaches, where the company in the headlines wasn’t the one operating the vulnerable system.
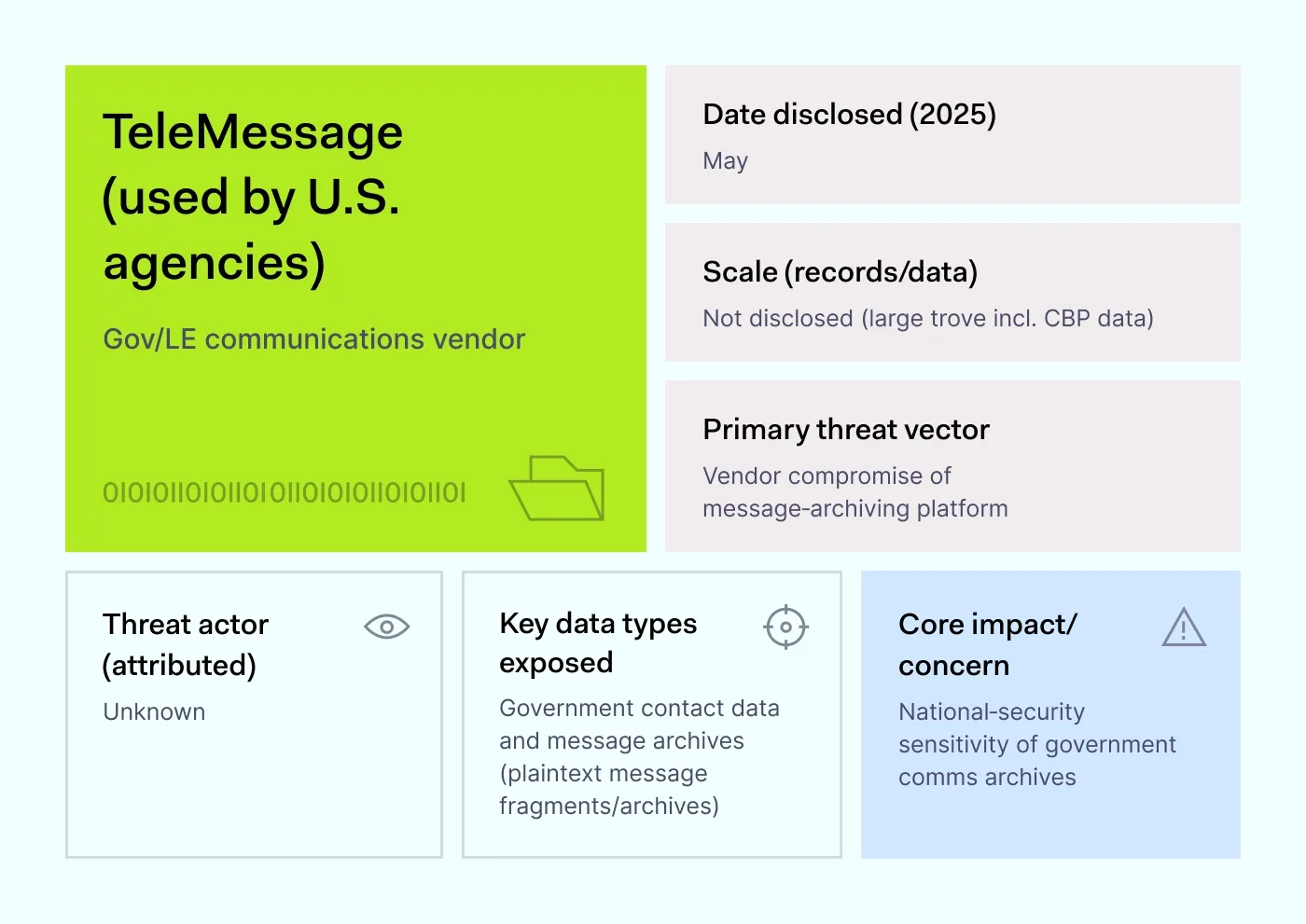
How it happened: On May 4, 2025, TeleMessage, a vendor that archives government communications, was breached. Collections of its data later appeared on activist sites that host leaked material. Reports said the exposed trove included plaintext message fragments, metadata, and government contact details, such as Customs and Border Protection addresses.
TeleMessage exists to meet legal record-keeping rules by storing copies of secure communications. But when those copies are kept in a less secure form, they become easier targets than the original encrypted apps. One point of entry can open an entire archive.
Why it matters: Archives centralize sensitive material. Without encryption, strict access, and short retention, archives become easier targets and raise cyber threats for every connected agency.
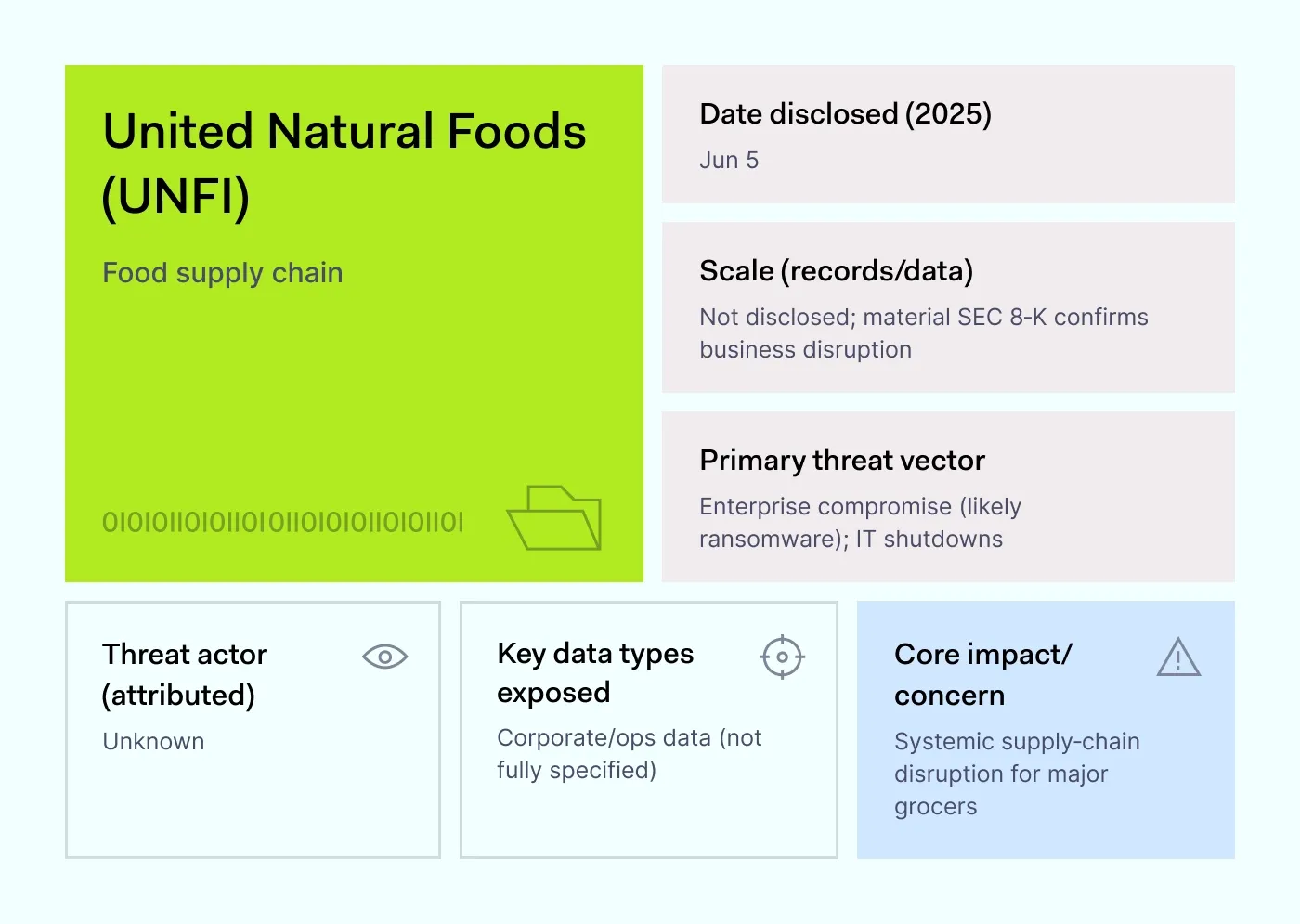
How it happened: On June 5, 2025, United Natural Foods filed an 8-K with the SEC saying it had shut down parts of its IT systems after a cyber incident. The disruption slowed order processing and food distribution, raising concerns about revenue and operations. For a supply chain that runs on tight margins and schedules, even short outages ripple quickly to store shelves.
The company did not release numbers on stolen or exposed records. Still, the case belongs in a data breach 2025 roundup because it shows how cyber incidents in logistics affect the public even when the scope of stolen data isn’t fully clear.
Why it matters: Logistics firms run on thin margins and tight schedules. Attacks here often combine data breach and downtime, which raises real-world impact even when record counts are not yet known.
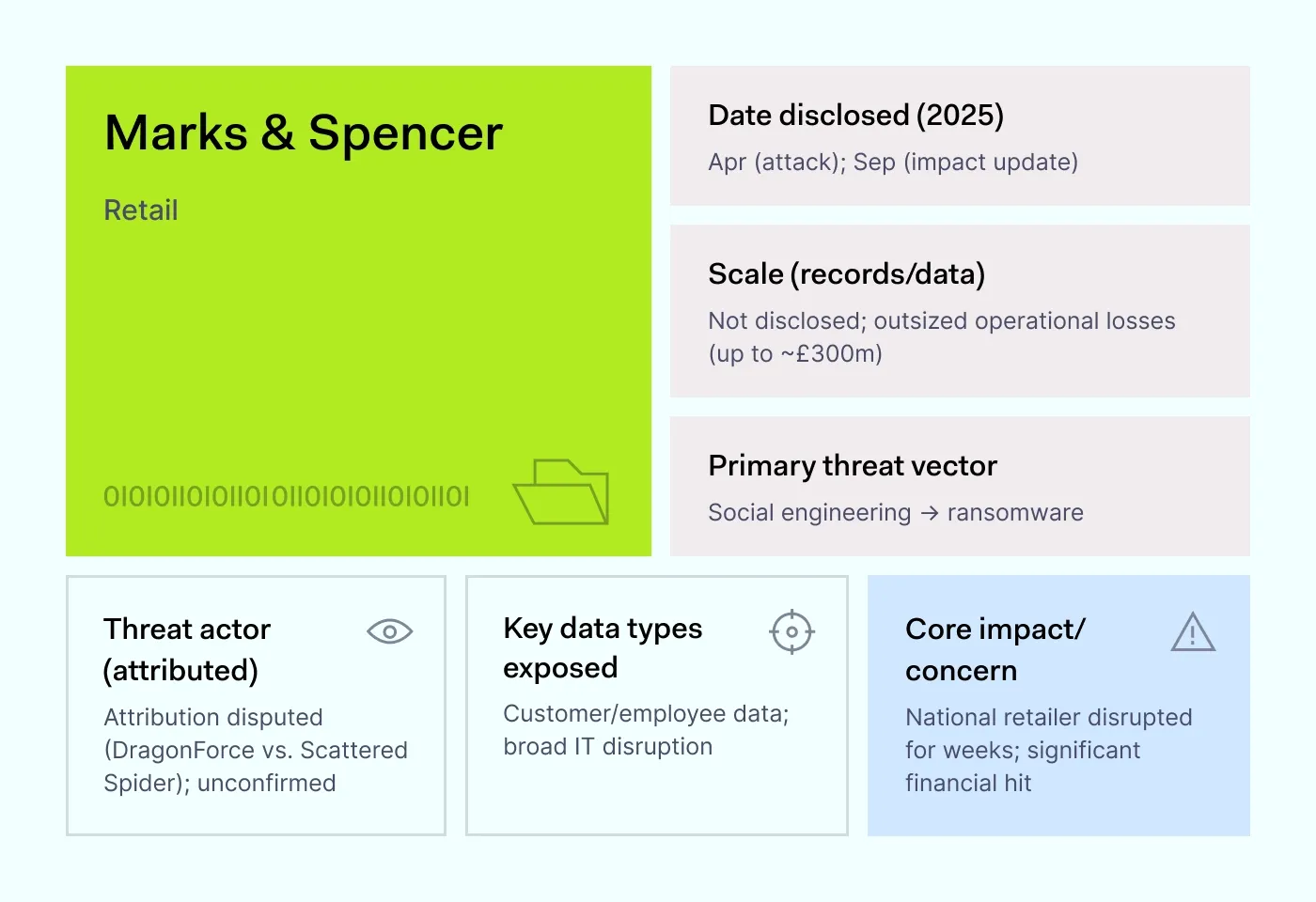
How it happened: In April 2025, Marks & Spencer faced a major disruption when threat actors used social engineering to gain access and launch ransomware. The attack crippled click-and-collect services and disrupted operations for weeks. By September, reports put the financial impact at around £300 million in lost profit.
Attribution bounced between different groups, but the tactics were familiar: convincing staff to hand over access that attackers then used to deploy ransomware and steal data. The retailer did not disclose how many records were affected, but the scale of the business disruption was clear.
Why it matters: Retail depends on always-on systems, from store checkouts to online orders. Once attackers seize accounts, they can shut down fulfillment and extract customer data in the same move. Preventing session hijacking, enforcing phishing-resistant MFA, and limiting employee permissions can block the kinds of tricks used here.
About one-third of breaches involve a partner or supplier. When access moves through help desk platforms, call centers, or SaaS connectors, every permission you grant becomes shared vulnerability.
Ransom demands cluster in the low six figures. As more victims refuse to pay, attackers increasingly resort to data-only extortion and multi-party pressure tactics.
The breaches at Yale New Haven Health, Oracle Health legacy servers, and DaVita show why: healthcare organizations have sprawling ecosystems, care that cannot pause, and long-lived records that keep high value to attackers. Average breach costs in healthcare sit far above the global average, and vendor issues keep reappearing.
Legacy servers, dormant accounts, weak MFA, and stolen browser cookies gave attackers simple paths. Infostealers and session hijacking turned browsers into skeleton keys, since many devices mix personal and work accounts on unmanaged endpoints. Edge gear with late patches added more vulnerabilities.
The picture is clear: bad actors pursue the path of least resistance—stolen identities, permissive tokens, neglected systems, and misconfigured analytics.
Executives do not need slogans. They need to make the blast radius smaller and remove clear vulnerabilities. The patterns across these 2025 data breaches point to direct controls that reduce cyber threats without stalling teams that ship products or care for patients.
The biggest 2025 data breaches show repeating weak points: stolen credentials, over-permissive vendor tools, and misconfigured systems that exposed sensitive data. To counter these, organizations need controls that reduce the chances of leaked data and shrink the impact if attackers get in.
NordLayer offers several tools that directly address these risks.
Together, these measures reduce the opportunities attackers exploited in many of the 2025 breaches. They reduce the chance that bad actors can exploit simple vulnerabilities, plant ransomware, or move stolen data to the dark web.
Subscribe to our blog updates for in-depth perspectives on cybersecurity.