Summary: Explore VNC basics, security risks, and how NordLayer’s Secure Remote Access and VPN keep remote connections safe and efficient.
If you're trying to use Virtual Network Computing (VNC) while working remotely, you’ve likely encountered the usual hurdles: blocked connections, security risks from exposed ports, and potential unauthorized access. From a security architecture perspective, there’s a safer, more efficient way to handle it.
VNC is a remote access technology that lets you control a remote computer as if you were sitting right in front of it. To safely access VNC from an outside network, a few best practices are essential. One of the most important is using a Virtual Private Network (VPN) to protect your data.
In this article, we’ll cover how VNC works, the risks involved, and how NordLayer’s Secure Remote Access solutions can make remote connections secure, efficient, and fully compliant.
What is VNC?
VNC is a graphical desktop-sharing system that allows users to control another computer remotely using the Remote Frame Buffer (RFB) protocol. Operationally, it transmits keyboard and mouse events from one device (the client) to another (the server), while sending graphical updates back to the client.
VNC is platform-independent and works across various operating systems, making it a popular choice for IT administrators, developers, and support teams who need remote access to servers or user machines.
How does VNC work?
VNC operates on a client-server model. The VNC server runs on the remote computer you want to control, while the VNC client (or viewer) runs on the device used for the connection.
When you initiate a session, the client connects to the server over TCP/IP (typically via port 5900) and exchanges display data using the RFB protocol. Port 5900 is the default communication channel that VNC uses to establish connections: each VNC display instance runs on a specific port (for example, 5901, 5902, etc.), allowing multiple sessions on the same host.
VNC client
The VNC client is the interface you use to access a remote device. It sends your input (mouse, keyboard) to the VNC server and displays the remote desktop.
VNC server
The VNC server runs on the remote computer and waits for incoming connection requests. It captures the screen and transmits it to the client. To make the server accessible outside your local network, you’d typically use port forwarding or a static IP address. Yet, that’s where most security risks arise.
Why exposing VNC on the internet is risky
When you open your VNC server to the internet through port forwarding, you’re effectively opening a door for potential attackers into your internal systems.
Is VNC secure by default?
Traditional VNC implementations transmit data—including usernames and passwords—in plain text. Without additional protection, anyone intercepting your network traffic could view or exploit those credentials.
Attackers often scan open ports, like 5900, to identify exposed VNC instances. Once discovered, these can be exploited through brute-force attacks, stolen credentials, or malware injection. Advanced risks include:
Lack of modern encryption support (e.g., TLS, SASL) in some VNC variants
Absence of native multi-factor authentication (MFA), leaving accounts vulnerable even with strong passwords
Related articles

Anastasiya NovikavaOct 8, 202513 min read

Aistė MedinėOct 23, 20259 min read
What is the RFB protocol?
The Remote Frame Buffer (RFB) protocol is the foundation of VNC. It transmits display and input data between the client and server. While simple and efficient, it was not originally designed with strong encryption or authentication, which makes VPN tunneling or secure remote access essential for safe use.
Understanding VNC vs. RFB: similarities and differences
Both VNC and RFB enable remote desktop access, but they serve different purposes within that process. Here’s how they compare:
Similarities:
Both enable remote control of a computer by transmitting keyboard, mouse, and screen data.
Operate on a client–server model, where a viewer connects to a host.
Both are platform-independent, working across different operating systems.
Differences:
RFB is the protocol that defines how data is transferred between devices.
VNC is the software built on RFB that enables actual remote desktop functionality.
RFB focuses on data exchange, while VNC provides a user-facing system that implements security, compression, and session management.
RFB lacks encryption by itself, so VNC connections often rely on a VPN or Secure Remote Access solution to stay protected.
In short, RFB is the language, VNC is the tool that speaks it.
How does VNC differ from VPN?
While VNC provides remote desktop control, a VPN creates a secure, encrypted tunnel for all your network traffic.
A Business VPN, like NordLayer, creates an encrypted tunnel that protects all communication between your client and server, shielding it from interception, credential theft, or unauthorized access. It also ensures that only verified users and devices can reach internal company systems through Zero Trust Network Access (ZTNA) and Secure Remote Access policies.
Used together, they provide end-to-end protection:
VNC = Remote desktop access, giving you visibility and remote control
VPN = Encrypted network tunnel, ensuring that data stays private and inaccessible to outsiders
With NordLayer, you can run VNC behind an encrypted tunnel, keeping your internal IP addresses hidden and eliminating the need for risky port forwarding—all while maintaining fast, reliable remote connections.
Keep calm and work from home
Rely on NordLayer VPN to safely access your company network no matter where you are
A secure approach: running VNC behind protected remote access
Instead of exposing VNC to the internet, the best practice is to run it behind a VPN or Secure Remote Access solution. This ensures that only authenticated users within a protected network can connect.
Here’s how it looks in practice:
| | |
|---|
| Exposed to the internet via port forwarding | Protected by an encrypted VPN tunnel |
|---|
| Anyone who finds the open port can attempt access | Only verified users/devices via Zero Trust |
|---|
| Public IP address is exposed | IP address masking hides the real IP |
|---|
| Must manually manage internal IPs | |
|---|
| | AES 256-bit and ChaCha20 encryption via Business VPN |
|---|
| | IP address allowlisting controls who connects |
|---|
With NordLayer, your VNC connections remain internal—even when working remotely—without needing to configure complex port forwarding rules or expose your VNC server to public networks. In other words, NordLayer eliminates the need for port forwarding altogether, simplifying your setup while maintaining a much higher level of security.
To achieve this, Secure Remote Access applies identity-based segmentation at the network layer. Each connection request is evaluated against the user and device context, ensuring only authenticated sessions can reach defined VNC endpoints. This replaces the static trust model of open ports with dynamic, policy-driven connectivity, while also logging and monitoring access for auditing and compliance purposes.
Benefits of using NordLayer for VNC
By integrating NordLayer with your existing VNC setup, you gain control, visibility, and encrypted connections without changing your workflow.
Traffic encryption: All traffic between the VNC server and client passes through a Virtual Private Network, protecting sensitive credentials and data from interception.
Secure Remote Access: NordLayer’s
Secure Remote Access framework means that only authorized users and devices can access private company resources. Each access request is verified, logged, and limited in line with Zero Trust principles.
IP address allowlisting: Using
IP allowlisting, you can specify exactly which IP addresses are allowed to enter your VNC environment. Unauthorized devices or networks are automatically denied access, minimizing the risk of compromise.
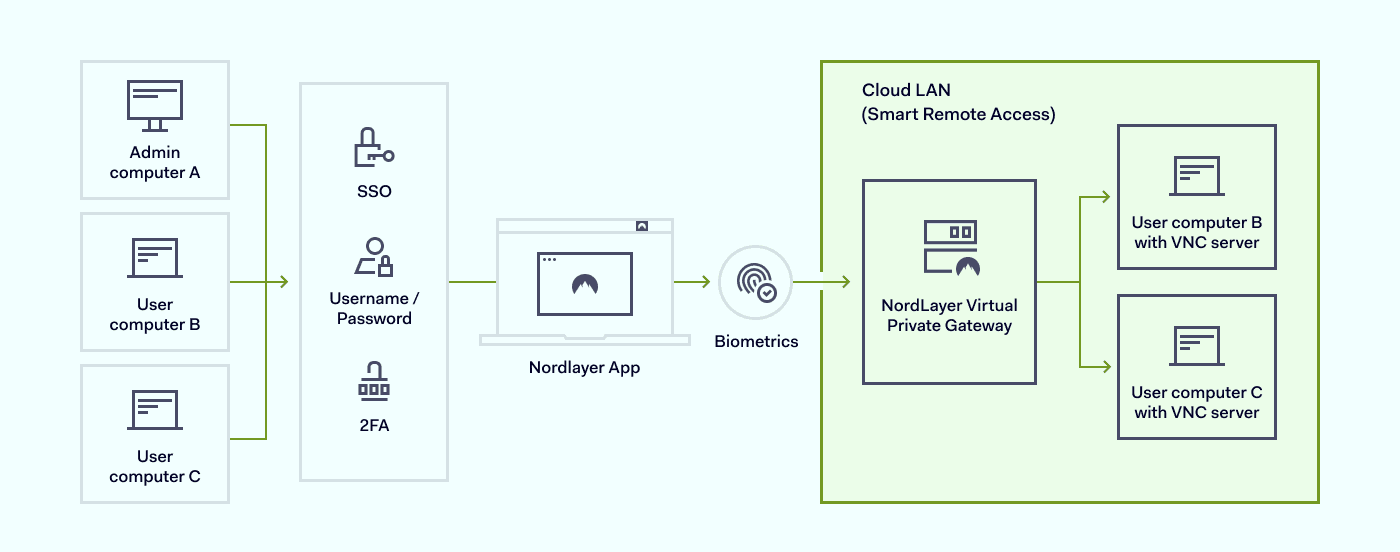
Cloud-based LAN: With
Cloud LAN, your distributed teams can access VNC as if they were on the same local network: no complicated internal IP address mapping or static IP configurations needed.
How to enable Secure Remote Access for your VNC setup
Setting up NordLayer to secure your VNC connections is simple:
Deploy NordLayer across your organization. Create an organization in the NordLayer Control Panel and invite team members.
Assign dedicated gateways. Configure
Dedicated IPs for internal VNC traffic to ensure consistent routing.
Enable Secure Remote Access. Set up private gateways and define access policies based on your team, device, or location.
Configure Cloud LAN. Allow your IT team or developers to securely reach devices and resources distributed across the public internet as if they were on the same local network.
Connect and work securely. Once connected to NordLayer, your team can launch their VNC Viewer, enter the internal IP address, and access remote devices safely—without any open ports or public exposure.
Final thoughts
Setting up VNC for remote access doesn’t have to mean compromising on security. By placing your VNC server behind NordLayer, you get all the flexibility of VNC along with encrypted traffic, IP allowlisting, and Zero Trust access controls.
Stop exposing ports to the internet. Instead, securely access VNC from outside the network with NordLayer’s Secure Remote Access as the smarter way to connect.
Have questions? Contact our sales team or explore our Control Panel demo to see how it works in practice.

Agnė Srėbaliūtė
Senior Creative Copywriter
Agne is a writer with over 15 years of experience in PR, SEO, and creative writing. With a love for playing with words and meanings, she crafts content that’s clear and distinctive. Agne balances her passion for language and tech with hiking adventures in nature—a space that recharges her.