Threat Prevention solutions
Neutralize cyber risks before they reach you—and act efficiently if they do. Bundle NordStellar with NordLayer for a comprehensive approach to threat prevention.
Overview
What is Threat Prevention?
Advanced Threat Prevention refers to the strategies and measures used to identify, mitigate, and defend against potential attacks targeting your network and systems. By integrating NordLayer’s network security and NordStellar’s detection capabilities, you minimize risks and can act fast if threats bypass your defenses. This combination covers every aspect of cybersecurity, protecting your business from unauthorized access, malware infections, leaked employee credentials, and other security incidents.
Secure the company network
Protecting only the perimeter is no longer enough—implement multi-layered access controls to ensure complete network security.
Safeguard devices regardless of location
Secure your devices against outside threats and detect jailbroken devices that could be used for malicious purposes.
Respond to incidents quickly
In the event of a perimeter breach, quick action is needed to narrow the area of attack and limit the scale of infiltration.
COMPREHENSIVE DEFENSE
Defend, detect, and respond with NordLayer & NordStellar
NordStellar is a threat exposure management platform that provides real-time visibility from an external perspective. When combined with NordLayer’s robust network protection, you get a powerful defense system. NordLayer safeguards your network perimeter, while NordStellar detects data leaks and infrastructure vulnerabilities early—allowing you to respond effectively. Together, they ensure you stay protected from all angles.
START WITH PREVENTION
Inside NordLayer’s Threat Prevention framework
NordLayer strengthens your organization’s cybersecurity by combining access control, encrypted connections, and intelligent traffic filtering. These capabilities work together to reduce risks and maintain a resilient network environment.
VPN encryption for safe data transfer
Encrypts all network traffic to protect data in transit and prevent interception or eavesdropping. Even on public networks, sensitive information stays private and secure.
Access control & multi-factor authentication
Controls access to your systems and privileged accounts with strict authentication policies, preventing unauthorized entry and reducing the risks of credential-based attacks.
Reliable & secure VPN connections
Establishes encrypted tunnels between users and company resources, keeping communications tamper-proof, private, and safe from Man-in-the-Middle (MitM) attacks.
Cloud Firewall & Network Segmentation
Divides your network into secure zones to contain breaches and limit lateral movement. This isolation minimizes damage if an attacker gains access to one part of your system.
DNS Filtering & Download Protection
Filters traffic to block access to malicious websites and includes malware detection to identify infected files before they can cause harm—keeping users and data safe from threats.
Interested in dual-layer defense?
Strengthen your company’s protection with NordLayer’s network security and NordStellar’s data leak detection. Contact our team for the best deals on this dual-layered solution.
NordLayer + CrowdStrike Secure your network, data, and endpoints together
Every growing business deserves the right to protect what matters most. With NordLayer and CrowdStrike, you can move forward with confidence, knowing that your network, your devices, and everything in between are safe and secure. Here’s how:
Stop ransomware attacks with AI-powered protection
Block attack vectors and proactively protect all your endpoints
Stop ransomware attacks with AI-powered protection
NORDSTELLAR DETECTION
Strengthen your security posture with continuous threat management
Gain real-time visibility into data leaks and infrastructure vulnerabilities before they escalate. Continuous monitoring and actionable threat intelligence help your team stay ahead of risks and respond with confidence.
Data breach monitoring
Monitor the deep and dark web for exposed employee or company data to detect leaks, compromised credentials, and prevent potential breaches.
Dark web monitoring
Track business-related keywords across dark web sources to spot potential data leaks early and stop them from turning into major security breaches.
Account takeover prevention
Detect compromised credentials across the deep and dark web to secure user accounts and prevent identity theft or online fraud.
Attack surface monitoring
Track your external assets—like domains, IPs, and cloud resources—to spot vulnerabilities, assess risk, and uncover suspicious activity early.
Session hijacking prevention
Identify users impacted by info-stealer malware, detect compromised session cookies, and block affected devices to prevent unauthorized access.
See how proactive threat management works in practice
Learn how ongoing monitoring, data leak detection, and threat insights come together to keep your business one step ahead of cyber risks.
CYBER-ATTACK STATISTICS
Attackers target corporate networks
76%
of businesses experienced a cyberattack in the last year
65%
of companies say data breaches have negatively impacted reputation
65%
of IT admins say the severity of attacks is increasing
Free guide: protect your team with tips to avoid malicious websites & their hidden risks
FEATURES
Explore our cybersecurity features
Web Protection
Network segmentation
2FA
Cloud LAN
Jailbroken device detection
Biometric authentication
SSO
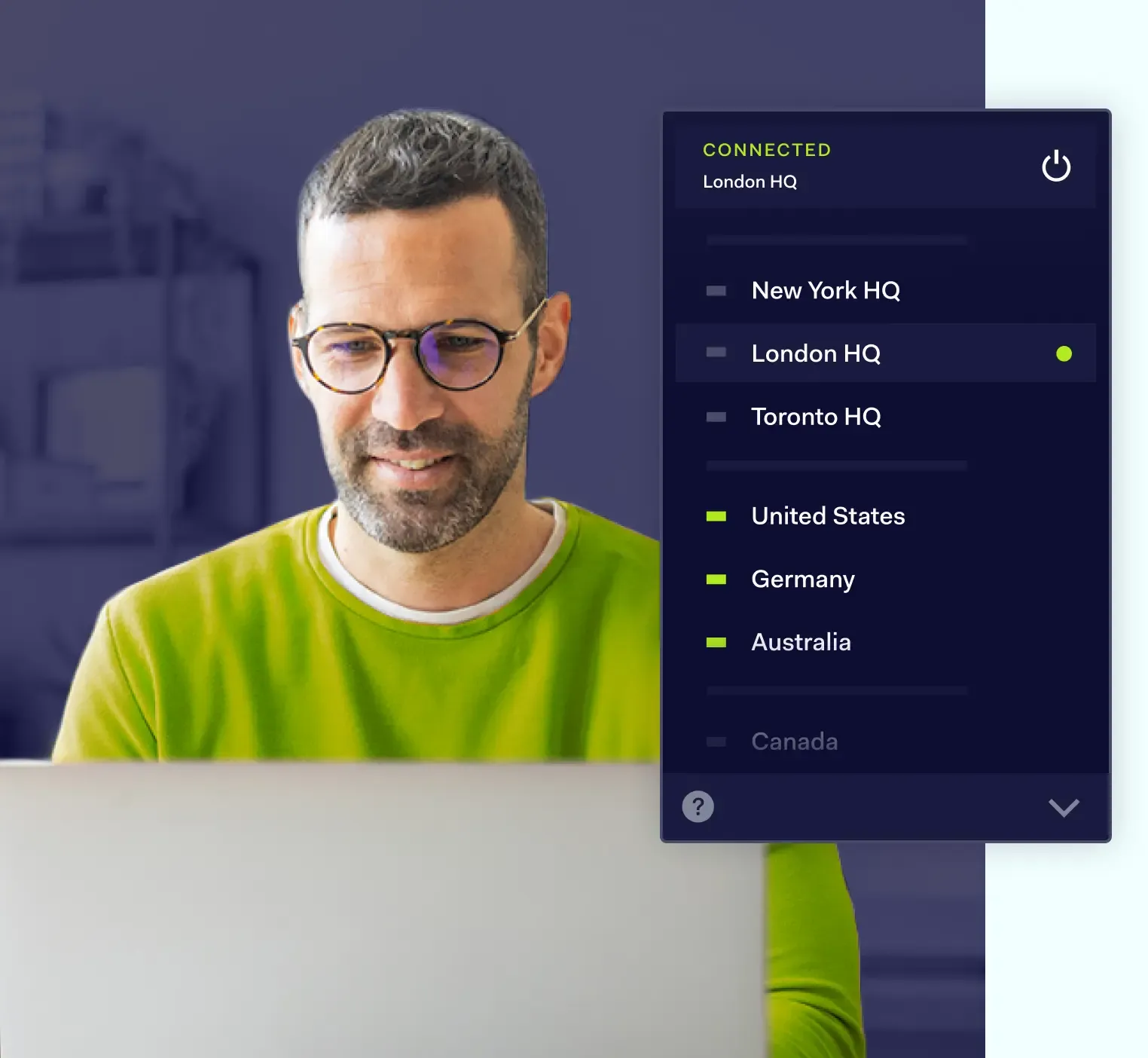
Safeguard your business with NordLayer
Start implementing advanced Threat Prevention, or contact NordLayer's cybersecurity specialist.
OUR INSIGHTS
Threat Prevention resources
Additional info
Frequently asked questions
It's a term used to describe how security solutions work together to protect the business network from malicious behavior or malicious code. Different features work in different ways to contribute to a multi-layered security offering that integrates into the existing network infrastructure.
Threat Prevention is crucial to organizations because it is in their best interests to secure valuable assets, data, and resources that are stored within their networks. Today, cyber-attacks and threats are more frequent than ever and can take many different forms. Having a robust and adaptive security solution like NordLayer can prevent these events from happening in the first place or limit the scale of damage if they do occur.
Businesses are often targeted by cybercriminals seeking to steal data, disrupt operations, or gain unauthorized access to systems. NordLayer & NordStellar help stop attacks like ransomware, phishing, and data breaches by blocking suspicious activity, securing network access, and protecting sensitive information from exposure.
Advanced Threat Prevention combines multiple tools and layers to stop attacks before they spread. These include endpoint protection for remote devices, secure access management to control user permissions, and Business VPN solutions that encrypt data and protect traffic from untrusted networks.
