Summary: In 2025, ransomware attacks have targeted organizations of all sizes, focusing on those with the greatest potential for damage and ransom payouts.
The year 2025 has been a brutal reminder that ransomware attacks aren’t slowing down. If anything, they’re getting smarter, faster, and even more targeted. Every month, reports came in of companies being breached—from small businesses to large enterprises—many of which were forced to pay hefty ransoms to regain access to their systems or data, or to prevent leaks.
In this article, we’re going to examine eight of the most significant ransomware incidents of 2025. We’ll dissect what went wrong, what the threat actors did, and what the real cost of the fallout was. More importantly, we’ll move past the what-ifs and give you the best practices for protecting your business against ransomware attacks.
Some of the major ransomware incidents of 2025
In 2025, ransomware attacks have often focused on high-value targets, where a breach can have far-reaching financial, operational, and reputational impacts. These organizations typically handle large volumes of sensitive data or provide critical services, which puts immense pressure on them to meet ransom demands.
1#: Ingram Micro
Date: July 2025
Impact: A leading global IT distributor, Ingram Micro, suffered a severe ransomware attack attributed to the SafePay hacker group. The breach disrupted operations worldwide, forcing it to take critical systems offline and impacting its ability to process orders and ship products. SafePay claimed to have stolen 3.5 terabytes of sensitive data, including customer information and internal documents, and threatened to release it unless a ransom was paid. The attack caused an estimated $136 million in daily revenue losses.
2#: Sunflower Medical Group
Date: January 2025
Impact: The Rhysida ransomware group targeted Sunflower Medical Group (SMG), resulting in the theft of sensitive data, affecting 220,968 individuals—though the perpetrators claimed a higher number. Compromised information included Social Security numbers (SSNs), driver’s license numbers, medical records, and health insurance details. The attackers allegedly demanded an $800,000 ransom to prevent the public release of the stolen data.
Stop ransomware before it stops your business
Discover defenses that help you stay one step ahead
3#: NASCAR
Date: April 2025
Impact: The premier U.S. stock car racing organization, NASCAR, suffered a cyber-attack that exposed personal information, including names and Social Security numbers, of racing fans. The Medusa ransomware group claimed responsibility and demanded a $4 million ransom. Although NASCAR did not confirm payment, it notified affected individuals and offered one year of free credit monitoring and identity theft protection through Experian.
4#: PowerSchool
Date: December 2024/January 2025
Impact: PowerSchool, a provider of cloud-based software for K-12 education, suffered a data breach that exposed sensitive data of over 62 million individuals across North America. The attackers allegedly demanded around $2.85 million in Bitcoin. Acting in the best interest of its customers, PowerSchool reportedly paid the ransom in exchange for promises that the stolen data would be deleted. Despite this, the threat actors later attempted to extort individual school districts using the same data, highlighting the ongoing risks of ransom payments and the persistence of ransomware threats in education.
5#: DEphoto
Date: December 2024/January 2025
Impact: The personal information of 555,952 customers of UK-based photography company DEphoto has reportedly been stolen. The breach is said to include 16,213 records containing full credit card details—such as card numbers, expiration dates, and CVV codes—along with hundreds of gigabytes of private photos, including images of children and event photographs. The threat actors, known as 0mid16B, demanded a ransom of approximately $60,000 to prevent the data from being leaked.
6#: Maryland Transit Administration
Date: August 2025
Impact: The Rhysida ransomware group claimed responsibility for a cyber-attack on the Maryland Transit Administration (MTA), part of the Maryland Department of Transportation. The breach exposed sensitive personal data, including names, Social Security numbers, driver’s licenses, and passports. The cybercriminals demanded a ransom of 30 Bitcoin (around $3.4 million) to stop the stolen information from being released publicly.
7#: Comcast Corporation
Date: September 2025
Impact: The Medusa ransomware group claimed to have carried out a ransomware attack on Comcast Corporation, a global media and technology company that oversees a wide range of TV networks, film studios, and streaming platforms. According to their dark web leak site, the attackers seemingly stole 834.4 gigabytes of company data and are demanding $1.2 million from anyone interested in accessing it. Comcast reportedly faces the same $1.2 million demand if it wants the data deleted rather than leaked or sold.
8#: DaVita
Date: March–April 2025
Impact: Another major breach in the healthcare sector was the Interlock ransomware group’s attack on DaVita, a major kidney dialysis provider. The group’s server infiltration, which lasted several weeks, exposed the sensitive data of more than 2.7 million patients. The stolen information was highly personal, including names, tax records, and medical results. DaVita reported approximately $13.5 million in recovery costs, excluding business interruption losses.
Related articles

Anastasiya NovikavaOct 1, 202515 min read

Anastasiya NovikavaDec 3, 20247 min read
How ransomware attacks evolved in 2025
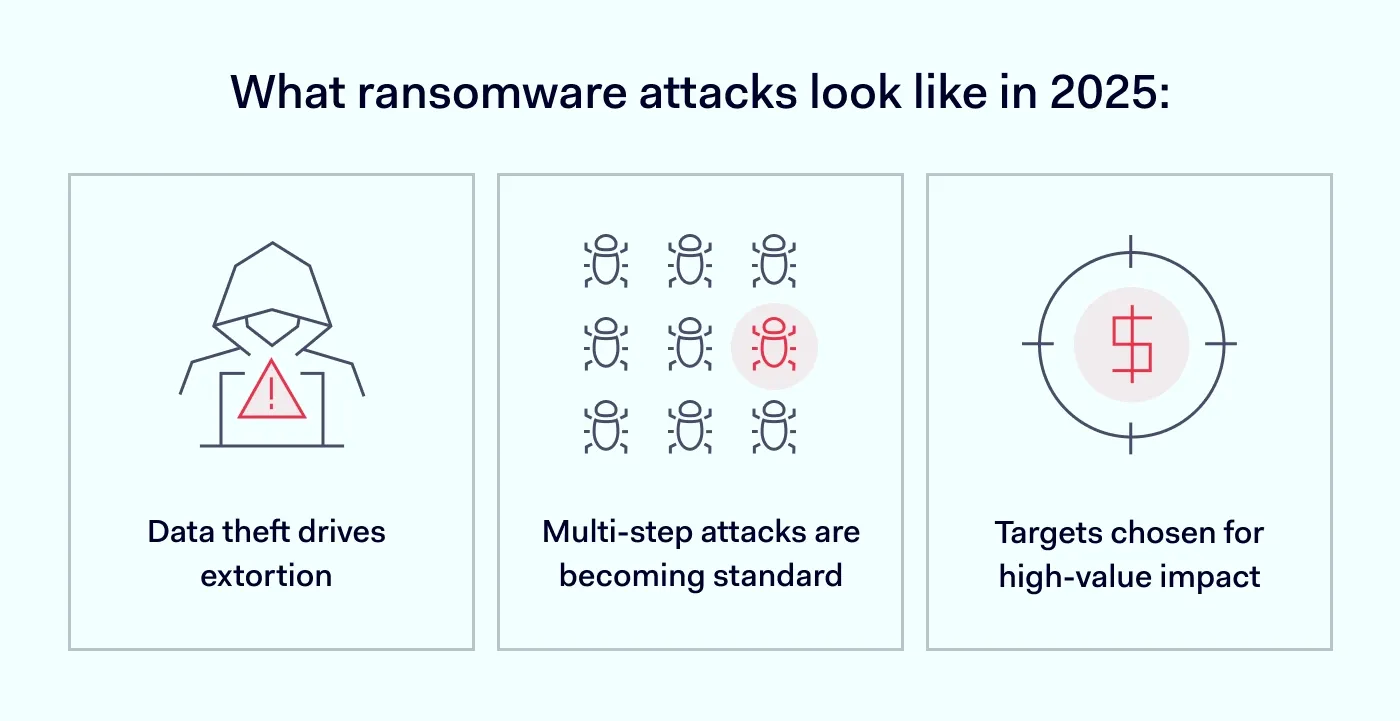
The cases described above show how ransomware has advanced far beyond just system-locking. Today’s ransomware groups operate as sophisticated criminal enterprises, running multi-layered campaigns designed for maximum profit.
Incidents like the NASCAR and Sunflower Medical Group breaches highlight the significant shift where the primary objective is often data theft for subsequent extortion. Even with reliable backups and rapid recovery, organizations remain exposed to the most damaging consequences: data leaks, regulatory fines, and reputational harm.
By 2025, multi-stage cyber extortion has become the norm. This means that even when a company pays the initial ransom, there is no guarantee that the attackers will not exploit the stolen data further. The PowerSchool case illustrates this, as threat actors reportedly targeted individual school districts using the compromised information.
We also need to recognize that attackers increasingly target sectors where data compromise has the greatest impact, like healthcare, education, entertainment, and supply chains.
Attackers don’t choose victims based on size—they target organizations that are most vulnerable or most likely to pay quickly to protect critical services and prevent the exposure of sensitive data. Small businesses are not exempt; if cybercriminals spot an opportunity, they will strike.
Ways to protect your business from ransomware attacks
The stories of high-profile ransomware attacks, while worrying, are a clear call to action. The good news is that the core principles of protection remain effective. By adopting a proactive, layered approach, you can significantly reduce your company’s risk exposure. Here’s what security experts recommend.
Implement Zero Trust Network Access (ZTNA)
The rise of sophisticated cyber threats has shown that traditional perimeter-based security—which assumes anything inside the network is automatically trusted—can no longer keep pace. That’s why a Zero Trust approach, built on the principle of “never trust, always verify,” is more effective against cyber-attacks.
In a Zero Trust model, no user, device, or application is trusted by default, no matter where they are, what their role is, or how long they’ve been with the company. Every connection request must be verified before access is granted.
Implementing ZTNA helps limit the damage if an attacker does compromise a single endpoint. The attacker’s ability to move around your network and access other systems is tightly controlled, reducing the chances of sensitive files being stolen or a large-scale ransomware attack taking place.
Divide your network into smaller parts
This strategy, known as network segmentation, is an effective defense against data breaches. By dividing your network into smaller, isolated zones—for example, keeping marketing systems separate from critical financial servers—you can better contain an attack.
Think of it as damage control. If one segment is compromised, the threat can’t easily spread to other sensitive parts of your infrastructure. This limits the blast radius of a breach, making containment faster and recovery less costly.
Manage vulnerabilities and patch rigorously
Ransomware thrives on overlooked vulnerabilities, often exploiting known, unpatched software flaws. That’s why every discovered weakness should be treated as a potential entry point for attackers.
Therefore, you must prioritize and apply security updates for operating systems and all third-party software without delay. This discipline dramatically reduces your attack surface, removing the low-hanging targets that threat actors rely on for initial access.
Develop a disaster recovery plan
The objective of a disaster recovery plan is to help ensure business continuity, no matter what challenges arise. This requires maintaining and rigorously testing immutable backups of all critical data. These backups cannot be modified or deleted, even in the event of a total system failure or security breach.
Test your recovery process frequently to ensure you can restore systems and data quickly. Crucially, your plan must include a clear incident response protocol covering the steps your team will take as soon as any significant disruption is detected.
Invest in comprehensive employee training
No amount of technology can fully compensate for a lack of security awareness. The human element remains one of the primary initial access vectors for ransomware attacks, often via social engineering and phishing.
That’s why you need mandatory, continuous training focused on recognizing and immediately reporting suspicious activity. Beyond basic awareness, robust password management practices must be enforced, ensuring everyone uses unique, complex credentials. This step closes one of the most fundamental security gaps that threat actors try to exploit.
How NordLayer can help?
The scale of today’s cyber threats is staggering, and ransomware can strike any organization, regardless of size or industry. Simply hoping your business won’t be targeted isn’t enough. NordLayer helps organizations build a multi-layered security framework that makes it much harder for ransomware groups and other malicious actors to succeed.
NordLayer is designed to make security effective, simple, and practical while adhering to recommended best practices. Functioning as a Business VPN, it creates a secure, encrypted tunnel between your organization’s resources and the employees accessing them. Its Zero Trust Network Access (ZTNA) solutions ensure that every user and device must prove they are trusted before entering this tunnel. This verification is further strengthened by multi-factor authentication (MFA), which rigorously confirms user identities.
Access is also governed by Device Posture Security (DPS), which ensures that only protected, compliant devices can connect to your network. This layered approach prevents attackers from using insecure devices to access your sensitive data. On top of that, NordLayer supports network segmentation, allowing you to isolate parts of your network so that a breach in one area cannot spread.
Defending against ransomware attacks isn’t about cutting your business off from the outside world. It’s about building a smart, layered system where every connection and access point is verified. NordLayer provides exactly that. It helps your business stay secure, agile, and operational, even in the face of persistent digital threats.

Maciej Sikora
Senior Copywriter
A man on a mission to engage audiences with creative wordplay, Maciej knows every complex idea can be broken down into simple words—and that’s his driving force. When he’s not writing, you’ll find him making music, taking a walk with his dog, or watching yet another movie.