
Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.
Trends & statistics
Summary: Stats for 2025 show ransomware in 44% of breaches and third-party risk doubling. The answer is Zero Trust and resilience.
By the numbers, 2025 was the worst year yet for organizations that expose remote services, trust third parties by default, or postpone identity hardening. Ransomware was present in nearly half of all security incidents, while the exploitation of edge and VPN devices surged. More data breaches than ever were traced back to someone else’s software or service.
Cybersecurity statistics paint a concerning picture. Two headlines set the tone. First, the updated scale of the Change Healthcare fallout (described as the largest U.S. health data breach on record, affecting roughly 190–193 million people) showed how a single compromise can disrupt prescriptions, claims, and care nationwide.
Second, the PowerSchool extortion and data-theft case demonstrated the unique harm to minors when K-12 data platforms are compromised at scale.

Ransomware attacks appeared in 44% of data breaches. In Mandiant’s casework, ransomware-related intrusions accounted for approximately 21% of investigations in 2024. Attackers move fast: 56.5% of ransomware incidents were discovered within a week, often because the adversary announces their presence via extortion.
The most common first step wasn’t phishing but brute-force attacks on remote services, followed by stolen credentials and exploits. Families like RANSOMHUB, Akira (REDBIKE), BASTA, and LOCKBIT consistently appear in investigations.
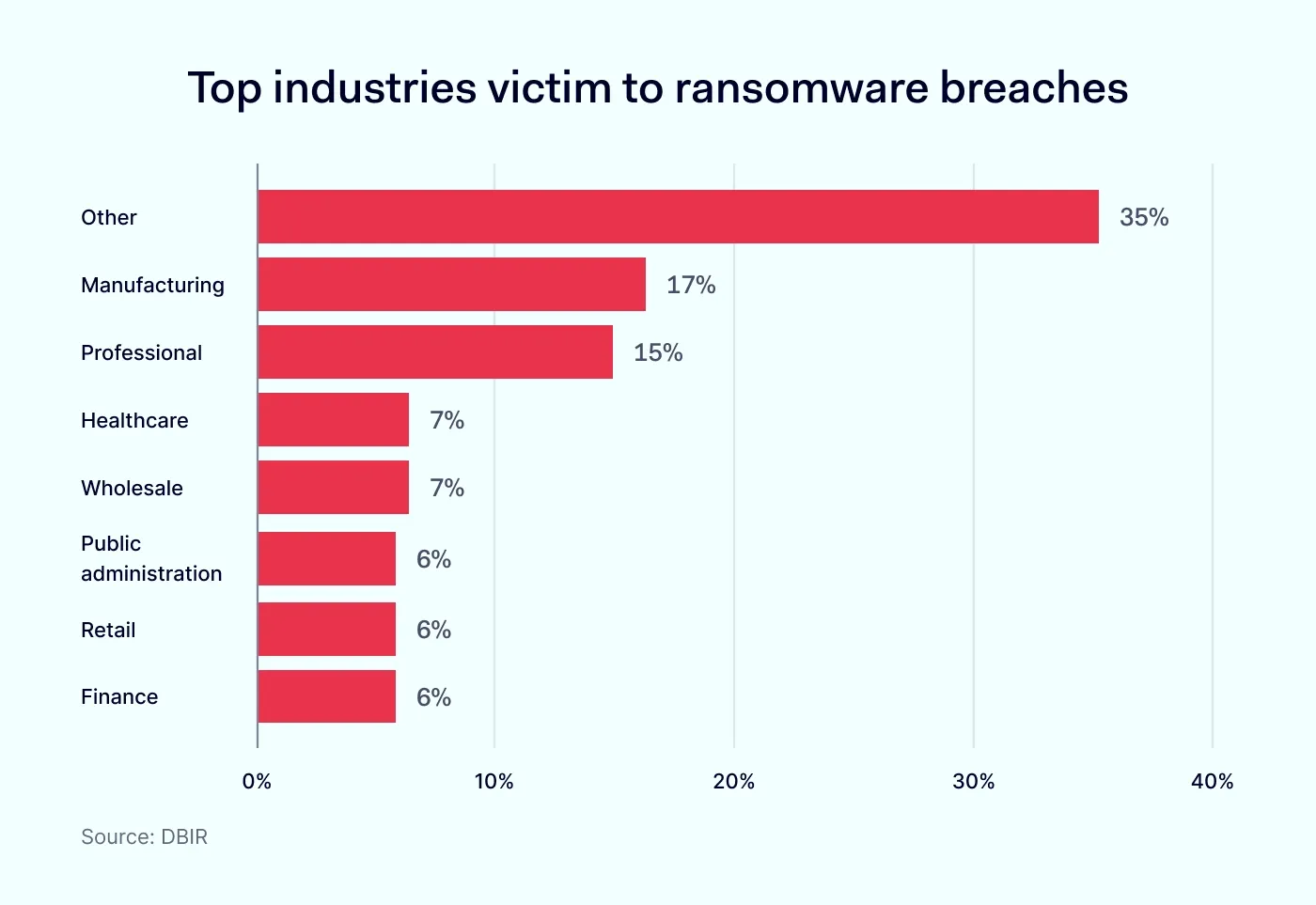
Why this matters: Ransom amounts might be falling, but the operational blast radius (from downtime to supplier disruption) continues to grow. Data-theft-only extortion without encryption is now a common variant. The primary control failures remain identity weaknesses, exposed remote services, and incomplete network segmentation.
The DBIR shows vulnerability exploitation jumping to 20% of initial access paths, driven by edge and VPN devices (22% of exploit vectors, an approximately 8x increase YoY).
Mandiant’s top exploited CVEs were:
Many of these were first seen as zero-days and rapidly adopted by multiple threat actor groups.
Why this matters: These devices sit on the network edge by design and often share an identity plane with corporate resources. Rapid weaponization and slow patch adoption mean identity-aware access policies must assume periodic exposure is inevitable.
The share of breaches involving a third-party component roughly doubled to 30%. Recent multi-tenant SaaS campaigns harvested OAuth tokens and CRM data across many organizations (e.g., attackers abusing Salesloft/Drift adjacencies). Government and healthcare incidents showed how vendor remote-support tools and legacy platforms can widen attack paths.
The lesson is that secure-by-default configurations and Zero Trust principles must be extended to vendor and SaaS due diligence. Excellent internal data protection is not enough.
Why this matters: A single supplier breach can create a blast radius across sectors and geographies. It can seed phishing attacks, business email compromise, and targeted intrusions among your customers and partners.
Credential-focused crime remains a pillar of cybercrime. Stolen credentials were the #2 initial vector in M-Trends (16%).
DBIR’s analysis of infostealer logs shows 30% of affected systems are enterprise-licensed, while 46% of devices mixing corporate logins are unmanaged (amplifying human error and shadow IT risk).
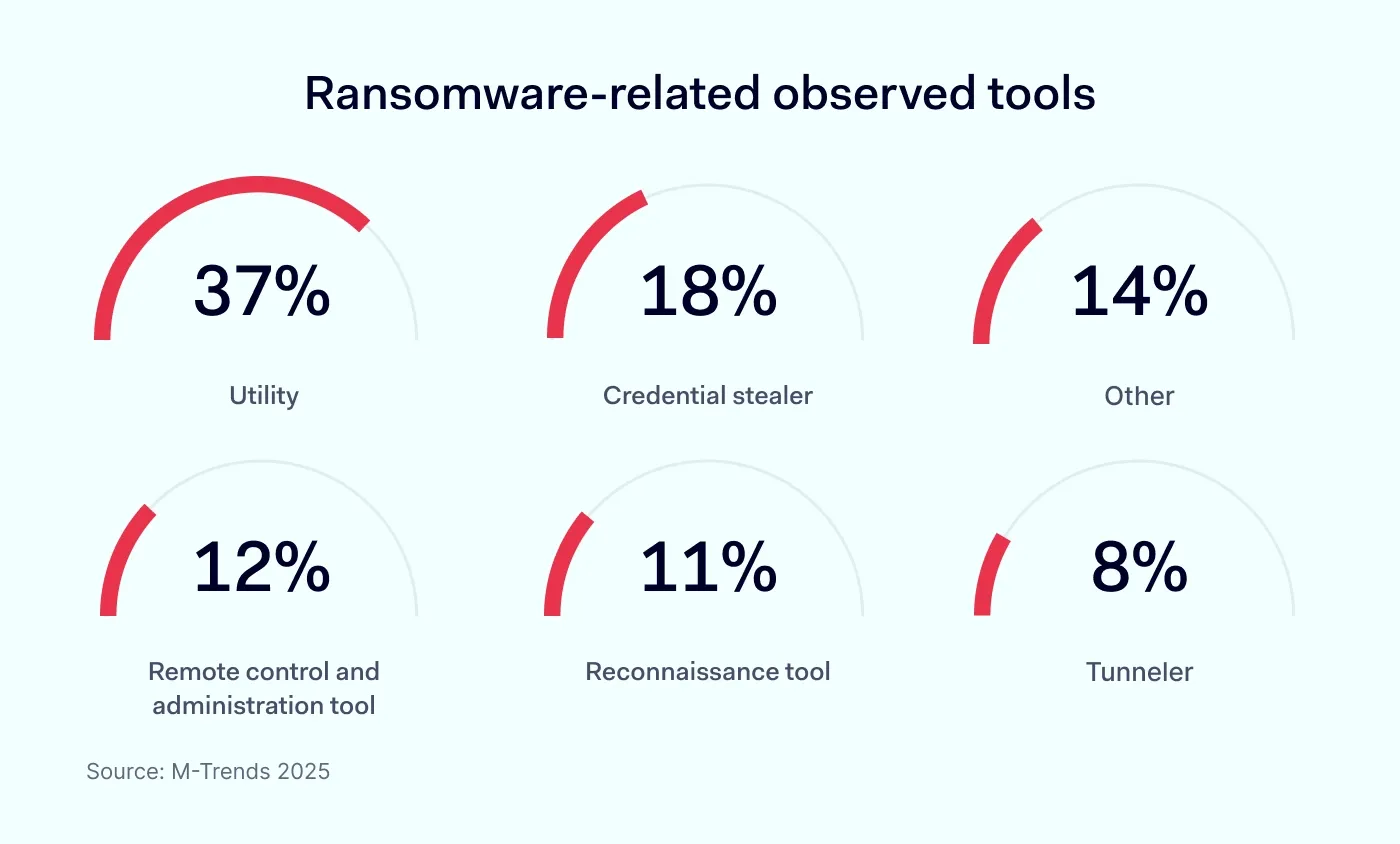
Attackers increasingly create persistent access with session cookies and app-specific tokens; for example, research in 2025 found nearly 94 billion leaked cookies across dark markets.
Why this matters: Traditional password policies and basic MFA are not enough. Controls must focus on phishing-resistant MFA, continuous device posture checks, and session/token governance to reduce credential reuse and session hijacks.
Front-line social engineering drove multiple high-profile intrusions.
Why this matters: People, not perimeters, remain the decisive "allow" button. Organizations need positive identity verification and out-of-band checks for any credential or MFA changes, plus the ability to block risky workflows (like ASPs) for high-risk users.
PRC-nexus operators (e.g., those using UNC6384/PlugX variants) hijacked captive portal checks to deliver digitally signed malware and deploy in-memory backdoors. APT41 used Google Calendar as a command-and-control channel in its “TOUGHPROGRESS” campaign. Russia-nexus activity (UNC6293) blended diplomatic lures with mailbox persistence.
Beyond data theft, several groups target edge devices, SaaS applications, and cloud misconfigurations to entrench themselves quietly. Espionage-motivated data breaches grew to approximately 17% in the DBIR's dataset.
Why this matters: These new threats blur lines between cybercrime and espionage. They often dual-purpose their access for both financial and intelligence goals. Defenses must apply the same rigor to identity, SaaS, and the network edge as they do to on-premises servers.
Availability-only incidents (from botched updates to targeted destructive actions) can rival data breaches in cost. Mandiant emphasizes using Isolated Recovery Environments (IREs) that are identity-separated from production, with immutable backups and console-only recovery workflows. This is a critical step, since modern attackers now seek out and destroy backups.
Why this matters: When cyber-attacks knock systems offline, security measures that accelerate clean rebuilds and validated recovery (in parallel with forensics) can determine whether a crisis is measured in hours, weeks, or quarters.
Financial services: Still the most targeted sector in Mandiant’s global investigations (a little over 17%). Attackers chase monetizable data, payment rails, and high-pressure operations.
Business and professional services; high tech; government; healthcare: The next most frequently impacted sectors in 2024 and early 2025. Each combines valuable sensitive data with complex third-party ecosystems.
Retail: 11% of victims posted on extortion sites in 2025 YTD (vs. ~8.5% in 2024). Payment disruption risk increases ransom pressure, and retail organizations hold vast PII.
Telecom: National-scale data breaches (e.g., SK Telecom) exposed SIM/USIM data and raised SIM-swap risks for millions. Core networks and identity systems are prime espionage targets.
Education: SaaS-driven K-12 platforms (e.g., PowerSchool) concentrate data on minors and staff; the exposure from a breach can be unprecedented in scope.
SMBs globally: Nearly half of SMB owners report an attack on their current business; almost 1 in 5 of those later closed or went bankrupt, showing the disproportionate impact of downtime and extortion.
The average global breach cost is $4.4M (down 9% YoY), but U.S. organizations still face a record $10.22M average.
Healthcare tops the charts at $7.42M. That is before factoring secondary impacts like delayed prescriptions or claims denials.
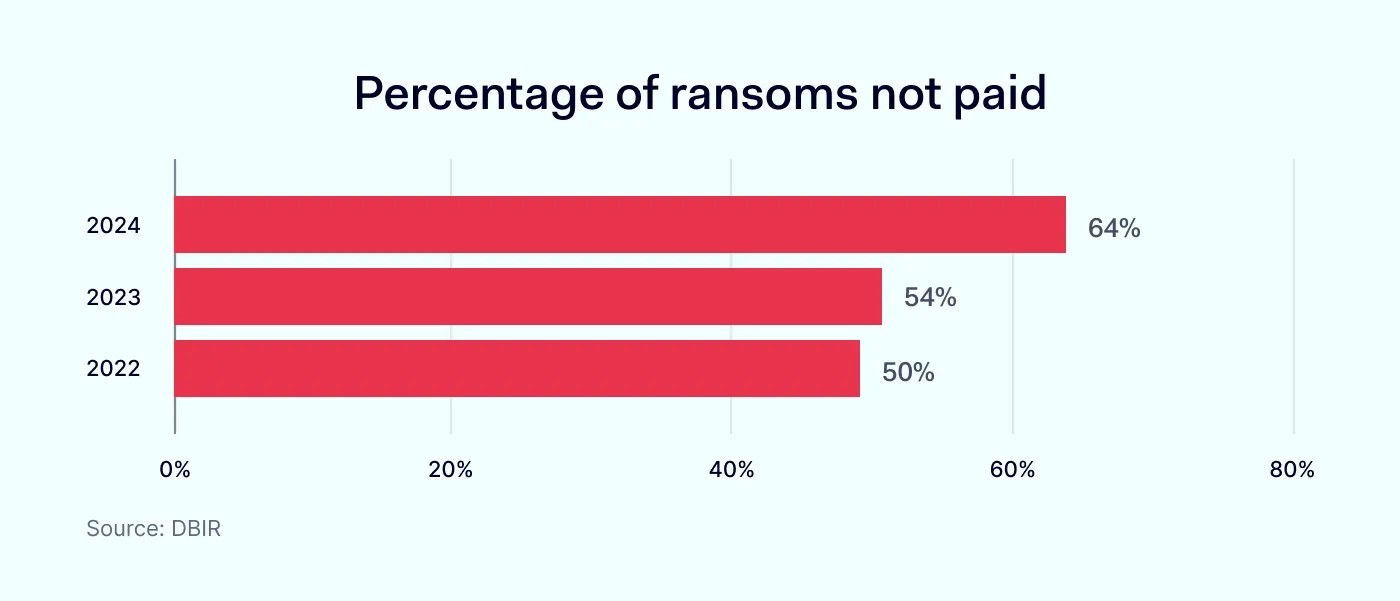
Importantly, the median ransom is $115K, yet most victims do not pay. That fact has shifted costs toward recovery, regulatory penalties, and reputational damage. These cybersecurity statistics prove that even without a ransom payment, the financial toll from ransomware attacks remains immense.
Here are some of the most significant cyber incidents and data breaches that have occurred this year.
In January 2025, a threat actor claimed to have stolen data for over 62 million students and nearly 10 million teachers from the systems of PowerSchool, a major student information system. By September, the Texas Attorney General filed a lawsuit against PowerSchool, confirming over 880,000 state residents were affected.
Investigators determined the attackers gained access using a contractor’s stolen credentials. Because PowerSchool is used to manage everything from grades and enrollment to bus routes, the breach exposed a wide range of sensitive information, including names, Social Security numbers, and even medical details in some districts.
In April 2025, South Korea’s largest telecom provider, SK Telecom, admitted that attackers had stolen authentication records tied to its USIM cards—the small chips that verify a phone’s identity. Regulators later revealed that malware had been in the company’s systems for years before being detected.
The exposed records could allow criminals to clone SIM cards, intercept text messages, and take over online accounts that use SMS for verification. Officials described the breach as nationwide in scale, impacting 26.96 million customers. The government fined the company and ordered it to improve its security controls.
In September 2025, the FBI issued a warning about two cybercriminal groups, UNC6040 and UNC6395, quietly stealing customer data from Salesforce tenants. The groups used sophisticated methods, including vishing (phone phishing) to trick employees into giving up multi-factor authentication codes and stealing OAuth tokens.
These tokens, which allow connected apps to access data without a password, gave attackers a direct line to CRM records. This was not a loud ransomware attack but a quiet theft of names, phone numbers, and business contacts. Because many companies use the same third-party apps, one stolen token could create a ripple effect across dozens of organizations.
In late December 2024, an incident that carried over into 2025 involved the U.S. Treasury, which learned that cybercriminals had broken into a contractor's remote support tool. Attackers used this access to reach unclassified Treasury computers and documents.
Investigations pointed to a group linked to China. The incident is a critical reminder of third-party risk, as these vendor tools are widely used. A single weak login at a contractor can give outsiders deep access into a secure environment, turning a small help desk session into a significant intrusion.
At the end of March 2025, hospitals reported that threat actors had broken into old Cerner "data migration" servers. These were outdated, on-premises systems used to move patient information. Oracle Health later confirmed that these obsolete servers were compromised but insisted its modern cloud systems were secure.
Notices sent throughout the summer named at least 14,485 affected individuals, though the total number is likely higher. Since the Cerner system is connected to many hospital environments, the breach created a widespread privacy risk. Even when only old servers are hit, the exposure of names, IDs, and medical details creates a long-term headache.
On April 11, 2025, Yale New Haven Health disclosed that hackers had been inside its systems since March 8, exposing the data of 5.56 million people. The breach is one of the largest hospital attacks of the year, equivalent to exposing the personal information of an entire small U.S. state's population.
The compromised files included demographic details and other protected health information, which is highly valuable for scams and identity theft. Patients quickly filed lawsuits, and the health system entered settlement talks by late summer, highlighting the severe financial and legal fallout from such a massive breach.
On April 9, 2025, Blue Shield of California admitted that a misconfigured Google Analytics setup had been leaking member data to Google Ads for years. This was not a malicious hack but an internal error where a marketing tool accidentally sent private information to advertising systems.
The configuration error affected approximately 4.7 million people. While full medical charts were not exposed, sensitive data such as browsing histories, insurance plan details, and claims information was leaked. The incident is a stark reminder that not all breaches are caused by external attackers; sometimes, the danger comes from a tool used with the wrong settings.

The through-line from this year’s cybersecurity stats is clear: reduce initial access, contain the blast radius of any intrusion, and accelerate recovery.
Make FIDO2-based MFA mandatory for administrators and high-risk roles. Remove SMS and voice fallbacks. Require multi-context checks (user, device, and location) for sign-ins, password resets, and all MFA enrollment. Investigations repeatedly show adversaries exploiting weak help-desk flows and device-agnostic policies to carry out devastating cyber-attacks.
Introduce positive identity verification, such as on-camera ID checks, before any sensitive change. Require out-of-band supervisor approval for high-risk modifications. During periods of elevated threat, temporarily disable self-service MFA resets. Train staff on social engineering tactics and provide them with easy escalation paths.
Inventory and prioritize patching for all edge and VPN appliances. Restrict management interfaces. Enforce allow-listed IPs and device posture checks for administrative access. Treat edge exposure as inevitable: monitor for web shells, unusual processes, and configuration drift.
Ban browser password storage for corporate accounts and block risky session types. Rotate secrets that have been exposed in Git or CI/CD pipelines. Implement short-lived tokens and ensure session revocation follows any risk event. Remember: nearly 94 billion cookies and tokens are in circulation, creating significant cybersecurity risks.
Use SSO everywhere and enable device-trust checks. Disable local accounts. Deny new connected apps by default. Restrict API access to approved applications and IPs. Require high-assurance sessions for data exports or downloads. Monitor for abnormal data pulls and new application grants, which can signal impending data breaches.
Apply least-privilege principles and micro-segmentation to isolate crown-jewel systems and sensitive data. Enforce "green zone" rules for administration. Disable lateral movement protocols (like SMB, RDP, and WinRM) by default and enforce just-in-time elevation for access.
Stand up a logically and physically separated enclave with immutable backups, one-way data replication, a separate identity provider, and console-only remediation workflows. Rehearse the rebuild of critical services quarterly. This is a crucial step in a modern data protection strategy, as attackers now target backups as a matter of course.
Turn on and retain logs for VPN/edge devices, IdP risk signals, and SaaS export events. Create detections for high-risk changes (like MFA enrollment), new connected apps, and bulk data access. Centralize this telemetry to speed up your mean time to detect incidents.
Define criteria for system isolation, communications, law-enforcement engagement, and customer notification. Practice the decision points (pay vs. rebuild), validate data-theft evidence, and test your out-of-band coordination channels before you need them.
Move beyond questionnaires. Require technical controls like MFA, SSO, and device posture checks in your vendor contracts. Monitor vendor security telemetry. Constrain partner connectivity with context-aware access and network segmentation. Plan for vendor failover where feasible.
Cybersecurity statistics from 2025 reveal that attackers follow the path of least resistance. Modern cyber-attacks target the network edge, user identity, and third-party services.
While ransomware attacks persist, their goal is increasingly data theft and operational pressure. The root causes remain familiar: phishing attacks, human error, and weak access management, though tactics now include using Google Calendar for command-and-control and abusing app-specific passwords.
In response to these threats, cybersecurity budgets are shifting away from perimeter appliances. The most effective security spending now focuses on Zero Trust, identity security, and resilience through faster patching, posture-aware access, and immutable backups.
NordLayer aligns with the controls highlighted above. It applies a Zero Trust model that uses identity-based, least-privilege access to block cyber threats from unmanaged devices and weak credentials. By integrating with identity providers like Okta and Microsoft Entra ID, it supports strong MFA to help prevent social engineering and account abuse. The platform also creates secure tunnels with DNS filtering and Secure Web Gateway capabilities, which help reduce exposure to phishing attacks and malware.
These central policy checks for device health and user access protect against insider threats. Adopting this approach with strong identity hygiene and a tested recovery plan may help change next year's statistics in your favor.
Subscribe to our blog updates for in-depth perspectives on cybersecurity.