Any data transferred over the internet needs ironclad security. Virtual Private Networks based on OpenVPN provide encryption and online anonymity, making cybersecurity disasters much less likely. But what is OpenVPN and how does it work?
OpenVPN protocol definition
OpenVPN is an open-source VPN protocol that creates secure, encrypted connections over the internet. It uses SSL/TLS for securing data and can work well even with firewalls and network address translators (NATs). OpenVPN is popular because it offers strong security, is flexible, and works on many devices and operating systems.
How does OpenVPN protocol work?
The first thing to understand about OpenVPN is that it is a VPN protocol. A protocol is a set of rules that creates VPN tunnels. It determines how to encrypt and label data packets passing across VPN connections.
There are many different protocol options for VPN users, including L2TP, TLS/SSL, and IPSec. Each one has its strong points, but OpenVPN is regarded as one of the industry leaders.
OpenVPN originated in 2001 and was the first open-source VPN protocol. Since then, a global community of developers has emerged. OpenVPN's open-source community checks bugs and refines the protocol, adding new features and updating security elements. Constant scrutiny means that the protocol is rarely left behind by new cyber threats.
OpenVPN is part of the Secure Socket Tunneling protocol (SSL) family of VPNs. This means that it operates at the Transport Layer (level 4) of the OSI model. It also gives OpenVPN access to the huge SSL library, providing plenty of customization options when creating VPNs.
On the technical side, OpenVPN secures data by encryption and anonymizes data via IP address reassignment like all VPNs. However, the set of tools used to achieve this is different from other VPN styles:
1. Encryption
The OpenVPN protocol uses SSL/TLS key exchange to apply encryption when creating VPN tunnels. This process employs 256-bit encryption as standard – a level of protection that even the NSA cannot crack.
If 256-bit encryption is insufficient, OpenVPN can go even further. The protocol supports advanced encryption techniques like Blowfish, AES, and CAST-128 – making data transmissions almost invulnerable to outside attacks.
Additionally, OpenVPN uses Perfect Forward Secrecy (PFS). PFS creates a unique encryption key for every session or data transfer. Replacing encryption keys makes it very hard for external attackers to steal keys and work around encryption ciphers.
2. Authentication
Alongside encryption, OpenVPN also uses advanced authentication procedures. Authentication ensures that every data packet is delivered to the correct address and in the right sequence.
When users send data via OpenVPN, a tool called TLS-auth applies Hash Message Authentication Code (HMAC) authentication. HMAC virtually guarantees accurate data transfers with minimal data loss.
When comparing TCP vs UDP, OpenVPN uses both transmission modes, which offers flexibility based on the user's needs. We'll look at both later. But for now, it's important to note that only TCP mode provides authentication services. TCP checks transfer to monitor lost packets, while UDP may lead to data loss.
OpenVPN packets can pass through any port. The use of SSL protocols means that traffic sent across the net is almost impossible to distinguish from regular data. With the correct configuration on Port 443, outsiders will not even be able to detect the use of a VPN.
This port configuration also makes OpenVPN very good at evading firewalls – an issue that can plague IPSec VPNs.
Benefits of OpenVPN
OpenVPN has become the go-to protocol for many commercial Virtual Private Networks, and there are plenty of good reasons for this. Benefits of the protocol include:
- Strong encryption with many options. 256-bit encryption is the standard mode with the OpenVPN protocol and should protect data from all cyber attackers. The default setting will keep sensitive data safe such as payment details or company logins. And if users want more robust encryption, different ciphers can be added when required.
- Easy to scale. OpenVPN systems can serve a single workstation connecting to a company network or scale up to enterprise-wide security systems. The VPN is designed to cover as many devices as users require. Users download pre-configured clients, install them to their devices, and are ready to go.
- Excellent device compatibility. One of the biggest OpenVPN benefits is that users can install OpenVPN clients on Windows, Linux, and macOS. The protocol offers Android and iOS functionality and can be configured for specific hardware if needed.
- Firewall performance. Not all VPNs can traverse NAT gateways or firewalls easily. That's not a problem with OpenVPN, which is known for its ability to handle firewalls and other filtering hardware.
- Protocol flexibility. The ability to switch between UDP and TCP is another strength of OpenVPN protocols. Gamers and streamers can enjoy the speed of UDP transmission. TCP is available for high-security transfers when speed is less critical.
- Plugin friendly. OpenVPN works with third-party add-ons and plugins. This enhances the basic VPN, adding a diverse range of services. These services include flexible authentication options – a handy feature for company networks. Plugins also include plenty of tools to create OpenVPN servers.
- Open-source distribution. Most VPN protocols are corporate-owned. For instance, Microsoft and Cisco own L2TP. But OpenVPN remains open source, ensuring the codebase is transparent. Users won't need to trust that corporations secure data and avoid security errors. A worldwide coding community fine-tunes OpenVPN to react to the latest cybersecurity trends.
Drawbacks of OpenVPN
The advantages listed above separate OpenVPN from most other VPN protocols. But no cybersecurity technology is flawless. OpenVPN is no exception, and there are several potential weaknesses users need to know about:
- Not always the fastest option. Security comes with a cost in the world of VPNs. That applies to OpenVPN, especially when using the secure UDP transfer mode. With strong authentication and encryption engaged, OpenVPN is approximately as fast as L2TP, while other tunneling protocols may be quicker.
- Can be complex to configure. Users can struggle to set up an OpenVPN system from scratch. The VPN's founders recommend a 20-stage manual configuration process, and each step is complex and time-consuming. In practice, most people purchase a ready-built OpenVPN client with the features they need. This is convenient, but companies with bespoke security needs may find other protocols more user-friendly.
- Not the best VPN for mobile devices. OpenVPN has become a streamlined solution for desktop and laptop operating systems but is not as slick for mobile users. Android and iOS implementations are not as advanced or user-friendly, although they are improving all the time.
When is OpenVPN used?
Now we know more about how OpenVPN technologies work and the balance of pros and cons. But what real-world uses are there for OpenVPN software?
Since 2001, OpenVPN has become an indispensable part of security solutions, and today's clients have many applications. Use cases could include:
1. Customized VPN setups
OpenVPN is the most flexible VPN protocol available due to its open-source nature. This flexibility makes it ideal when creating a customized security setup.
Admins can toggle advanced encryption or switch between TCP and UDP. As long as users respect the conditions of the OpenVPN software license agreement, they can use the code as they desire - something you won't find with one-size-fits-all alternatives.
2. Robust encryption for remote access
With 256-bit AES encryption part of the package, OpenVPN is secure enough to protect sensitive client data and confidential project documents.
Companies can create a secure tunnel between on-premises data centers and home workstations. And employees can log onto OpenVPN portals as they travel the world. Even better, home workers can switch from TCP to UDP connections to stream or play games outside office hours.
3. Creating Zero Trust network configurations
Zero Trust Network Access (ZTNA) is a set of security ideas that follow the principle "never trust, always verify". OpenVPN technologies are a good foundation for many ZTNA systems.
With a VPN installed, companies can protect data passing across the network perimeter. They can filter access to the internet and prevent access to dangerous websites. And with an OpenVPN cloud implementation, companies can encrypt data flowing to and from SaaS apps.
Meanwhile, access control plugins with multi-factor authentication add an extra element of control, keeping unauthorized actors away from critical assets.
The critical aspect of OpenVPN is its flexibility. Users can apply it to home networks, it can lock down public wifi connections, and link together branch locations securely. Wherever anonymity and encryption are needed, OpenVPN may well have a role to play.
What are OpenVPN UDP and TCP?
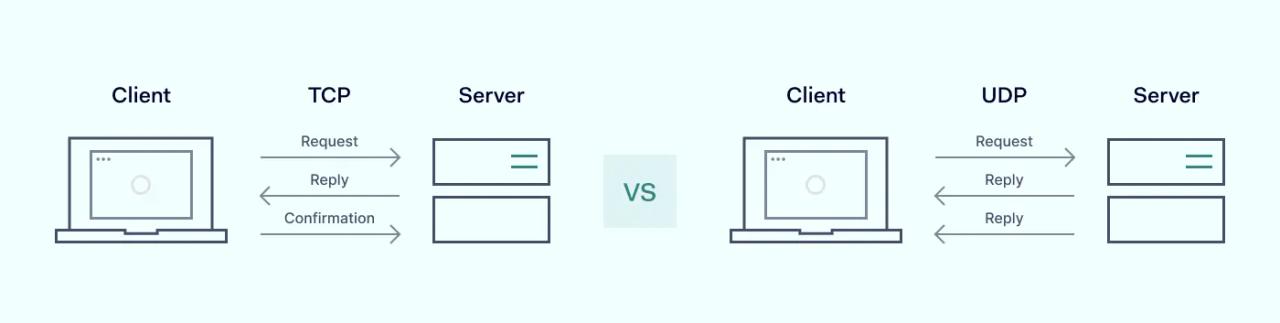
OpenVPN breaks into two protocols, and users can use both TCP and UDP modes for data transmission. The key difference between TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) is that TCP is connection-based; it sets up a connection before data transfer to ensure reliable delivery. UDP is connectionless; it sends data without a connection, which makes it faster but less reliable. For example, TCP works well for tasks like email or file transfers, where accuracy is important, while UDP is better for live streaming or online gaming, where speed matters more than perfect data delivery.
OpenVPN UDP mode
User Datagram Protocol (UDP) mode transports data over UDP Port 1194 and is the default OpenVPN mode. UDP is defined as a stateless connection protocol because servers do not retain session state data during data transfers.
When users send data in UDP mode, there are no mechanisms to verify and correct mistakes. Clients and VPN servers connect directly. The UDP packet format has a checksum attached which enables authentication but the server does not send authentication requests back to the client. There is also no facility to re-send data if an error occurs.
UDP minimizes the number of steps required to send data. This makes it ideal for low-latency situations such as gaming, where data fidelity is less important than raw speed. Eliminating packet replacement frees up a lot of bandwidth, smoothing out graphics and streams.
However, because UDP lacks a handshake process, connections can be insecure and unreliable. It is possible to lose data during transmission, making UDP less suitable for business situations where accurate transfers are all-important.
OpenVPN TCP mode
Transmission Control Protocol (TCP) is the other OpenVPN mode. In this case, TCP is categorized as a stateful protocol. This means that the server retains data about the session state. The server also refers back to the client for verification purposes.
Every packet is authenticated and checked for data integrity when data travels via a TCP tunnel. The client sending data will wait for an acknowledgement that packets have arrived before sending the next frame. If the transfer times out, TCP will repeat the process until transmission succeeds.
TCP also records the sequence of every packet in a transfer. If packets arrive out of order, the protocol will reassemble the structure of the original sequence. This adds another element to ensure data integrity.
With OpenVPN, TCP generally opens TCP port 443. This allows the protocol to traverse firewalls reliably.
On the negative side, TCP consumes more bandwidth than the UDP protocol. This results in noticeably slower speeds when surfing the web and streaming video. Authentication guarantees high-fidelity transfers, which makes the protocol suitable for business tasks. But authentication comes with a cost in terms of speed and efficiency.
How secure is OpenVPN?
OpenVPN technologies have earned a reputation for security, making it one of the most popular VPN platforms. But is this reputation still justified?
Generally speaking, OpenVPN is secure enough for business and personal VPN users. The protocol employs 256-bit encryption and can be enhanced with even more secure ciphers if desired. This encryption has not been exposed as vulnerable to hackers and should ensure data is protected and private at all times.
Moreover, OpenVPN includes Perfect Forward Secrecy, which destroys and replaces encryption keys when sessions conclude. The means of decoding data is rarely exposed to attackers, making their task extremely difficult.
When data travels via the OpenVPN TCP mode, packets are thoroughly authenticated and verified for integrity. HMAC authentication is also available if needed. Users can be confident that their files and messages will arrive safely, with minimal risks of interception via man-in-the-middle attacks.
The OpenVPN open-source community is another security bonus. As an open-source connection protocol, OpenVPN is always under scrutiny from a global community of privacy experts, who make their findings public. If weaknesses exist, they are quickly flagged and dealt with. With other protocols, users must trust companies to stay current and fix vulnerabilities.
Is OpenVPN completely secure? Not always. The complexity of setting up OpenVPN configurations means that users can leave security gaps. For instance, users may forget to switch from UDP to TCP when extra protection is necessary. Admins could also choose the convenience of static encryption keys, although public key infrastructure (PKI) is more secure.
It is also important to remember that alternatives exist. Wireguard has emerged as a challenger to OpenVPN in recent years and offers similar security features with potential speed benefits. Web-based TLS/SSL VPNs or IPSec VPNs also have benefits in specific contexts. But for general VPN users, OpenVPN is often the best choice.
OpenVPN: Speed and security for robust data protection
OpenVPN is an open-source VPN protocol that powers many of the world's most popular VPN services. Users can set up OpenVPN themselves, but most implementations are via third-party clients.
OpenVPN has many benefits:
- Users enjoy flexibility via different encryption standards and transfer modes
- 256-bit encryption is the default mode and is virtually uncrackable
- UDP mode suits gamers and streamers. TCP works well for businesses
- OpenVPN caters to almost every device and any OS.
- Data can pass across firewalls. Very few online services block OpenVPN.
- As an open-source VPN, OpenVPN is transparent, and finding support is easy.
- OpenVPN can scale easily, providing coverage for company networks.
OpenVPN has some drawbacks. It is complex for beginners, not perfect for mobile users, and may suffer from latency. But on core metrics like security it matches any competing VPN standards.
NordLayer provides full OpenVPN support for business users. We can help you create OpenVPN connections for Linux, macOS, and Windows. Create custom servers for any network topography, install pre-built OpenVPN solutions, and integrate OpenVPN with SASE or Zero Trust systems.