This article will explain what that means and how companies can achieve cloud security compliance goals. We will look at compliance challenges, suggest some cloud compliance best practices, and explain how compliance frameworks make it easier to meet regulatory obligations.
Cloud compliance definition
Cloud compliance involves designing cloud deployments that comply with laws, regulations, or other relevant standards.
Typical features of compliant cloud environments include strict data security and access management policies. Robust risk assessment processes identify compliance needs. And audit procedures ensure that controls function efficiently.
Cloud security compliance varies between industries and jurisdictions. Single, multi-cloud, or hybrid deployments also affect compliance strategies. Butno matter how they are designed, cloud environments must be compliant.
Cloud compliance challenges
Cloud computing brings huge benefits but also presents significant compliance challenges. Securing data in the cloud is not simple. Awareness of critical challenges is vital. Here are some cloud security compliance issues that organizations routinely face.
1. Achieving visibility across hybrid cloud deployments
Companies require total awareness of data and application deployments. But achieving this degree of visibility is difficult in hybrid environments. Security teams must deal with many connection systems and component profiles. This complexity makes it challenging to monitor the entire cloud deployment.
Security teams must work with third-party vendors to secure multi-tenancy environments and physical data centers. Hybrid cloud environments also change constantly. Administrators must track application changes and limit the development of shadow IT practices. These tasks are time-consuming and complex. And mistakes can easily lead to data security compliance violations.
2. Managing workflows in complex cloud environments
Cloud assets must be available and dynamic. Companies rely on dynamic cloud computing to adapt and evolve. Workflows change constantly. New projects emerge, application configurations change, and user communities grow. Careful management is needed to balance availability and security.
Dynamic workflows present several serious cloud security compliance challenges. Remote workers may access cloud assets via unregulated devices and insecure locations. User roles can change, providing users with excessive privileges. And when cloud deployments grow fast, administrators can lose control over change management processes.
To ensure compliance, companies must track configuration changes and access requests. They must log the status and movement of data. And they must enable in-depth audits. Achieving this is tough when cloud environments constantly change.
3. Creating effective auditing processes
Cloud security compliance strategies must include an audit component. Audits assess whether security systems are functional. They compare cloud security policies with actual outcomes. And this provides regulators with evidence that the organization is compliant. But creating efficient auditing processes is challenging.
Security teams must ensure visibility. They must configure cloud platforms and applications to deliver logging data. And they need the right tools to put that data to work.
4. Leveraging automation solutions
Failure to use automation effectively can lead to violations and make compliance management harder than necessary. Security teams can leverage automation tools to handle patch management and user provisioning. Automation tools automatically classify and track sensitive data. They also configure new cloud apps without centralized input.
Automation saves time and executes important compliance tasks. But administrators must take into account relevant compliance frameworks when configuring automation systems.
5. Securing data in the cloud
Most companies use the cloud to store data. Many organizations use cloud solutions to construct cardholder data environments and store confidential client information. Reliance on the cloud makes securing data a core compliance challenge.
Compliance frameworks in the cloud always demand watertight information security. Data breaches result in fines, suspension from payment systems, reputational damage, and prosecution.
Cloud deployments can present a large attack surface for potential attackers. Apps and user devices can expose data to malicious outsiders. And ever-changing deployments can create openings without the knowledge of security teams.
To mitigate these problems, companies should encrypt data and configure firewalls properly. They must manage encryption keys securely, enforce tight access controls, and segment cloud environments to protect high-value data.
Common cloud compliance frameworks
Compliance frameworks are sets of rules and practices that allow companies to achieve compliance. For instance, the PCI-DSS framework includes rules for organizations that handle credit card data. Companies can use the PCI-DSS framework as a basis for compliance strategies.
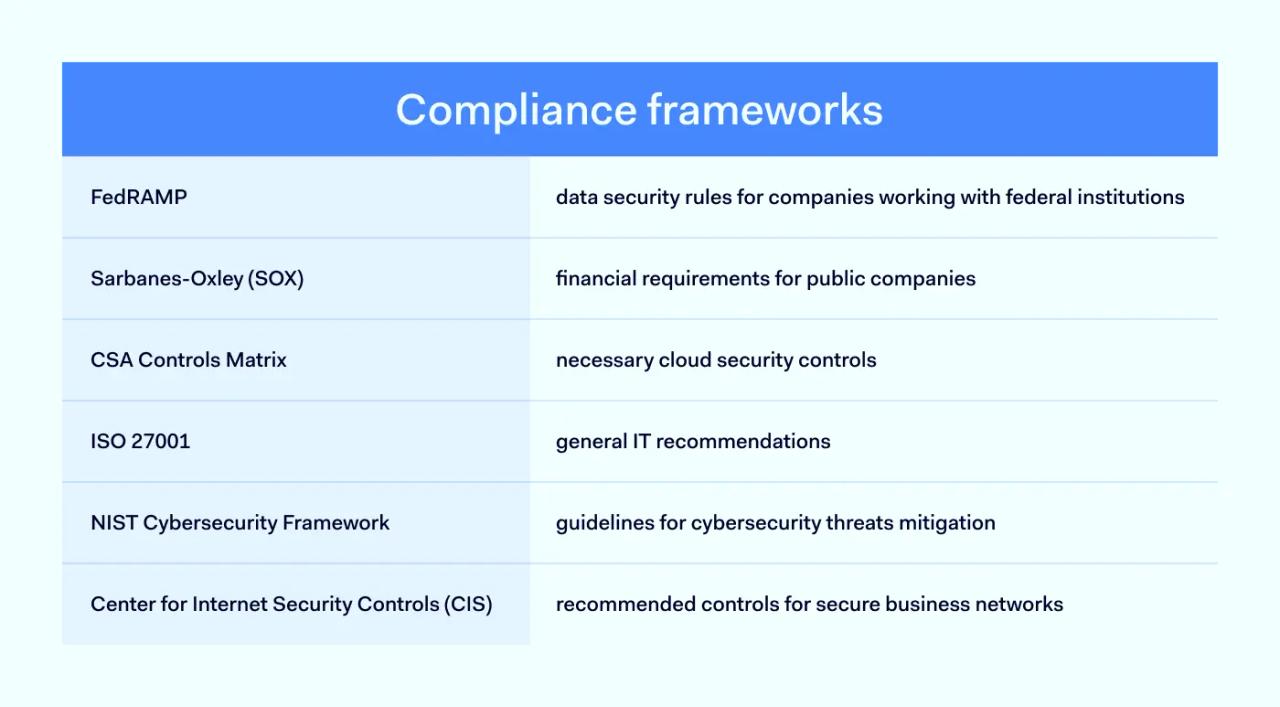
Cloud compliance frameworks apply to virtualized business environments. They explain how to bring cloud security processes in line with regulatory requirements. And there are various styles of cloud security compliance frameworks. Significant cloud-centric security standards include:
- FedRAMP. FedRAMP is a body of data security rules for companies that work with Federal institutions. Companies that operate cloud deployments must comply with FedRAMP standards. These rules include minimum security requirements, such as data encryption and access controls.
- Sarbanes-Oxley (SOX). SOX governs financial reporting requirements. All public companies must adhere to SOX guidelines when reporting their accounts and handling financial data. SOX is not specifically cloud-centered. But cloud security controls are a critical component of SOX requirements.
- CSA Controls Matrix. Maintained by the Cloud Security Alliance, the Controls Matrix provides a robust foundation for cloud-dependent companies. This framework sets out necessary cloud security controls. The matrix makes implementing protective measures and security auditing systems easier. The Controls Matrix is also a valuable reference point for assessing third-party cloud vendors.
- Cloud well-architected frameworks. These frameworks include recommendations about how to design secure cloud deployments. Google, Amazon Web Services, and Microsoft Azure all have individual well-architected frameworks. Companies should refer to them when building cloud infrastructure, designing cloud governance strategies, and securing data.
- ISO 27001. Created by the International Organization for Standardization, ISO 27001 includes general information security recommendations. It also features cloud-specific measures to secure data and applications, enabling organizations to meet the highest data protection standards.
- NIST Cybersecurity Framework. The National Institute for Standards and Technology has created a framework to detect and neutralize cybersecurity threats. This constantly updated document provides the latest guidance regarding security in the cloud.
- Center for Internet Security Controls. CIS is a non-profit that advises companies about creating secure business networks. The organization provides a set of recommended controls. These controls act as an "on-ramp" to meet compliance regulations such as HIPAA and PCI-DSS. They are a strong starting point for many private-sector cloud deployments.
Key concepts of cloud compliance frameworks
Compliance frameworks tend to have elements in common. For example, important cloud compliance concepts include:
- Risk management. Organizations must put in place processes to assess compliance risks. Risk assessments should classify and prioritize risks and implement mitigation measures.
- Security policies. Cloud deployments require robust security policies. These documents record controls and processes. They provide guidelines about secure behavior. And they explain penalties for policy breaches.
- Data security. Frameworks include clear information about how to achieve secure cloud storage. Data security includes segmentation, encryption, classification, access controls, and rules about how users should handle data.
- Access management. Organizations should limit access to cloud environments by connecting user privileges to roles. Frameworks also include measures to manage users and remove obsolete accounts as required.
- Auditing. Frameworks include guidelines about how to collect and use audit data. They inform organizations about how frequently they must audit systems to ensure compliance. Frameworks also provide recommendations about which audit techniques to use.
- Incident response. Most frameworks require incident response plans for data breaches. Companies should implement alert systems to detect problems. Back-ups and data restoration policies should ensure secure restoration of cloud assets when attacks occur.
- Third-party risks. Cloud security standards include guidance about working with cloud vendors and service providers. Frameworks usually refer to the shared responsibility model, which divides security roles between providers and users.
- User training. Frameworks require organizations to train cloud users. Users should be aware of security policies and risks. And training should evolve with new threats and security practices.
- Compliance awareness. Most frameworks recommend continuous assessment and improvement. Organizations should be aware of changes to regulations and technology.
Cloud compliance best practices
How can organizations turn compliance frameworks into functioning security systems? Use these cloud security compliance best practices to protect apps, guard critical data, and remain compliant.
1. Run regular network security audits
Network audits detect compliance issues before they result in violations. Companies should execute quarterly network scans via external professionals or internal security teams.
Create audit policies that define what requires assessment. And arrange a clear audit schedule that relates to compliance reporting timescales. For instance, organizations should complete audits before submitting an Attestation of Compliance with PCI-DSS rules.
2. Integrate compliance into everyday security practices
Don't limit compliance checks to audits. Implement systems that assess cloud environments and workflows in real-time. And bring cloud security measures together in a single management system.
- Regularly assess access privileges and ensure users only have access to essential data.
- Check that firewalls and anti-virus software are updated and functional.
- Carry out data integrity checks to ensure data is encrypted and stored securely.
- Run disaster recovery tests to prepare for attacks. Don't assume you are protected. Preparing for data breaches is a core compliance challenge.
3. Segment cloud environments
Data security regulations require extra protection for critical data. Micro-segmentation of cloud infrastructure provides a solution. Segmentation provides a couple of significant cloud security compliance benefits.
Segments are discrete sections of the environment with additional access controls and protective measures. Micro-segmentation critical data lets you lock down cardholder data environments and protect private health data.
Segments also limit movement within cloud networks. Segmentation restricts the assets that users can access. Malicious intruders will find it difficult to move within network boundaries. This reduces the attack surface and makes data breaches much less likely.
4. Focus access control settings
Access control is a core aspect of cloud compliance. Focus compliance efforts on maintaining firewall settings. Regularly check firewall rules to ensure they allow legitimate access but block attackers. And update device firmware as often as possible.
Implement role-based access controls. Restrict access based on employee needs, and apply Zero Trust principles to exclude other network users. Extend secure access policies to remote devices and require multi-factor authentication (MFA) for user log-ins.
Use automation to remove unused accounts and manage privileges. Minimize the number of privileged admin accounts. And log every access event to create an audit trail. You should know who connects to assets within the cloud environment and when they do so.
5. Assess cloud providers to understand security needs
Most cloud users rely on at least one cloud service provider. Cloud providers manage hosting, deliver SaaS apps, and provide security assistance. But every third-party provider brings potential compliance risks.
Assess all third parties thoroughly. Only use partners with a commitment to security. And keep the shared responsibility model in mind when choosing partners. CSPs will deal with some security issues. But users generally must secure their data and manage access.
Don't assume that partners handle core security functions. Check every service level agreement (SLA) before commissioning services. And make sure you understand your data security obligations.
What cloud compliance frameworks are used the most?
The cloud compliance landscape is constantly evolving. But some compliance frameworks have become established as widely-used benchmarks.
Information technology standards
In the IT sector, the NIST Cybersecurity Framework is the gold standard. NIST's guidelines provide a comprehensive roadmap to secure cloud deployments and handle cybersecurity threats. ISO 270001 is also extremely popular. Both frameworks are information sources about data security techniques.
Companies worldwide look to NIST and the ISO for guidance and compliance information. The Cloud Security Alliance Cloud Controls Matrix (CSA-CCM) is also a popular reference point when assessing cloud vendors and security providers.
Privacy standards
Global businesses must consider the EU GDPR compliance framework when designing cloud architecture. GDPR applies to all companies operating in the European Union and imposes financial penalties for organizations that compromise user privacy. Securing cloud-hosted data is a critical aspect of the regulations.
Industry-specific standards
Other compliance frameworks are industry-specific. For example, companies handling customer credit card data must refer to PCI-DSS guidelines when building cloud payment systems. Companies processing patient data in cloud settings must comply with HIPAA standards. And as mentioned above, FedRAMP sets out strict conditions for companies working with Federal bodies.
Conclusion: meet your cloud security compliance goals
Cloud compliance involves creating cloud infrastructure that complies with data security regulations. Cloud platforms are vulnerable to data breaches, malware, and zero-day exploits. And securing data in the cloud is a complex challenge.
Compliance frameworks provide essential guidance for organizations that depend on the cloud. They recommend controls and policies. And they explain how companies can design cloud deployments that meet regulatory standards.
Find a framework that suits your organizational requirements. And follow our best practices to create a secure, compliant cloud environment.
