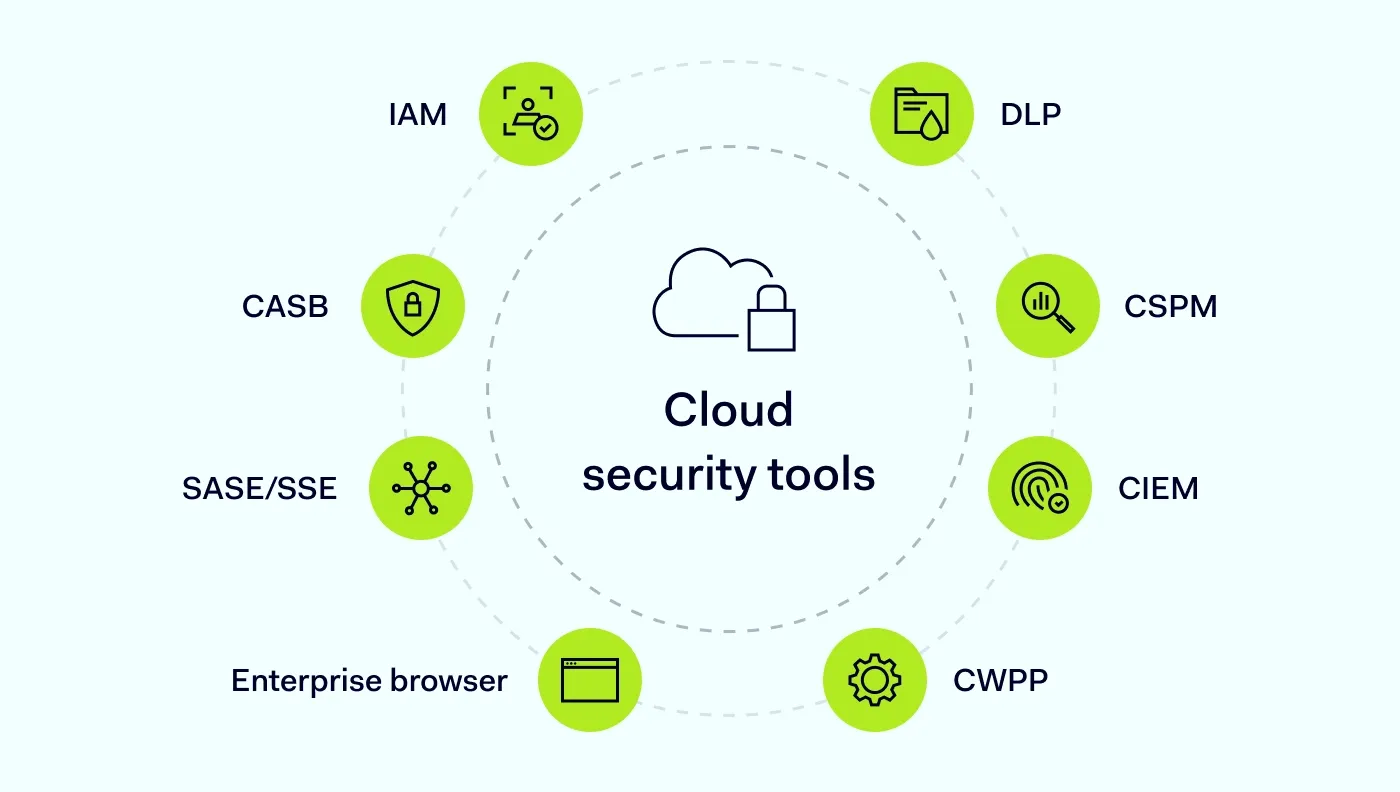
Summary: Learn the eight cloud security tool types—IAM, CASB, SASE/SSE, enterprise browsers, DLP, CSPM, CIEM, CWPP—and how NordLayer supports access security.
Cloud adoption has reshaped how organizations operate—and how they approach risk. Work increasingly happens outside traditional network boundaries. That’s why cloud security tools have become essential for maintaining control, protecting sensitive data, and keeping access in check across modern environments.
Securing SaaS and cloud platforms today is less about guarding a single perimeter and more about maintaining visibility and trust wherever users and applications interact. That shift demands security models designed specifically for dynamic, cloud-first architectures.
This article explores eight core types of cloud security tools organizations rely on to protect SaaS and cloud infrastructure. It covers how they complement one another, and what security teams should consider when building a scalable cloud security strategy.
Key takeaways
Cloud security tools address risks that traditional perimeter security can no longer cover.
Effective cloud security relies on layered controls, as no single solution protects everything.
Identity, access, and visibility are at the core of modern SaaS and cloud security.
Misconfigurations and excessive permissions remain major causes of data breaches.
Choosing the best cloud security tools depends on your organization's scale, maturity, and operational complexity.
Why cloud security is more important than ever
Cloud environments offer flexibility, speed, and scalability. These benefits have driven widespread adoption of the cloud and SaaS applications. However, growing threats make cloud security essential for protecting data and maintaining safe operations.
According to recent industry research, cloud security incidents are now ubiquitous. Studies show that a significant majority of organizations experienced a cloud security incident in recent years. For example, one survey reported that 80–83% of companies faced serious cloud security issues in 2023 and 2024.
At the same time, cloud environments now store large volumes of sensitive information. In another study, 75% of businesses reported that over 40% of their cloud data was classified as sensitive, yet only a minority of this data was fully encrypted.
These trends matter because the cost and impact of cloud security failures are real. The global average cost of a data breach—including those involving the cloud—stands at around $4.3–$4.4 million, and these breaches often expose sensitive customer information, disrupt operations, and harm reputations.
The expanding attack surface
Cloud infrastructures change constantly. Resources such as virtual machines, storage instances, and APIs are created and modified, often across multiple cloud providers. This broadens the attack surface compared to traditional on-premises systems.
Security risks in the cloud don’t typically stem from zero-day exploits. Instead, they most often arise from everyday issues—many of which are cloud-native—such as misconfigurations, weak permissions, poor vulnerability management, and a lack of operational visibility.
Misconfigurations remain one of the top causes of cloud incidents.
Forbes points out that
cloud breaches often involve misconfigured resources, such as open storage buckets or overly permissive access policies.
Human error continues to cause a large share of failures:
one dataset found that
nearly 88% of cloud breaches involve human mistakes, including incorrect settings or poor identity practices.
Identity threats—such as stolen credentials or excessive permissions—are also on the rise, with many organizations reporting identity issues as a major cloud security concern.
These vulnerabilities are amplified by the scale and complexity of modern cloud environments. Many enterprises now operate in multi-cloud configurations—meaning they use more than one public cloud provider—and this complicates visibility, governance, and controls across environments.
Related articles

Joanna KrysińskaSep 15, 202510 min read

Joanna KrysińskaAug 27, 20258 min read
Human and operational challenges
Even as organizations adopt more tools, gaps persist. Cloud security reports often highlight challenges such as limited visibility across cloud and SaaS environments, difficulty enforcing consistent identity and access policies, misconfigurations or overly broad permissions, and skills gaps when securing complex multi-cloud setups.
Cloud security is further complicated by the speed at which breaches happen and the difficulty of spotting them quickly. A majority of cloud incidents aren’t detected or remediated within the first critical hours, increasing the risk of massive data theft or service disruption.
Moreover, as more sensitive data moves to the cloud—including personal, financial, and health information—organizations must ensure compliance with GDPR, HIPAA, PCI DSS, and other frameworks that mandate strong protections for data in transit and at rest.
Why traditional security models fall short
Traditional, perimeter-based network security was not designed to handle the distributed, API-driven nature of cloud workloads and SaaS platforms. Perimeter defenses, such as on-premises firewalls and VPNs, often don’t provide enough visibility into cloud environments or reliably enforce controls once users, apps, and data move outside a defined network boundary.
Instead, organizations need cloud security solutions built for cloud architectures. Such solutions should provide:
Identity and access management (IAM) and control across SaaS and cloud platforms
Continuous monitoring to detect misconfigurations and overly broad permissions
Detection and response tailored to dynamic cloud workloads
Data loss prevention (DLP) and compliance workflows (for example, policy enforcement and audit-ready reporting)
These cloud security tools help keep sensitive data, cloud workloads, and business workflows protected as cloud adoption grows.
The 8 core types of cloud security tools
Modern cloud protection relies on combining several categories of tools. Each addresses a different layer of risk, and together they help security teams maintain control across complex cloud environments.
1. Identity and access management (IAM)
Identity and access management is the foundation of cloud security. In cloud environments, identity—not the network perimeter—is the primary control plane. IAM tools define who can access what, from where, and under which conditions.
IAM platforms manage:
User identities (employees, contractors, partners)
Service accounts and machine identities
Authentication methods (passwords, multi-factor authentication (MFA), certificates)
Authorization policies and role-based access control
Strong IAM reduces security risks by enforcing least-privilege access and preventing unauthorized use of the cloud. Poorly managed identities, on the other hand, can contribute to cloud data breaches.
IAM also plays a key role in:
Conditional access policies
Integration with SASE and enterprise browsers
Without strong IAM, other cloud security tools are less effective.
2. Cloud access security broker (CASB)
Cloud access security brokers sit between users and the cloud, acting as policy enforcement points for SaaS usage. CASBs give you visibility and control over how cloud applications are accessed and used.
Typical CASB capabilities include:
Discovering unsanctioned or risky SaaS applications
Enforcing security policies across approved apps
Monitoring user behavior and access patterns
Protecting corporate and regulated data stored in SaaS platforms
CASBs are especially valuable for organizations struggling with shadow IT, where employees use cloud tools without security review. By identifying and controlling SaaS usage, CASBs can reduce blind spots and prevent data leakage.
While CASBs remain relevant, many of their capabilities are increasingly absorbed into broader architectures like SASE and SSE.
3. Secure access service edge and security service edge (SASE/SSE)
SASE and SSE move security toward a unified, cloud-delivered model. Instead of relying on multiple security solutions deployed at different locations, SASE combines networking and security services into a single, scalable platform.
Key components often include:
Secure web gateways
Zero Trust network access
Firewall-as-a-service
DNS filtering
Threat detection and traffic inspection
SSE focuses on the security components of SASE, without the networking layer.
By routing user traffic through cloud-based security controls, SASE/SSE helps organizations:
Secure remote and hybrid users
Enforce consistent security policies
Reduce reliance on legacy VPNs
Improve visibility across cloud and SaaS environments
4. Enterprise browser
The enterprise browser is an emerging category of cloud security tools designed to secure activity at the browser level—the primary interface for SaaS and cloud applications.
Unlike traditional browsers, enterprise browsers have built-in security controls, allowing organizations to:
Isolate business activity from personal browsing
Prevent data exfiltration through copy/paste or downloads
Enforce access rules based on identity and device posture
Monitor sessions without intrusive endpoint agents
For SaaS-heavy environments, enterprise browsers offer a powerful way to protect confidential business information without degrading user experience. They are particularly effective for:
Contractors and third-party access
Bring your own device (BYOD) scenarios
High-risk SaaS applications
Zero Trust implementations
As browser-based work continues to grow, enterprise browsers are becoming a foundational layer for securing access to SaaS and cloud resources.
5. Data loss prevention (DLP)
Data loss prevention (DLP) tools focus on protecting business-critical information as it moves across cloud environments, endpoints, and SaaS platforms. DLP solutions identify, monitor, and control how data is accessed, shared, and stored.
Core DLP capabilities include:
Classifying sensitive data (personally identifiable information (PII), financial data, intellectual property (IP)
Monitoring data in motion, at rest, and in use
Preventing unauthorized sharing or uploads
Enforcing compliance with regulatory requirements
In cloud services, DLP helps prevent accidental exposure—such as uploading confidential documents to public SaaS apps—or intentional misuse.
Modern DLP tools now integrate with:
CASBs
Enterprise browsers
SASE platforms
This integration allows security teams to apply consistent protection across multiple security tools.
6. Cloud security posture management (CSPM)
Cloud security posture management tools continuously assess cloud environments for misconfigurations, compliance gaps, and policy violations. They scan cloud infrastructure against best practices and regulatory frameworks.
CSPM helps address:
Publicly exposed storage
Weak encryption settings
Insecure network configurations
Non-compliant cloud services
Because misconfigurations are a common cause of cloud security incidents, CSPM plays a critical role in proactive cloud security. Many CSPM tools can also support vulnerability management by identifying configuration-related weaknesses and prioritizing their remediation based on risk.
CSPM tools are essential for maintaining security hygiene across large, fast-changing cloud environments.
7. Cloud infrastructure entitlement management (CIEM)
Cloud infrastructure entitlement management (CIEM) focuses on permissions—specifically, who has access to what in cloud environments, and whether those permissions are actually needed.
CIEM tools analyze:
Excessive or unused privileges
Cross-account access paths
Identity relationships and trust chains
Risky permission combinations
Over time, cloud environments accumulate “permission sprawl,” where users and services retain access they no longer require. CIEM helps enforce least privilege and reduce blast radius in the event of compromise.
For mature cloud security programs, CIEM is a natural extension of IAM and CSPM.
8. Cloud workload protection platform (CWPP)
Cloud workload protection platforms secure the workloads themselves—virtual machines, containers, Kubernetes clusters, and serverless functions.
CWPP tools provide:
Runtime threat detection
Malware and exploit prevention
Integrity monitoring
Protection for cloud workloads across environments
Unlike CSPM, which focuses on configuration, CWPP addresses active threats targeting running workloads. CWPP also contributes to vulnerability management by helping identify exploitable weaknesses in active workloads and responding to threats in real time.
Together, CSPM and CWPP provide complementary coverage for both configuration and runtime security.
Build your cloud’s safety net
Download the free Cloud Security Guidelines PDF and keep risks under control
What to look for when choosing cloud security tools
With so many cloud security tools available, selection the right one can be challenging. The best options are not necessarily the ones with the most features, but the ones that align with your operational reality.
When evaluating cloud security solutions, consider:
Visibility: Can the tool see across all cloud services and SaaS platforms you use?
Integration: Does it work with existing identity systems and security tools?
Scalability: Can it support growth without operational overhead?
Policy management: Are security policies easy to define and enforce?
Signal quality: Does it reduce noise and focus on real security risks?
User experience: Does it protect users without slowing them down?
Avoid overloading your stack with overlapping tools that don’t integrate. A streamlined, well-aligned security approach delivers stronger protection than a fragmented one.
How NordLayer can help
NordLayer helps organizations secure access to SaaS and cloud services by focusing on identity-first, Zero Trust security. Rather than relying on legacy network perimeters, NordLayer protects users, devices, and data wherever work happens.
Key capabilities include:
Secure access to cloud services and SaaS applications
Encrypting traffic to protect against interception
DNS filtering and threat detection
Centralized security policy enforcement
Fitting into modern architectures like SASE
By combining secure access, visibility, and control, NordLayer’s cloud security solutions help organizations reduce risk, simplify operations, and protect cloud environments without compromising productivity.
Cloud security is not a single tool or technology—it’s a strategy. By understanding the eight core tools and how they work together, you can build resilient defenses that scale with your cloud adoption.

Agnė Srėbaliūtė
Senior Creative Copywriter
Agne is a writer with over 15 years of experience in PR, SEO, and creative writing. With a love for playing with words and meanings, she crafts content that’s clear and distinctive. Agne balances her passion for language and tech with hiking adventures in nature—a space that recharges her.