Micro-segmentation is the division of networks into small units. It limits communication within networks by controlling user movement between resources.
The word “micro” means that segments involved are much smaller than regular network macro segmentation. Managers can segment networks at tier, workload, application, or process levels. The result is a high degree of granularity and control over user access. This level of control is also a robust basis for Zero Trust security built around the principle of least privilege.
Micro-segmentation is extremely valuable in modern business settings. It shrinks the threat surface, protecting network assets against attackers breaching the security perimeter. Proper segmentation also helps corporations meet demanding industry regulations via robust data protection.
What are the main types of micro-segmentation
When answering the question what is micro segmentation, we need to be aware of the various segmentation types. Micro segmentation is a broad category and includes a diverse range of approaches. Major variants include:
Network micro-segmentation
This variety closely follows standard network segmentation. It uses Virtual Local Area Network (VLAN) technology to segment data center resources. Access Control Lists (ACL) or IP registers control VLAN access, limiting entry to authorized users.
Network micro-segmentation architecture is familiar. This makes it relatively easy for most IT departments to put in place. But it comes with several drawbacks. Maintaining ACLs and IP constructs is time-consuming and prone to human error. Gaps can emerge between VLAN coverage, providing openings for cyber attackers. The relatively large size of VLAN segments also makes it harder to put in place fine-grained east-west controls.
Hypervisor micro-segmentation
In this form of segmentation, all network data must flow through a hypervisor. The hypervisor creates a virtualized network environment that overlays the existing network infrastructure.
This technique suits companies that need to segment virtual machines. It is a preferred solution for many businesses dependent on VMWare infrastructure. But it is less effective when managing a hybrid mix of wired, remote, and cloud-based assets.
Host agent micro-segmentation
Host agent segmentation takes a different approach. In this case, segmentation revolves around Software Defined Networking (SDN) agents. These agents operate on all endpoints, granting user access and monitoring network traffic.
SDN agents create secure tunnels to route traffic. They apply security policies for each segment and user, authenticating every access request. Network teams can install agents in the cloud, bare metal, and hybrid settings. This diversity makes SDN an effective solution for modern corporate networks.
Flexibility is a critical advantage of host agent segmentation. Managers can determine settings for each app or process via centralized security controls. They can also automate policy delivery and device discovery, ensuring total security coverage.
Agent based segmentation has some drawbacks. The need for many host agents can make this method complex. Network throttling can occur as more devices come online. But host agent micro-segmentation remains a strong option for contemporary settings. It works well in environments mixing remote work, central data centers, and cloud resources.
How does micro-segmentation work?
Most micro-segmentation solutions involve Software Defined Networking controllers. Networking teams can manage SDN controllers on central data centers. But they operate via agents distributed to every endpoint.
SDN agents act as access controls for workloads. Managers determine which assets to include in workload definitions. Organizations can define workloads on a departmental basis, or for different staff roles. The separation of software development departments from production environments offers a good example.
SDN controllers deliver specific security policies to each agent. These policies apply when users access workloads. They then determine whether to permit or deny access. Installed across the network, they provide strong protection against unauthorized east-west movement.
Access controls and agents work alongside network firewalls. Firewalls operate around each workload or application, wrapping the segment in encryption. Tunneling protocols also protect data passing between hosts and the data center. This provides a tightly focused barrier against intrusion.
All data on the network passes through software-defined network agents. Data flowing through these agents generates instant feedback. Managers can learn about network traffic and user behavior. IT teams can instantly detect threats. And technicians can change security policies for any connected device. There’s no need for hardware reconfiguration as everything works via software tools.
Micro-segmentation can apply at many levels:
- Application – Segments protect critical applications or processes. Controls limit east-west communication with other apps. Coverage can extend across on-premises data centers, cloud or hybrid cloud settings. Segmentation protects every aspect of the application along with associated high value data.
- Environmental – Network teams can create segments for different corporate departments and deployment environments. For example, managers can divide software development operations from testing and production. Segmentation controls govern communication between environments. This makes east-west movement much harder.
- Application tier – Organizations can segment networks to gather related tools together for seamless communication. Protections limit access for tiers with more distant connections. For example, companies might microsegment their database, load balancing and processing tiers.
- Users – Segments apply to groups of users such as project members. In this case, network managers can apply controls via Microsoft Active Directory. Policies assign privileges to each user related to their role. No hardware changes are needed.
Micro-segmentation: benefits and challenges
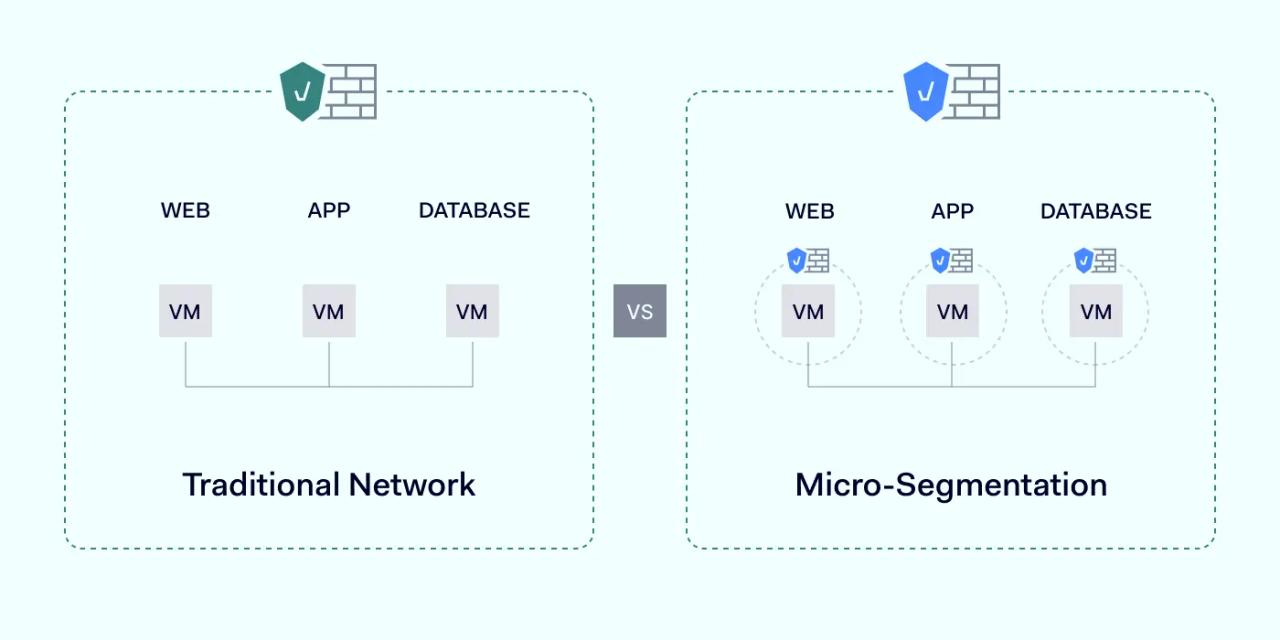
Micro-segmentation offers many benefits compared to traditional network segmentation or perimeter defenses.
1. Shrinking the threat surface
Tightly segmented networks are much less vulnerable to external attackers. Segmenting core assets shrinks the attack surface dramatically. Encryption and security controls secure points of network entry. There are no gaps between VLANs, and networks are not reliant on external firewalls or VPNs.
The use of text to identify network segments also helps reduce the attack surface. Segments defined by text labels are less vulnerable to common network attacks targeting IP addresses or allowed ports.
2. Data breach containment
Traditional network segmentation operates broad Layer 4 controls. Micro-segmentation solutions integrate controls down to Layer 7. This is the level where applications and processes connect to network infrastructure. Segmentation at Layer 7 allows fine-grained controls over lateral movement between apps.
Attackers gaining access to a data center will have nowhere to go. They cannot move between servers or applications, as segmentation renders sensitive data off-limits. Security teams can instantly detect threats. They can contain attackers before they have the ability to cause damage.
3. Flexible scaling and incident response
Micro-segmentation scales effectively as businesses grow. Managers can add new departments or users. They can register role-based security policies featuring user privileges to access essential resources. There is no need to add extra hardware as networks expand. Companies can add or change cloud deployments at will. This makes it easier to find a configuration to balance security and business needs.
4. Enhanced regulatory compliance
Micro-segmenting sensitive data is a reliable route to regulatory compliance in many sectors. PCI-DSS regulations specify tight data handling rules in the credit processing sector. HIPAA lays down strict regulations for storing patient data. In both cases, micro-segmentation is a sensible risk management option for compliance management.
5. Network learning
More information means greater awareness and visibility. A well-informed IT team is ideally placed to manage networks efficiently. Networking and security teams can track data flowing between workloads. The data produced can help identify traffic bottlenecks. Security experts can detect misconfigurations, and isolate vulnerabilities for security teams to resolve.
Micro-segmentation use cases
Applying fine-grained micro-segmentation solves many critical security and networking problems. Companies can deploy the technology in many ways, with a wide range of potential use cases.
Dividing development, testing, and production systems
Segmenting networks separates discrete business processes. This is a strategy often found in software development settings. Segmentation separates development workloads from testing processes. It divides both processes from production or implementation settings, ensuring minimal friction.
Proper segmentation guards against development staff casually accessing sensitive data without authorization. It also contains lateral movement of malware infections acquired during the development phases.
Smooth cloud transitions
Many companies are transitioning from on-premises workloads to cloud environments and SaaS. Making this change can pose security challenges. Legacy security approaches or macro-segmentation are often inadequate when securing cloud resources.
Micro-segmentation is a cloud-optimized solution for companies moving into the cloud. Managers can configure segments for apps spanning many cloud environments and multiple data centers. They can allow app access across distributed geographical sites. Security policies cover every data center and endpoint. Closing gaps in the security perimeter also significantly reduces the risk of data exfiltration.
Strengthening data protection
Data breaches are a critical reputational and financial risk for most companies. This risk is particularly relevant for organizations complying with HIPAA or PCI-DSS regulations. For instance, PCI-DSS compliance requires a secure credit storage environment. HIPAA dictates strong protections for patient records.
Micro-segmentation allows security teams to construct targeted shields around confidential data. Companies can segment cloud containers or information within data centers. This enables privileged access along Zero Trust lines.
Effective malware protection
Micro segmentation is a reliable protection against malware infections. Attackers gaining access to user accounts will only have access to specific resources. Centralized panels track suspicious behavior across the data center. Firewalls and security controls restrict lateral movement denying access without privileges.
Logs generated by host agents form the basis for effective incident response. Security teams can extract in-depth data about any incident. They can use that information to improve security policies. Real-time user tracking also makes it possible to detect and isolate threats as they emerge.
Which businesses need to segment their networks?
Micro-segmentation does not suit all businesses. In some cases, legacy macro-segmentation solutions will suffice. Host agent segmentation may burden network traffic and prove incompatible with core resources. Even so, many modern organizations are using segmentation technology to safeguard their data.
Micro segmentation is well-suited to companies handling large amounts of confidential data. This includes healthcare companies managing patient records. It also spans educational establishments protecting student data, and networks handling credit data.
Network micro-segmentation also fits companies juggling data storage and cloud infrastructure. Agile companies using SaaS solutions for payments and other core business tasks will see major benefits. Standard network perimeter concepts are becoming irrelevant in these situations. Host-agent or hypervisor micro-segmentation is a much more adaptable and effective solution.
Segmentation is also highly relevant for organizations with large communities of remote workers. Network perimeters change when employees choose to work from home. Remote devices pose extra network security risks. Traditional perimeter security measures struggle to provide effective protection.
Software-defined agent micro-segmentation provides a robust solution. Access management tools ensure remote workers can access essential resources while minimizing east-west movement. Poor device security can admit malware agents onto the network. Security tools within micro segmentation packages identify threats quickly.
How to implement micro-segmentation
- Plan your micro-segmentation approach. Before making any infrastructure changes, devise a micro-segmentation strategy. Decide which network resources have the highest priority and need urgent protection. Some resources will need tight security controls. Others require less oversight. It’s a good idea to refer to relevant data regulations at this stage. Ensure that your strategy covers all critical data containers.
- Map the segmentation environment. Create a network map showing every critical app and device on the network. Include data about how they interact. Use these connections to map clusters of resources for each workload. These clusters form the basis for micro-segmentation. When drawing up the network map, clearly label every section. Ensure that these labels are informative and legible for all stakeholders.
- Create and distribute security policies. After drafting a segmentation map, create security policies for every endpoint and user. Assign appropriate security privileges for every role in the organization. Ensure access to role-specific resources only.
- Commission the correct segmentation tools. Choose a micro segmentation solution that meets your needs. Solutions could be purely software-based but may include hypervisor coverage. Organizations not fully transitioned to SaaS may need hybrid setups integrating on-premises hardware.
- Set the right pace for segmentation rollout. Look for “easy wins” when you roll out your micro-segmentation plan. Focus on core data resources to meet compliance requirements. Or separate production from development teams. Short-term tasks set a segmentation baseline and protect critical resources.
- Plan for gradual implementation with zero gaps. Proceed gradually. Test the security integrity of each segmented workload as the project develops. Ensure that workers have access to necessary applications and data. And test network performance to avoid conflicts between segmentation and bandwidth.
- Install network monitoring and threat detection. Put in place security protocols to track network traffic and deal with alerts. Segmentation software should include centralized monitoring tools. Use these tools to track user behavior and detect suspicious patterns. Schedule regular audits, including threat testing. And use network data as raw material to fine-tune segmentation setups where possible.
Choose the ideal segmentation strategy for your network
Micro segmentation is one way to secure network resources and reduce your attack surface. It is well-suited to protecting cloud resources. It can be calibrated to divide workloads and departments. And it offers adaptable protection against east-west movement within data centers.
All of those reasons make fine-grained segmentation an appealing option for cloud-reliant businesses or organizations with large remote working communities.