
Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.
Cybersecurity
Summary: Shadow IT grows when teams need speed. Manage it with visibility, fast approvals, and browser-based controls.
It is 10 A.M. on a Tuesday, and your marketing lead just uploaded the entire customer database to a trendy new AI tool to generate email copy. Do you know where your data just went?
Learning to manage shadow IT is one of the most critical challenges for CIOs and security leaders. With the explosion of AI and intuitive SaaS platforms, the barrier to adopting new software is effectively zero.
A Microsoft report indicates that 71% of UK employees have used unapproved consumer AI tools at work. The days of locking down the perimeter are over. The goal now is governance without gridlock.
Shadow IT is the use of hardware, software, or cloud services by employees within an organization without the explicit approval or knowledge of the IT department. It captures everything from unauthorized smartphones and personal laptops to unverified SaaS subscriptions and public cloud storage accounts. While often adopted to work on tasks, it hides critical digital assets from security protocols and leaves the organization vulnerable to threats.
To solve the problem, you must first understand the motivation. Employees rarely install unauthorized apps or use personal devices because they want to cause a data breach. They do it because they want to do their jobs, and your current IT infrastructure might be getting in their way. In many organizations, the sanctioned technology stack moves at a glacial pace compared to the consumer market.
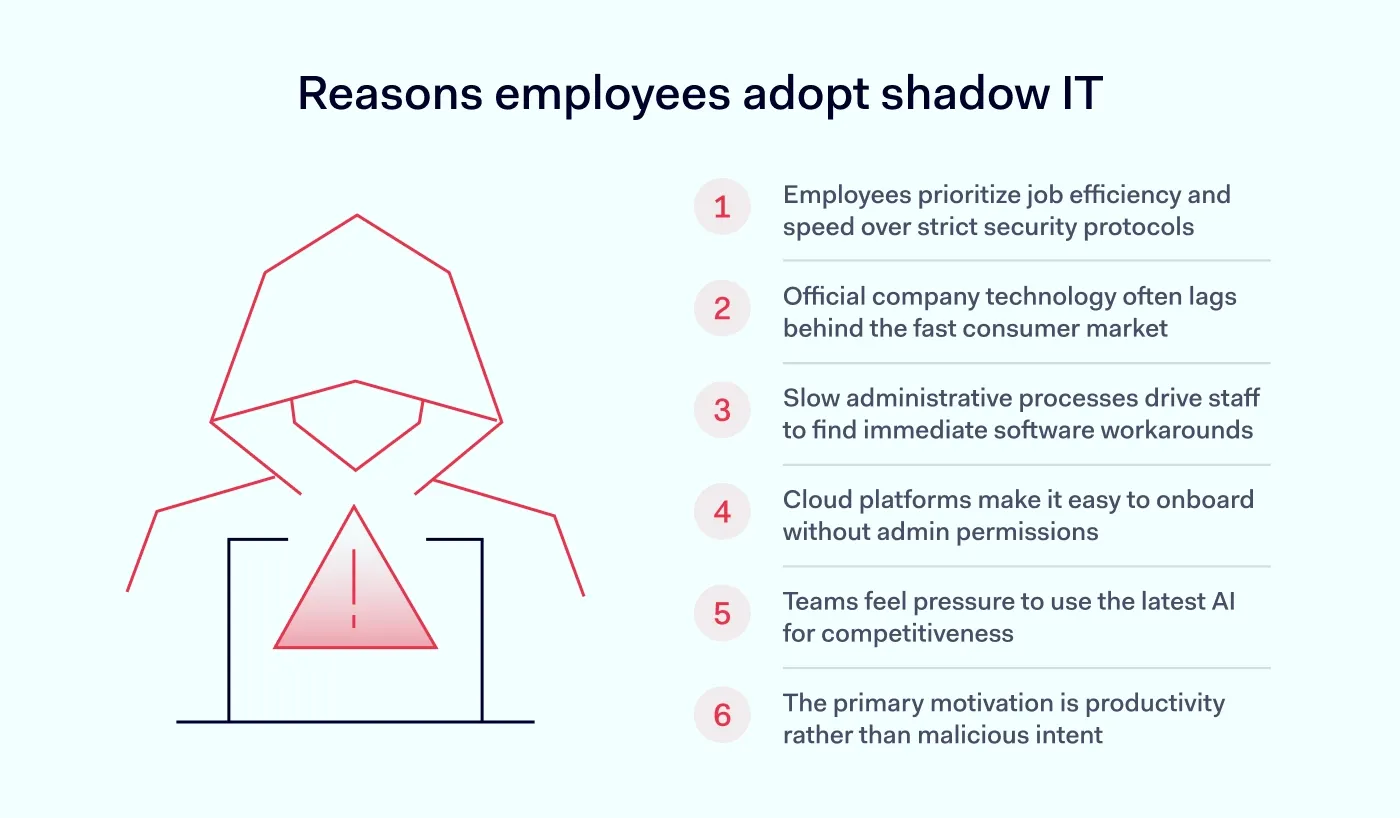
Consider the perspective of a sales director. If they need to convert a PDF to an editable format immediately to close a deal, and the company-approved PDF editor requires a ticket that takes 48 hours to process, they will inevitably find a free online converter. They prioritize business processes and speed over security protocols. This drive to boost productivity is the primary cause of shadow IT.
What’s more, the rise of cloud-based applications has made software procurement incredibly easy. A decade ago, installing software meant physical disks and admin rights. Today, it simply means visiting a website and signing up with a corporate credit card—or even a free tier email. The friction has vanished.
The pressure to adopt AI for competitive advantage also adds fuel to the fire. Teams feel they will fall behind if they don't use the latest unauthorized massive language models, regardless of whether IT has vetted them or not. The intention is almost always benign, but the outcome creates a chaotic, invisible web of unsanctioned dependencies.
While the intent is productivity, the result is often a nightmare for security teams. The most obvious danger is the massive expansion of the attack surface. When IT is unaware of an application, they cannot patch it, monitor it, or secure it.
Data leakage is perhaps the most pervasive threat. When employees move company data into unapproved tools, that data leaves your sphere of control. It might be stored on a server in a country with lax privacy laws, or it might be fed into a public AI model that uses your proprietary code to train its algorithm.
Once sensitive data leaves the managed environment, you cannot recall it. This creates severe compliance risks. You cannot prove you are protecting customer data if you don't even know where it is stored.
There is also the issue of data silos and fragmentation. When a department adopts cloud services without telling anyone, critical institutional knowledge gets trapped in that app. If the employee leaves, access to that data often vanishes with them.
Additionally, unauthorized tools rarely integrate with the central identity and access management (IAM) system. This means there is no offboarding process. An ex-employee could retain access to a project management board or a file-sharing site months after they have been terminated, posing a risk of malicious insider activity. The combined weight of these factors—compliance failure, data loss, and unmanageable access—makes the security risks of shadow IT untenable for modern enterprises.
The “Department of No” mentality, which reflexively denies every new software request, is a failed model. If you try to block every unknown URL and lock down every workstation, users will simply switch to their personal devices and 4G networks. This pushes shadow IT further into the dark where you have zero visibility.
To improve your security posture, you need a mindset shift. You must acknowledge that the existence of shadow IT is actually a signal. It tells you exactly where your approved tools are failing to meet the needs of the workforce. If half the company is using an unauthorized file transfer service, your approved alternative is likely too slow or too difficult to use.
The strategy, therefore, is to bring shadow IT into the light. This involves a concept often called “sanctioned flexibility.” You provide a suite of approved tools that are best-in-class, but you also create a “fast lane” for vetting new tools.
If a marketing team wants a new analytics platform, the security review shouldn't take six weeks. Make the evaluation of cloud-based applications faster, and you reduce the incentive for users to go rogue. You allow the business to move at the speed of the market while wrapping a layer of identity management and data protection around the new applications.
Banning every app will only drive users underground. You need a strategy. Managing shadow IT requires a tactical approach that combines technology, policy, and culture.
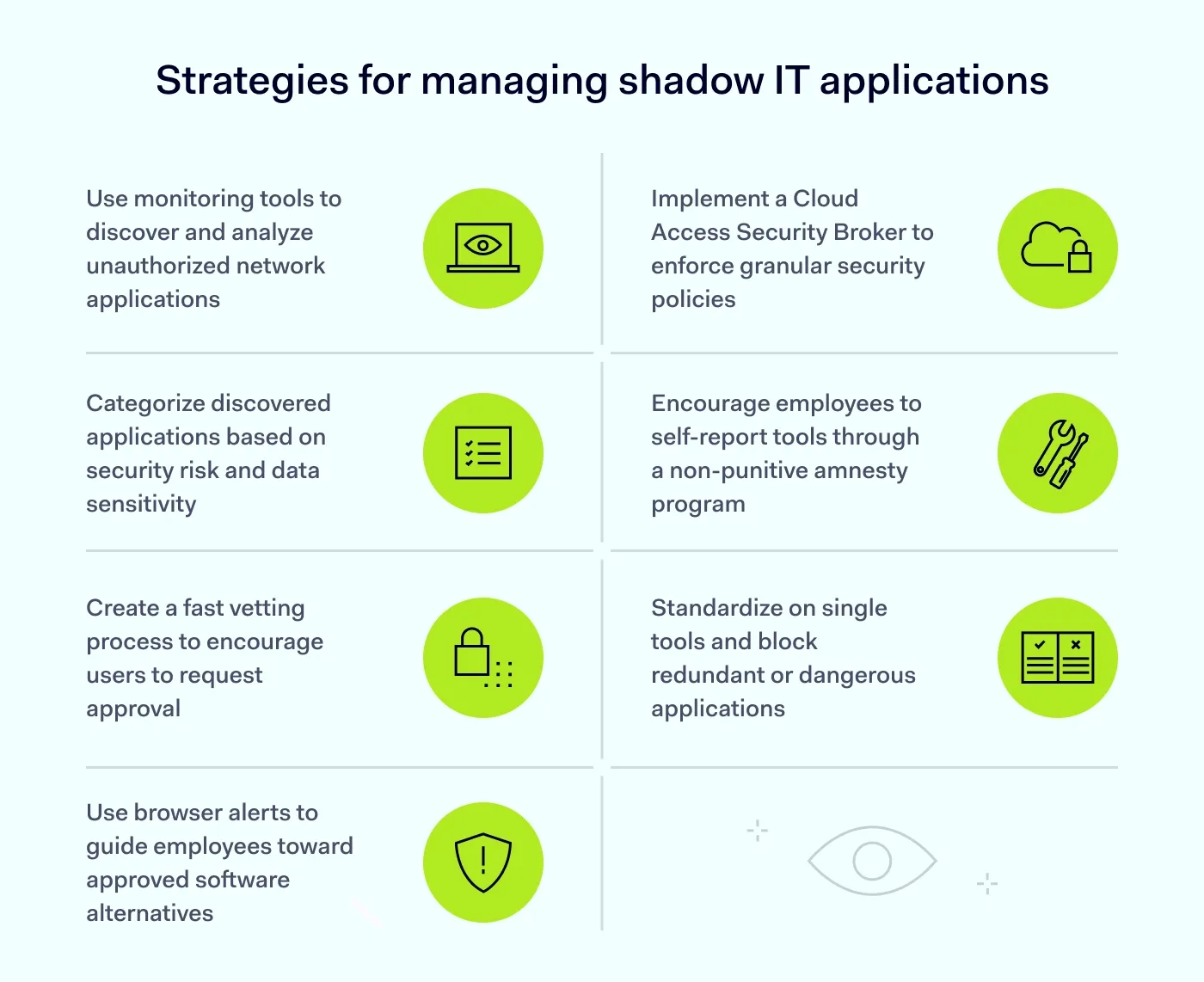
The first step in managing shadow IT is to use monitoring tools that analyze log data from your firewalls, web gateways, and endpoints. A discovery scan will reveal exactly which SaaS applications are running on your network, often uncovering hundreds of apps that IT was unaware of. A baseline assessment is crucial for understanding the true scope of your exposure.
Not all unauthorized apps are equal. A project manager testing a new to-do list app poses a significantly lower risk than a developer pasting source code into a public code repository. Classify discovered shadow IT apps by risk level. Focus your immediate attention on high-risk services that handle sensitive data or require high-level permissions.
To stop users from bypassing you, you must be faster than the alternative. Create a lightweight security review process for low-risk SaaS tools that takes days, not months. If employees know that they can get an official “yes” or “no” quickly, they are far more likely to submit a request rather than simply signing up and hoping for the best.
Instead of hard blocks, use technology that intervenes at the moment of access. When an employee tries to sign up for a known but unsanctioned tool, an enterprise browser can display a warning: “This tool is not approved. Please use [Approved Tool Name] instead.” This guides behavior toward approved tools without causing the frustration of a hard “Access denied” screen.
A CASB acts as an intermediary between your users and cloud service providers. It allows you to manage shadow IT and enforce security policies—such as encryption or data loss prevention (DLP)—even on traffic destined for cloud apps you don't fully control. This technology is essential for granular control, allowing users to view content on a site while preventing them from uploading corporate files to it.
Sometimes the best intelligence comes from asking nicely. Announce a thirty-day “amnesty” period where employees can list the shadow IT tools they are using without fear of reprimand. Frame this as a budget optimization exercise (“We want to pay for the tools you love”) rather than a security crackdown. You will uncover business processes that automated scans might miss.
Once you have identified shadow IT in your organization, look for redundancies. If you find five different video conferencing tools in use, standardize on one and block the others. This reduces costs and simplifies your security posture. Explain the “Why” to your teams so they understand the decision is based on efficiency and security, not arbitrary control.
Managing shadow IT is not a spring cleaning event, it is a lifestyle change. The SaaS market evolves daily. Unauthorized tools that are popular today will be obsolete next year, replaced by new, riskier alternatives. Maintaining control requires continuous monitoring of your network traffic and endpoint behavior.
Regular auditing is essential. Make quarterly reviews of your SaaS inventory standard practice. During these reviews, compare your list of active users in the identity provider against the actual usage logs.
You will often find “zombie accounts”—paid subscriptions that are unused. Or conversely, free accounts that have technically grown into enterprise-level usage without the enterprise-level security contract.
Education also plays a vital role in long-term control. Security awareness training must evolve beyond phishing simulation. It needs to include modules on the economics of free software. Teach employees that “free” usually means they are paying with company data.
When staff understand that uploading a client list to a random website constitutes a data breach, they become partners in security rather than adversaries. By combining monitoring tools with education, you create a resilient environment where innovation can flourish without sacrificing safety.
Ultimately, the most effective way to secure the modern, dispersed workplace is to control the gateway to the web itself. Traditional VPNs secure the tunnel, but they often lack visibility into what happens inside the browser where SaaS applications live. NordLayer is evolving beyond simple access control to offer deep visibility and governance over how your teams interact with the cloud.
With the introduction of browser-based solutions, NordLayer allows organizations to enforce policies right at the edge. You can detect unsanctioned SaaS usage in real-time and apply data loss prevention rules that stop sensitive information from being pasted into unverified AI chatbots.
This approach gives IT leaders the granular control needed to legitimate shadow IT management without deploying heavy agents that slow down user devices. Trusting NordLayer means you can finally bridge the gap between keeping your teams productive and keeping your data locked down.
Subscribe to our blog updates for in-depth perspectives on cybersecurity.