Summary: Learn what ransomware is, how it spreads, its real costs, and 10 practical defenses to prevent attacks and keep business operations running.
Prevent ransomware attacks before they start—that’s the most critical step organizations can take to defend their data, operations, and reputation. Ransomware has evolved into one of the most damaging forms of malicious software, and no industry or business is immune, regardless of size. As threat actors improve their tactics, companies must strengthen their cybersecurity and proactively close the doors that attackers rely on to exploit.
This guide breaks down what ransomware is, how it spreads, and 10 tested, practical strategies to avoid ransomware attacks, all supported by expert insights and industry research.
Key takeaways
Ransomware is a type of malicious software that encrypts files and systems until the victim pays a ransom.
Modern ransomware attacks target businesses of all sizes, often using social engineering, email attachments, and vulnerable remote access points.
A layered approach, including multi-factor authentication (MFA), patching, employee training, segmentation, threat protection, backups, and regular audits, is essential.
Strong ransomware prevention reduces financial loss, downtime, data breaches, and long-term reputational damage.
Solutions like NordLayer provide secure remote access, threat protection, and network segmentation to support ransomware prevention and strengthen organizational defenses.
Ransomware definition
Ransomware is a form of malicious software (malware) that infiltrates devices or networks, encrypts critical files, and blocks access until attackers demand payment—usually in cryptocurrency. A ransomware infection can disrupt business operations, expose sensitive data, and cause significant financial loss. These intrusions often begin with suspicious activity that goes unnoticed until the damage is done.
Recent reports reveal the significant changes in ransomware attacks over the past few years. In 2025, around 41% of ransomware families use AI-based tools to deliver attacks that adapt to each target. This includes automated phishing, polymorphic malware that rewrites itself on the fly, AI-assisted manipulation (such as convincing vishing calls), and payloads that adapt to the victim’s environment.
According to Check Point’s Q2 2025 ransomware report, cybercriminals rarely rely on simple file encryption anymore. Many campaigns now combine encryption with data theft (double extortion), and nearly one-third of major incidents involve triple extortion, where criminals also threaten to leak data publicly or launch DDoS attacks to increase pressure.
These AI-driven methods allow threat actors to move faster, remain hidden longer, and run extortion campaigns more efficiently. As a result, organizations need to stay alert and update their defenses to keep up with these more sophisticated operations.
This means traditional defenses may not be enough: companies that fail to adapt risk falling behind in an arms race in digital extortion.
The importance of ransomware prevention
Ransomware is not only widespread—it’s accelerating. According to our analysis of ransomware attacks, modern campaigns have become faster, more automated, and more destructive, with attacks now capable of encrypting entire networks in minutes. Meanwhile, our broader cybersecurity statistics overview highlights that:
Ransomware remains one of the top three most common types of cyber-attacks worldwide.
Average downtime following an attack increased significantly.
A majority of businesses that suffered ransomware attacks reported long-term operational impact.
The importance of ransomware prevention, therefore, goes far beyond “avoiding a fine” or “protecting customer data.” It determines whether your business can continue operating at all.
Companies need strong ransomware protection in order to:
Maintain operational continuity
Avoid costly recovery efforts
Prevent reputational damage
Protect sensitive workloads
Keep systems compliant
Reduce the success rate of threat actors
Ransomware is designed to take advantage of human error, outdated systems, weak authentication, and open network paths. Its prevention is far easier—and far cheaper—than recovering from the damage or facing ransom demands.
The true cost of ransomware attacks
Ransomware attacks carry far deeper consequences than the initial ransom demand. Even if organizations refuse to pay, the financial and operational damage can be devastating. According to Sophos’ The State of Ransomware 2024 report, the average cost to recover from a single ransomware attack climbed to $2.54 million—a 50% increase compared to previous years. This figure includes technical recovery, system rebuilding, incident response, legal work, and the long-term impact on business operations.
One of the highest hidden costs is downtime. Many organizations face weeks of partial or complete outage, leaving teams unable to serve customers, fulfill orders, or maintain normal workflows. During this time, companies often lose revenue and customer trust, and their productivity is lowered, especially when service-level agreements (SLAs) are impacted.
The financial pressure intensifies with the use of double and triple extortion techniques. Modern ransomware attacks no longer rely solely on scrambling files. Instead, cybercriminals often steal sensitive data first, then demand an additional ransom to prevent exposure. Some attackers escalate further by threatening public data leaks, contacting customers directly, or launching DDoS attacks until payment is made.
Real-world cases show just how steep the costs can become. 61% of mid-size manufacturing companies tend to pay between $500,000 and $1,000,000 to the perpetrators. Yet the ransom itself accounts for only a fraction of the damage. Post-incident forensics, system rebuilding, downtime, legal fees, and contract penalties make up the total cost of the attack. Even after restoring operations, such a company can face shipment delays and customer churn for months.
When compared to these losses, prevention is significantly more cost-effective. Measures like MFA, strict access controls, network segmentation, employee training, and secure off-site backups require far smaller investments than the cost of recovering from even one incident. In most cases, strengthening defenses and implementing consistent ransomware prevention practices saves organizations millions in potential losses, while ensuring business continuity and minimizing long-term risk.
Related articles

Maciej SikoraOct 15, 20257 min read

Agnė SrėbaliūtėJun 17, 20256 min read
How ransomware infects your network
Knowing the true cost and impact of an attack is only half the picture. The next step is understanding how ransomware gets in. In most cases, it infiltrates organizational networks through one of the following paths:
Phishing emails and malicious attachments
The most common method. A user opens a harmful file disguised as an invoice, shipping notice, or internal document. Examples include malicious PDFs, ZIP files, macros, and disguised executables. Attackers often craft these emails to mimic trusted vendors or colleagues, increasing the likelihood of a click. Once opened, the payload can automatically download ransomware or establish a foothold for a larger intrusion.
Social engineering
Threat actors manipulate employees into giving access, sharing login credentials, or interacting with infected files. These attacks rely on psychological tactics such as urgency, fear, or impersonation to bypass technical security controls. Manipulation-based attacks often combine email, phone calls, and fake support messages to build credibility. Even well-trained staff may fall for highly targeted attacks (spear-phishing) that reference real projects or colleagues.
Exploiting unpatched vulnerabilities
Outdated operating systems or applications provide cybercriminals with direct entry points. Attackers routinely scan the internet for known vulnerabilities, especially those with publicly available exploit kits. If patches are delayed, threat actors can gain remote code execution or escalate privileges with minimal effort. Large environments with fragmented update processes are particularly susceptible.
Compromised remote access
Weak RDP configurations, VPN misconfigurations, or exposed ports often serve as entry points. Attackers may brute-force or credential-stuff remote access portals to gain an initial foothold. In some cases, misconfigured firewalls leave remote services publicly exposed without MFA. Once inside, adversaries can move laterally and deploy ransomware across multiple endpoints.
Drive-by downloads
Simply visiting a compromised website can trigger a stealth ransomware installation. These sites often host malicious scripts or exploit kits that silently probe the visitor’s browser for vulnerabilities. Users don’t need to click or download anything—just loading the page may be enough. Drive-by attacks often originate from legitimate websites that have been hijacked or contain malicious ads (malvertising).
Credential theft
Attackers purchase or steal login credentials and use them to access internal systems. Credentials are frequently obtained through infostealer malware, phishing, or breaches of unrelated services. With valid credentials, cybercriminals can bypass many perimeter defenses. High-value accounts, such as domain admins, enable threat actors to deploy ransomware quickly and broadly.
Once inside, ransomware spreads laterally, escalates privileges, and scrambles your data. Some variants also exfiltrate data first, enabling double-extortion (pay to decrypt + pay to stop the leak). Modern ransomware groups often operate like professional organizations, using toolkits, support teams, and automated scripts to speed up the attack lifecycle.
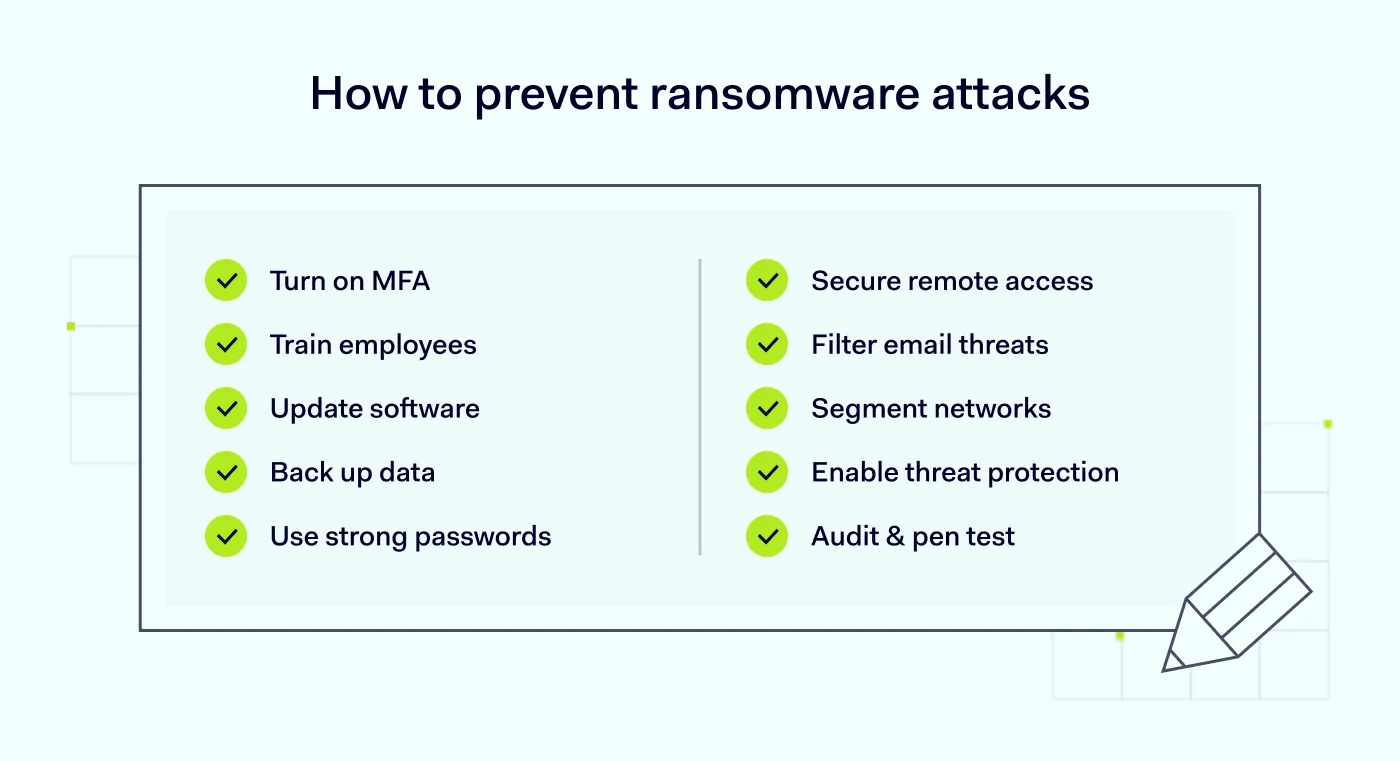
10 tested strategies to prevent ransomware attacks
Below are ten proven best practices to strengthen ransomware prevention, reduce infection risk, and improve your organization's overall security posture.
1. Enforce multi-factor authentication (MFA)
Multi-factor authentication is one of the simplest and most effective methods for ransomware prevention. MFA ensures that even if attackers steal a password through phishing or credential leaks, they still cannot access critical systems without a second verification step.
Effective MFA methods include:
Authenticator apps
Hardware tokens
Push notifications
Biometrics (depending on context)
MFA significantly reduces unauthorized access and blocks ransomware infection attempts that rely on stolen credentials.
2. Train employees on security awareness
Human error is the most common cause of malware attack incidents. Employees must be trained to detect suspicious activity, such as:
Unusual email attachments
Urgent requests to bypass security
Unexpected password reset links
Unknown senders
Files requiring macro activation
Security awareness training should cover manipulation tactics, phishing identification, safe browsing, correct password practices, and reporting procedures. Informed teams are one of the strongest defenses against ransomware.
3. Keep software and systems updated
Unpatched systems are a goldmine for attackers. Many ransomware campaigns exploit widely known vulnerabilities, including ones that have had patches available for months or years. Best practices include:
Automated patch management
Regular OS and application updates
Firmware updates for routers, firewalls, and IoT devices
Prioritizing critical vulnerabilities (CVSS 8+)
Consistent updates close security gaps and significantly reduce infection routes.
4. Backup data regularly and securely
Backups are the foundation of ransomware recovery and prevention. Even if attackers scramble your systems, up-to-date backups allow you to restore operations without paying ransom. Follow the 3-2-1 backup rule:
3 copies of important data
2 different types of storage
1 offsite or offline backup (e.g., immutable storage)
Ensure backups are encrypted, regularly tested, and physically or logically separated from the main network as part of an effective ransomware prevention.
5. Implement strong password policies
Weak or reused passwords increase the risk of credential theft—one of the leading causes of ransomware attacks. To reduce risk:
Enforce long, unique passwords
Require periodic password updates
Prevent password reuse across systems
Combine with MFA
Use password managers to simplify compliance
A strong password policy limits attackers’ ability to brute-force or guess their way into accounts.
6. Secure remote access with VPNs or Zero Trust
Remote access creates new paths cybercriminals can exploit. A secure VPN or Zero Trust Network Access (ZTNA) drastically reduces these risks. NordLayer provides secure remote access solutions that shield connections, isolate access rights, and verify user identity before granting entry.
Zero Trust principles ensure:
Users access exactly what they need—nothing more
Only approved and compliant devices can connect
Access is granted based on specific, verified contexts (e.g., location or time)
Lateral movement is restricted
Unauthorized connections are blocked
Encryption protects data in transit
This significantly increases ransomware protection for remote workers and hybrid environments.
7. Implement email security filters
Since most ransomware begins with phishing emails, strong filtering tools are essential. Effective email protection includes:
Spam filtering
Attachment scanning
Malicious URL detection
Sandboxing
DMARC, SPF, DKIM policies
These filters stop phishing attempts before they reach employees’ inboxes.
8. Use network segmentation
Network segmentation isolates critical systems and reduces how far ransomware can spread if an infection occurs. Network segmentation features include:
Isolated network zones
Limited lateral movement
Granular access controls
Improved visibility into internal traffic
Reduced attack surface
Segmentation ensures that even if threat actors breach one endpoint, they cannot compromise the whole network.
9. Deploy advanced threat protection (ATP)
Basic antivirus tools are no longer enough. Businesses need advanced threat protection capable of detecting sophisticated malware, command-and-control activity, and suspicious behavior. Threat Protection solution offers:
Blocking malicious websites
Anti-malware analysis
Real-time ransomware detection
Prevention of risky outbound traffic
ATP technology is essential for identifying and stopping ransomware before it executes.
10. Conduct regular security audits and penetration testing
Periodic audits help organizations identify weak points such as:
Outdated software
Insecure configurations
Risky access rights
Unprotected endpoints
Overlooked shadow IT
Penetration testing simulates real-world attacks to validate the strength of your defenses. These assessments reveal vulnerabilities long before cybercriminals find them.
Route to safer sites
Keep your network traffic flowing smoothly and safely with NordLayer DNS filtering
How NordLayer helps you prevent ransomware attacks
NordLayer provides tools that help reduce ransomware risk, enable secure remote access, and strengthen overall security. With NordLayer, you can:
Implement a ZTNA approach
Use
Cloud Firewall and access controls to segment networks and limit lateral movement
Block access to malicious websites and detect malware in downloads with DNS Filtering and
Download ProtectionEnforce consistent access policies for all users
Protect remote workers across devices and locations
Monitor connections and device posture, and block non-compliant access based on your policies
NordLayer combines easy deployment with enterprise-grade security controls, helping companies reduce the risk of ransomware attacks and maintain secure operations.
Frequently asked questions
How do I know if I have ransomware?
Signs include encrypted files, locked screens, ransom notes, unusual file extensions, disabled security tools, and sudden system slowdowns. Many modern variants also disconnect backups and attempt lateral movement. Our article Ransomware Attacks in 2025 covers recent attack behaviors.
What does ransomware do?
Ransomware scrambles your files, blocks access to systems, steals sensitive data, and requires payment for decryption. Many forms also attempt double extortion, which means releasing data publicly if the ransom is not paid.
What happens if you get ransomware?
Businesses face downtime, financial loss, data breaches, legal risks, and reputational harm. According to Cybersecurity Statistics of 2025, recovery costs often exceed the initial ransom demand.
Does ransomware go away if you pay?
No. Paying does not guarantee file recovery or prevent future attacks. Many victims who pay are attacked again within months. Cybersecurity experts strongly advise against paying ransom.

Agnė Srėbaliūtė
Senior Creative Copywriter
Agne is a writer with over 15 years of experience in PR, SEO, and creative writing. With a love for playing with words and meanings, she crafts content that’s clear and distinctive. Agne balances her passion for language and tech with hiking adventures in nature—a space that recharges her.