Cybersecurity
Simple and clear guidance on network security, IAM, compliance, and other key cybersecurity aspects.
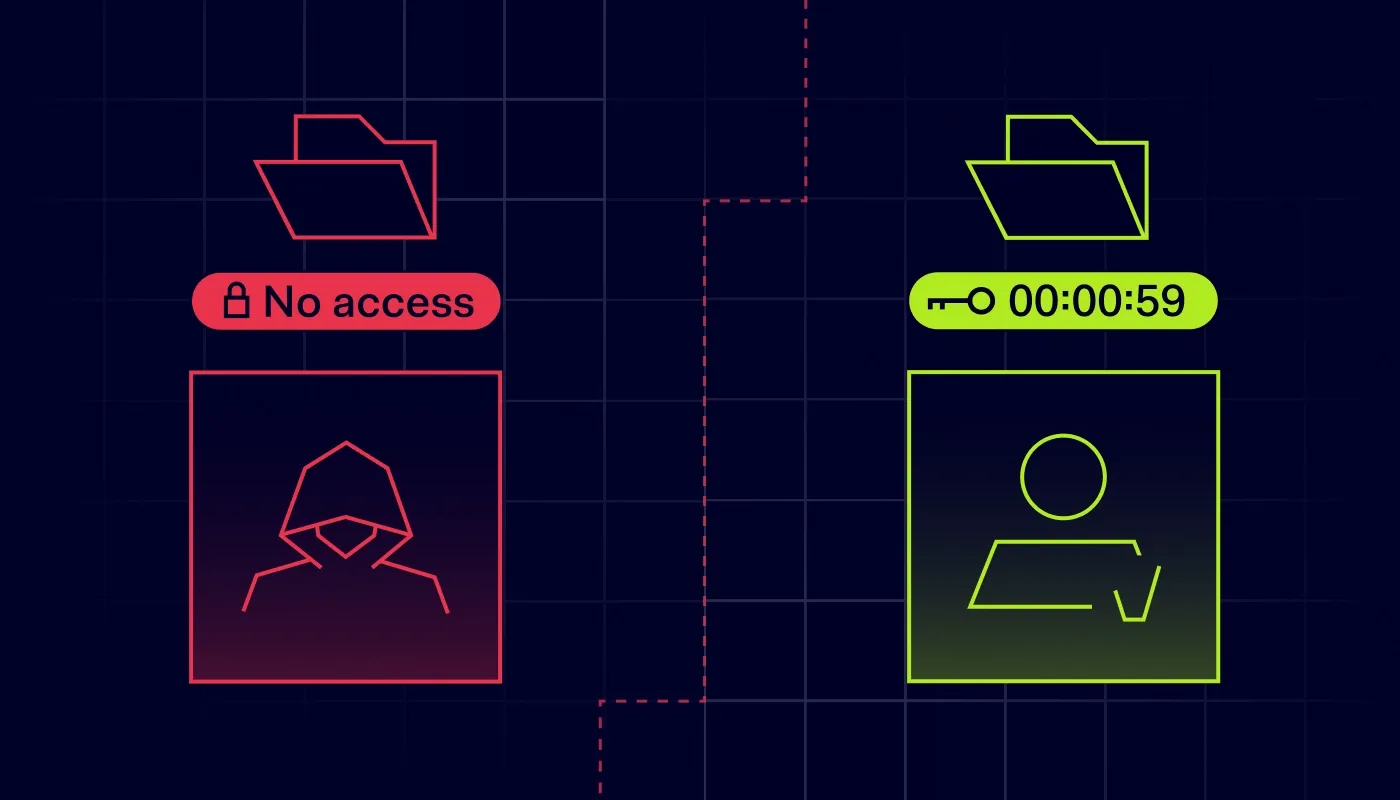
SaaS security fails when stolen creds look “normal.” Verify identity, block risky devices, restrict sharing, and review access regularly.
Stay in the know
Subscribe to our blog updates for in-depth perspectives on cybersecurity.