You don’t need to closely follow cybersecurity news outlets to know the scope of threats that are menacing businesses. New trends like remote and hybrid work only contribute to already swamped businesses trying to catch up in cybersecurity.
For this reason, new security measures are needed to tackle risks that are no match for legacy tools. Thankfully, there’s a good variety of various methodologies that can help businesses out. One such example would be network segmentation.
Key takeaways
- In the face of mounting cyber threats, businesses should explore a range of cybersecurity solutions, with the understanding that revolutionary technology is not always a prerequisite for significant contributions to their security.
- Network segmentation, as an administrative practice, involves dividing a network into smaller segments. These segments can be customized with different security levels for specific networks and limitations on overall user access.
- Network segmentation can be implemented through various methods, including physical segmentation using hardware or virtual segmentation with software. Virtual segmentation itself can be further classified into types such as VLAN or firewall segmentation.
- Network segmentation offers significant benefits, including improved isolation between segments, enhanced access control, monitoring capabilities, and regulatory compliance, making it a straightforward yet highly effective strategy for network security.
Network segmentation definition
Network segmentation involves dividing a large network into smaller sub-networks for improved security and management. By compartmentalizing the network, administrators can implement precise security controls, create tailored security policies, and enforce access restrictions.
How does network segmentation work?
The network’s division into segments allows it to manage each of them individually. Network traffic protocols can supervise what connections and content are allowed. Security protocols can also be applied for each subnetwork to manage overall security rules better.
Network segments frequently have dedicated hardware to minimize touching points between networks. Network configurations usually define interconnectivity between them. This branches out network segmentation into its two types.
Physical segmentation
As you could guess from its name, physical segmentation used dedicated hardware to set up closed-off networks. This also means that this is one of the most difficult and costly network segmentation approaches. Each network segment requires separate internet connections, physical hardware, and a firewall.
This approach is sometimes called perimeter-based segmentation, and everything else outside the network perimeter is considered untrustworthy. The problem is that once hackers penetrate such networks, they don’t have any capabilities to protect themselves. There is no internal filtering, so every user can access everything on the network by default. What made the situation even worse was that due to the amount of currently used endpoints, it was very hard to inspect each connecting device thoroughly.
Virtual segmentation
The modern workplace has so many endpoints that it’s almost impossible to pinpoint where the perimeter ends. Therefore, virtual segmentation aims to extend beyond the perimeter. Switches manage virtual local area networks, and the firewalls are deployed to oversee the whole network independently of physical infrastructure.
Essentially, this flips the idea of the perimeter on its head, and segmentation is something that allows the creation of numerous virtual structures for easier supervision. It has the same benefits as the physical approach but in a distributed model that isn’t susceptible to flaws. This approach is also cheaper and allows adjusting security policies within each segment.
Why do businesses need network segmentation?
For modern organizations, IT infrastructure security is one of the key assets. Network segmentation is a good way to achieve this and reduce cybersecurity expenses. Perimeter-based segmentation plans are being phased out with more modern solutions that better respond to current business needs.
Network segmentation enforces security policies and helps to create boundaries between the teams to prevent data spills. It also helps to distribute network traffic, increasing performance more evenly.
Benefits of network segmentation
Better administrative controls are undeniably one of the greatest appeals of network segmentation. However, this isn’t the only advantage that this approach brings.
- Network isolation. Creating boundaries between different sub-segments increases security, obstructing lateral movement for hackers once they breach the network. With such movement restrictions, it’s also much easier to mitigate threats.
- Strict access control. Subsegment rules can be applied to close off particular network areas, only allowing access to those with clearance.
- In-depth monitoring. Due to their smaller scope, detecting a threat in a subnet is much easier than in a larger network.
- Higher performance. A network’s size can negatively affect its performance. Smaller subnets can be more effective, and it will be easier to balance their load. One segment won’t throttle another segment’s traffic allowing fluid business operations free of network congestion.
- Helps to meet compliance requirements. Most regulatory frameworks require administrators to ensure data’s inaccessibility to unauthorized users. Successful adoption of network segmentation can contribute to your organization’s compliance.
- Safer network and endpoints. A secure network means that threats can’t easily spread to endpoints. The opposite is true — the whole network can’t get infected as it’s limited only to the endpoint.
Challenges of network segmentation
While network segmentation benefits are undeniable, actual preparation and implementation can be a struggle. Several barriers should be considered when implementing it in your business.
Oversegmentation
While it’s true that smaller networks are easier to manage and secure, this should be done reasonably. It’s easy to go too far and begin micro-segmenting your network, which takes time to implement without achieving meaningful results. Good strategic insight can be invaluable here to balance out how small segments should be beneficial rather than detrimental.
Resource mismanagement
Restructuration of the whole network is a serious undertaking in an enterprise. Therefore, it’s important to prepare beforehand to see whether there will be enough personnel to make it happen. Not to mention the needed skillets and other business projects and ventures where they may also be needed. Poor planning can lead to huge setbacks and threaten the project’s success.
Treating network segmentation as a finished project
Cybersecurity shouldn’t be treated as something that’s already taken care of and can be crossed off the list. The same applies to network segmentation. Even after finalizing network segmentation, it should be periodically audited. The reason is that cybersecurity threats constantly change, and your security needs to be improved to better secure against them.
Types of network segmentation
There are many ways to achieve network segmentation, even with virtual means. Here are the most common ones that you could encounter.
[IMAGE OF TYPES]
VLAN network segmentation
Virtual local area networks (VLANs) create smaller network segments using IP addresses for partitioning. This method achieves everything expected from network segmentation and protects against threats spreading from VLANs to VLANs. However, this entails managing an access control list to track which devices can access.
Firewall segmentation
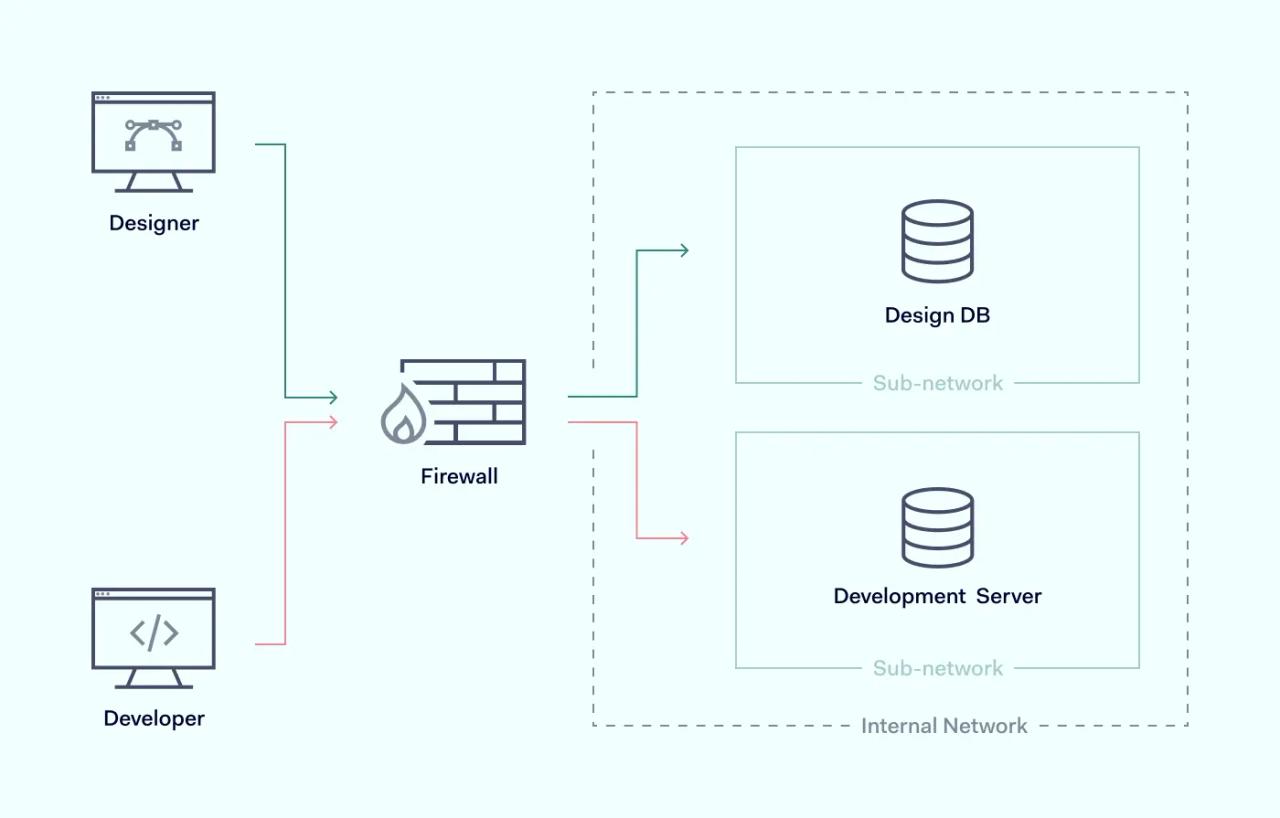
Instead of relying on virtual networks, you can deploy firewalls carving out particular zones. This can block internal communications between them, which helps to limit the spread if the network becomes infected. However, depending on your organization’s size, you may need hundreds of firewalls implemented. Due to its scope, it’s easy to miss important details and introduce considerable complexity to the system.
SDN-based segmentation
Software-defined networking (SDN) uses centralized controllers abstracted from the network’s physical hardware. Its main benefit is that it supports greater segmented network automation and programmability, so it’s possible to set them to do exactly what you need. However, the most frequent use case for those is network security policies implementation rather than security visibility into workflows.
Host-based segmentation
This method relies on special software installed on endpoints to report data back to a central location. It uses technologies like workload telemetry and visualizations to paint a map of multi-cloud environments that humans can easily control from a central dashboard.
Micro-segmentation
This approach uses firewalls deployed in the data center to segment the network by blocking all traffic except for what is allowed. That way, the workloads are divided by applying predefined rules to each unique segment.
Zero Trust & network segmentation
Network segmentation is very useful when paving the way for the Zero Trust approach, where implicit trust is eliminated from the IT infrastructure. In this framework, trust has to be earned through verification.
This helps to address previous network cybersecurity models’ flaws that assumed their perimeter is secure. Therefore, access to Zero Trust is a privilege, and it’s granted only on a case-by-case basis.
Network segmentation is a perfect fit as network division can help to introduce tighter controls for important assets. User access permissions can be configured for each subnetwork, creating barriers to enforcing Zero Trust across the network infrastructure.
In this framework, users aren’t allowed to roam the internal network, and data is freely provided only on a ‘need to know basis. This protects from insider and external threats and reduces the attack surface the hackers could use.